FEDERAL COURT OF AUSTRALIA
CPC Patent Technologies Pty Ltd v Apple Pty Limited [2025] FCA 489
File number(s): | NSD 998 of 2021 |
Judgment of: | BURLEY J |
Date of judgment: | 15 May 2025 |
Catchwords: | PATENTS – patents for secure access systems – claim construction – infringement – validity PATENTS – construction of the asserted claims – construction of seven contested integers PATENTS – infringement – where the impugned devices incorporate biometric security systems utilising fingerprint and face recognition – factual contest regarding operation of the impugned devices – no contested integers found to be embodied in the impugned devices – no infringement found PATENTS – validity – relevant priority date – where patents claim a priority date based on provisional specification –whether patents fairly based on disclosure in provisional specification – external fair basis test – patents not fairly based – deferred priority date applies PATENTS – validity – novelty – where novelty case largely considered on an alternative construction of the contested integers to that accepted by the Court – whether four prior art publications being patents and patent applications anticipate the claimed invention – various claims anticipated on an alternate construction – some claims also anticipated on proper construction PATENTS – validity – insufficiency – ground not established |
Legislation: | Intellectual Property Laws Amendment (Raising the Bar) Act 2012 (Cth) Patents Act 1990 (Cth) ss 7, 18(1)(a), 18(1)(b)(i), 40(2)(a), 40(3), 43(2) Patents Amendment (Innovation Patents) Act 2000 (Cth) Patents Regulations 1991 (Cth) regs 3.12(1)(b), 3.12(1)(c), 3.12(2)(a), 3.12(2C) Statute of Monopolies (1623) (21 Jac 1, c 3) s 6 |
Cases cited: | Anaesthetic Supplies Pty Ltd v Rescare Ltd [1994] FCA 304; (1994) 50 FCR 1 Apotex Pty Ltd v ICOS Corporation (No 3) [2018] FCA 1204; (2018) 135 IPR 13 Aristocrat Technologies Australia Pty Limited v Konami Australia Pty Limited [2015] FCA 735; (2015) 114 IPR 28 AstraZeneca AB v Apotex Pty Ltd [2015] HCA 30; (2015) 257 CLR 356 AstraZeneca AB v Apotex Pty Ltd [2014] FCAFC 99; (2014) 226 FCR 324 Australian Securities and Investments Commission v Hellicar [2012] HCA 17; (2012) 247 CLR 345 Bitech Engineering v Garth Living Pty Ltd [2010] FCAFC 75; (2010) 86 IPR 468 Britax Childcare Pty Ltd v Infa-Secure Pty Ltd (No 4) [2015] FCA 651; (2015) 113 IPR 280 Catnic Components v Hill & Smith Ltd [1982] RPC 183 CCOM Pty Ltd v Jiejing Pty Ltd [1994] FCA 396; (1994) 51 FCR 260 Commissioner of Patents v Rokt Pte Ltd [2020] FCAFC 86 (2020) 277 FCR 267 Coretell Pty Ltd v Australian Mud Company Pty Ltd [2017] FCAFC 54; (2017) 250 FCR 136 Encompass Corp Pty Ltd v InfoTrack Pty Ltd [2019] FCAFC 161; (2019) 372 ALR 646 Flour Oxidizing Company Ltd v Carr & Co Ltd [1908] 25 RPC 428 General Tire & Rubber Co v Firestone Tyre & Rubber Co Ltd [1971] 7 WLUK 130; [1972] RPC 457 Hanwha Solutions Corporation v REC Solar Pte Ltd [2023] FCA 1017; (2023) 180 IPR 315 Jupiters Ltd v Neurizon Pty Ltd [2005] FCAFC 90; (2005) 222 ALR 155 Leonardis v Sartas No 1 Pty Ltd [1996] FCA 449; (1996) 67 FCR 126 Lockwood Security Products Pty Ltd v Doric Products Pty Ltd [2004] HCA 58; (2004) 217 CLR 274 Merck Sharp & Dohme Corporation v Wyeth LLC (No 3) [2020] FCA 1477; (2020) 155 IPR 1 Meyers Taylor Pty Ltd v Vicarr Industries Ltd [1977] HCA 19; (1977) 137 CLR 228 Novartis AG v Pharmacor Pty Limited (No 3) [2024] FCA 1307 Pharmacia LLC v Juno Pharmaceuticals Pty Ltd [2022] FCA 92; (2022) 165 IPR 200 Rescare Ltd v Anaesthetic Supplies Pty Ltd [1992] FCA 811; (1992) 111 ALR 205 Technological Resources Pty Limited v Tettman [2019] FCA 1889; (2019) 375 ALR 185 |
Division: | General Division |
Registry: | New South Wales |
National Practice Area: | Intellectual Property |
Sub-area: | Patents and associated Statutes |
Number of paragraphs: | 673 |
Date of last submission/s: | 18 February 2024 |
Date of hearing: | 16–20 October 2023; 27 October 2023 – 3 November 2023; 5–9 February 2024 |
Counsel for the Applicant / Cross-Respondent: | Mr AJL Bannon SC, Mr C Dimitriadis SC, Ms M Evetts |
Solicitor for the Applicant / Cross-Respondent: | Gilbert + Tobin |
Counsel for the Respondents / Cross-Claimants: | Mr B Caine KC, Mr A Lang SC, Mr P Creighton-Selvay |
Solicitor for the Respondents / Cross-Claimants: | DLA Piper |
ORDERS
NSD 998 of 2021 | ||
| ||
BETWEEN: | CPC PATENT TECHNOLOGIES PTY LTD (ACN 615 736 028) Applicant | |
AND: | APPLE PTY LIMITED (ACN 002 510 054) First Respondent APPLE INC. Second Respondent | |
AND BETWEEN: | APPLE PTY LIMITED (ACN 002 510 054) (and another named in the Schedule) First Cross-Claimant | |
AND: | CPC PATENT TECHNOLOGIES PTY LTD (ACN 615 736 028) Cross-Respondent | |
order made by: | BURLEY J |
DATE OF ORDER: | 15 MAY 2025 |
THE COURT ORDERS THAT:
1. The parties confer and supply to the chambers of Justice Burley by 4pm on 12 June 2025 draft short minutes of order giving effect to these reasons and a proposed timetable for further steps to be taken in the proceedings.
2. Until further order, the reasons for judgment not be disclosed to or published by any person, save for those persons who have executed suitable confidentiality agreements as determined in the first instance by the solicitors acting for the parties.
3. The parties confer and supply to the chambers of Justice Burley by 4pm on 12 June 2025:
(a) a list identifying any paragraphs or parts therefore of these reasons for judgment which are said to contain confidential information and that ought not be published in an unredacted form, including the reasons why such a confidentiality claim is made; and
(b) a copy of these reasons for judgment with the paragraphs or parts therefore which are said to contain confidential information highlighted (or otherwise marked for identification).
4. Insofar as the parties are unable to agree to the terms of the draft short minutes of order referred to in order 1 or the list of confidential information referred to in order 3, the areas of disagreement should be set out in mark-up.
5. The proceedings be listed for case management at 9:30am on 18 June 2025.
Note: Entry of orders is dealt with in Rule 39.32 of the Federal Court Rules 2011.
REASONS FOR JUDGMENT
BURLEY J:
1. INTRODUCTION
1.1 The proceedings
1 CPC Patent Technologies Pty Ltd contends that Apple Pty Ltd and Apple Inc (collectively, Apple) have infringed claims of two patents, both entitled “Remote entry system”, by the use of biometric security systems – fingerprint recognition (touch ID) and face recognition (face ID) – for the purpose of unlocking all or parts of certain Apple devices. The patents relate to the field of secure access systems and, in particular, to systems using wireless transmission of security code information.
2 The patents claim a priority date of 13 August 2003. CPC contends that Apple has infringed claims 1, 2, 3, 5 and 6 of Australian patent no. 2004301168 (168 patent) and claims 1, 27, 29, 37, 39 and 41 of Australian patent no. 2009201293 (293 patent). These are referred to below as the asserted claims.
3 Apple denies infringement and contends that the patents are invalid for want of novelty, absence of an inventive step, lack of manner of manufacture and grounds pursuant to s 40 of the Patents Act 1990 (Cth).
4 The applicable version of the Patents Act is that following the amendments made by the Patents Amendment (Innovation Patents) Act 2000 (Cth), but before those made by the Intellectual Property Laws Amendment (Raising the Bar) Act 2012 (Cth) (RTB Act).
5 By orders made on 6 May 2022 questions of liability for infringement are to be heard and determined separately and before questions relating to pecuniary relief. This judgment accordingly addresses liability only.
1.2 CPC’s infringement case
6 In its further amended statement of claim, CPC contends that Apple infringes the patents by offering for sale and selling in Australia, at various identified dates, 49 devices with touch ID and 21 devices with face ID, and 48 accessories that work with some or all of those devices. CPC sets out its infringement case in its fifth further amended position statement on infringement dated 27 October 2023 and in a document of the same date entitled “Applicant’s integer breakdown with cross-references to the Workings Documents”.
7 The parties agreed in advance of the trial that disputes in relation to the workings of these devices and accessories can be resolved by reference to the following five exemplar categories:
(1) iPhones and iPads with touch ID;
(2) MacBooks with touch ID;
(3) iPhones and iPads with face ID;
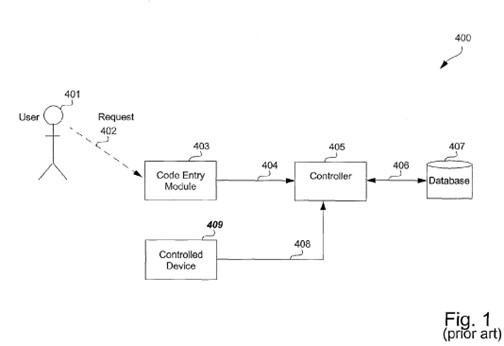
(4) Apple Watches in combination with Apple Devices; and
(5) Magic Keyboards in combination with Apple Devices.
I refer below to the impugned iPhone, iPad and MacBook devices as the Apple Devices.
8 It may be noted that iPhones and iPads use the iOS operating system and MacBooks use the MacOS operating system. This distinction is relevant to consideration of the infringement case.
9 The infringement case raises significant issues concerning the construction of the asserted claims and their application to the Apple Devices.
10 During the interlocutory stages of the proceedings there were also a number of issues about whether or not Apple had adequately disclosed the workings of its devices. This is perhaps not surprising given that they are complex items of hardware and software. I refer to some of the disputed matters later in these reasons. However, I note that by the time of closing submissions disputes as to the operation of the devices were largely resolved. Thus, the major dispute concerns whether or not the Apple Devices fall within the scope of the claims.
11 I set out in some detail, in section 5 below, the operation of the Apple Devices, including the role of various hardware and software components within the Apple Devices, and the steps undertaken by them in the biometric enrolment and biometric matching processes. The internal operations of the Apple Devices are, I accept, confidential. Accordingly, it has been necessary to mark the parts of these reasons that provide details of those operations relevant to the dispute between the parties as not for publication.
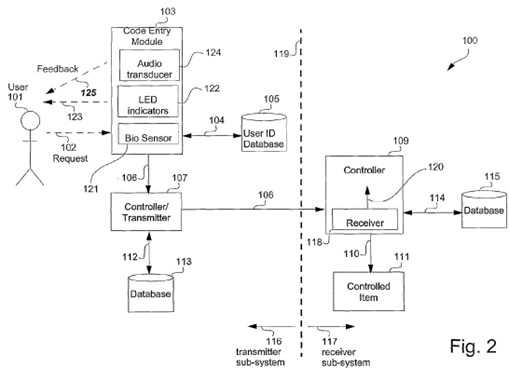
1.3 Apple’s invalidity case
12 In its further amended statement of cross claim dated 4 October 2023 Apple advances the following grounds for the revocation of the asserted claims of the 168 patent, namely that the asserted claims:
(1) are not entitled to claim priority from 13 August 2003 based on the earliest priority document filed in respect of that patent, being Australian patent application no. 2003904317 (provisional specification), because the asserted claims are not fairly based on matters disclosed in the provisional specification, as required by s 43(2) of the Patents Act, with the consequence that the deferred priority date of 13 August 2004 applies, being the filing date of the 168 patent;
(2) are not novel because of the publication, before the priority date, of each of:
(a) United States patent no. 6,164,403 (Wuidart);
(b) United States patent application no. 2002/0138767 A1 (Hamid);
(c) United States patent no. 6,484,260 B1 (Scott);
(d) United States patent no. 6,182,221 B1 (Hsu); and
(e) Reference Guide – hp iPAQ Pocket PC h5400 series – Document Part Number: 281984-001 (iPAQ Reference Guide);
(3) are not novel because of the publication, before the deferred priority date, of each of the documents identified in (2) above and:
(a) United States patent application no. 2004/0123113 A1 (Mathiassen);
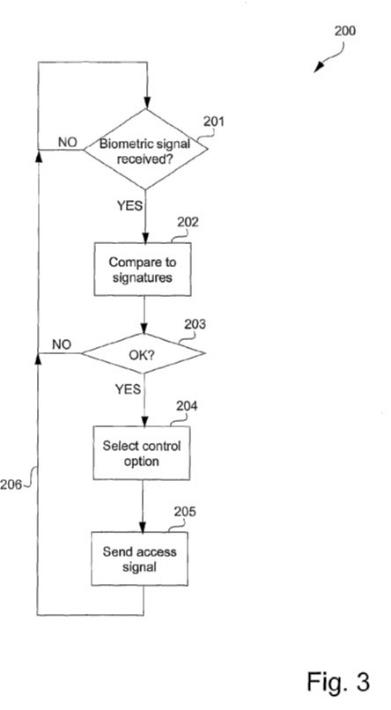
(4) lack inventive step before the priority date in the light of the common general knowledge alone and also having regard to the disclosure of each of Hamid, Scott and Hsu;
(5) lack inventive step before the deferred priority date in the light of the common general knowledge alone and also having regard to the disclosure in each of the documents identified in (3) and (4) above;
(6) lack a manner of manufacture;
(7) lack fair basis within s 40(3) of the Patents Act;
(8) lack clarity within s 40(3) of the Patents Act; and
(9) are not valid because the complete specification does not fully describe the invention as claimed, as required by s 40(2)(a) of the Patents Act.
13 Apple advances the substantially the same grounds of invalidity in respect of the asserted claims of the 293 patent.
14 On 18 February 2024, following closing submissions in the proceedings, Apple indicated that it: (a) no longer presses its novelty case in respect of Hsu; and (b) no longer presses its lack of inventive step case based on s 7(3) of the Patents Act, and seeks only to press its lack of inventive step case as at the relevant priority date in light of the common general knowledge alone. It also indicated that it does not press certain grounds of invalidity dependent upon the resolution of some of the construction arguments. I refer to this further below.
1.4 Agreed primer and common general knowledge summary
15 The parties produced a document entitled “Combined Primer and CGK Summary” in response to directions made early in the proceedings. Those directions required that: (a) CPC identify a portion of its expert evidence in chief on its infringement claim that contains an introduction to the relevant technology and a glossary of relevant terms as at the priority date which may serve as a technical primer; (b) Apple identify a portion in its expert evidence in chief on its cross-claim that includes a summary of the relevant common general knowledge known to the person skilled in the art before the priority date; and (c) each party respond, by its expert evidence, to the primer and the common general knowledge summaries indicating whether the expert agreed with its contents and otherwise marked it up to indicate where they disagree with or wish to supplement its contents with additional detail.
16 A separate document was then prepared which included this mark-up, resulting in the combined primer and common general knowledge summary document, as filed. In the present case, Associate Professor Boztas and Dr Dunstone were the experts who contributed to the primer and the common general knowledge summary. Where I refer below to the primer or common general knowledge summary, it is generally to the relevant portions of the Combined Primer and CGK Summary that have been agreed.
2. THE WITNESSES
2.1 Apple Engineers
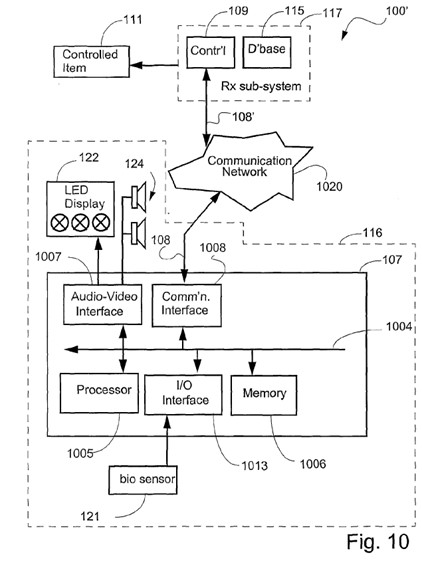
17 Petr Kostka has been a software development manager for the Core OS team at Apple Inc. since 2012. He is based in Prague, Czech Republic, and is responsible for the management of a team of nine engineers and managers whose role is to create and update the software that provides biometric services to software applications running on Apple’s operating systems. His team is also responsible for the software that controls touch ID and most of the software that controls face ID, including the interaction between the software the controls face ID and certain hardware components such as the Secure Enclave Processor (SEP). He gives evidence that he has a detailed understanding of the design, development and operation of touch ID and face ID on all Apple products since 2012. Mr Kostka affirmed three affidavits, on 12 July 2023, 28 September 2023 and 14 October 2023. He also verified the accuracy of the Product and Process Description (PPD) dated 27 May 2022.
18 In his first affidavit, Mr Kostka addresses the PPD, provides an overview of touch ID and face ID as it operates at a high level and describes the process of enrolling a fingerprint using touch ID. He refers to the hardware and software components involved in enrolment for touch ID and face ID and provides some detail of the process of unlocking the device using touch ID. He also describes enrolling and unlocking the device using face ID and the use of the fingerprint sensor on the Magic Keyboard and responds briefly to evidence given by Associate Professor Boztas.
19 In his second affidavit, Mr Kostka gives evidence about Apple Wallet and Apple Pay, including the role of a piece of code known as SSE (or Secure, Secure Element) and the authentication process for Apple Pay. In his third affidavit, he responds to evidence given by Professor Smith.
20 Mr Kostka was cross examined.
21 Wade Benson is a software development engineer and has been working within the Security Engineering and Architecture team at Apple Inc. since 2011. He affirmed three affidavits, on 12 July 2023, 28 September 2023 and 14 October 2023.
22 In his first affidavit, he addresses a number of matters including the security architecture used during the unlocking of an Apple product by reference to a high-level description of the hardware and software components of the device and gives evidence about data protection on Apple products. He describes unlocking an Apple product using a passcode, communication between and within the Application Processor (AP) and the Secure Enclave Processor (SEP) and unlocking an Apple product following a touch ID or face ID match. He refers to the PPD and gives evidence that in his affidavit he describes “with greater precision and detail” aspects to which reference is made in the PPD.
23 In his second affidavit, Mr Benson describes further detail regarding unlocking an Apple product and describes further levels of authentication for particular applications within an Apple product, accessing a Keychain item on an Apple device, applications imposing security policies, multi-user access on macOS devices and differences in unlock processes depending on the type of user account. In his third affidavit, he responds to evidence given by Professor Smith.
24 Mr Benson was cross examined.
25 Nicole Wells has, since October 2019, been a machine learning manager in the Face ID Algorithm Team in the Video Engineering Group at Apple Inc., which is responsible for the software that controls the face ID matching and enrolment algorithms located in the Secure Enclave on the System on a Chip (SoC). She affirmed one affidavit on 12 July 2023 where she describes enrolling a face on Apple products using face ID, the algorithms used in that process and the process of matching to unlock the device.
26 Ms Wells was cross examined.
27 Timothy Paaske is an electrical engineer who has been employed by Apple since 2011 in a variety of roles related to hardware architecture. His current role is as an Engineering Director of two teams, Platform Architecture Security and Power/Performance/Thermals. Mr Paaske affirmed two affidavits, on 7 September 2023 and 14 October 2023.
28 In his first affidavit, he gives evidence about the role and functionality of the “Apple Fabric”. In so doing, he explains that the term “fabric” in computer systems refers to the interconnections between components that are formed into a single silicon chip and that the Apple Fabric is used to refer to the silicon interconnections between different fabric agents and the memory sub-system. He explains that the term “agent” is used to refer to a component that accesses and communicates over the Apple Fabric. He also gives evidence that the Apple Fabric may be described as a “bus”, being a communications system that transfers data between components inside a computer.
29 In his second affidavit, he provides annotations to a block diagram included in his first affidavit, as well as some corrections to his first affidavit.
30 Mr Paaske was cross examined.
31 I refer to Mr Kostka, Mr Benson, Ms Wells and Mr Paaske collectively as the Apple Engineers.
2.2 Apple Lay evidence
32 Brenda Sherman has been a senior litigation paralegal at HP Inc., the successor to the Hewlett-Packard Company, since 2009. Ms Sherman affirmed an affidavit on 31 May 2023, giving evidence about the publication of the iPAQ Reference Guide, which is relied upon by Apple in its invalidity case.
33 Ms Sherman was not cross examined.
34 Christopher Butler is an office manager at the Internet Archive, a website that provides access to a digital library of internet sites. He gives evidence about the operation of the “Wayback Machine”, which enables users to browse historical webpages stored in the Internet Archive’s web archive. He annexes to his affidavit a print-out of the programs for The Biometric Consortium Conferences held in February and September 2002.
35 Mr Butler was not cross examined.
2.3 Expert evidence
36 Serdar Boztas is an Associate Professor of Information Security at the Royal Melbourne Institute of Technology University with over 40 years’ experience in biometrics, cryptography and information security. In this role, he has convened courses on cryptography, information and coding theory, information security, smartcard cryptosystems and mathematics. Associate Professor Boztas is also the Director of Communications, Cybersecurity and Cryptography Research at the University Research Foundation, Maryland Advanced Development Laboratory. In 1990 he was awarded a Doctorate in Electrical Engineering from the University of Southern California and from 1992 to 1995 he was a lecturer at Monash University focussing on courses in communication engineering.
37 Associate Professor Boztas was asked to give expert evidence by CPC and affirmed four affidavits, dated 2 March 2023, 25 July 2023, 17 August 2023 and 29 October 2023.
38 In his first affidavit he identifies and describes technical terms used in the field of the patents and specific terms and phrases used in the specifications. He also gives evidence that he had reviewed the PPD and various other Apple documents which he relies upon to provide his opinion as to whether the Apple Devices fall within the asserted claims. In his second affidavit, he gives his opinion as to the qualifications, experience and expertise of the skilled addressee of the patents and responds to Dr Dunstone’s evidence regarding the common general knowledge before addressing the evidence of Dr Dunstone concerning the relevance of the prior art documents, relied upon by Apple, to the claimed invention. In his third affidavit, Associate Professor Boztas records that he was provided with the affidavits of Mr Kostka, Mr Benson and Ms Wells dated 12 July 2023, the fifth affidavit of Dr Dunstone dated 14 July 2023 and some confidential source code applicable to the Apple Devices and provides his confidential responses to these in the context of the infringement case. In his fourth affidavit, he was provided with additional material relating to the touch ID and face ID functionality in the Apple Devices by reference to extracts of oral evidence from Mr Kostka, Mr Benson and Ms Wells. He reviews those extracts and gives additional evidence in relation to CPC’s infringement case.
39 Hugh Smith is a Professor of Computer Science/Computer Engineering at California Polytechnic State University, with over 40 years’ experience in programming and computer hardware and software. He was asked to give expert evidence by CPC and swore four affidavits, on 15 August 2023, 7 October 2023, 12 October 2023 and 17 October 2023 which largely set out his understanding of the components and workings of the Apple Devices in respect of touch ID and face ID as disclosed in the PPD, Apple documents provided to him by Gilbert + Tobin, the solicitors acting for CPC, and the affidavits of the Apple Engineers.
40 Professor Smith was the subject of limited cross examination and did not participate in the preparation of a joint expert report or concurrent evidence. Where I refer below to the evidence of the experts, unless otherwise stated, this is a reference to Associate Professor Boztas and Dr Dunstone, but not Professor Smith.
41 Edward Dunstone is a computer systems engineers and the Chief Executive Officer of Biometix Pty Ltd, a biometric consultancy that assists governments and other organisation with biometric and identity security systems. Dr Dunstone has worked in the field of secure access and biometrics for over 25 years. He was asked to give expert evidence by Apple and affirmed seven affidavits dated 20 March 2023, 24 March 2023, 5 May 2023, 17 May 2023, 14 July 2023, 29 September 2023 and 29 October 2023.
42 In his first affidavit, he gives details of his background and experience before the priority date, how he kept up with developments in the field of the patents and matters he considered to be within the common general knowledge in the field. In his second affidavit, he gives evidence of how he would solve an hypothetical problem posed by the solicitors instructing him and the characteristics of a person skilled in the art relevant to the patents. He addresses the prior art relied upon in Apple’s lack of novelty and lack of inventive step cases and then turns to the patents, providing his understanding of their disclosure and his understanding of terms in the claims. He also addresses the disclosure of the provisional specification, being the priority document for the patents. In his third affidavit, Dr Dunstone makes corrections to his earlier affidavits.
43 In his fourth affidavit, he considers the iPAQ Reference Guide in the context of the infringement, lack of novelty and lack of inventive step cases. In his fifth affidavit, Dr Dunstone is provided with a copy of the PPD and various Apple documents annexed to the PPD, as well as some additional Apple materials and the first affidavits of Associate Professor Boztas, Mr Kostka, Mr Benson and Ms Wells. He also refers to inspecting Apple’s source code in June 2023 and provides a summary of his understanding of the operation of the touch ID and face ID functionality of the Apple Devices. He then gives his opinion as to whether the integers in each of the asserted claims are present in the Apple Devices before responding to the evidence of Associate Professor Boztas in relation to the construction of the patents and infringement of the asserted claims.
44 In his sixth affidavit, Dr Dunstone annexes copies of his first and second affidavits with the amendments indicated in his third affidavit shown in mark-up. In his seventh affidavit, Dr Dunstone refers to the October 2023 affidavits of Messrs Benson, Kostka and Paaske and the transcript of their oral evidence and the oral evidence of Ms Wells. He is also provided with two confidential workings documents. He then gives opinion evidence concerning the infringement case.
45 Associate Professor Boztas and Dr Dunstone participated in a series of joint expert conferences and produced a joint expert report on 15 September 2023 (JER 1). Following the filing of further evidence of Messrs Kostka, Benson and Paaske in September 2023 shortly before the commencement of the hearing on 16 October 2023, Associate Professor Boztas and Dr Dunstone conferred and produced a second joint expert report on 5 October 2023. They gave concurrent evidence and were cross examined.
46 Rodney Cruise is an IP researcher and patent attorney, a partner of Phillip Ormonde Fitzpatrick and manager of IP Organisers Pty Ltd, an intellectual property research service company. He was asked to give expert evidence by Apple and affirmed an affidavit on 24 March 2023. He gives expert evidence about two searches that he was instructed to carry out for publications available on various databases prior to 13 August 2003 and 13 August 2004 and gives his opinion as to whether various prior art documents relied upon by Apple in its invalidity case would have been available before those dates.
47 Mr Cruise was cross examined.
48 George Mokdsi is a patent searcher and a director of The Patent Searcher Pty Ltd, a company specialising in patent analysis and research. He has been engaged full time in the conduct of patent searching and analytics since 2000. He was asked to give expert evidence by CPC and swore two affidavits, on 28 July 2023 and 27 October 2023. He gives evidence in answer to the affidavit of Mr Cruise, taking issue with the searches that he conducted, and the opinions expressed regarding those search results, including in relation to the searching parameters available in August 2003 and August 2004 and the results likely to have been returned as at those dates.
49 Mr Mokdsi was cross examined.
3. THE PATENTS
50 The specification of each the patents is materially the same with the exception of the consistory clauses and claims. For convenience, unless otherwise stated, the references below are to the 168 patent.
3.1 The specification
51 The “Field of the Invention” relates to secure access systems and, in particular, to systems using wireless transmission of security code information.
52 The “Background” provides some detail by reference to figure 1 (below) which is said to show a prior art arrangement for providing secure access:
53 Figure 1 is described in the specification to involve a user (401) making a request (402) by way of secure code such as a sequence of secret numbers or a biometric signal (such as a fingerprint or retinal pattern) directed to a code entry module (403) such as a keypad or a biometric sensor mounted on the external jamb of a secure door. The code entry module (403) conveys the request by sending a corresponding signal (404) to a controller (405) which is typically located in a remote or inaccessible place. The controller authenticates the security information by interrogating a database (407). If the user is authenticated and has the appropriate access privileges, the controller sends an access signal (408) to a device (409) in order to provide the desired access. (In this respect I note that the arrow on the line identified as 408 points in the wrong direction.) The device can be, for example, the locking mechanism of a secure door or an electronic lock on a personal computer which the user desires to access.
54 The specification on page 2, at lines 1 to 12, identifies problems with the prior art arrangement so described as follows:
Although the request 402 can be made secure, either by increasing the number of secret digits or by using a biometric system, the communication infrastructure in Fig. 1 is typically less secure. The infrastructure 400 is generally hardwired, with the code entry module 403 generally being mounted on the outside jamb of a secured door. In such a situation, the signal path 404 can be over a significant distance in order to reach the controller 405. The path 404 represents one weak point in the security system 400, providing an unauthorised person with relatively easy access to the information being transmitted between the code entry module 403 and the controller 405. Such an unauthorised person can, given this physical access, decipher the communicated information between the code entry module 403 and the controller 405. This captured information can be deciphered, replayed in order to gain the access which rightfully belongs to the user 401, or to enable modification for other subversive purposes.
55 The specification then refers to prior art systems as depicted in figure 1 using a communication protocol called “Wiegand”. The specification explains that it is a simple one-way data protocol that can be modified to ensure uniqueness of the protocol between different security companies, but it does not secure the information being sent between the code entry module (403) and the controller (405). It then goes on as follows (page 2 line 19 to page 3 line 3):
More advanced protocols such as RS 485 have been used in order to overcome the vulnerability of the Wiegand protocol over the long distance route 404. RS 485 is a duplex protocol offering encryption capabilities at both the transmitting and receiving ends, ie. the code entry module 403 and the controller 405 respectively in the present case. The length of the path 404 nonetheless provides an attack point for the unauthorised person.
Due to the cost and complexity of re-wiring buildings and facilities, security companies often make use of existing communication cabling when installing and/or upgraded security systems, thereby maintaining the vulnerability described above.
56 The specification then proceeds under a heading, “Summary”, to provide that it is an object of the invention to overcome or ameliorate one or more disadvantages of existing arrangements.
57 It then sets out a number of aspects of the invention, the language of which in the 168 patent correlates with the language of each of claims 1 to 5, 14, 16 and 17 and meets the definition of a “consistory clause”, being a statement of what the inventor asserts to be the invention of the type identified in Lockwood Security Products Pty Ltd v Doric Products Pty Ltd [2004] HCA 58; (2004) 217 CLR 274 (Lockwood No 1) at [10]. In section 3.2 below I have set out in full each of the asserted claims of the 168 patent, being claims 1, 2, 3, 5 and 6, although it is to be noted that in the “Summary”, the patentee asserts as its invention all of the aspects so described. The specification of the 293 patent adopts the same approach by recording a number of aspects of the invention asserted using language that conforms with each of claims 1, 14, 21, 27, 31, 33, 37, 39 and part of 41.
58 There follows a brief description of each of the 10 figures which are subsequently described in greater detail, aspects of which are referred to below.
59 Figure 2 is a diagram of an arrangement for providing secure access according to the invention:
60 The “Detailed Description” explains that a user (101) makes a request (102) to a code entry module (103), which includes a biometric sensor (121) such as a fingerprint sensor panel. The code entry module interrogates a user identity database (105) containing biometric signatures for authorised users and, if the user’s identity can be authenticated against the database, the code entry module sends a signal (106) to a controller/transmitter (107).
61 This checks the “current rolling code” in a database (113) which offers non-replay encrypted communication. The specification provides at page 10 lines 9 to 13:
The controller/transmitter 107 checks, as depicted by an arrow 112, the current rolling code in a database 113. The controller 107 then updates the code and sends the updated code, this being referred to as an access signal, as depicted by an arrow 108 to a controller 109. The rolling code protocol offers non-replay encrypted communication.
62 The controller (109) contains a receiver (118) that converts the access signal (108) into a form that the controller can use and provides it to the controller which tests the rolling code received against the most recent rolling code which has been stored in a database (115) and, if it is found to be legitimate, the controller (109) sends a command (110) to a controlled item (111). The “controlled item” (page 10 lines 18 to 20):
…can be a door locking mechanism on a secure door, or an electronic key circuit in a personal computer (PC) that is to be accessed by the user 101.
63 The specification explains that the arrangement in figure 2 has been described for the case where the secure code in the access signal is based on the rolling code, although this is merely one arrangement and other secure codes such as the Bluetooth protocol or the WiFi protocols can be used.
64 The specification explains the use of rolling codes as follows (page 11 lines 9 to 23):
Rolling codes provide a substantially non-replayable non-repeatable and encrypted radio frequency data communications scheme for secure messaging. These codes use inherently secure protocols and serial number ciphering techniques which in the present disclosure hide the clear text values required for authentication between the key fob (transmitter) sub-system-system 116 and the receiver/controller 118/109.
Rolling codes use a different code variant each time the transmission of the access signal 108 occurs. This is achieved by encrypting the data from the controller 107 with a mathematical algorithm, and ensuring that successive transmissions of the access signal 108 are modified using a code and/or a look-up table known to both the transmitter sub-system 116 and the receiver sub-system 117. Using this approach successive transmissions are modified, resulting in a non-repeatable data transfer, even if the information from the controller 107 remains the same. The modification of the code in the access signal 108 for each transmission significantly reduces the likelihood that an intruder can access the information replay the information to thereby gain entry at some later time.
65 It will be noted that in figure 2 a distinction is drawn between the transmitter sub-system and the receiver sub-system. The specification explains that the sub-system falling to the left-hand side, the transmitter sub-system, can be implemented in a number of different forms. On page 12, the specification provides that it can be incorporated into a small portable device carried by the user (called a ‘fob’ or ‘key fob’) or mounted on the outside jamb of a secured door. Typically, the transmitter sub-system communicates with the receiver sub-system via a wireless communication channel, as in the case of a portable fob. However, the communication may be via a wired medium.
66 The specification explains that there may be some flexibility in terms of whether functional parts are located in the transmitter sub-system or receiver sub-system (page 12 lines 13 to 21):
The biometric signature database 105 is shown in Fig. 2 to be part of the transmitter sub-system 116. However, in an alternative arrangement, the biometric signature database 105 can be located in the receiver sub-system 117, in which case the communication 104 between the code entry module 103 and the signature database 105 can also be performed over a secure wireless communication channel such as the one used by the access signal 108. In the event that the secure access system is being applied to providing secure access to a PC, then the secured PC can store the biometric signature of the authorised user in internal memory, and the PC can be integrated into the receiver sub-system 117 of Fig. 1 [sic, Fig. 2].
67 The specification states that where a remote fob is used, the combination of biometric verification and encrypted wireless communication between the transmitter sub-system and the receiver sub-system provides significant advantages over current systems. This is because a wired communication path is avoided and the fob incorporates the biometric authentication arrangement, such that only one biometric signature is stored in the fob which reduces the requirements on the central database (115). Once the fob authenticates the user through biometric signature (e.g. fingerprint) verification, the rolling code in the access signal is transmitted to the controller (109) in the receiver sub-system for authorisation of the user.
68 On page 13, the specification provides that in addition to authenticating the user, the biometric sensor (121) in conjunction with the controller (107) can check other access privileges of the user contained in the database (105). An example is given whereby Tom Smith can be authenticated using a thumb press on the biometric sensor panel. After his biometric identity is authenticated, the transmitter sub-system (116) can check if he is allowed to use the particular door secured by the device (that is, controlled item (111)) on weekends, thereby screening him for more than simply his identity but also his entitlement to more comprehensive access privileges.
69 On page 14, the specification says that the transmitter sub-system (116) is preferably fabricated in the form of a single integrated circuit (or IC) to reduce the possibility of an unauthorised person bypassing the biometric sensor (121) in the code entry module and forcing the controller (107) to emit the rolling code access signal (108).
70 Figure 3 depicts the operation of the transmitter sub-system (116), providing a sequence of steps in the form of a flow chart from the point of receipt of a biometric signal to the sending of an access signal:
71 The specification further explains the method of operation of the transmitter sub-system which it also described as a “remote control module”. It provides for the initial steps at page 14 lines 6 to 15:
The method 200 commences with a testing step 201 in which the biometric sensor 121 in the code entry module 103 checks whether a biometric signal 102 is being received. If this is not the case, then the method 200 is directed in accordance with an NO arrow back to the step 201 in a loop. If, on the other hand, the biometric signal 102 has been received, then the method 200 is directed in accordance with a with a YES arrow to a step 202. The step 202 compares the received biometric signal 102 with information in the biometric signature database 105 in order to ensure that the biometric signal received 102 is that of the rightful user 101 of the sub-system 116.
A subsequent testing step 203 checks whether the comparison in the step 202 yields the desired authentication.
72 The specification then goes on to address biometric authentication and the provision of an “accessibility attribute”, which is of some relevance to the issues between the parties, at page 14 line 15 to page 15 line 1:
If the biometric signature matching is authenticated, then the process 200 is directed in accordance with a YES arrow to a step 204. The authentication of the biometric signature matching produces an accessibility attribute for the biometric signal 102 in question. The accessibility attribute establishes whether and under which conditions access to the controlled item 111 should be granted to a user. Thus, for example, the accessibility attribute may comprise one or more of an access attribute (granting unconditional access), a duress attribute (granting access but with activation of an alert tone to advise authorities of the duress situation), an alert attribute (sounding a chime indicating that an unauthorised, but not necessarily hostile, person is seeking access) and a telemetry attribute, which represents a communication channel for communicating state information for the transmitter sub-system to the receiver sub-system such as a “low battery” condition.
73 The specification then refers, at page 15 lines 1 to 13, to a further facility available to the user in this embodiment by reference to a “control option”:
The step 204 enables the user 101 to select a control option by providing one or more additional signals (not shown) to the controller 107. Thus for example the control option could enable the user 101 to access one of a number of secure doors after his or her identity has been authenticated in the step 203. In the subsequent step 205 the controller 107 sends the appropriate access signal 108 to the controller 109. The process 200 is then directed in accordance with an arrow 206 back to the step 201.
Thus for example the sub-system 116 can be provided with a single biometric sensor 121 in the code entry module 103 which enables the user 101 to select one of four door entry control signals by means of separate buttons on the controller 107 (not shown). This would enable the user 101, after authentication by the biometric sensor 121 in the code entry module 103 and the controller 107 to obtain access to any one of the aforementioned for [sic, four] secure doors.
74 Figure 4 (not reproduced) depicts the operation of the receiver sub-system (also referred to as the “control sub-system”) in the form of a flow chart. Various steps are described including where the controller (109) compares the rolling code received via the access signal (108) with a reference code in the database (115). This is described in the expert evidence as a decryption step.
75 Figure 5 (not reproduced) shows incorporation of a protocol converter into the arrangement of figure 2.
76 Figure 6 (not reproduced) depicts, in the form of a flow chart, another process of operation of the remote access system. The flowchart identifies a mechanism for populating the user ID database (105) if it is empty, as would be the case if the code entry module is new and has never been used, or if the user has erased all the information in the database (105). If the database is empty, the flowchart provides a direction to figure 8, to which reference is made below.
77 The specification, at page 18 lines 12 to 21, provides:
If the database 105 is empty, then the process 700 is directed by an arrow 703 to 706 in Fig. 8, which depicts a process 800 dealing with the enrolment or the administration function for loading relevant signatures into the database 105. If on the other hand the database 105 is not empty, the process 700 is directed to a step 704 that determines if the biometric signal that has been received is an administrator’s biometric signal.
The disclosed remote entry system can accommodate at least three classes of user, namely administrators, (ordinary) users, and duress users. The administrators have the ability to amend data stored, for example, in the database 105, while the ordinary users do not have this capability.
78 The specification goes on to describe one means by which the “administrator” is identified, at page 18 lines 21 to 25:
The first user of the code entry module 103, whether this is the user who purchases the module, or the user who programs the module 103 after all data has been erased from the database 105, is automatically categorised as an administrator. This first administrator can direct the system 100 to either accept further administrators, or alternately to only accept further ordinary users.
79 The specification explains that although the description refers to “users”, in fact it is “fingers”, which are the operative entities in system operation when the biometric sensor is a fingerprint sensor. A single user can enrol two or more of their fingers as separate administrators or ordinary users of the system by storing corresponding fingerprints for corresponding fingers in the database (105) via the enrolment process described by reference to figure 8.
80 The specification describes how the first administrator can provide control information to the code entry module by providing a succession of finger presses to the sensor (121). If those presses are of the appropriate duration and quantity, and are input within a predetermined time, they are accepted by the controller (107) as control information.
81 Figure 7 (reproduced in section 4.4.2 below) shows the process by which a biometric signal (102) is processed to provide access to the controlled item (111). The specification describes that the system uses four types of “user defined bits” that can be inserted into the access signal (108) to effect desired control functions in the receiver sub-system, namely to indicate: (a) that the user belongs to the duress category; (b) a “battery low” condition or other system state for the code entry module; (c) that the biometric signal represents a legitimate user so that access to the controlled item can be granted; or (d) that the biometric signal is unknown whereupon the controller in the receiver sub-system sounds an alert tone.
82 Figures 8 and 9 (not reproduced) show processes for implementing various enrolment procedures.
83 Figure 10 provides a schematic block diagram of the system in figure 2 in which the secure access methods are preferably practiced using a computer system arrangement. Shown in figure 10 are the processes of figures 3 to 4 and 6 to 9, which may be implemented as software, such as application program modules executing within that computer system:
84 The method steps for providing secure access in this embodiment are said to be effected by instructions in the software carried out under direction of the processor modules (107) and (109) which are in the transmitter sub-system and the receiver sub-system, respectively. The instructions may be formed as one or more code modules, each performing one or more tasks. The specification says at page 26 lines 3 to 13:
Fig. 10 is a schematic block diagram of the system in Fig. 2. The disclosed secure access methods are preferably practiced using a computer system arrangement 100’, such as that shown in Fig. 10 wherein the processes of Figs. 3-4 and 6-9 may be implemented as software, such as application program modules executing within the computer system 100’. In particular, the method steps for providing secure access are effected by instructions in the software that are carried out under direction of the respective processor modules 107 and 109 in the transmitter and receiver sub-systems 116 and 117. The instructions may be formed as one or more code modules, each for performing one or more particular tasks. The software may also be divided into two separate parts, in which a first part performs the provision of secure access methods and a second part manages a user interface between the first part and the user.
85 The specification goes on at page 26 line 21 to page 27 line 9:
The following description is directed primarily to the transmitter sub-system 116, however the description applies in general to the operation of the receiver sub-system 117. The computer system 100’ is formed, having regard to the transmitter sub-system 116, by the controller module 107, input devices such as the bio sensor 121, output devices including the LED display 122 and the audio device 124. A communication interface/transceiver 1008 is used by the controller module 107 for communicating to and from a communications network 1020. Although Fig. 2 shows the transmitter sub-system 116 communicating with the receiver sub-system 117 using a direct wireless link for the access signal 108, this link used by the access signal 108 can be effected over the network 1020 forming a tandem link comprising 108-1020-108’. The aforementioned communications capability can be used to effect communications between the transmitter sub-system 116 and the receiver sub-system 117 either directly or via the internet and other network systems such as a Local Area Network (LAN) or a Wide Area Network (WAN).
86 The body of the specification concludes with a heading, “Industrial Applicability”, that includes a statement that the embodiments described are illustrative rather than restrictive and provides at page 28 lines 17 to 20 that the system (100) can be used to provide access to controlled devices generally:
The system 100 can also be used to provide authorised access to lighting systems, building control devices, exterior or remote devices such as air compressors and so on. The concept of “secure access” is thus extendible beyond mere access to restricted physical areas.
3.2 Asserted claims of the 168 patent
87 Set out below are the claims asserted by CPC in its infringement case, with integer numbers added for convenience:
1. (1) A system for providing secure access to a controlled item, the system comprising: (2) a transmitter subsystem for enrolling biometric signatures into a database and for providing an accessibility attribute if a legitimate biometric signal is received; and (3) a receiver sub-system for providing access to the controlled item dependent upon said accessibility attribute.
2. (1) A transmitter sub-system adapted for operation in a system for providing secure access to a controlled item, (2) the system further including a receiver sub-system for providing access to the controlled item dependent upon an accessibility attribute received from the transmitter sub-system; (3) wherein the transmitter subsystem comprises: (4) means for enrolling biometric signatures into a database; and (5) means for providing the accessibility attribute if a legitimate biometric signal is received.
3. (1) A method of enrolling, by a transmitter sub-system, biometric signatures into a database of biometric signatures (2) in a system for providing secure access to a controlled item, (3) the system comprising the transmitter sub-system and (4) a receiver sub-system (5) for providing access to the controlled item (6) dependent upon an accessibility attribute received from the transmitter sub-system; said method comprising the steps of: (7) storing a biometric signal received by the transmitter sub-system in the database as an administrator signature; and (8) enabling administrative processing of information stored in the database if a biometric signal matching the stored administrator signature is received by the transmitter.
5. (1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute; (6) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; and (7) means for enrolling biometric signatures into the database; (8) and a receiver sub-system comprising; (9) means for receiving the transmitted secure access signal; and (10) means for providing access to the controlled item dependent upon said information.
6. A system according to claim 5, wherein the means for enrolling biometric signatures comprises: (11) means for determining if the database of biometric signatures is empty; and (12) means for storing a biometric signal received by the biometric sensor in the database as an administrator signature if the database of biometric signatures is empty.
3.3 Asserted claims of the 293 patent
88 The asserted claims of the 293 patent are set out below, with integer numbers added for convenience:
1. (1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction; (9) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (10) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; (11) said system further comprising: a receiver sub-system comprising; (12) means for receiving the transmitted secure access signal; and (13) means for providing conditional access to the controlled item dependent upon said information.
27. (1) A method for providing secure access to a controlled item, the method comprising the steps of: (2) enrolling, by a transmitter sub-system, relevant signatures into a database using a biometric sensor, by receiving a series of entries of the biometric signal, (3) said series being characterised according to at least one of the number of said entries and a duration of each said entry, (4) mapping said series into an instruction, and (5) enrolling relevant signatures into the database according to the instruction; (6) receiving, by the transmitter sub-system, a biometric signal; (7) matching, by the transmitter sub-system, the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; (8) emitting, by the transmitter sub-system, a secure access signal conveying information dependent upon said accessibility attribute; and (9) providing conditional access to the controlled item dependent upon said information.
29. A method according to claim 27, (10) wherein the database of biometric signatures comprises signatures in at least one of a system administrator class, a system user class, and a duress class.
37. (1) An apparatus for providing secure access to a controlled item, said apparatus comprising: (2) a transmitter sub-system comprising: (3) a biometric sensor for receiving a biometric signal; (4) means for enrolling relevant signatures into a database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (5) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (6) means for mapping said series into an instruction; and (7) means for enrolling relevant signatures into the database according to the instruction; (8) the transmitter sub-system further comprising: (9) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (10) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; and (11) wherein conditional access is provided to the controlled item dependent upon said information.
39. (1) An apparatus, in a transmitter sub-system, (2) for enrolling relevant signatures into a database of biometric signatures in a system for providing secure access to a controlled item, the system comprising: (3) said database of biometric signatures; (4) the transmitter subsystem, comprising: (5) a biometric sensor for receiving a biometric signal; (6) means for enrolling relevant signatures into the database using the biometric sensor; (7) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (8) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; the system further comprising: (9) a receiver sub-system comprising; (10) means for receiving the transmitted secure access signal; and (11) means for providing conditional access to the controlled item dependent upon information in said secure access signal; (12) said apparatus comprising: (13) means for receiving a series of entries of the biometric signal; (14) means for determining at least one of the number of said entries and a duration of each said entry; (15) means for mapping said series into an instruction; and (16) means for enrolling relevant signatures into the database according to the instruction.
41. (1) A method of enrolling a biometric signature into a database of biometric signatures in a system for providing secure access to a controlled item, the system comprising: (2) said database of biometric signatures; (3) a transmitter subsystem for receiving a biometric signal, the transmitter subsystem comprising: (4) a biometric sensor; (5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (7) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (8) means for mapping said series into an instruction; and (9) means for enrolling relevant signatures into the database according to the instruction; (10) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (11) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; the system further comprising: (12) a receiver sub-system comprising: (13) means for receiving the transmitted secure access signal; and (14) means for providing conditional access to the controlled item dependent upon information in said secure access signal; said method comprising the steps of: (15) receiving a biometric signal; and (16) enrolling the relevant signatures into the database using the biometric sensor as administrator if the database of biometric signatures is empty.
3.4 The field of the invention
89 The field of the invention is described in the patents to relate to secure access systems and particularly to systems using wireless transmission of security code information. The prior art problems described by reference to figure 1 identify a particular problem with “signal path 404” which represents a weak point in the security system, providing an unauthorised person with easy access to the information being transmitted between the code entry module and the controller, which can be deciphered and misused. The specification asserts that communication protocols do not secure the information being so sent – I note that there is some criticism in the expert evidence of the description of the protocols, which is presently immaterial – and that the length of the path, which goes from the code entry module to the controller, “provides an attack point for the unauthorised person”.
90 The invention is then described by reference to various aspects for the provision of secure access to a “controlled item” which broadly involves a “transmitter sub-system” having various characteristics and, often but not uniformly, a “receiver sub-system”.
91 The meaning of each of these terms is the subject of dispute and is considered below. However, it is apparent that an important aspect of the invention described is that the determination of whether and under which conditions access should be granted is within the transmitter sub-system prior to communication with a receiver sub-system which then grants the requisite access. In broad terms the field of the invention is directed to providing secure access to a controlled item utilising biometrics, cryptography, microelectronics and embedded systems.
3.5 The skilled addressee
92 CPC contends that the skilled addressee is an engineer or “team” of engineers with expertise in biometric secure access systems, cryptography and signal processing. Apple contends that the patents are addressed to the manner in which a biometric secure access system may be designed and as such the person skilled in the art would be an engineer responsible for integrating all elements of an engineered product, with expertise in microelectronics and embedded systems, including designing circuits and microchips and writing their controlling software with several years’ practical experience working on biometric secure access systems.
93 Persons skilled in the art, or skilled addressees of the patents, will be those likely to have a practical interest in the subject matter of the invention. The notional skilled reader may be an individual or a team, whose combined skills would normally be employed in the art in interpreting and carrying into effect instructions such as those which are contained in the document to be construed. Put another way, the skilled addressee is a notional person who may have an interest in using the products or methods of the invention, making the products of the invention, or making products used to carry out the methods of the invention either alone or in collaboration with others having such an interest; Catnic Components v Hill & Smith Ltd [1982] RPC 183 at 242 (Diplock LJ); General Tire & Rubber Co v Firestone Tyre & Rubber Co Ltd [1971] 7 WLUK 130; [1972] RPC 457 at 485 (Sachs LJ); Aristocrat Technologies Australia Pty Limited v Konami Australia Pty Limited [2015] FCA 735; (2015) 114 IPR 28 at [26] (Nicholas J); Pharmacia LLC v Juno Pharmaceuticals Pty Ltd [2022] FCA 92; (2022) 165 IPR 200 at [111] (Burley J); Hanwha Solutions Corporation v REC Solar Pte Ltd [2023] FCA 1017; (2023) 180 IPR 315 at [86] (Burley J).
94 In this context it is important to recall that the notional skilled reader, although sometimes characterised as a “team”, is an artificial construct through which the Court is able to construe the patent and, where appropriate, consider whether or not the invention claimed lacks an inventive step. Although skills drawn from different areas of expertise may be relevant, the person skilled in the art thinks with one mind, speaks with one voice, and draws, when and to the extent necessary, on the disparate knowledge and skills of all of the members of the “team” – it is one indivisible whole; Novartis AG v Pharmacor Pty Limited (No 3) [2024] FCA 1307 at [149] (Yates J).
95 In the present case, I consider that each of Dr Dunstone, Associate Professor Boztas and Professor Smith have relevant expertise to assist the Court in formulating the views of the person skilled in the art, noting that the notional person should not be understood to be a mere avatar of any of these witnesses: AstraZeneca AB v Apotex Pty Ltd [2015] HCA 30; (2015) 257 CLR 356 at [23] (French CJ).
96 Each party was critical of the expert evidence given by the other. In my view the experts did their best to assist the Court in explaining the technology and their views. To some extent their oral testimony was buffeted by the winds of the forensic contest between the parties, particularly in interpreting the patents. However, except where identified specifically below, I found the evidence of the experts to be of assistance in considering the issues. In this context, as the authorities note, it is the task of the Court to construe terms used in the patent and the evidence of the expert cannot supplant that task: Commissioner of Patents v Rokt Pte Ltd [2020] FCAFC 86 (2020) 277 FCR 267 at [73] (Rares, Nicholas and Burley JJ).
4. CLAIM CONSTRUCTION
4.1 Introduction
97 The closing submissions of the parties indicate that construction issues arise in relation to the following terms, integers or groups of integers:
(a) “controlled item” (all asserted claims);
(b) “transmitter sub-system” and “receiver sub-system” (all asserted claims, although claims 27, 29 and 37 of the 293 patent do not refer to a receiver sub-system);
(c) “accessibility attribute” (all asserted claims);
(d) “secure access signal” (claims 5 and 6 of the 168 patent and all asserted claims of the 293 patent);
(e) providing conditional access to the controlled item dependent upon said information / information in said secure access signal (all asserted claims of the 293 patent);
(f) “administrator signature” (claims 3 and 6 of the168 patent) and, relatedly “administrator class” and “administrator” (claims 29 and 41 of the 293 patent); and
(g) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry, means for mapping said series into an instruction and means for enrolling relevant signatures into the database according to the instruction (all asserted claims of the 293 patent). I refer to his below as the series feature.
4.2 Relevant law
98 There is no dispute as to the relevant principles of claim construction. One construes the claims in the context of the specification as a whole, through the eyes of the person skilled in the art, having regard to the common general knowledge as it existed at the priority date of the claims. Although many cases have referred to the principles applicable to claim construction, one convenient authority that summarises key aspects of those principles is Jupiters Ltd v Neurizon Pty Ltd [2005] FCAFC 90; (2005) 222 ALR 155 where Hill, Finn and Gyles JJ said at [67]:
(i) the proper construction of a specification is a matter of law: Décor Corp Pty Ltd v Dart Industries Inc (1988) 13 IPR 385 at 400;
(ii) a patent specification should be given a purposive, not a purely literal, construction: Flexible Steel Lacing Company v Beltreco Ltd (2000) 49 IPR 331 at [81]; and it is not to be read in the abstract but is to be construed in the light of the common general knowledge and the art before the priority date: Kimberley-Clark Australia Pty Ltd v Arico Trading International Pty Ltd (2001) 207 CLR 1 at [24];
(iii) the words used in a specification are to be given the meaning which the normal person skilled in the art would attach to them, having regard to his or her own general knowledge and to what is disclosed in the body of the specification: Décor Corp Pty Ltd at 391;
(iv) while the claims are to be construed in the context of the specification as a whole, it is not legitimate to narrow or expand the boundaries of monopoly as fixed by the words of a claim by adding to those words glosses drawn from other parts of the specification, although terms in the claim which are unclear may be defined by reference to the body of the specification: Kimberley-Clark v Arico at [15]; Welch Perrin & Co Pty Ltd v Worrel (1961) 106 CLR 588 at 610; Interlego AG v Toltoys Pty Ltd (1973) 130 CLR 461 at 478; the body of a specification cannot be used to change a clear claim for one subject matter into a claim for another and different subject matter: Electric & Musical Industries Ltd v Lissen Ltd [1938] 56 RPC 23 at 39;
(v) experts can give evidence on the meaning which those skilled in the art would give to technical or scientific terms and phrases and on unusual or special meanings to be given by skilled addressees to words which might otherwise bear their ordinary meaning: Sartas No 1 Pty Ltd v Koukourou & Partners Pty Ltd (1994) 30 IPR 479 at 485-486; the Court is to place itself in the position of some person acquainted with the surrounding circumstances as to the state of the art and manufacture at the time (Kimberley-Clark v Arico at [24]); and
(vi) it is for the Court, not for any witness however expert, to construe the specification; Sartas No 1 Pty Ltd, at 485-486.
4.3 Controlled item
99 The term “controlled item” is present in all of the asserted claims. However, it is convenient to consider its meaning primarily by reference to claim 1 of the 168 patent, neither party suggesting that the term is to be understood as having a different meaning in the other claims.
100 For convenience, claim 1 of the 168 patent is repeated below:
(1) A system for providing secure access to a controlled item, the system comprising: (2) a transmitter subsystem for enrolling biometric signatures into a database and for providing an accessibility attribute if a legitimate biometric signal is received; and (3) a receiver sub-system for providing access to the controlled item dependent upon said accessibility attribute.
(Emphasis added)
4.3.1 The submissions
101 CPC submits that the term “controlled item” refers to an item which the user can seek to access. It may be a physical item (such as a door) or a logical item such as files, systems and programs stored on a computer. It is not limited to a single discrete item to be accessed but can include multiple sub-items within a controlled item which may require additional authentication to access. It submits, as an example, that the patents describe accessing any one of multiple doors or accessing a personal computer which could, in turn, have varying sub-components, themselves requiring further authentication for access.
102 Apple disputes that a “controlled item” may include items which require additional authentication to obtain access. It submits that to construe “controlled item”, it is necessary to have regard to its relationship to the accessibility attribute and the receiver sub-system. An accessibility attribute establishes whether and under which conditions access to the controlled item is to be granted. The receiver sub-system provides secure access to the controlled item dependent on the accessibility attribute. Accordingly, a controlled item is the item to which the accessibility attribute establishes access and to which the receiver sub-system, as part of the claimed system provides ‘secure access’. It cannot be an item that is not controlled by the system or an item to which the receiver sub-system cannot provide secure access dependent on the accessibility attribute. Thus, the patents provide as examples of a controlled item a “door lock mechanism” or an “electronic key circuit” but not the whole room or building, nor the whole computer.
4.3.2 Consideration
103 It is apparent that the system of integer (1) is to be understood by reference to the particular details provided in integers (2) and (3). The system “for providing secure access” being a system that is suitable for the purpose of providing such access to the controlled item.
104 “Secure access”, as that term was understood in the art, concerns provision of authorised access to a person depending on the system being satisfied as to who they are (e.g. a biometric identifier), what they have (e.g. a swipe card), or what they know (e.g. a password). By integer (2), it is apparent that access to the controlled item is dependent on the first of these options, because the system must include a transmitter sub-system for enrolling biometric signatures into a database and for providing an accessibility attribute if a legitimate biometric signal is received. By integer (3) a receiver sub-system must be able to provide access to the controlled item dependent upon the accessibility attribute. Accordingly, the question of “who they are” is answered by reference to the biometric signature provided.
105 The parties disagree on the breadth of the how “controlled item” is to be understood. It is not a defined term nor a term of art. CPC contends that it is to be understood broadly as meaning any item to which access is granted upon the provision of an accessibility attribute and gives the example of a physical facility; whereby access to the facility permits use of certain machines located therein, but not others which may require additional steps to access once inside. Notwithstanding the limited functionality that may be granted by the access, the controlled item remains the whole of the physical facility.
106 In my view, the internal logic and language used in claim 1 suggests that the “controlled item” is that to which the system defined by integers (2) and (3) may (or may not) grant access, depending on whether conditions (2) and (3) are satisfied. Integer (1) is for providing secure access to a controlled item, indicating that the outcome of the process described in integers (2) and (3) should be either a grant or a refusal of access to that item. To give a physical example, take a building with a red exterior door leading into a room with a blue interior door, each of which has a lock with a biometric keypad. John approaches the red door and presses his thumb on the biometric sensor, the transmitter sub-system receives a legitimate biometric signal and produces an accessibility attribute (integer 2). The receiver sub-system then provides access upon receipt of the accessibility attribute (integer 3). In that scenario the controlled item is the lock on the secure red door. The controlled item remains the lock, even if John is refused access to the door. However, if there is another door, such as the secure blue interior door, then the secure blue door is not the relevant controlled item. In the case of the secure blue door, it may be a different controlled item.
107 The description in the body of the specification, although not determinative, tends to support this construction. The passage on page 10 lines 18 to 20 provides:
The controlled item 111 can be a door locking mechanism on a secure door, or an electronic key circuit in a personal computer (PC) that is to be accessed by the user 101.
108 In the first of these examples the controlled item is not a room, but a door locking mechanism. In the second, the controlled item is a key circuit, not a personal computer. The conclusion that the controlled item is the single locking mechanism is supported by the language of the claims, which in each case refer to obtaining access to “a controlled item”.
109 The specification, by reference to figure 3, explains that the method of operation of the transmitter sub-system commences with a testing step (201) in which the biometric sensor (121) in the code entry module (103) (shown in figure 2) checks whether a biometric signal is being received. If not, the method (200) is directed back to the testing step (as indicated by the “no” arrow). If a biometric signal is received, then the method is directed toward step 202 (as indicated by the “yes” arrow) whereby the received biometric signal is compared with information in the biometric signature database (105) to ensure that the biometric signal received is that of the rightful user of the transmitter sub-system (116). A subsequent testing step (203) checks whether the comparison in step 202 yields the desired authentication. The specification, at page 14 line 15 to page 15 line 1, then states:
If the biometric signature matching is authenticated, then the process 200 is directed in accordance with a YES arrow to step 204. The authentication of the biometric signature matching produces an accessibility attribute for the biometric signal 102 in question. The accessibility attribute establishes whether and under which conditions access to the controlled item 111 should be granted to a user. Thus, for example, the accessibility attribute may comprise one or more of an accessibility attribute (granting unconditional access), a duress attribute (granting access but with activation of an alert tone to advise authorities of the duress situation), an alert attribute (sounding a chime indicating that an unauthorised, but not necessarily hostile, person is seeking access) and a telemetry attribute, which represents a communication channel for communicating state information for the transmitter sub-system to the receiver sub-system such as a “low battery” condition.
(Emphasis added)
110 The passage on page 15 of the specification to which CPC refers in support of its proposition provides an example of a “control option” being exercised by a user that enables access to one of a number of secure doors after an authentication step has taken place. In this example, no reference is made to a “controlled item”. I do not consider that it provides support for the construction of the term “controlled item” advanced by CPC.
111 Accordingly, I disagree with the submission advanced by CPC that the “controlled item” may be more than a single discrete item to be accessed and can include multiple sub-items within, each requiring additional authentication to access.
4.4 Accessibility attribute
112 Whilst the parties’ submissions characterise the dispute between them as concerning the words “accessibility attribute”, in fact the experts and the parties agree that the meaning of “accessibility attribute” is explained on page 14 lines 18 to 19 as follows:
The accessibility attribute establishes whether and under which conditions access to the controlled item 111 should be granted to a user.
113 The dispute concerns how the words “accessibility attribute” should be understood in the context of the claims where those words appear.
4.4.1 The submissions
114 CPC submits that the definition in the specification is consistent with an understanding of the words in their ordinary meaning; “attribute” meaning a quality, and an “accessibility attribute” being a quality of access. The detail as to whether and under which conditions access to the controlled item is to be granted must be communicated through the “positive match result” or the “message” sent. CPC submits that the words “accessibility attribute” do not provide any limitation as to the means by which the transmitter sub-system provides or outputs the accessibility attribute. It is sufficient that there is a means for “providing” or “outputting” something which, in the context in which this occurs, establishes whether and under which conditions access should be granted. CPC submits that where the user seeking access identifies the specific condition of access sought, the authentication (being a biometric match) itself may constitute the provision or output of the accessibility attribute, because it establishes whether and under which conditions access should be granted in response to the specific access request. This, CPC submits, is consistent with the disclosures in the specification at page 14 line 18 to page 15 line 13. CPC further submits that the claims do not impose any requirement that the accessibility attribute only concern conditions that specifically arise from the matching outcome, as opposed to “preconditions”, nor must the conditions be specified by the particular biometric signature. The claims only require for an accessibility attribute to be “provided” or “output” if a legitimate biometric signal is received. This, however, should not be interpreted as meaning that the claims require the biometric match to “produce” the accessibility attribute. Furthermore, the accessibility attribute must be output or provided within the transmitter sub-system, meaning that it is the transmitter sub-system that determines the nature of the access to be granted, and no further verification or authentication step should occur in the receiver sub-system.
115 Apple disputes that a positive biometric match will be sufficient to fall within the meaning of accessibility attribute or that the accessibility attribute need not itself contain the conditions of access. It submits that there is a distinction drawn between access privileges and an accessibility attribute.
116 Apple submits that an accessibility attribute must establish conditions in response to matching which cause the receiver sub-system to respond in different ways. The accessibility attribute must: (a) be produced by the authentication of biometric signature matching; and (b) establish whether and under which conditions access to the controlled item should be granted. Claim 1 of the 168 patent makes clear that a precondition to the provision of an accessibility attribute is the receipt of a legitimate biometric signal. The experts considered the term “legitimate” to mean a biometric match or a close enough match to a biometric stored in the database. Accordingly, within the structure of claim 1, an accessibility attribute is something that is different from the mere identification of a match, the system within claim 1 being to provide an accessibility attribute in response to a biometric signal that is a match of a stored template. This, it submits, is confirmed by the language of the specification, one example being the description of figure 7 and the experts’ evidence in relation to that figure. Apple submits that a system that merely involves determining whether preconditions to access have been met and either grants or refuses access does not involve the provision of an accessibility attribute; the accessibility attribute must establish conditions in response to matching which cause the receiver sub-system to respond in different ways. In this context it refers to the conjunction “and” in the definition of accessibility attribute in the specification.
4.4.2 Consideration
117 Each of the asserted claims includes an accessibility attribute.
118 In claim 1 of the 168 patent, the transmitter sub-system of integer (2) must provide “an accessibility attribute if a legitimate biometric signal is received” and the receiver sub-system of integer (3) must provide access to the controlled item “dependent upon said accessibility attribute”.
119 Claim 2 of the 168 patent also requires the transmitter sub-system to include means for providing an accessibility attribute “if a legitimate biometric signal is received” but additionally requires a receiver sub-system for providing access to the controlled item “dependent upon an accessibility attribute received from the transmitter sub-system”. Claim 3 of the 168 patent contains no express reference to receipt of a legitimate biometric signal but contains a similar requirement in respect of a receiver sub-system.
120 The remainder of the asserted claims (claims 5 and 6 of the 168 patent and claims 1, 27, 29, 37, 39 and 41 of the 293 patent) require the transmitter sub-system to have means: (a) for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated (noting that the authentication requirement is also not present in claims 5 and 6 of the 168 patent); and (b) for emitting a secure access signal conveying information “dependent upon” the accessibility attribute. Those claims then require that conditional access be provided (by the receiver sub-system in claims 5 and 6 of the 168 patent and claims 1, 39 and 41 of the 293 patent) “dependent upon” information in the secure access signal, which is information derived from the accessibility attribute.
121 It is apparent from the claim language that the step of matching a biometric signature and conveying a match will not of itself amount to an accessibility attribute. Taking claim 1 of the 168 patent as an example, an accessibility attribute is produced if a legitimate biometric signal is received. The balance of the asserted claims generally also require an accessibility attribute to be provided only in response to the receipt of a “legitimate” or “authenticated” biometric signal, which the experts agreed, and I accept, equated to a biometric match (or close enough match) to a biometric held in the database.
122 The transmitter sub-system must then “provide” or “output” an accessibility attribute that meets the definition in the specification of conveying whether and under which conditions access to the controlled item should be granted to a user. This tells against a construction whereby the confirmation of a biometric match itself may be considered to amount to an accessibility attribute.
123 In my view, this is supported by the language of the specification. The steps described by reference to figure 3 at page 14 lines 15 to 19 are set out in context in section 3.1 above, but warrant repetition:
If the biometric signature matching is authenticated, then the process 200 is directed in accordance with a YES arrow to a step 204. The authentication of the biometric signature matching produces an accessibility attribute for the biometric signal 102 in question. The accessibility attribute establishes whether and under which conditions access to the controlled item 111 should be granted to a user.
(Emphasis added)
124 As the experts agreed, the patents explain that successful biometric authentication “produces an accessibility attribute…As per the specification…this accessibility attribute can be one or more of: an access attribute granting unconditional access, a duress attribute, an alert attribute and a telemetry attribute” (JER1 at [10]). Dr Dunstone and Associate Professor Boztas explain in their evidence that an “attribute” is a term used in the field to signal the presence or absence of a condition. Dr Dunstone further explains that attributes are frequently used in sets with mapping that interprets the meaning of the transmitted attributes. A single attribute may be enabled or disabled, with the presence of an attribute requiring that there be at least two possible conditions – that is, attribute present or attribute not present.
125 The claims require the biometric signal received to be compared (matched) against signatures stored in the database. If the outcome of that matching process is that a legitimate biometric signal has been received, then the receiver sub-system “provides” an accessibility attribute.
126 In my view, the “attribute” will be an output, separate to the match, that meets the definition of “accessibility attribute” namely, that it establishes whether and under which conditions access to the controlled item is granted. The accessibility attribute provides a different function to the communication of a biometric match and will enable the receiver sub-system to respond in different ways to different legitimate biometric signals, depending on the nature of the attribute produced. However, the claims impose no limitation on the particular form that the accessibility attribute takes, provided that it meets the definition.
127 Figure 7 (below) shows one embodiment of an access process by which a biometric signal (102) (as depicted in figure 2) is processed in order to provide access to the controlled item (111), or to take other action.
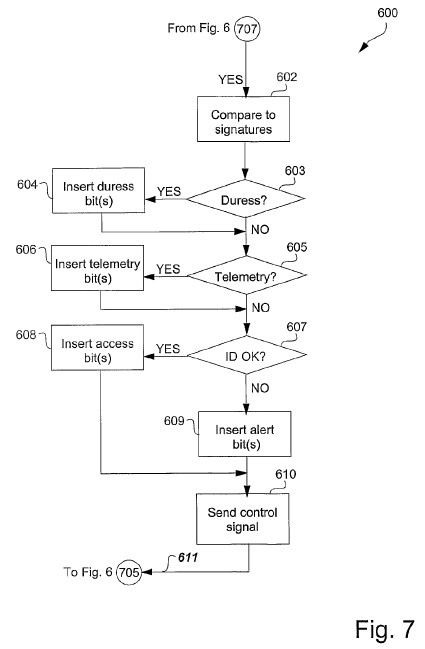
128 The specification says on page 20 line 21 to page 21 line 14:
Entering the process at 707 from Fig. 6, the process 600 proceeds to a step 602 that compares the received biometric signature to signatures stored in the database 105. A following step 603 determines if the received signal falls into the “duress” category. Signatures in this category indicate that the user 101 is in a coercive situation where, for example, an armed criminal is forcing the user 101 to access the secure facility (such as a bank door). If the step 603 determines that the signature is in the duress class, then a following step 604 prepares a “duress” bit for incorporation into the code access signal 108. The aforementioned duress bit is an access attribute of the biometric signal 102. Thereafter the process 600 proceeds to a step 605.
Modules used in the code entry module for producing the rolling code enable a number of user defined bits to be inserted into the access signal 108, and these bits can be used to effect desired control functions in the receiver sub-system 117. The disclosed system 100 utilises four such user bits, namely (a) to indicate that the user belongs to the duress category, (b) to indicate a “battery low” condition, or other desired system state or “telemetry” variable, for the code entry module 103, (c) to indicate that the biometric signal represents a legitimate user in which case the secure access to the controlled item 111 is to be granted, or (d) to indicate that the biometric signal is unknown, in which case the controller 109 in the receiver sub-system 117 sounds an alert tone using a bell (not shown) or the like.
(Emphasis added)
129 The process described here gives an example of how the process may operate, including the insertion of duress, telemetry, access and alert bits into the access signal (108) in steps 603 to 609, respectively. It describes the biometric authentication process undertaken to establish whether access is granted and the conditions upon which it is granted, represented by the presence or absence of these bits.
130 Although in some of his earlier oral evidence, Associate Professor Boztas appeared to suggest that a simple match would be sufficient to classify as an accessibility attribute, he and Dr Dunstone later agreed that the definition of an accessibility attribute on page 14 of the specification makes clear that such an attribute is produced after the authentication or matching process and is different to biometric signature matching in that it must establish two things, whether access should be granted and under which conditions access should be granted. Later, the experts explained:
MR LANG: And then, Associate Professor Boztas, would you go to claim 1 of the 168 patent which is page 29 at the top of that patent, court book volume 2, tab 24, court book page 1069.
ASSOC PROF BOZTAS: Yes.
MR LANG: And, at line 6, “for providing an Accessibility Attribute if a legitimate biometric signal is received”; is that another way of saying biometric authentication produces the Accessibility Attribute?
ASSOC PROF BOZTAS: A “legitimate biometric signal” means that the biometric is matched. Yes.
MR LANG: Thank you. And, Dr Dunstone, do you have any comments on that?
ASSOC PROF BOZTAS [sic DR DUNSTONE]: No, I agree with that position.
131 In his oral evidence Associate Professor Boztas described his understanding of an accessibility attribute by reference to Exhibit D (set out below), a table that he drew on a whiteboard during the hearing, explaining that it is possible, under certain conditions, to “grant binary access and nothing else upon checking some other conditions”.

132 Associate Professor Boztas went on to explain Exhibit D as follows:
So we have an administrator signature and the access column actually just describes whether the signature is legitimate, whether the matching is granted. And, in the – in that case, the output is that the administrator is allowed access. The second case is a regular user. So they’re not in the administrator class. And there is a match with their biometric, the one on the second column, and there is no duress sent so they’re accessing the system. So you would – even in this case, it may well be that this is not purely binary access because the system may check whether there’s a duress bit activity or not. And the third one is uninteresting but, just for completeness, sometimes you didn’t access because nothing matches, there’s no legitimate signature.
The last one is there is a match but also the duress bit is set, which means the duress pattern or any other what you might call out of band technique of signalling is used, that is, those inputs are still all within the conditions specified by the accessibility attribute and, in which case, you would grant access. So what we have in the patent under the terms of the accessibility attribute is a sophisticated system for granting access corresponding to different conditions, including granting binary access sometimes as a result of checking these conditions. So that still falls within the accessibility attribute.
(Emphasis added)
133 Dr Dunstone agreed with this description, which is consistent with his evidence as summarised above.
134 CPC submits that where a user seeking access specifically identifies a condition of access sought, the authentication itself may constitute the provision or output of the accessibility attribute, because the authentication complies with the definition of establishing whether and under which conditions access should be granted in response to the specific access request. It submits that nothing in the claim language suggests that this kind of secure access is excluded from the claims. It relies on the following passage at page 15 lines 1 to 13 of the specification, by reference to figure 3, to support the contention that the accessibility attribute need not, separately to the biometric authentication, provide for the conditions of access:
The step 204 enables the user 101 to select a control option by providing one or more additional signals (not shown) to the controller 107. Thus for example the control option could enable the user 101 to access one of a number of secure doors after his or her identity has been authenticated in the step 203. In subsequent step 205 the controller 107 sends the appropriate access signal 108 to the controller 109. The process is then directed in accordance with an arrow 206 back to the step 201.
Thus for example the sub-system 116 can be provided with a single biometric sensor 121 in the code entry module 103 which enables the user 101 to select one of four door entry control signals by means of separate buttons on the controller 107 (not shown). This would enable the user 101, after authentication by the biometric sensor 121 in the code entry module 103 and the controller 107 to obtain access to any one of the aforementioned for [sic, four] secure doors.
(emphasis added)
135 It submits that in this instance the accessibility attribute need not itself contain the conditions of access of the user (as opposed to simply a biometric “match”), because the user has already identified the control option (i.e. the condition of access) sought, which will be granted after their identity has been authenticated and an appropriate access signal has been sent. Where the user seeking access identifies the specific condition of access sought, the authentication may constitute the provision of the accessibility attribute, because it establishes whether and under which conditions access should be granted in response to the specific access request.
136 For the reasons given above, I do not consider that the language of the claims supports this construction. Nor do I consider that the passage cited assists the argument advanced by CPC. It is an example that the patentee provides where the user is afforded an opportunity to select a “control option”, which is a different concept to an accessibility attribute which, as the passage on page 14 (discussed above) indicates, is produced in response to authentication of the biometric signature received. The specification distinguishes between use of a control option and the provision of an accessibility attribute. For an accessibility attribute, it is the system recognition of the biometric signal that identifies the applicable conditions of access and signals an accessibility attribute, no element of user selection is involved, a point upon which the experts agreed.
137 More particularly, the claims distinguish between the provision of an accessibility attribute only if (first) a legitimate biometric signal is received (in the case of claims 1 and 2 of the 168 patent) and the provision of an accessibility attribute upon “matching the biometric signal against members of the database of biometric signatures” to thereby “output an accessibility attribute” (in the case of claims 5 and 6 of the 168 patent and all asserted claims of the 293 patent). Claim 3 of the 168 patent is silent as to the conditions for the provision of the accessibility attribute, save for that it be received from the transmitter sub-system. As such, neither the language of the asserted claims nor the specification supports the contention advanced by CPC.
138 Finally, CPC submits that the accessibility attribute must be output or provided within the transmitter sub-system, such that the transmitter sub-system determines the nature of the access to be granted, and no further verification or authentication steps (required to determine the nature of access) should occur in the receiver sub-system. Apple takes issue with CPC’s contention and seeks to make a distinction between the role of the transmitter sub-system in establishing whether and on which conditions access is granted following the receipt of a legitimate biometric signal, and the requirement that it alone “determine access”. It contends that further authentication and decryption processes must occur in the receiver sub-system once the secure access signal is received in order for access to be provided and on that basis the receiver sub-system has a role to play in determining access.
139 It appears that Apple’s submission proceeds on a misconception of the arguments developed by CPC. As I understand it, CPC does not advance the submission that no further decryption or processing of the accessibility attribute may take place (at all) in the receiver sub-system. Such a submission would be untenable having regard to the claim language and body of the specification.
140 For instance, claim 1 of the 168 patent requires the transmitter sub-system to provide an accessibility attribute if a legitimate biometric signal is received, and a receiver sub-system for providing access “dependent upon said accessibility attribute”. Nothing in that language precludes the receiver sub-system from taking other steps such as verifying or authenticating the accessibility attribute once received. Claim 5 of the 168 patent requires that the transmitter sub-system emit a secure access signal conveying information “dependent upon said accessibility attribute” and that the receiver sub-system have means for “receiving the transmitted secure access signal” and for “providing access to the controlled item dependent upon said information”. These claims provide no limitation as to what steps the receiver sub-system may perform in order to grant access to the controlled item upon receipt of an accessibility attribute. Nor do the other asserted claims.
141 Furthermore, the specification discloses on page 11 that the arrangement in figure 2 describes the scenario where the secure code in the access signal (108) used between the transmitter sub-system and the receiver sub-system is based on a rolling code. The rolling codes are described as using inherently secure protocols and serial number ciphering techniques which hide the clear text values required “for authentication” between the key fob (being the transmitter sub-system) and the receiver sub-system. On page 16, the specification describes, by reference to figure 4, a method of operation of the receiver sub-system in which, upon receipt of the secure access signal (108), the process is directed to step 302 in which “the controller 109 [within the receiver sub-system] compares the rolling code received by means of the access signal 108 with a reference code in the database 115” thereby confirming that the receiver sub-system may have a role in interpreting the signal (based on the accessibility attribute) received.
142 Later, on page 20, the specification refers, by reference to figure 7, how particular bits are used to signify various different conditions of access. It provides (page 20 line 22 to page 21 line 3):
A following step 603 determines if the received signal falls into the “duress” category. Signatures in this category indicate that the user 101 is in a coercive situation where, for example, an armed criminal is forcing the user 101 to access the secure facility (such as a bank door). If the step 603 determines that the signature is in the duress class, then a following step 604 prepares a “duress” bit for incorporation into the code access signal 108. The aforementioned duress bit is an access attribute of the biometric signal 102.
143 The accessibility attribute in this example takes the form of a code containing one or more bits that will need to be recognised by the receiver sub-system.
144 In my view these passages support the contention that the patents disclose and then claim an invention that does not restrict the manner in which, upon receipt by the receiver sub-system of the accessibility attribute, the accessibility attribute is interpreted or decoded. Consistently with this, claim 1 of the 168 patent requires the transmitter sub-system to determine if a legitimate biometric signal has been received and, if so, provide an accessibility attribute.
145 However, to the extent that it is submitted that the steps of determining whether and under which conditions access is granted upon receipt of a biometric signal must be completed in the transmitter sub-system with the provision of the accessibility attribute, I agree. It is the resulting accessibility attribute that crystallises (or “determines”) the nature of a user’s access. Upon receipt of the accessibility attribute, the receiver sub-system identifies, based on the accessibility attribute, the particular kind of access that has been granted and then provides the corresponding kind of access. The specification teaches that the receiver sub-system must, in order to perform its function, take steps in relation to authentication, including decoding any encryption of the accessibility attribute emitted by the transmitter sub-system.
4.5 Transmitter sub-system and receiver sub-system
146 The term “transmitter sub-system” appears in all the asserted claims of the patents, while the term “receiver sub-system” appears in all the asserted claims of the 168 patent and claims 1, 39 and 41 of the 293 patent.
147 Notwithstanding that the terms appear in a majority of the asserted claims, it is convenient to commence consideration of their meaning primarily by reference to claim 1 of the 168 patent, noting that neither party suggested that the terms are to be understood differently depending on the claims in which they appear.
4.5.1 The submissions
148 CPC advances three propositions as to its construction of “transmitter sub-system” and “receiver sub-system”. First, it contends that the transmitter sub-system and the receiver sub-system are not pre-defined sub-systems of physically separate or finite hardware or software components. Rather, they are defined purely by the functionalities required by each claim. Secondly, it submits that the transmitter sub-system and receiver sub-system may comprise overlapping hardware and software components. It submits that the claims do not exclude other forms of interaction or communication between particular components that might form part of the transmitter sub-system and receiver sub-system, either with each other or with other components in the system or the device, nor do they exclude the key components that might form part of these sub-system performing some other role within the device. Thirdly, it contends that each of the transmitter sub-system and receiver sub-system will include the “key” or “quintessential” hardware and/or software components responsible for effecting those functionalities but that the sub-systems need not include components that are ancillary or incidental to achieving those functionalities.
149 CPC contends that its position is supported by the language of the claims, the disclosures in the specification, the expert evidence and the common general knowledge at the priority date.
150 Apple disputes that the transmitter sub-system and receiver sub-system are to be defined in purely functional terms. It submits that the claims require the use of two separate and distinct sub-systems which perform different functions and are functionally and physically separate. It submits that the claims require an identifiable transmitter sub-system which transmits something and, where present in the relevant claim, a receiver sub-system which receives something, each of which is defined by reference to their functions as a “transmitter” and “receiver”. It similarly disputes the second of CPC’s contentions, emphasising that the claims require there to be a functional relationship between the transmitter sub-system and the receiver sub-system such that they cannot overlap, otherwise the language of transmitter sub-system and receiver sub-system would be incoherent and redundant. Apple also disputes the third proposition advanced by CPC and contends that there is no basis to exclude from the transmitter and receiver sub-systems components that are ancillary or incidental to achieving the functionalities required by the claims.
4.5.2 Consideration
151 The terms “transmitter sub-system” and “receiver sub-system” are not defined in the specification, nor are they terms of art. The primer provides an agreed definition of “transmitter”, as a device or component which is used to transmit information and of “receiver”, as a device or component which is used to receive information. This accords with the ordinary meaning of those words.
152 The meaning of the term “sub-system” was not agreed upon in the primer. However, in JER1 at [7], Associate Professor Boztas and Dr Dunstone agreed that in engineering and computer science:
…a subsystem is a secondary or subordinate system that is a component of a larger system. A subsystem typically performs a specific function within the context of the larger system and is sometimes designed to be modular, so it can be removed, upgraded or replaced without affecting the functionality of the overall system. Subsystems can consist of both hardware and software components and may interact with other subsystems within the system to carry out complex operations.
153 As a point of difference, Dr Dunstone considered that to qualify as a sub-system, there should be well-defined boundaries. Associate Professor Boztas, on the other hand, expressed the view that the boundaries “can be fluid and that a single system can function both as a transmitter and a receiver” and that “the subsystem’s function may overlap with other system components”. In expressing these views, both experts sought to draw support from the body of the specification.
154 Turning to the language of the claims, claim 1 of the 168 patent is for a system comprising, in integer (2), a transmitter sub-system “for enrolling biometric signatures into a database and for providing an accessibility attribute if a legitimate biometric signal is received”.
155 The requirement of this integer is that the transmitter sub-system be “for” (which I take to mean “suitable for”) the two functions identified namely, enrolling biometric signatures into a database and “providing” an accessibility attribute. To be a transmitter sub-system, the integer requires the further element that the sub-system be capable of performing the role of a transmitter, namely that it be capable of transmitting information. In this regard, I do not accept that integer (2) will be satisfied where there is a sub-system that is capable of performing only the two functions of enrolling biometric signatures and providing an accessibility attribute. That construction would give the word “transmitter” no work to do. This view is supported by the evidence of the experts.
156 Integer (3) of claim 1 of the 168 patent requires the system to have “a receiver sub-system for providing access to the controlled item dependent upon said accessibility attribute”. This integer requires first, that the receiver sub-system provides access to the controlled item, secondly, that such access be dependent upon the accessibility attribute and, thirdly, (for the same reasons given in relation to “transmitter”) that the receiver sub-system be capable of receiving information.
157 It is apparent from this review, taking the language of claim 1, that whilst there is no requirement that it be the transmitter sub-system that communicates the accessibility attribute directly to the receiver sub-system, there is a requirement that there be a transmitter sub-system and a receiver sub-system capable of performing transmission and reception functions, respectively.
158 Other of the asserted claims provide additional or different integers that give more detail as to the functions that the transmitter sub-system and receiver sub-system must perform. A number contain integers that there must be a more direct relationship between the transmitter sub-system and the receiver sub-system than required by claim 1 of the 168 patent.
159 For example, in the 168 patent:
(a) claims 2 and 3 require the receiver sub-system to receive the accessibility attribute “from the transmitter sub-system”; and
(b) claims 5 and 6 require the transmitter sub-system to have “means for emitting a secure access signal conveying information dependent upon said accessibility attribute” and a receiver sub-system comprising “means for receiving the transmitted secure access signal”.
160 Similarly for the asserted claims in the 293 patent:
(a) in claims 1, 39 and 41, the transmitter sub-system have “means for emitting a secure access signal” and the receiver sub-system have “means for receiving the transmitted secure access signal”; and
(b) in claims 27, 29 and 37, each has a step of emitting, by the transmitter sub-system, a secure access signal, although no receiver sub-system is included in these claims.
161 These claims make clear that there must be a functional relationship between the transmitter sub-system and the receiver sub-system within the overall system. In my view, they support the proposition that each sub-system is separate and distinct. There would be no need to refer to each as a “sub-system” if the functions of the two could be merged. Nor would it be coherent to have one sub-system communicate with another sub-system if they are not functionally separate from each other.
162 I disagree with the submissions advanced by CPC that the components comprising the transmitter sub-system and receiver sub-system need not be separately identifiable and may be described in purely functional terms.
163 The language of these claims indicates that there is to be a flow of information from the transmitter sub-system to the receiver sub-system (although not all of the claims are explicit as to how that flow is to occur, as claim 1 of the 168 patent demonstrates). Associate Professor Boztas and Dr Dunstone agreed in JER1 that the concept of a sub-system implies that boundaries for these components should exist within a larger system. However, Associate Professor Boztas’ view that “overlap” is permissible between a transmitter sub-system and a receiver sub-system tends to blur that distinction, apparent from the structure of the asserted claims, which indicate a flow of information from the transmitter sub-system (and often directly) to the receiver sub-system. The view which I prefer, is that each of the transmitter sub-system and receiver sub-system must be discernible as identifiably separate components and that there be a flow of information from one to the other.
164 At one point in his evidence, Associate Professor Boztas accepted this position. However, later he qualified his views on this, saying that the components of the two sub-systems can have multiple roles so long as they perform the functions of transmission and reception, emphasising that, as a matter of design, hardware and software components could perform overlapping functions. Whilst I accept that, as a matter of the underlying technology, it is possible to design a computer system, utilising hardware and software, where for efficiency it is useful to have hardware and software components that overlap in function, I do not consider that the language of the claims under scrutiny allow for that outcome. Dr Dunstone consistently expressed the view that there must be a clear boundary between the transmitter sub-system and the receiver sub-system. That is the view that I prefer.
165 The specification identifies non-exhaustive embodiments of the invention and leaves it open to those skilled in the art to implement the invention of the claims (and consistory clauses) in a suitable way. Despite the fact that the specification describes only preferred embodiments, none of the references identified by CPC in its submissions identify a basis for concluding that the transmitter sub-system and receiver sub-system can overlap in the manner for which CPC contends.
166 Nor does the disclosure in the specification by reference to figure 10 assist. CPC submits that the reference in the specification, at page 26 line 25 to page 27 line 2, to a “communication interface/transceiver 1008” and communications going both to and from the transmitter sub-system and receiver sub-system indicates that the patents contemplate the sub-systems having shared functionalities. However, figure 10 clearly depicts, and the specification clearly describes a distinction between the transmitter sub-system (116) and the receiver sub-system (117). Dr Dunstone and Associate Professor Boztas agreed in their oral evidence that control module (107) (within the transmitter) and control module (109) (within the receiver) are two separate pieces of hardware driven by software. There is no reference or description to suggest that the “communication interface/transceiver 1008”, itself one of several identified parts within the transmitter sub-system (116), is engaged in the receipt of any information from the receiver sub-system (117) or the control module (109). Indeed, the specification consistently describes and depicts separation between the transmitter sub-system and the receiver sub-system.
167 It is apparent from the above that I consider that the claims define parts of the system, method and apparatus concerned by reference to the functions that they perform. However, I consider that the transmitter sub-system and, where present, the receiver sub-system, must be separate and distinct sub-systems, and that the claims identify by different integers and in varying levels of detail, the functions that the transmitter sub-system and receiver sub-system (respectively) must perform.
168 CPC also submits that a transmitter sub-system or receiver sub-system may be identified by reference to what it considers to be the “key” or “quintessential” components required to perform the functions of the relevant sub-system. It submits that the mere fact that a component played a role, even an important role, in executing a particular function does not mean that the sub-system must include that component, and that an expert can “draw those boundaries where it makes sense”. However, the evidence of the experts that CPC cites in support of this position was not referring to the patent, but a document created by Apple that referred to the operation of the Apple Devices and, in that context, the operation of what is referred to as “the Touch ID or Face ID subsystems”. It was in relation to that document that the experts agreed that such sub-systems may have boundaries drawn “where it makes sense”. They did not, however, accept that a sub-system may be defined by the key or quintessential components. Nor were they asked about such matters by reference to the patent specification or the claims. Indeed, as Apple submits, until closing submissions this construction was not advanced and was not put to any of the experts, nor did it find expression in any of the written evidence filed on behalf of CPC.
169 Finally, at one point it appeared to be an issue between the parties whether or not a single computer or device could contain both the transmitter sub-system and the receiver sub-system. It does not appear to be in dispute that the language of the claims does not preclude such an arrangement. Taking claim 1 of the 168 patent as an example, it simply calls for a “system for providing secure access to a controlled item”. Unlike the heading of the patents (“Remote entry system”), the claims contain no language that indicates there be a requisite distance between the transmitter sub-system and the receiver sub-system.
4.6 Secure access signal
170 The term “secure access signal” appears in claims 5 and 6 of the 168 patent and all of the asserted claims in the 293 patent. No party suggested that the meaning of the term differed based on the claim in which it appears.
171 It is convenient to consider it by reference to claim 5 of the 168 patent:
(1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute; (6) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; and (7) means for enrolling biometric signatures into the database; (8) and a receiver sub-system comprising; (9) means for receiving the transmitted secure access signal; and (10) means for providing access to the controlled item dependent upon said information.
(Emphasis added)
4.6.1 The submissions
172 CPC contends first that the term “secure access signal” should be understood as a signal that contains the necessary information to inform the receiver sub-system whether and under which conditions access should be granted. The signal must contain the entirety of the information necessary for the receiver sub-system to discern the conditions of access without need for any further verification or authentication process to take place after receipt of the signal to ascertain whether and under which conditions access should be granted. Apple takes issue with this point in the same way it does in relation to the similar argument concerning the role of the accessibility attribute. My consideration of that point in section 4.4.2 above applies equally here. Secondly, CPC submits that based on the language of the claims, which require that “a secure access signal” be emitted, there can only be one secure access signal sent from the transmitter sub-system to the receiver sub-system, the contents of which differs depending on the condition of access granted. This contention, CPC submits, is consistent with the evidence of both Dr Dunstone and Associate Professor Boztas. Apple advances no submission to dispute this point.
173 Thirdly, the secure access signal must be “secure in some way, whether by encryption, authentication or otherwise”, thereby giving content to the word “secure”. Apple submits that a secure access signal is a signal which is secure in the sense that it is incorporated in a secure access system, such that if the transmission of a signal is confined to persons who have provided a legitimate biometric identifier, it is a secure access signal. Apple submits that the concept of “secure access” is referred to in the common general knowledge summary as describing the control of physical or logical access by granting access privileges on certain people while denying them to others. As at the priority date, secure access could be conferred based on something the privileged person knows (e.g. a password), has (e.g. a swipe card), or is (e.g. by a biometric identifier). Accordingly, it might be considered that a “secure access signal” is a signal that is secure because one of these conditions is met and there is no requirement that the signal itself be secure or secured in some additional way.
4.6.2 Consideration
174 There is a degree of ambiguity in the term “secure access signal”, because “secure” could be understood in a general sense to mean that it is an access signal within the system overall that is a secure system, or “secure” could have a more particular meaning in that something additional is required for the signal such that it can be considered a “secure” signal, regardless of the security of the system as a whole. Associate Professor Boztas recognised this ambiguity and takes the more particular view that the access signal must have an additional or a dual level of security (over and above simply being transmitted in a “secure” system in response to a biometric match) – for example by being encrypted – for it to qualify. Dr Dunstone appeared in his affidavit evidence also to take the view that an additional level of security in the form of encryption was required. However, in JER1 and his oral evidence, he takes the view that “secure” relates primarily to the access being granted by the signal, not necessarily to encryption or any other form of securing the signal.
175 Integer (1) of claim 5 of the 168 patent provides that it is a system for providing “secure access” to a controlled item. The means by which such secure access is provided is described by reference to the integers that follow. Everything in integers (2) to (10) may be considered to form part of a “secure access” system. However, integer (6) additionally requires that the transmitter sub-system include “means for emitting a secure access signal…”. The word “secure” indicates that the access signal itself must be secure. To give the phrase meaning, in my view, it is not sufficient that the access signal simply be within a system that is generally “secure” but that the signal itself be secure. Within the field of the invention, this would typically mean that it is encrypted or has other protected mechanisms applied to it. To take a different view would be to deprive the word “secure” of content.
176 The question is not whether or not a person has secure access, but whether the signal itself is secure. The word “secure” in “secure access signal” will be given content provided that the communication meets that requirement. In each case, that will depend on the specific system concerned. It must properly be said that the access signal within the system is secure, whether by encryption, authentication or some other means.
4.7 Conditional access
177 The construction of the term “conditional access” arises in relation to the 293 patent only. Claims 1, 39 and 41 require the receiver sub-system to comprise a “means for providing conditional access to the controlled item dependent upon” information conveyed by a secure access signal. A similar requirement appears in claims 27, 29 and 37 without reference to any receiver sub-system.
178 Although claim 1 of the 293 patent is lengthy, it warrants repetition to put the integer containing these words into context:
(1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction; (9) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (10) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; (11) said system further comprising: a receiver sub-system comprising; (12) means for receiving the transmitted secure access signal; and (13) means for providing conditional access to the controlled item dependent upon said information.
(Emphasis added)
4.7.1 The submissions
179 CPC submits first, that access must be “conditional” in the sense that a condition is imposed on the access. For example, a user may be allowed to access one part of the controlled item, but not another, at least not without further authentication. Secondly, CPC contends that unlimited access is still a “condition” of access, provided there are other conditions of access which might be imposed. Thirdly, the conditional access provided must be dependent upon information contained in the secure access signal.
180 Apple submits that “conditional access” means any condition imposed upon the relevant access sought, citing the evidence of Associate Professor Boztas and Dr Dunstone. It further submits that the requirement of conditional access in each of the asserted claims in the 293 patent appears in addition to the requirement that “secure access” be provided and that accordingly these are cumulative requirements. On that basis, it submits that the denial of access is not “conditional access” and that conversely, a system that only has the capacity to grant unconditional access simply grants “access” and does not meet the requirements of the relevant asserted claims.
4.7.2 Consideration
181 The term “conditional access” does not appear in the body of the specification of the 293 patent, except for the consistory clause.
182 Taken in the context of claim 1 of the 293 patent, it is apparent that the receiver sub-system must: (a) have the capacity to provide conditional access; (b) that such access must be provided to the “controlled item”; (c) that such access must be dependent on information conveyed by the secure access signal; and (d) that the information conveyed by the secure access signal must be “dependent upon said accessibility attribute”.
183 Despite their competing submissions, it appears that nothing of substance separates the parties on this issue (setting to one side the dispute regarding “controlled item” which I have addressed above). Both accept that access must be “conditional” in the sense that a condition is imposed on access. Both also accept that a system that contains, amongst other options, an ability to grant unconditional access, will have a means for providing conditional access within the requirement of the integer. Both also accept that a system that only has the capacity to grant unconditional access does not meet the requirements of the claim, because it simply grants “access” and not conditional access.
184 I accept these matters.
4.8 Administrator signature
185 Claims 3 and 6 of the 168 patent require a biometric signal to be stored in the database “as an administrator signature”. A similar requirement appears in claim 41 of the 293 patent. Claim 29 of the 293 patent also refers to a signature of a “system administrator class”. No party suggested that the meaning of the word “administrator” differed based on the claim in which it appears.
186 It is convenient to consider this term by reference to claim 3 of the 168 patent:
(1) A method of enrolling, by a transmitter sub-system, biometric signatures into a database of biometric signatures (2) in a system for providing secure access to a controlled item, (3) the system comprising the transmitter sub-system and (4) a receiver sub-system (5) for providing access to the controlled item (6) dependent upon an accessibility attribute received from the transmitter sub-system; said method comprising the steps of: (7) storing a biometric signal received by the transmitter sub-system in the database as an administrator signature; and (8) enabling administrative processing of information stored in the database if a biometric signal matching the stored administrator signature is received by the transmitter.
(Emphasis added)
4.8.1 The submissions
187 CPC submits first that an “administrator” is an individual who has been granted special privileges, namely the authority to manage and oversee a system, network or application. Secondly, that the way in which the system stores and recognises a signature as an administrator signature is not limited by the claims in any particular way – provided the system has a way of storing a signature in the database and providing a person (the first person to be enrolled in the case of claim 6 of the 168 patent and claim 41 of the 293 patent) with the authority to manage and oversee the system, network or application, this is sufficient to meet the requirement of the claims. Nothing in the language of the claims requires the template in the database itself to be “tagged” as an administrator. Whilst the specification provides an example of all signatures stored in the database being tagged as belonging to one or more classes of user, this is not a limiting example. CPC submits that, consistent with this position, Dr Dunstone accepted that the biometric signature of the claims would not itself contain any metadata that indicates that a user is an administrator, and the specification disclosed that a first user could be an administrator by reason of their power to control the system.
188 Apple submits that what is required by the relevant claims is the storing, in the database, of a biometric signal “as an” administrator signature and that this requires the signature to be identified, in the database, as an administrator signature. Apple contends that to be an “administrator signature”, the ability to amend biometric data stored in the database must be granted to that signature, such that administrative privileges must be attached to the signature, not merely the person to whom the signature relates.
4.8.2 Consideration
189 In the context of claim 3 of the 168 patent, the term “administrator signature” arises as an integer of a method for enrolling, by a transmitter sub-system, biometric signatures into a database of biometric signatures in a system for providing secure access to a controlled item, the method including the steps of: “storing a biometric signal received by the transmitter sub-system in the database as an administrator signature” (integer (7)); and “enabling administrative processing of information stored in the database if a biometric signal matching the stored administrator signature is received by the transmitter” (integer (8)).
190 The term “administrator signature” identifies a type of signature. The common general knowledge summary indicates that an “administrator” is someone with the access privileges needed to perform administrative functions, such as enrolling new users. The primer provides that the term “administrator class” describes a class of user who has a higher level of access compared to non-administrator class users, with access privileges to files for non-administrator class users. The primer identifies that a “biometric signature”, also referred to as a “template”, is a mathematical representation of information obtained from a biometric signal, relating to a certain entity or person, that is used for authentication purposes.
191 The common general knowledge summary indicates that it was common general knowledge that “matching” involved the “use of a means to compare a sample biometric attribute with one or more templates/signatures stored in the database of a secure access system. The result of the comparison was a ‘score’ that indicated the likelihood that the biometric attribute being presented to the system was the same as one that was the stored template. If the score exceeded a pre-set threshold, the system treated it as a match”.
192 In this context, the use of the term “administrator signature” should be taken to refer to a mathematical representation of information obtained from a biometric signal that matches a stored biometric signal in the database signifying that the person whose signature is used has administrator privileges. Put another way, it is not sufficient that there be a person designated as an administrator whose signature is enrolled in the database. Rather, the system must recognise that the signature is an “administrator signature”.
193 The distinction between an administrator as a person and the administrator signature is supported by the language of the specification, which explains at page 19 lines 1 to 6:
Although the present description refers to “users”, in fact is its “fingers” which are the operative entities in system operation when the biometric sensor 121 (see Fig. 2) is a fingerprint sensor. In this event, a single user can enrol two or more of his or her own fingers as separate administrators or (ordinary) users of the system, by storing corresponding fingerprints for corresponding fingers in the database 105 via the enrolment process 800 (see Fig. 8).
194 Associate Professor Boztas and Dr Dunstone agreed in their oral evidence, in the context of the description in the specification, that “administrative privileges” are “attached to the biometric signature which is enrolled in the database” as an administrator signature, not to the person to whom the signature relates. This is the way in which the references to “administrator signature” and “administrator” as used in the claims should be understood.
4.9 Series feature
195 The asserted claims of the 293 patent require that there be a means for enrolling relevant signatures into the database of biometric signatures. This is defined by the parties as the series feature. By reference to claim 1 of the 293 patent, the requirements of the series feature are set out in integers (6) to (8):
(1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction; (9) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (10) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; (11) said system further comprising: a receiver sub-system comprising; (12) means for receiving the transmitted secure access signal; and (13) means for providing conditional access to the controlled item dependent upon said information.
(Emphasis added)
4.9.1 The submissions
196 CPC submits that the series feature is directed to obtaining a quality biometric signature and requires there to be a sufficient number of entries and duration of each entry to obtain a sufficient quality scan that can be mapped into an instruction. It requires: (a) capturing multiple scans or images of a finger, where the finger has to be held on the sensor for long enough to obtain a scan; and (b) mapping those scans or images into a single mathematical representation, which is then saved in the database as a biometric signature according to the mathematical representation. CPC further submits, relying on the oral evidence of Associate Professor Boztas and Dr Dunstone, that once the series is captured by the biometric sensor, there needs to be a process, pursuant to a set of instructions, to convert the raw biometric data into a template and store that template in the database. It relies on passages in the specification at pages 26 and 28 to support its construction and criticises Apple’s construction as being too heavily reliant on one optional embodiment in the specification.
197 Apple submits that the purpose of the series feature is to provide a mechanism by which a user may instruct the system to enrol biometric signatures. It involves a series of sequential steps that are spelt out in the integers of the asserted claims of the 293 patent. Additionally, Apple advances a challenge to Associate Professor Boztas’ independence on the basis of the varied and “self-contradictory” evidence he gave during the course of the hearing as to his construction of this integer. Apple submits that Associate Professor Boztas ultimately accepted that his evidence in this respect was “incoherent”.
4.9.2 Consideration
198 It was known, as at the priority date, that when a user sought to authenticate their biometric attribute in a secure access system, the system would seek to match their signature against one that was already enrolled. Users who were new to a secure access system needed to enrol their relevant biometric attributes. There were different ways of doing so depending on the specific secure access system. Usually, they involved presenting the biometric attribute to a sensor several times to ensure a sufficient quality scan. The primer records that enrolment was known before the priority date to take place according to one of two arrangements. In one, the same biometric sensor would be used for enrolment and matching. In another, one biometric sensor at a central server was used for enrolment and another biometric sensor at each secure access point was used for matching. It is plain from the language of the series feature that it concerns the process of enrolment.
199 Claim 1 of the 293 patent requires that the system for providing secure access to a controlled item include a transmitter sub-system with means for enrolling signatures into the database using the biometric sensor (integer (5)) with the characteristics of the following integers to meet that purpose:
(6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction;…
200 The claim then requires by integers (9) and (10) a means for matching, output of an accessibility attribute and emitting a secure access signal.
201 Nothing in the language of the claim indicates or suggests the purpose of integers (6) to (8) is to obtain a quality biometric signature. Indeed, were that to be so, one wonders why that requirement was not also a requirement of the “matching” feature of integer (9). Both the enrolment and matching processes require a sufficient quality biometric reading to be taken for the system to effect either process. The language of the claim is silent as to purpose, other than to indicate in integer (5) that it is part of a means for enrolling relevant signatures into the database.
202 The reference to “enrolling” finds expression in the description in the specification of figure 8. In the context of figure 6, the specification at page 18 lines 12 to 14 provides that “[i]f the database 105 is empty, then the process 700 is directed by an arrow 703 to 706 in Fig. 8 which depicts a process 800 dealing with the enrolment or the administration function for loading relevant signatures into the database 105.”
203 Integer (6) requires “means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry”.
204 The primer provides that as at the priority date, it was understood in the field that the term “biometric signal” meant “a signal in the form of a sample of raw biometric data associated with an entity, such as data relating to a fingerprint, retina, iris or face, which is conveyed from a biometric sensor.”
205 This integer requires a series of entries of such a signal and that the series be “characterised” (defined by the Macquarie Dictionary as meaning “distinguished as a characteristic”) by either or both of (“at least one of”): (a) the number of entries of the biometric signal; and (b) the duration of each entry.
206 An example of such entries is provided in the specification by reference to figure 8 which depicts the “enrolment process 800”. The specification, at page 19 lines 9 to 21, goes on as follows:
The first administrator can provide control information to the code entry module by providing a succession of finger presses to the biometric sensor 121, providing that these successive presses are of the appropriate duration, the appropriate quantity, and are input within a predetermined time. In one arrangement, the control information is encoded by either or both (a) the number of finger presses and (b) the relative duration of the finger presses. If the successive finger presses are provided within this predetermined time, then the controller 107 accepts the presses as potential control information and checks the input information against a stored set of legal control signals.
One example of a legal control signal can be expressed as follows:
“Enrol an ordinary user” -> dit, dit,dit, dah
Where “dit” is a finger press of one second’s duration (provided by the user 101 in response to the feedback provided by the Amber LED as described below), and “dah” is a finger press of two second’s duration.
(Emphasis added)
207 Integer (7) requires that the means for enrolling relevant signatures includes “means for mapping said series into an instruction”.
208 Integer (8) requires that there be “means for enrolling relevant signatures into the database according to the instruction”.
209 The Macquarie Dictionary defines “instruction” in the context of computers to be “a number or symbol which causes a computer to perform some specified action”. The experts agreed that “instruction” means “a direction or command”, an example of which, Associate Professor Boztas accepted, was that italicised in the passage quoted above being the instruction to “[e]nrol an ordinary user” in response to the input “dit, dit, dit, dah”. Although the word “instruction” is not used in the passage, I consider that the reference to a stored set of “legal control signals” equates to an “instruction” onto which the successive finger presses in the example are checked (or mapped).
210 In light of these matters, in my view, integers (7) and (8) require that the series of entries be mapped into a pre-existing direction or command (e.g. “dit, dit, dit, dah”) and that there be means for enrolling the signatures into the database according to that instruction. The instruction necessarily pre-exists the entry of the series because otherwise there would be nothing for the series to be mapped onto to give effect to enrolment. This was the view adopted by Dr Dunstone, which I accept.
211 It is apparent from the foregoing that I do not accept that the series feature is directed to obtaining a quality biometric signature or that it requires there to be a sufficient number of entries and duration of each entry to obtain a single mathematical representation, which is then saved in the database as a biometric signature according to the mathematical representation. Integer (5) provides simply for a “means for enrolling relevant signatures into the database…” and does not confine the operation of the means by reference to any concept as to the quality of the signatures received. The entries of integer (6) are characterised not by reference to the quality of the biometric signature, but rather by either the number of entries or duration of each entry (or both) and that series, by integer (7), is mapped into an instruction. As Dr Dunstone explained in his evidence, the series feature can be understood as a mechanism for communicating to a secure access system that there is a need to enrol a signature in circumstances where the system has no user interface to otherwise communicate such a request. By using a pattern of presses of fixed number and/or duration, the system recognises the series of biometric signals as a request for enrolment, those presses being mapped into an instruction for enrolment.
212 CPC’s submission relied in part on the evidence of Professor Boztas. However, cross examination revealed that his construction was not dependent on the language of the claims and was difficult to understand. I did not find it helpful in this respect.
5. THE APPLE DEVICES
5.1 Introduction
213 As I have noted in section 1.2 above, the parties agreed in advance of the trial that the Apple Devices could be corralled into five exemplar categories. In the course of advancing their arguments concerning infringement, their position matured to the point where the parties agreed that the question of infringement could be analysed primarily by reference to the contents of two working documents which were prepared during the course of evidence. Working document 1, the details of which I refer to further below, describes in stepwise fashion the process of biometric enrolment for Apple Devices with touch ID and Face ID within each of the exemplar categories. Working document 1 also describes the process of biometric matching to access the home screen of the Apple Devices in each of the exemplar categories. Working document 2, also described in further detail below, explains the process of biometric matching to access a 1st or 3rd party application (or part of an application on the Apple Device that requires biometric authentication for access) for Apple Devices in each of the exemplar categories. It also describes the biometric matching process required for access to the Apple Wallet application, which may be provided with or without access being granted to any other part of the device. The steps described in each of these documents is accompanied by flowcharts which depict these operations of the Apple Devices.
214 It will be seen in section 6 below that the bulk of the dispute between the parties concerning infringement may be addressed by reference only to working document 1. This is because the biometric matching steps are not materially different between access to the home screen addressed in that document and access to 1st and 3rd party applications or the Apple Wallet.
215 Before describing these working documents in further detail, I first address some of the background to the evidence concerning the operation of the Apple Devices.
5.2 The evidence concerning the Apple Devices
216 Some controversy unfolded during the conduct of the proceedings regarding how the Apple Devices operated.
217 In an early case management hearing on 16 December 2021, CPC was ordered to file and serve a position statement on infringement in accordance with paragraph 6.12 of the Intellectual Property Practice Note (IP-1 PN) and Apple was ordered to file and serve a PPD describing the relevant features of each of the impugned Apple Devices and a position statement on infringement in accordance with paragraphs 6.15 and 6.16 of the IP-1 PN, respectively. The parties did this. The PPD was verified as correct by Mr Kostka.
218 After these steps were complete, by orders dated 7 October 2022, Apple was required to, and did, permit CPC’s independent expert to inspect computer source code in accordance with an agreed protocol.
219 Notwithstanding these steps, there continued to be disputation between the parties as to the way the impugned Apple Devices operated.
220 On 12 July 2023, Mr Benson, Mr Koska and Ms Wells filed evidence which contained significantly more detail than the information contained in the PPD concerning the operation of the Apple Devices. On 7 September 2023, Apple filed an affidavit from Mr Paaske, which described the role of a communication “bus” used in the Apple Devices that was not included in the PPD. Subsequently, at CPC’s request, Apple produced micro-architecture specifications providing further information about the operation of the Apple Devices. The evidence of the Apple Engineers expanded upon or qualified aspects of the PPD, such that on 19 September 2023, Apple agreed in a notation to orders made on that date that the PPD had been superseded by the evidence of the Apple Engineers.
221 On 28 September 2023, less than three weeks before the hearing was scheduled to commence, Apple filed further evidence from Mr Kostka and Mr Benson.
222 On 14 October 2023, Apple filed additional affidavits from Messrs Kostka, Benson and Paaske.
223 As I have noted, on 15 August 2023, 7 October 2023, 12 October 2023 and 17 October 2023 Professor Smith swore affidavits setting out his understanding of the components and workings of the Apple Devices, based on the PPD, the evidence of the Apple Engineers and the source code that he had inspected. Associate Professor Boztas also filed responsive affidavit evidence.
224 The trial commenced on 16 October 2023.
225 During the course of cross-examination of the Apple Engineers, yet further detail emerged as to the operation of the Apple Devices which was addressed, by leave, in the fourth affidavit of Associate Professor Boztas.
226 On 30 October 2023, part way through the hearing, CPC sought to rely on a fifth further amended position statement of infringement dated 27 October 2023, adjusting its infringement case to meet the additional affidavit evidence of the Apple Engineers, as well as evidence adduced in cross-examination. No objection was taken by Apple to CPC’s reliance on this position statement.
227 It may be seen that the operation of the Apple Devices and CPC’s infringement case were, until the conclusion of the trial, moving sands.
228 CPC criticises Apple’s conduct in relation to its disclosure of the operation of its devices, contending that it reflects a drip feeding of information as it suited its position in the litigation resulting in critical aspects of the biometric functionalities of the Apple Devices not being uncovered until late in the proceeding, including key communications steps. As such, CPC submits that it was required to continually adjust its infringement case each time more information came to light, including in response to the evidence of the Apple Engineers. CPC submits that no criticism can reasonably be advanced at Associate Professor Boztas for changing his evidence regarding the presence of features of the asserted claims in the Apple Devices having regard to the unfolding evidence of the operation of those devices.
229 Apple in turn criticises CPC for reformulating its infringement case multiple times, asserting it shifted its position as to the construction of various integers of the claims in search of a credible infringement theory. It submits that the additional evidence of the Apple Engineers was necessary to meet CPC’s belatedly re-pleaded infringement case as to the operation of the Apple Devices. It submits that, regardless of the further affidavit evidence, it provided extensive disclosure of the Apple Devices throughout the course of the proceedings, including providing access to the underlying source code for the operation of the Apple Devices.
230 To the extent necessary, I address these matters below in the context of my consideration of the infringement case.
5.3 The development of the working documents
231 Several versions of the working documents were prepared by CPC during the course of the proceedings with amendments broadly following the course of the evidence described above. Each was heavily footnoted by reference to the evidence and, through its various iterations, was the subject of review by Apple. Despite vigorous forensic disputation, the parties were ultimately able to agree to most of their contents.
232 The penultimate version of the working documents was tendered after the conclusion of the evidence of the Apple Engineers and became exhibit 10. Exhibit 10 is entitled “The First and Second Working Documents of the Apple Devices provided on 1 November 2023”.
233 Tab 1 of exhibit 10 is titled “Confidential Second Further revised Applicant’s document on the workings of the Apple Devices in relation to Touch ID and Face ID” dated 27 October 2023. Section B describes by reference to steps 1 to 19 the process of biometric enrolment for Apple Devices with touch ID and face ID within exemplar categories 1 to 4, noting that no biometric enrolment steps are carried out by the Apple Watch. The same steps apply to Apple Devices in exemplar category 5, save for slightly amended steps 7, 8 and 9.
234 Section C describes by reference to steps 1 to 30 the process of biometric matching to access the home screen of the Apple Devices in exemplar categories 1 to 3. The same steps apply to Apple Devices in exemplar category 4 (plus an additional process that takes place in conjunction with step 28, described by reference to step 28B) and exemplar category 5 (save for slightly amended steps 12 to 14).
235 Annexures A and B to tab 1 of exhibit 10 are flow charts depicting the biometric enrolment and matching processes described.
236 Tab 2 of exhibit 10 is titled “Second Further Revised Confidential Second Workings Document” dated 27 October 2023. Section A describes by reference to steps A1 to A29 the process of biometric matching to access a 1st or 3rd party application (or part of an application that requires biometric authentication for access) for Apple Devices in each of the exemplar categories. It also describes, in section B, by reference to steps W1 to W25 the biometric matching process required to access to the Apple Wallet application with or without access being granted to any other part of the device. Flowcharts of the biometric matching steps described in tab 2 are annexed.
237 During the hearing, on 29 October 2023, Dr Dunstone affirmed a seventh affidavit in the proceedings, in which he describes, based on the evidence of the Apple Engineers and by reference to tab 1 of exhibit 10, his understanding of the process of biometric template encryption and decryption during enrolment and matching in the Apple Devices. Dr Dunstone gives evidence that annexures A and B to tab 1 of exhibit 10 do not depict various steps undertaken by the Apple Devices in this respect and annexes (as ESD-66 and ESD-67) to his affidavit amended versions of those flowcharts with the steps he considers to be missing identified in green. Annexures ESD-66 and ESD-67 form tabs 6 and 7, respectively, of exhibit 9 entitled “Bundle of schematic drawings of the operation of the Apple Devices provided on 1 November 2023”. Given the factual dispute between the parties, as I explain further below, it is Dr Dunstone’s amended version of the flowcharts depicting biometric enrolment and matching processes that I reproduce below.
238 On 3 November 2023, Apple produced a mark-up of exhibit 10, setting out where it contended amendments should be made to the working documents based on the evidence adduced at trial. CPC reviewed the mark-up produced by Apple and indicated by way of yellow highlighting the amendments it opposed. A copy of tab 1 and tab 2 of exhibit 10 (excluding their annexures) containing Apple’s proposed amendments in mark-up and CPC’s areas of disagreement in yellow highlight was provided to my chambers by email on 28 November 2023.
239 It is this version of tab 1 and tab 2 of exhibit 10 that I refer to (and rely upon) below as working document 1 and working document 2, respectively.
240 In its closing submissions CPC pressed the six discrete areas of dispute it identified in working document 1 and working document 2 in relation to the operation of the Apple Devices. In answer, Apple sought to press its amendments only in respect of three of the disputed areas identified by CPC. To the extent the details of working document 1 and working document 2 are extracted below, only the areas that remain in contest between the parties are shown in mark-up.
241 The factual issues in dispute as to the operation of the Apple Devices are now limited to the following three matters:
(a) the role of SecureKeyStore (SKS) / AppleKeyStore (AKS) [redacted] [redacted] [redacted] [redacted] [redacted] in biometric enrolment and matching;
(b) [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]; and
(c) [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
242 Disputed factual matter (c) concerns step A4 of the process for accessing 1st and 3rd party applications, as set out in working document 2. CPC contends that, having regard to its construction of the “transmitter sub-system” and “receiver sub-system” aspects of the asserted claims, the dispute concerning this aspect of working document 2 is immaterial. Apple’s position in relation to construction likewise does not depend on this aspect of its device. Accordingly, it is unnecessary for me to consider this disputed matter.
5.4 Background to the operation of the Apple Devices
243 Before turning to consider the disputes identified in (a) and (b) above, in section 5.4.1 below, I first provide an overview of the operation of the Apple Devices. It is convenient to provide some background information regarding the many abbreviations used in the working documents. Below is a glossary of the terms used, the content of which is agreed, with the exception of two rows, which bear mark-up supplied by Apple reflecting its points of disagreement. Having regard to the footnoted references in those passages (which I have omitted below), I am satisfied that Apple’s mark-up is appropriate and should be included.
Software / hardware component | Description |
Application Processor (AP) | Is the main processor in Apple Devices which runs, among other things, the operating system. The memory that runs the software is divided into the user space and the kernel. |
Springboard (iOS Apple Devices) / LoginWindow (macOS Apple Devices) | Are internal software components operating in the user space in the AP that manage the Apple Device’s lock and home screens. |
Apple Wallet | Apple Wallet is a software component in the AP used to add and manage credit, debit and store cards and to make payments with Apple Pay. |
1st / 3rd party apps | A first party application is an Apple application and a third party application is a non-Apple application. |
Secure Element | Is a hardware component involved in enabling access to Apple Wallet in Apple Devices. |
AppleSEPManager | Is a software component [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] enabling drivers to register SEP endpoints, as well as implementing several endpoints with the SEP on its own. |
Apple Key Store | Is a software component in the AP that enables access to parts of the Apple Device through storage and management of keys. which is the endpoint in the AP that communicates with SKS in the SEP. During unlocking of an Apple Device, it receives a notification from SKS that the lock state of the keybag has changed, enquires of SKS what the current lock state is, and receives notification that the keybag has been unlocked. AKS does not itself enable access by storing and managing keys – that is the role of SKS. |
[redacted] | [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] |
NAND Flash Storage | Is a hardware memory device that stores biometric signatures. |
Mailbox / OOL Buffer | The mailbox is an interface between the AP and the SEP which uses OOL [out-of-line] communication. |
[redacted] [redacted] | [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] |
Secure Enclave | Is described by Apple as a dedicated secure subsystem integrated into its systems on chip. Includes the SEP. |
Secure Enclave Processor (SEP) | Is a dedicated processor that provides the main computing power for the Secure Enclave to perform secure services and operates within that trusted environment, and enables the handling of cryptographic materials. |
Secure Neural Engine | Is a dedicated software engine within the Secure Enclave on devices with Face ID, which converts 2D images and depth maps into a mathematical representation of a user’s face. |
SBIO (Touch ID) / [redacted] [redacted] [redacted] | Are software components in the SEP responsible for managing involved in performing aspects of the biometric enrolment and matching processes. |
SCRD | Is a software component in the SEP [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. |
SKS | Is a software component in the SEP [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. |
SSE | Is a software component in the SEP [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. |
5.4.1 Overview of the touch ID, face ID and data protection architecture
244 In its closing submissions, Apple provided a heavily cross-referenced overview of the operation of the Apple Devices, which provides a convenient summary for the purpose of this judgment and is largely replicated below. It is substantially taken from the evidence of the Apple Engineers.
245 Touch ID and face ID work in conjunction with the underlying data protection architecture in the Apple Devices. They do not replace the need for a passcode but provide an alternative means of authentication to unlock an Apple Device. They use hardware and software components, including those located on the System on a Chip (SoC) which is an integrated circuit. It contains an Application Processor (AP) and Secure Enclave Processor (SEP). The AP is the micro-processor that runs the operating system for the Apple Devices. The SEP is a separate micro-processor responsible for all cryptographic operations (not only unlocking) on Apple Devices.
246 Each Apple Device with touch ID has a fingerprint sensor. [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Each Apple Device with face ID has a TrueDepth Camera System [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
247 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
248 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
249 Touch ID enrolment can be enabled at any time, following entry of the user’s passcode. A maximum number of five fingerprints can be enrolled. To enrol a fingerprint, a user is asked to place their finger on the sensor from different angles. Biometric enrolment or deletion requires entry of a passcode.
250 Face ID enrolment involves the user placing their face in the frame on the user interface and moving their head in a circle to enable the TrueDepth Camera System to capture two- and three-dimensional images. A user can enrol two faces, each of which is granted the same access privileges. Biometric enrolment or deletion requires entry of a passcode.
251 The components involved in biometric enrolment for touch ID and face ID are identified in the flowchart and steps set out in section 5.5 below. The components and steps for biometric matching to access the home screen, 1st and 3rd party applications and the Apple Wallet for touch ID and face ID are described by reference to the flowchart and steps set out in section 5.6 below.
252 Where a user seeks to access a 1st and 3rd party application, they may be required a user to enter their password or other login details (including providing their biometric) in order to access the application. A user can elect to store their login details or password on the Keychain (an SQLite database) on the device. The Keychain functions as a repository of login details and passwords that a user might need to access an application. [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. When a user unlocks a device – whether using touch ID, face ID or a passcode – [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
253 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
254 Apple submits, and I accept, that the evidence of Associate Professor Boztas supports three matters of significance it makes in relation to access to 1st and 3rd party applications. First, biometric authentication for providing access to [redacted] [redacted] [redacted] is a separate process which is not related to, and must occur after, the process of unlocking an Apple Device. Secondly, the requirement that a user undertake that separate biometric authentication process is not established by the biometric authentication process for unlocking an Apple Device. Thirdly, the outcome of that separate process is binary in that the end result will be that a user is either granted or refused access to [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
255 The process of obtaining access to Apple Wallet is independent of the process for unlocking the Apple Device. If biometric authentication is enabled, access to Apple Wallet is granted after: (a) a user requests access to Apple Wallet and presents a biometric; [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
256 Apple submits, and I accept, that the evidence supports its view that the biometric authentication process involved in obtaining access to Apple Wallet is separate to the authentication process involved in unlocking the Apple Device and the requirement of a separate authentication process is not established by any aspect of biometric authentication involved in unlocking the Apple Device. Nor, if a party seeks and obtains access to Apple Wallet when an Apple Device is locked, will they be granted access to the device. Finally, the outcome of the authentication process for Apple Wallet is binary in that access is either granted or refused.
5.5 Biometric enrolment
257 Working document 1 describes the steps by which biometric enrolment takes place in the Apple Devices. As indicated above, Dr Dunstone prepared an amended flowchart illustrating those steps for the Apple Devices used without accessories, which is set out below. Apple contends that the steps marked in green ought to be included, which CPC disputes.
5.5.1 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]

5.5.2 Steps involved in biometric enrolment – exemplar categories 1, 2 and 3
258 The steps for biometric enrolment for Apple Devices in exemplar categories 1, 2 and 3 are explained as follows. These steps are largely agreed between the parties, save for the matters identified in mark-up, which are contended for by Apple and opposed by CPC. For the reasons set out in section 5.7 below I find that Apple’s proposed mark-up in relation to step 5 to be correct in part and correct in its entirety in relation to steps 18.
259 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
260 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
261 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
262 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
263 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
264 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
265 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
266 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
267 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
268 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
269 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
270 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
271 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
272 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
273 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
274 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
275 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
276 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
277 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
5.5.3 Steps involved in biometric enrolment – exemplar categories 4 and 5
278 The same steps for biometric enrolment apply to exemplar category 4 as no biometric enrolment steps are carried out by the Apple Watch. The same steps also apply to exemplar category 5 with the exception that steps 7, 8 and 9 are replaced with slightly different steps. None of these differences have been identified by either party as material to the question of infringement and accordingly, it is not necessary to address them in more detail.
5.6 Biometric matching
279 Working document 1 also describes the steps by which biometric matching takes place to access the home screen of the Apple Devices. As indicated above, Dr Dunstone prepared an amended flowchart illustrating those steps for the Apple Devices used without accessories, which is set out below. Apple contends that the steps marked in green ought to be included, which CPC disputes.
280 Working document 2 describes the steps by which biometric matching takes place in the Apple Devices to access a 1st or 3rd party application (or part of an application that requires biometric authentication for access) and the Apple Wallet application, with or without access being granted to any other part of the device.
1.1.1
5.6.1 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]

5.6.2 Steps involved in biometric matching to access the home screen – exemplar categories 1, 2 and 3
281 The steps for biometric matching to access the home screen for Apple Devices in exemplar categories 1, 2 and 3 are explained as follows. These steps describe the matching process in the case of unlocking the Apple Device to gain access, excluding to applications, parts of applications or setting options that require additional authorisation to access. The same dispute in relation to step 18 of the biometric enrolment process applies to step 18 of the biometric matching process described below. For the reasons given in section 5.7 below, I find that Apple’s mark-up should be accepted.
282 Step 1: a user wakes the device by either pressing the home button or power button, or by raising the device or tapping the screen.
283 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
284 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
285 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
286 Steps 5 to 10 are not applicable and have been deleted from working document 1.
287 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
288 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
289 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
290 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
291 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
292 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
293 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
294 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
295 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
296 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
297 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
298 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
299 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
300 Steps 24 and 25 are not applicable and have been deleted from working document 1.
301 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
302 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
303 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
304 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
305 Step 30: the user of the device has access to the home screen.
5.6.3 Steps involved in biometric matching to access the home screen – exemplar categories 4 and 5
306 The same steps for biometric matching to access the home screen apply to exemplar category 4, with the addition of a further process that takes place in conjunction with step 28. The same steps also apply to exemplar category 5 with the exception that steps 12, 13 and 14 are replaced with slightly different steps. None of these differences have been identified by either party as material to the question of infringement and accordingly, it is not necessary to address them in more detail.
5.6.4 Steps involved in biometric matching to access 1st and 3rd party applications
307 The steps for biometric matching to access 1st and 3rd party applications (or part of an application) on Apple Devices that requires touch ID or face ID authorisation for access are explained as follows. The steps are largely uncontested, save for step A4. However, as I have noted above, neither party contends that the one disputed area regarding these steps, which is set out in mark-up below, requires determination for the purpose of resolving the issues of infringement central to the case. Accordingly, whilst I note the difference, it is not a matter that I address.
308 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
309 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
310 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
311 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
312 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
313 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
314 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
315 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
316 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
317 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
318 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
319 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
320 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
321 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
322 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
323 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
324 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
325 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
326 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
5.6.5 Steps involved in biometric matching to access Apple Wallet
327 The steps for biometric matching to access Apple Wallet or part of Apple Wallet, with or without access to any other part of the Apple Device are explained as follows. There is no contest between the parties as to the accuracy of these steps and are set out here for completeness.
328 Step W1: A user requests access to the Apple Wallet application or part of the Apple Wallet application on the Apple Device by the following means:
(a) double tapping on the home button (for iOS Apple Devices with touch ID);
(b) double tapping on the side button (for iOS Apple Devices with face ID);
(c) opening the Apple Wallet application and selecting the card to be used; or
(d) when the Apple Device detects a Near Field Communication (NFC) field from a card reader.
329 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
330 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
331 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
332 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
333 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
334 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
335 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
336 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
337 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
338 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
339 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
340 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
341 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
5.7 Disputed factual matters
5.7.1 Role of [redacted] [redacted] in biometric enrolment – step 5 of biometric enrolment
342 As set out above, step 5 provides that in devices with touch ID, [redacted] [redacted] [redacted] [redacted], and that for devices with face ID, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
343 Apple contends that missing from this step is a statement to the effect that AppleMesaSEPDriver and [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Apple’s proposed addition has been included in mark-up in section 5.5.2 above. It relies on the evidence of Mr Kostka in support of this contention. CPC contends that in re-examination, Mr Kostka clarified that AppleMesaSEPDriver [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. In any event, CPC considers that this issue is not material to the infringement dispute.
344 In his first affidavit, Mr Kostka states that the AppleMesaSEPDriver [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. In his oral evidence, he describes this component as “one of the key drivers” in the touch ID enrolment process. In re-examination, he was asked about this and responded that [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
345 Although not explored further, in my view, the evidence supports the addition sought by Apple in so far as it relates to AppleMesaSEPDriver. The relevant language in step 5 provides that [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Although, in its submissions, Apple contends that [redacted] – in the case of devices with face ID – [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted], the evidence to which the parties refer does not support that contention. Accordingly, I accept the change proposed by Apple insofar as it concerns the AppleMesaSEPDriver.
5.7.2 Role of [redacted] [redacted] in encrypting and decrypting templates in biometric enrolment and matching – step 18 of biometric enrolment and biometric matching
346 As set out above, step 18 of the biometric enrolment process (including the amendments in mark-up sought by Apple) is as follows:
[redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
347 Apple also seeks an amendment in similar terms (and supported by largely the same evidence given by the Apple Engineers) to step 18 of the biometric matching process to access the home screen of Apple Devices, which is set out in mark-up in section 5.6.2 above. Although my consideration below of this factual dispute between the parties is in the context of biometric enrolment, my reasons apply equally to the amendment sought by Apple in respect of biometric matching.
348 CPC contends that the amendments should not be permitted for three reasons. First, because the changes were proposed too late, after the Apple Engineers had ample opportunity to respond to earlier drafts of working document 1 and did not suggest that such amendments were necessary to be included. Secondly, because the amendments are proposed by Dr Dunstone in his seventh affidavit affirmed on 29 October 2023 (immediately before he gave evidence in concurrent session) based on (inaccurate) assumptions having regard to the evidence of the Apple Engineers. Thirdly, because the issue is ultimately not material to the infringement dispute.
349 Apple submits that the controversy regarding SKS / AKS arose because between 28 and 29 October 2023, after Professor Smith, Mr Kostka and Mr Benson had given oral evidence, CPC served: (a) the working documents that comprise exhibit 10; (b) its (revised) integer breakdown with cross-references to exhibit 10, where it identified for the first time step 28 in the biometric matching process (described in working document 1) to be the secure access signal and dividing line between the transmitter sub-system and the receiver sub-system within the claims; and (c) the fourth affidavit of Associate Professor Boztas identifying (for the first time) step 28 in the biometric matching process as the secure access signal transmitted by the transmitter sub-system to the receiver sub-system. Apple accepts that the amendments are not decisive of infringement (see section 4.5 as to whether or not the transmitter sub-system and receiver sub-system are separate and discrete sub-systems) but submits that they are material because the roles of SKS and AKS expose further overlap between the alleged transmitter sub-system and receiver sub-system. The amendments indicate that AKS is involved in encryption and decryption of templates as well as the enrolment and matching of templates, making it part of both the alleged transmitter sub-system and receiver sub-system. It submits that the evidence of Mr Benson in his first and third affidavits provides a factual basis for the amendments and that the evidence of Dr Dunstone simply relies on that evidence rather than on assumptions as to the manner of operation of the Apple Devices.
350 In order to address this dispute, it is necessary to recount the relevant evidence and its timing.
351 In his third affidavit dated 14 October 2023, Mr Benson responds to an earlier version of working document 1 where step 18 of biometric enrolment provides:
[redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
(Footnotes omitted)
He says at [7(a)]:
[redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
352 In his first affidavit dated 12 July 2023, Mr Benson explains that Apple products use data protection to protect stored data and provides an overview of that functionality. He explains that data protection is only enabled once a user has created a passcode. If the user does not create a passcode, the user can access all data at any time and the Apple product is never locked. [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
353 In the paragraphs of “Benson 1” at [40] and [41] referred to in Mr Benson’s third affidavit at [7(a)] (quoted above), Mr Benson explains that when a file is created on any Apple product, a 256 bit key (the per-file key) [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
354 Mr Benson also explains at [42] that for the system to access and read an encrypted file, the file key protecting the file must be unwrapped (or decrypted). The process by which this takes place is as follows: [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
355 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
356 Mr Benson also explains in his first affidavit at [59] to [63] the communications between the AP and the SEP. I note that these paragraphs are footnoted in relation to a number of steps in working document 1 and working document 2. In Mr Benson’s explanation, the AP and SEP communicate over [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] which allows signals to be transmitted between the AP and the SEP; [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
357 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
358 In cross-examination on 20 October 2023, Mr Benson was asked about earlier versions of working document 1 and working document 2. [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. He was challenged as to why the detail included in his oral evidence was not explained in his second affidavit. However, in my view, Mr Benson adequately responded to that challenge by indicating that he considered that his first affidavit included detail regarding [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Having regard to the evidence recited above, I accept that answer.
359 In his seventh affidavit affirmed on 29 October 2023, Dr Dunstone refers to [7(a)] of Mr Benson’s third affidavit and [40], [41] and [60] of Mr Benson’s first affidavit and contends that the tab 1 of exhibit 10 should be amended to incorporate Mr Benson’s evidence in step 18 (of enrolment) and to the associated flowchart, by the inclusion of steps 18(a) to 18(k) marked in green, in order to accurately reflect the role of AKS and SKS in enrolment.
360 CPC challenges Dr Dunstone’s evidence as unfounded assumption not properly based on the evidence of the Apple engineers. However, for the reasons set out above, I do not consider that the criticism advanced to be well founded. It plainly based on the evidence given by Mr Benson in his first affidavit.
361 Nor do I consider that the evidence of Dr Dunstone should not be permitted because it came too late in the proceedings. It is apparent that Dr Dunstone’s seventh affidavit was prepared and filed in response to CPC’s provision of various additional and/or amended materials following the conclusion of oral evidence of the Apple Engineers. The evidence emerges as a response to CPC’s fresh contention as to the dividing line between the transmitter sub-system and the receiver sub-system in the Apple Devices. Further, the evidence upon which Dr Dunstone relied is substantially based on evidence given by Mr Benson in his first affidavit which was filed and served well before he was cross-examined and to which Mr Benson drew attention in his third affidavit. CPC had ample opportunity to cross-examine Mr Benson on his evidence in this respect. Finally, in the circumstances summarised above, in my view the decision in Australian Securities and Investments Commission v Hellicar [2012] HCA 17; (2012) 247 CLR 345 at [165] has no application.
362 Accordingly, in my view the amendments proposed to step 18 of biometric enrolment in working document 1 and the associated flowchart should be included. Having regard to my comments above, by parity of reasoning, I consider that the amendments proposed to step 18 of the biometric matching process detailed in working document 1 and the associated flowchart should also be included.
6. INFRINGEMENT
6.1 Introduction
363 Five issues separate the parties on the question of infringement. CPC contends that all integers of the asserted claims are to be found in the Apple Devices. Apple submits that integers of the asserted claims within which the following terms appear (or are embodied) are absent because the feature so described is not present in the Apple Devices:
(a) controlled item;
(b) transmitter sub-system and receiver sub-system;
(c) accessibility attribute;
(d) the series feature; and
(e) administrator signature.
364 CPC accepts that the question of infringement turns principally on the resolution of the questions of construction addressed in section 4 above. It notes that the critical dispute relevant to all asserted claims concerns whether or not the Apple Devices can be said to have a transmitter sub-system and a receiver sub-system and whether they produce or output an accessibility attribute.
365 In the reasons that follow, I address the arguments concerning construction in the context of the Apple Devices. The parties have substantially addressed their submissions by reference to the iOS Apple Devices (with either face ID or touch ID) (exemplar categories 1 and 3) described in working document 1, concluding their infringement submissions separately by short references to matters relevant to the MacOS devices with touch ID (exemplar category 2), iOS Apple Devices used in conjunction with the Apple Watch (exemplar category 4) and MacOS devices used in conjunction with the Magic Keyboard (exemplar category 5). Little turns on the differences between the various devices (and whether they are used with or without accessories), and the infringement issues can substantially be addressed by reference to the biometric enrolment and matching processes of iOS Apple Devices (without accessories) as described in working document 1. Similarly, little turns on the differences identified in working document 2 insofar as they concern obtaining access to 1st and 3rd party applications once access has been gained to an Apple Device, or those differences in working document 2 insofar as they concern access to the Apple Wallet. Where relevant, they are mentioned in the section that follows.
6.2 Controlled item (and conditional access to the controlled item)
366 I have in section 4.3 above addressed the debate between the parties concerning the meaning of the term “controlled item” in the context of the asserted claims. I have concluded that “a controlled item” as that term is used in the asserted claims must be understood to refer to the item to which access is granted or refused dependent on and following the provision of an accessibility attribute. I have rejected the argument advanced by CPC that a controlled item may be more than a single discrete item to be accessed and can include multiple sub-items, which require additional authentication to access.
367 It is clear from the parties’ submissions that the infringement dispute between them concerns only the asserted claims of the 293 patent which requires not only a “controlled item” but a “means for providing conditional access to the controlled item dependent upon” the information conveyed by the secure access signal.
368 To understand this point in context, I reproduce the claim 1 of the 293 patent below, there being no suggestion that a different construction of integer (13) is available for any of the other asserted claims:
(1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction; (9) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (10) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; (11) said system further comprising: a receiver sub-system comprising; (12) means for receiving the transmitted secure access signal; and (13) means for providing conditional access to the controlled item dependent upon said information.
(emphasis added)
6.2.1 The submissions
369 CPC contends in its position statement that each of the following is a controlled item in relation to an Apple Device:
(a) the Apple Device itself;
(b) any one or more of the applications on the Apple Device which are accessible when the Apple Device is unlocked; and
(c) any accessory to the Apple Device, such as the Apple Watch, which is accessible when the Apple Device is unlocked via the system.
370 CPC submits that a controlled item may have different components, including components that require further authentication for access, which then form part of the conditional access granted. Accordingly, accessing 1st and 3rd party applications, or Apple Wallet, does not involve separate items that are not part of the Apple Device. Nor is it correct, CPC submits, to distinguish “unlocking” an Apple Device from those two scenarios, on the basis that “unlocking” grants a form of access to the device whereas the other two scenarios do not. CPC submits that, properly characterised, each scenario involves a form of access to the device subject to particular conditions as to the functionality on the device which is made accessible. As a result, CPC submits that the acts of unlocking an Apple Device, accessing 1st and 3rd party applications and accessing Apple Wallet, each reflect particular conditions of access granted to the user of the Apple Device, being the controlled item. This, it submits, is consistent with the way that a user interacts with the device, namely by using the same touch ID or face ID authentication process in each case which produces a form of access that permits certain applications or functions on the device to be used.
371 Apple does not argue that the asserted claims of the 168 patent are not infringed by reason of the absence of integers containing “a controlled item”. However, it contends that neither face ID nor touch ID within the Apple Devices grants “conditional access” to any “controlled item” dependent upon information conveyed by any secure access signal as required by each of the asserted claims of the 293 patent. Rather, they involve a biometric authentication process, resulting in either the grant or denial of unconditional access in every case. Apple contends that there is never any “condition imposed upon the relevant access”.
6.2.2 Consideration
372 My conclusion in relation to the proper meaning of “a controlled item” in the context of the claims, including claim 1 of the 293 patent, is largely determinative of this issue.
373 Within the structure of that claim, the system for providing secure access to a controlled item includes a transmitter sub-system that can (amongst other things) output an accessibility attribute upon authenticated matching (integer (9) and emit a secure access signal conveying information dependent upon the accessibility attribute (integer (10)). The system must also have a receiver sub-system that includes “means for providing conditional access to the controlled item dependent upon said information” (integer (13)).
374 As I have found, the “controlled item” is that which may be accessed by using the system described by the claim. In the case of the Apple Devices, the use of the touch ID or face ID functionality leads to the opening of the home screen, as working document 1 describes by reference to step 30 of the biometric matching process. The question of whether or not “conditional access” is granted to the controlled item depends on the terms upon which access is granted to the opening of (here) the home screen. It is not answered by reference to whether other components of the Apple Device require further authentication for access. That is because those further components are not the controlled item within the claim.
375 On this basis, whilst I accept that the home screen of each of the Apple Devices is a “controlled item”, I reject the submission advanced by CPC that the Apple Device itself (as a whole) is a controlled item within the meaning of the asserted claims.
376 It follows that I also reject the submission that access sought and granted to the Apple Device can take one of three forms, each of which is a form of conditional access to that device which involves particular functionality on the device being made available. Access to the home screen (and unrestricted applications) is one form of conditional access and different forms of conditional access arise in relation to accessing 1st and 3rd party applications and Apple Wallet, which may require additional authentication. The argument advanced by CPC is to the effect that the access granted is conditional access because in each of these three scenarios “the user gets access to the device subject to conditions which relate to the functionality that’s being accessed. It doesn’t give access to all the functionality on the phone in any scenario…only particular functionality. And therefore it is conditional”. In my view, this argument represents a drift in focus from the language of the asserted claims which requires attention upon the identity of the controlled item.
377 Furthermore, integer (13) requires that the receiver sub-system have means for providing conditional access to the controlled item “dependent upon” the information conveyed by the secure access signal (which is dependent upon the accessibility attribute). CPC’s construction does not explain how access to the Apple Device as a whole (had I accepted its definition of “controlled item”) could be so dependent.
378 Accordingly, CPC fails in this argument.
6.3 Transmitter sub-system and receiver sub-system
379 Each of the asserted claims contains a transmitter sub-system integer and most also include a receiver sub-system integer. The claims provide different levels of detail as to what is required, with claim 1 of the 168 patent being the broadest.
380 I have considered the construction of the asserted claims in section 4 above, and the meaning of “transmitter sub-system” and “receiver sub-system” in section 4.5. In that section I found that there must be a functional relationship between the transmitter sub-system and receiver sub-system and that each must be separately identifiable and distinct, rejecting CPC’s submission that they may overlap with each other. I have found that the language of the claims is such that there must be a flow of information from the transmitter sub-system to the receiver sub-system. I have rejected the submission that each sub-system may be characterised by reference to “key” or “quintessential” components, or that the boundaries between such sub-systems can be drawn where an expert thinks it “makes sense”.
6.3.1 The submissions
381 CPC submits that as a matter of construction the transmitter sub-system and receiver sub-system are not pre-defined subsystems of physically separate or finite hardware or software components. Rather, they are defined by the functionalities required by each claim and will include the “key” or “quintessential” hardware and/or software components required for effecting those functionalities, but not components ancillary or incidental to achieving those functionalities. Further, the transmitter sub-system and receiver sub-system may, as a matter of construction, comprise overlapping hardware and software components. Notwithstanding this view, CPC contends that the question of overlapping components does not arise in the present case.
382 In relation to the component parts of the transmitter sub-system, CPC advances its submissions by reference to abbreviations that substitute for particular integers in the asserted claims, the word “enrolment”, substituting for those integers in the asserted claims that address the enrolment function of the transmitter sub-system, “matching” as an abbreviation for those integers that concern the matching of a biometric signal against members of a database in the transmitter sub-system to output an accessibility attribute, and “emitting a secure access signal” as an abbreviation for those integers that involve the transmission of a signal if a legitimate biometric signal is received.
383 CPC submits that the transmitter sub-system in the Apple Devices is comprised of those components responsible for enrolling, matching and emitting a secure access signal. Those components are: (a) SBIO / [redacted]; (b) SKS; and, where the claim relevantly requires, (c) the face ID or touch ID sensor. Save for the [redacted] [redacted], each of these components resides within the SEP.
384 CPC submits that the receiver sub-system in the Apple Devices is comprised of those components within the AP responsible for receiving the accessibility attribute or secure access signal from the SEP and providing access to the controlled item dependent upon said information. [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
385 CPC submits that because these identified components are key or quintessential to the performance of the functions required by the claims, they respectively form the transmitter sub-system and receiver sub-system, such that the sub-systems are separate and discrete.
386 Apple submits that the Apple Devices take a different approach to secure access to that disclosed and claimed by the patents. The iOS Apple Devices are each a single physical device which grants access to itself (rather than access to a remote item). On that basis, the Apple Devices are not required to overcome the “weak point” in the communication of information that is addressed by the patents because the devices do not require an access signal to be sent over a distance. Instead, the Apple Devices deal with the issue of insecure storage of biometric data. They do so by using integrated biometric security systems protected by layers of cryptographic keys [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. As such, there is no involvement of any discernible transmitter sub-system or receiver sub-system, which the patents require for the secure processing and provision of biometric data for the purpose of secure access.
387 Apple contends that CPC’s case is not supported by the expert evidence. It submits that Associate Professor Boztas, during the course of his evidence, identified at least four different variants of the transmitter sub-system and receiver sub-system. However, none of those variations bear resemblance to CPC’s final submitted characterisation of the respective sub-systems, which Apple considers results in neither the transmitter sub-system nor the receiver sub-system being capable of performing the functions of any of the asserted claims, because it says that the components excluded by CPC as “ancillary” are in fact essential to the performance of the functions required by the asserted claims. Apple further challenges CPC’s use of the “quintessential” or “ancillary” criteria as a means by which software and hardware components of the Apple Devices are selected for inclusion in or exclusion from the transmitter or receiver sub-system and submits that such an approach is not supported by the patents or asserted claims. CPC’s approach wrongly seeks to exclude SKS from the receiver sub-system, which, Apple submits, is incoherent.
6.3.2 Consideration
388 CPC first puts its case on the basis that the sub-systems of the claims need not be physically separate from each other or comprised of finite hardware or software components but are defined by the functionalities required by each claim. I have rejected that argument as a matter of construction. CPC also contends that the sub-systems may comprise overlapping hardware and software components, however, CPC considers that a finding in its favour on this point is no longer essential. Instead, CPC suggests that when one looks at the Apple Devices and properly characterises the key components involved in the relevant functionalities for each sub-system, they are in fact distinct components that do not overlap and reside in separate parts of the devices. For this argument to succeed, CPC relies on the notion that the claims permit the transmitter sub-system and receiver sub-system to be identified by reference to what it characterises as those parts of the sub-system that are “key” or “quintessential” to the functions involved. Although I have rejected this argument as a matter of construction, I consider it below in the context of the factual matters relied upon by CPC.
389 For ease of exposition, I deal with this issue by reference to claim 5 of the 168 patent, which contains the integers of the transmitter sub-system and receiver sub-system to which the parties refer in their submissions.
390 Claim 5 of the 168 provides:
(1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute; (6) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; and (7) means for enrolling biometric signatures into the database; (8) and a receiver sub-system comprising; (9) means for receiving the transmitted secure access signal; and (10) means for providing access to the controlled item dependent upon said information.
(Emphasis added)
391 In respect of the transmitter sub-system, it is convenient first to consider integer (7) of claim 5 of the 168 patent which refers to the enrolment function. It will be recalled that the process of enrolment is described in steps 1 to 19 of working document 1 (see section 5.5 above).
392 CPC contends that the “quintessential” steps for enrolment are steps 12 to 14 in working document 1 [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. The other components are not key components involved in enrolment and do not form part of the transmitter sub-system. This represents a change in position on the part of CPC, which in its integer breakdown and position statement identified each of steps 1 to 19, and the components identified within those steps, as relevant to enrolment.
393 In support of its submission, CPC cites a passage of evidence where Associate Professor Boztas and Dr Dunstone agreed with a proposition put to them that steps 12 to 14 are “quintessential” to the enrolment process. However, for the following reasons I am unable to accept that the expert evidence supports CPC’s position.
394 First, neither expert was asked to consider the question of what comprised the “quintessential” or “key” components of the transmitter sub-system within the patents or the claims or whether the Apple Device met the enrolment integer by reference to steps 12 to 14. They were simply asked whether steps 12 to 14 were “quintessential” or “key” to the enrolment process.
395 Secondly, Dr Dunstone pointed out in his answer that “any part of the enrolment process is important” in the sense that all steps are required to give effect to enrolment and accepted only that in terms of the [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] then steps 12 to 14 are the key steps.
396 Thirdly, Associate Professor Boztas gave evidence that insofar as it concerned enrolment, the transmitter sub-system should be identified to be everything within steps 1 to 18, and possibly the NAND flash storage / DRAM within step 19:
ASSOC PROF BOZTAS: So, yes, I will need a little more time to check with the matching. So, I believe for the enrolment, the exact point at which the [transmitted sub-system] terminates for enrolment would be 18, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. And, in comparison, if you look at the matching, at some point with the matching – I mean, initially these steps are parallel, so let me just clarify what I’m saying.
HIS HONOUR: So, the transmission subsystem – transmitter subsystem is all of steps 1 through to 18, and it finishes at 18.
ASSOC PROF BOZTAS: Yes. And again, I mean – because everything goes through the [redacted] [redacted], it’s a little bit arbitrary where you terminate it, whether before the last pass through the [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. It really makes not that much functional difference.
397 Fourthly, working document 1, a document largely agreed to be accurate by the parties, indicates that the enrolment process engages each of the components identified in steps 1 to19 (and depicted in the accompanying flowchart), which includes components in both the AP and the SEP. As such, the enrolment process is described by reference to parts of the Apple Devices that CPC characterises as the separate receiver sub-system, being select components within the AP.
398 It is difficult to discern a rationale to justify why the transmitter sub-system does not include each of the components identified in working document 1 as relevant to enrolment, as opposed to only SBIO / [redacted] other than the fact that it is convenient to the CPC case to draw this point of distinction.
399 Fifthly, in my view, the characterisation of a transmitter sub-system by reference to its “key” or “quintessential” parts gives an amorphous and arbitrary character to the sub-system that I do not consider meets the requirement of the claim.
400 Taking biometric enrolment as an example, steps 1 to 19 define the process of biometric enrolment. Each step is necessary for enrolment to take place. This cannot be in dispute, having regard to the content of the agreed components of working document 1. That view is supported by the evidence of both experts.
401 Integer (5) deals with matching (including the provision of an accessibility attribute). The process of biometric matching within the Apple Devices is described in section 5.6 above, by reference to steps 1 to 30 in working document 1 (for access to the home screen), steps A1 to A29 in working document 2 (in relation to 1st and 3rd party applications) and steps W1 to W26 in working document 2 (in relation to Apple Wallet). The arguments advanced can be addressed by reference to steps 1 to 30 of working document 1 as no different conclusion arises from consideration of the other steps.
402 CPC submits that the steps quintessential to the matching process are steps 19 and 20 which are also managed by the SBIO / [redacted]. It submits that this is the only component involved in (and capable of) [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. CPC contends that within the matching integer, the determination of whether access should be granted, which concerns the accessibility attribute, is managed by [redacted] [redacted] at step 20. CPC’s closing submissions may be contrasted with its integer breakdown, which notes that an accessibility attribute is provided by one or more of the steps identified in working document 1 from the return of the positive biometric match by [redacted] [redacted] (step 20) up to and including step 28.
403 In support of its contention, CPC relies on evidence from the experts that steps 19 and 20 are managed by the [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. For the following reasons I reject the argument advanced by CPC.
404 First, in the passage cited by CPC in support of their content, the experts were not considering the question of the components of the transmitter sub-system or their bearing on the construction of the claims. The agreement given by Dr Dunstone, adopted by Associate Professor Boztas, was that those steps were the “key steps” but “not… the only steps” in the matching process and that step 20 is the point at which a positive match result is generated. Neither were addressing the claims of the patents, the meaning of the words transmitter sub-system and receiver sub-system or considering whether functions to which attention was being directed read onto the claims.
405 Secondly, the evidence of Associate Professor Boztas as a whole does not support the position advanced by CPC. In his first affidavit he considered that the matching process involved each of the components involved in the steps he identifies, which largely correlates with each of the steps in working document 1 up to and including step 20, which results in a positive match being returned by [redacted] [redacted] [redacted]. This was a position that Associate Professor Boztas maintained in all of his affidavit evidence.
406 Associate Professor Boztas, when considering the identity of the transmitter sub-system more generally, gave the following evidence in concurrent session, referring to the steps for biometric matching detailed in the working document 1:
ASSOC PROF BOZTAS: - - - 27 and so on. The reason for that is the encrypted processing has to happen inside the SEP. So there is a difference between the division into transmitter and receiver subsystem in terms of the sequence of events as – and – in terms of the components that take part in it. So maybe if I could try and explain it this way. So 21 was TSS. And then the transition from 21 to 22, we cross TSS to RSS. And, when we come back, the two ends of 27 at the bottom, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted], you could put as being part of RSS. But, once you come back to the SEP to continue that processing before going back out again, you’re inside the TSS again.
HIS HONOUR: So it – the way you’re describing that, the TSS is a physical – it’s a location from where things are sent; is that right?
ASSOC PROF BOZTAS: It’s not just the physical component but it’s – we can say that certain parts of the physical division, of the physical components, are – play a part in the TSS.
HIS HONOUR: So does that mean that – I’m just a bit curious about line 27 when it goes back into the Secure Enclave. There’s – is that a transmission that’s taking place, transmission 27?
ASSOC PROF BOZTAS: Well, there is a communication taking place.
HIS HONOUR: So is that a transmission from the receiver - - -
ASSOC PROF BOZTAS: RSS back to the TSS.
HIS HONOUR: So it perform[s] both reception and transmission function?
ASSOC PROF BOZTAS: Yes, yes.
HIS HONOUR: Okay. And did I – and what about line 28, that’s – is that a - - -
ASSOC PROF BOZTAS: No, that’s a transmission back.
HIS HONOUR: That’s – so that’s a transmission subsystem that’s doing that?
ASSOC PROF BOZTAS: Yes, back to the receiver subsystem.
HIS HONOUR: So the final version of – or final event from the TSS is line 28 or line 29?
ASSOC PROF BOZTAS: I would say 28.
HIS HONOUR: So line 29 is an example – is that a – is that emanating from the receiver subsystem?
ASSOC PROF BOZTAS: Yes.
407 It may be seen that by the time of his oral evidence, whilst Associate Professor Boztas had a fairly confusing view as to the identity of the transmitter sub-system and its relationship with the receiver sub-system, he did not share the view that CPC now adopts, that the “matching” integer resides solely in steps 19 and 20 or that the relevant components are [redacted] [redacted]. Nor did Dr Dunstone give evidence that supports CPC’s approach.
408 Indeed, as Apple convincingly demonstrated in cross examination, Associate Professor Boztas repeatedly changed his position during the course of his oral evidence as to what components were within the transmitter sub-system and receiver sub-system within the claims, having identified at least four different variants. None of Associate Professor Boztas’ opinions as to the components of the transmitter sub-system and receiver sub-system have been adopted as the construction now favoured by CPC and I have not been asked to consider their veracity. As such, it is unnecessary to traverse these.
409 CPC submits that its changing position, and the changing evidence of Associate Professor Boztas arose because of the oral evidence of the Apple Engineers given in cross examination, which contained significant detail absent from their affidavit evidence. In the present context, I do not accept that submission. Most of the evidence of Associate Professor Boztas in relation to the operation of the Apple Devices did not alter as a result of the oral evidence given by the Apple engineers. The consistent evidence of Dr Dunstone was that there is no identifiable transmitter sub-system or receiver sub-system within the Apple Devices.
410 Furthermore, there is a logical fallacy in seeking to justify changing approaches to the construction of the claims by reference to further disclosures as to the operation of the impugned product. Doing so pointedly suggests that the construction advanced by CPC is with an eye to the infringing article, an approach that has repeatedly been abhorred by the authorities, construction being a matter that should be objectively determined on the basis of the disclosure of the patent, read through the eyes of the person skilled in the art in the light of the common general knowledge; CCOM Pty Ltd v Jiejing Pty Ltd [1994] FCA 396; (1994) 51 FCR 260 at 267–268 (Spender, Gummow and Heerey JJ); Hanwha at [92] (Burley J).
411 Turning from the transmitter sub-system to the receiver sub-system, CPC submits that, for the claims that include a receiver sub-system, the sub-system (in iOS Apple Devices when accessing the home screen) consists of [redacted] [redacted] [redacted] [redacted] [redacted] being the key components within the AP responsible for receiving the accessibility attribute or secure access signal from the SEP and providing access to the controlled item dependent upon said information. In the case of 1st and 3rd party applications it contends the receiver sub-system consists of [redacted] [redacted] [redacted] [redacted] and in the case of the Apple Wallet, [redacted] [redacted] [redacted] [redacted] [redacted]. It is again sufficient to consider to the arguments by reference to the steps for accessing the home screen in iOS Apple Devices.
412 I consider that there is an arbitrariness to CPC’s delineation of the receiver sub-system that is not supported by the evidence. Two examples suffice to demonstrate the point.
413 The first is by reference to the role of [redacted]. In respect of biometric enrolment, [redacted] is identified as playing a role in relation to steps 10, 11, 15 and 16. In respect of biometric matching, [redacted] is identified as playing a role in relation to steps 16, 22, 27 and 28.
414 CPC submits that [redacted] forms part of the receiver sub-system, identifying it as “quintessential” or “key” to that sub-system on the basis that it is [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. However, CPC does not identify [redacted] as forming part of the transmitter sub-system, despite working document 1 describing, by steps 15 and 16 (for biometric enrolment) and step 16 (biometric matching), [redacted] performing the same function as that which CPC identifies it performing in the receiver sub-system. Associate Professor Boztas included [redacted] as a component of both the transmitter sub-system and the receiver sub-system.
415 The second is by reference to CPC’s inclusion of SKS in the transmitter sub-system and omission from the receiver sub-system. Apple contends that this is incoherent and points to the agreement of the experts that [redacted] has a role to play in the decryption processes required for matching and unlocking of an Apple Device. This contention is to be considered in light of my factual findings as to the role of [redacted] and [redacted] in the encryption and decryption of templates at section 5.7.2 (above) from which it is clear that [redacted] is engaged in the process of encryption and also decryption. In his oral evidence, Associate Professor Boztas accepted that in order to obtain access to an Apple Device, it is necessary for [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
416 Integer (10) of claim 5 of the 168 patent provides that the receiver sub-system includes “means for providing access to the controlled item dependent upon said information”. All of the asserted claims (save for claims 27, 29 and 37 which do not contain a requirement for a receiver sub-system) require the receiver sub-system (not the transmitter sub-system) to provide access to the controlled item. I accept the submission advanced by Apple that no logically probative explanation has been advanced by CPC for why it considers that the SKS does not form part of the receiver sub-system as a component required to provide access to the controlled item.
417 Having regard to the above, I reject the characterisation of the transmitter sub-system and receiver sub-system put forward by CPC. These matters similarly inform my conclusion that CPC has not established that the Apple Devices have within them either a transmitter sub-system or a receiver sub-system as required by the claims.
418 In conclusion, two further points may be made.
419 First, there is no support in the claims for the notion that a transmitter sub-system or a receiver sub-system may be characterised by reference to “quintessential” or “key” components. The experts agreed understanding of a “sub-system” (as set out in JER1 and extracted in section 4.5.2 above) is that it is a component of a larger system that typically performs a specific function within the context of the larger system.
420 Apple further submits that the specification teaches against the approach adopted by CPC. In this regard, it draws attention to figure 2, which it says expressly identifies certain components within the separately defined transmitter sub-system and receiver sub-system. Within the transmitter sub-system is a code entry module (103), and within that an audio transducer (124) and LED indicators (122). Apple submits that none of these might be characterised as quintessential to enrolment or matching and yet they are expressly identified as forming part of the transmitter sub-system. From this, one may consider that the patentee did not choose in that embodiment to separate out quintessential components from less important components in the sub-system. I accept that this gives some flavour to the proposition that the specification does not support the approach adopted by CPC, although of itself it is no more than somewhat indicative.
421 Secondly, by excluding components considered to be “ancillary”, the asserted sub-system-system is not functional in a manner that is consistent with the meaning of a “sub-system”. For instance, having regard to the biometric enrolment and biometric matching flowcharts, CPC excludes from the transmitter sub-system all components involved in those processes that reside within the AP. Yet none of the functions of enrolment, matching or emitting could take place without those components, as the evidence of the experts made clear – see the evidence of Associate Professor Boztas extracted above at [396] as one of several examples. The fact is, and I find, that each component contained in working document 1 is necessary for the performance of the functions specified.
422 In an annexure to its closing submissions, Apple lists 15 components that, by reason of its approach, CPC has excluded from either the transmitter sub-system or the receiver sub-system. One such software component is [redacted] [redacted] which is involved in step 2 of the enrolment process. Yet the agreed description of step 2 of biometric enrolment contained in working document 1 provides that this component initiates the biometric enrolment process.
423 Another software component is AppleMesaSEPDriver or [redacted] (for touch ID or face ID respectively), which in step 6 of the biometric enrolment process activates the sensors required for enrolment. As I have found in section 5.7.1 above AppleMesaSEPDriver, during step 5 of biometric enrolment, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
424 Both are examples of components that are significant in the operation of the Apple Devices that are excluded by CPC.
425 Having regard to the foregoing, it is my view that CPC has failed to identify a coherent basis upon which it may be concluded that there exists any separate transmitter sub-system or receiver sub-system within the Apple Devices. As the detailed review above indicates, CPC’s attempt to describe such sub-systems by reference to key or quintessential components fails. CPC has abandoned reliance on the evidence of Associate Professor Boztas in this regard, who made several attempts – different to those of CPC – to identify the transmitter sub-system and receiver sub-system within the Apple Devices
426 Although the matters addressed above were submitted on in respect of iOS Apple Devices without accessories (exemplar categories 1 and 3), they apply equally to MacOS Apple Devices without accessories (exemplar category 2). In any event, CPC did not contend that its infringement analysis differed in relation to exemplar categories 2, 4 and 5. However, CPC noted that in respect of exemplar category 4, the “emitting” integer (explained by reference to integer (6) of claim 5 of the 168 patent) is met by step 28B of the biometric matching process.
427 Apple largely relied on its submissions in respect of infringement for all exemplar categories but made some additional submissions in respect of Apple Devices in exemplar categories 4 and 5. However, having regard to the conclusions that I have reached it is unnecessary to address those further.
428 Having regard to my conclusions set out above and given that all of the asserted claims include a transmitter sub-system and a majority also include a receiver sub-system, CPC’s infringement case must fail.
6.4 Accessibility attribute
429 In section 4.4 above, I have construed the term "accessibility attribute” within the context of the claims in which it appears. I have found that an “accessibility attribute” is something that is provided or output by the transmitter sub-system in response to the receipt of a legitimate biometric signal or authentication of the biometric signature (i.e. a successful biometric match) and must establish whether and under which conditions access to the controlled item should be granted.
6.4.1 The submissions
430 CPC submits that in the case of the Apple Devices, for all asserted claims other than claims 2 and 3 of the 168 patent, the output or provision of an accessibility attribute occurs in [redacted] [redacted]. It submits that following a positive match, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
431 CPC submits that in each case, steps 20, A20 and W20 contain content that is referable to the type of access that is to be granted and that in each case the accessibility attribute is output or provided by the same component in the [redacted] [redacted] [redacted] [redacted] and differs depending on which condition of access is granted. It is these steps in and of themselves, which CPC submits equates to the output or provision of an accessibility attribute.
432 Alternatively, CPC submits that it is possible to deem the provision of the accessibility attribute as continuing from: step 20 up to and including step 28 (in the case of the home screen and unrestricted 1st and 3rd party applications); step A20 up to and including step A26 (in the case of restricted 1st and 3rd party applications); and step W20 up to and including step W24 / W25 (in the case of Apple Wallet).
433 In the case of claims 2 and 3 of the 168 patent, CPC contends that the provision of the accessibility attribute occurs at steps 20, A20 and W20 and continues to steps 28, A26 and W24 / W25. That is because, for those claims, the accessibility attribute must be received by the receiver sub-system. In the alternative, it submits that the accessibility attribute for those claims may be limited to steps 28, A26 and W24 / W25.
434 Apple submits that the alleged accessibility attribute in the Apple Devices, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] do not establish whether and under which conditions access is granted to any controlled item. Rather, they are involved in granting binary access to different items. In each case, the only determination made is whether access is to be granted to a particular item to which a user has sought access, and no conditions are imposed – or able to be imposed – upon access to that item.
435 Apple makes several points in support of its argument. First, it challenges the consistency of the evidence of Associate Professor Boztas, whose evidence identifying an accessibility attribute within the Apple Devices varied. Apple goes on to say that each of the variations identified by Associate Professor Boztas should be rejected for reasons including that they are not supported by the language of the claims. Secondly, it submits that the outcome of the biometric authentication process is binary, such that a biometric signal will either be authenticated (and the user will be granted access to the Apple Device) or not. As such, the [redacted] [redacted] [redacted] [redacted] do not establish any conditions of access. Thirdly, it submits that the requirement that a user undertake a separate authentication process to obtain access to [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] is in the nature of a “pre-condition” on access to a particular controlled item that is not imposed in response to biometric authentication required for access to the Apple Device itself, but exists independently in the data security architecture in the Apple Devices. Finally, Apple also criticises CPC’s alternative submission, that the provision of the accessibility attribute may be understood as a range of steps, as unclear.
6.4.2 Consideration
436 In section 4.4 above, I have found that it is apparent from the claim language that the step of matching a biometric signature and conveying a match will not of itself amount to an accessibility attribute. The asserted claims generally require an accessibility attribute to be provided only in response to the receipt of a “legitimate” or “authenticated” biometric signal. In other words, after a positive biometric match, the transmitter sub-system must provide or output an accessibility attribute that conveys the information (“establishes”) of whether and under which conditions access to the controlled item should be granted to a user.
437 As noted, CPC contends that the accessibility attribute is the result of the operations of [redacted] [redacted] [redacted]. Following the positive match, they do one of three things depending on which scenario one considers. First, for accessing the home screen of Apple Devices, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Secondly, in the case of access to restricted 1st and 3rd party applications, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Thirdly, in the case of Apple Wallet, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. These are steps 20, A20 and W20 respectively.
438 Significantly, CPC contends that, considered cumulatively, these three options are determining not only whether access should be granted but are each subject to different conditions.
439 Senior counsel for CPC properly accepted in argument that this approach to infringement depends on the resolution of the argument as to the identity of the controlled item the subject of the claims. It is therefore dependent upon the success of the argument advanced by CPC to the effect that the controlled item is the Apple Device as a whole. In such a situation, CPC submits, access granted to the Apple Device can take one of three forms, each of which is a form of conditional access to that device which involves particular functionality on the device being made available. Accordingly, the accessibility attribute is made to a different software component depending on which scenario applies.
440 However, I have rejected that argument. The consequence is that the outcome of the receipt of a legitimate biometric signal must be an accessibility attribute that provides for access to the controlled item within the meaning of the asserted claims. In the case of the Apple Devices, that is the lock screen, not the device as a whole. Obtaining access to the restricted 1st and 3rd party applications or Apple Wallet will require further authentication. For this reason alone, CPC’s argument concerning the presence of the accessibility attribute must fail.
441 However, turning now to the mechanics within the Apple Devices, I will further address CPC’s contention by reference to step 20 in the biometric matching process to access the home screen, which is:
[redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
(Emphasis added)
The equivalent steps A20 and W20 for 1st and 3rd party applications and Apple Wallet, respectively, are materially the same.
442 In this instance, [redacted] [redacted] [redacted] (in the case of touch ID or face ID, respectively) undertakes a binary assessment of determining whether there is a positive biometric match i.e. whether the [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. In response to a positive match result, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. Here, as well as for each of steps A20 and W20, the [redacted] [redacted] [redacted] [redacted] that is output will only determine whether access is to be granted to the item to which the user seeks access. As such, [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] output or communicated by [redacted] [redacted] in steps 20, A20 and W20 does not establish whether and under which conditions access to the controlled item is granted.
443 CPC’s alternative case is that the output or provision of the accessibility attribute continues from step 20 (A20 or W20) up to and including step 28 (A26 or W25 / W25). However, it points to no aspect of these additional steps that gives rise to any separate consideration that is applicable. Indeed, the submission advanced is that if the accessibility attribute is logically present in step 20, it is also logically present in the steps that follow based on the same condition. This argument must accordingly be rejected for the same reasons.
444 Accordingly, the infringement case advanced by CPC also fails because it has not established that the Apple Devices contain an “accessibility attribute” within the meaning of the asserted claims.
6.5 Series feature
445 Each of the asserted claims of the 293 patent require that the series feature be present. By reference to claim 1 of the 293 patent (extracted below), the requirements of the series feature is set out in integers (6) to (8). The parties accept that there is no material variation between the asserted claims of the 293 patent in this respect.
(1) A system for providing secure access to a controlled item, the system comprising: (2) a database of biometric signatures; (3) a transmitter subsystem comprising: (4) a biometric sensor for receiving a biometric signal; (5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction; (9) means for matching the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; and (10) means for emitting a secure access signal conveying information dependent upon said accessibility attribute; (11) said system further comprising: a receiver sub-system comprising; (12) means for receiving the transmitted secure access signal; and (13) means for providing conditional access to the controlled item dependent upon said information.
(Emphasis added)
6.5.1 The submissions
446 CPC submits that the series feature requires: (a) capturing multiple scans or images of a finger, where the finger has to be held on the sensor for long enough to obtain a scan; and (b) mapping those scans / images into a single mathematical representation, which is then saved in the database as a biometric signature according to the mathematical representation. It submits that in both touch ID and face ID enrolment processes of the Apple Devices, multiple images are taken of the finger or face. The software of the Apple Devices is coded to direct that those images be taken and converted into a single mathematical representation or template which is enrolled in a database as a template for comparison purposes during matching. Although there is no fixed number of times or period of time that the user is required to touch their finger to present their face in order to produce the necessary images in the enrolment process, the practical consequence of the enrolment algorithms is that the finger or face must be presented a minimum number of times and for a minimum amount of time in order to obtain sufficient quality images that can be mapped into a mathematical representation and template. CPC submits that, on the proper construction of the claims, the duration and number of entries of the biometric signal do not need to be pre-determined; and the claims do not require that the biometric signatures in the database be defined by reference to any number or duration.
447 In what CPC characterised as an alternative argument, it submits that if there is a requirement in the asserted claims for some predetermined value for the number of scans required and the duration of each scan for touch ID or face ID, then the evidence regarding the operation of the Apple Devices supports that conclusion that such a requirement would be satisfied at least by the Apple Devices with face ID.
448 Apple submits that, on the basis of the proper construction of the series feature, the Apple Devices do not contain the integers asserted.
6.5.2 Consideration
449 I have in section 4.9 rejected the submission advanced by CPC that the series feature must be understood as being for the purpose of obtaining a quality biometric signature. I have also rejected the contention that it requires capturing multiple scans or images and mapping those scans or images into a single mathematical representation which is then saved in the database as a biometric signature according to the mathematical representation. Rather, the asserted claims set out in stepwise fashion the requirements of a system. Whether or not the Apple Devices meets those requirements depends on what the impugned devices do.
450 CPC accepts that in the Apple Devices, there is no fixed number of times or period of time that the user is required to touch their finger or present their face in order to produce the necessary images in the enrolment process. Yet the requirement of integer (6) is that there be means for receiving a series of entries characterised by the number of entries and/or duration of each such entry. Put another way, the series of entries is defined by a specified number of entries or a specified duration of each entry (or both). This series of entries must be mapped onto an “instruction” according to integer (7), which, I have found, must be pre-existing within the system.
451 In relation to face ID within the iOS Apple Devices, Ms Wells gave evidence that during enrolment, the user is directed to move their head around in a circular motion, during which time, 2D and 3D images of the user’s face were captured at various angles. These images are then sorted into nine pre-determined “bins” which correspond to the different angels of the face. Ms Wells indicated that [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. CPC relies on the following passage of evidence given by Ms Wells during cross-examination:
And is it right that the system is set up so that the user needs to keep looking at the camera with their face in the appropriate orientation for a sufficient time to enable those images to be captured so as to create those feature vectors? [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted].
452 In relation to touch ID within the iOS Apple Devices, Mr Kostka’s evidence was that multiple images are of a user’s fingerprint are captured by the touch ID sensor [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted] [redacted]. He says that whilst there is no minimum amount of time required by the Apple Devices for a user to press their finger on the sensor, a user must touch the sensor for long enough for an image to be captured and if the sensor is not touched for long enough, no image will be captured.
453 For both touch ID and face ID systems, the evidence indicates that the Apple Devices must capture an image of sufficient quality to enable enrolment to take place. It is this evidence that forms the basis of the submission advanced by CPC. However, the series feature, by its language, does not prescribe that enrolment take place by reference to the result to be achieved (such as the quality of the image) but rather it prescribes that enrolment take place by reference to the requirements of the particular steps identified in the asserted claims. As CPC has not established that those steps are taken within the Apple Devices, this aspect of its infringement case must fail.
6.6 Administrator signature
454 Apple disputes that claims 3 and 6 of the 168 patent and claims 29 and 41 of the 293 patent are infringed by any of the Apple Devices because they do not have the features required by the “administrator signature” integer (or its equivalent in the case of claim 29 of the 293 patent).
6.6.1 The submissions
455 CPC submits that an administrator is an individual with special privileges to manage and oversee the system, network or an application and that the asserted claims do not require the signature to be specifically tagged in the database as an administrator signature. It contends that it is sufficient that the signature is enrolled and that it is, in fact, the signature of an administrator. CPC goes on to say that the first enrolled user of an Apple Device can be an administrator by reason of their power to control the system. Accordingly, CPC submits that the Apple Devices have an “administrator signature” within the meaning of the asserted claims. In support of this contention, CPC points to the following features:
(a) all of the Apple Devices have a means for determining if the database of biometric signatures is empty; and
(b) for iOS Apple Devices, when the first user enrols their biometric signature using face ID or touch ID they are required to enter a passcode or set up a passcode. After doing so, the first enrolled user can enrol another user by using touch ID or face ID to access the home screen and the settings app, accessing the face ID and passcode settings folder and then entering their passcode. The first enrolled user may also delete other users by a similar process.
456 CPC submits that because these steps cannot be undertaken by anyone other than the first enrolled user who has the passcode, the holder of the passcode is in a unique position and is the only user who can manage the device, including by enrolling additional users or deleting their biometric signatures from the database.
6.6.2 Consideration
457 For the reasons given in section 4.8 above, in my view, an “administrator signature” within the meaning of the asserted claims is not a reference to a signature enrolled in the database belonging to a person designated as an administrator, but rather the signature stored in the database that is recognised by the system as conferring administrator privileges on the person to whom the signature belongs. It is not enough that a person have the ability to perform administrative functions by virtue of being in possession of an enrolled signature and a passcode, rather, their signature must be recognised as an “administrator” by the system.
458 During enrolment the Apple Devices do not store the biometric signal received as an administrator signature. There is no such provision within the Apple Devices to tag a signature received or template stored as such. In order to enrol or delete other users, a user must always enter a passcode and cannot exercise administrative privileges simply by presenting a biometric. Put another way, a user of an iOS Apple Device cannot exercise administrative privileges simply by presenting a biometric signature.
459 In relation to MacOS Apple Devices, CPC identifies that they have a slightly different functionality which it submits is relevant to the question of infringement here. CPC submits that in MacOS Apple Devices users can be identified as an “administrator” or “standard user” (based on the status of the user account, rather than the user’s biometric).
460 However, by reference to claim 3 of the 168 patent, it may be seen that the requirement of the claim is that not only must an “administrator signature” be stored in the database (integer (7)) but the receiver sub-system must also provide a means for enabling administrative processing of information stored in the database “if a biometric signal matching the stored administrator signature is received by the transmitter” (integer (8)). In MacOS Apple Devices, it remains a requirement that the user also input a password before any administrative privileges are enabled. As such, administrative processing is not permitted on the basis of an administrator signature as such because of the added requirement of a password.
461 Accordingly, I am not satisfied that CPC has established the presence of the administrator signature integers in the iOS Apple Devices or the MacOS Apple Devices.
6.7 Conclusions in relation to infringement
462 On the basis of the reasons set out above, I have concluded that CPC has failed to establish that the iOS Apple Devices have infringed:
(a) any of the asserted claims in the 293 patent because none possess the “conditional access” feature (section 6.2 above);
(b) any of the asserted claims because none possess a “transmitter sub-system” or “receiver sub-system” as required (section 6.3 above);
(c) any of the asserted claims because none possesses an “accessibility attribute” as required (section 6.4 above);
(d) any of the asserted claims of the 293 patent because none possess the “series feature” as required (section 6.5 above); and
(e) claims 3 and 6 of the 168 patent and claims 29 and 41 of the 293 patent because none possess the “administrator signature” feature (section 6.6 above).
463 The above findings address the parties’ submissions in relation to the iOS Apple Devices, which are the Apple Devices in exemplar categories 1 and 3. CPC advances a minor point in relation to MacOS Apple Devices (exemplar category 2) in relation to the “administrator signature” feature that I have addressed in section 6.6 above.
464 In relation to iOS Apple Devices used with the Apple Watch (exemplar category 4), CPC contends that the position in relation to infringement remains unchanged from iOS Apple Devices used without accessories. Apple submits that where an Apple Watch is paired with an iOS Apple Device the position as to what amounts to the transmitter sub-system and the receiver sub-system is further confused and the identification of any conditions of access imposed by the accessibility attribute is yet more difficult. Having regard to the conclusion that I have reached in relation to those matters above, it is not productive to address these matters any further.
465 Finally, in relation to the MacOS Apple Devices used with the Magic Keyboard (exemplar category 5), CPC submits that the only difference is that the biometric sensor is on the Magic Keyboard, rather than the macOS Apple Device itself. Neither party contends that this is material to the questions of infringement considered above.
7. VALIDITY
466 In its cross claim, Apple pleads grounds of invalidity based on; lack of novelty, lack of inventive step, lack of manner of manufacture and non- compliance with the requirements of s 40 of the Patents Act.
467 Apple’s pleaded novelty case included six items of prior art being Wuidart, Hamid, Scott, Hsu, Mathiassen (on the assumption of a deferred priority date) and the iPAQ Reference Guide. The lack of inventive step case advanced was based on the common general knowledge alone and also having regard to the disclosure of each of Hamid, Scott and Hsu (in accordance with s 7(3) of the Patents Act).
468 During the course of closing oral argument, Apple submitted that much of its invalidity case was dependent upon the infringing construction of the asserted claims advanced by CPC, although some aspects of its invalidity case were advanced based on its non-infringing construction of certain integers of the asserted claims. After the conclusion of oral submissions, it clarified its position by stating that:
(a) it no longer pressed a lack of novelty case based on Hsu;
(b) it no longer pressed a lack of inventive step case based on s 7(3) of the Patents Act;
(c) if the court construes “accessibility attribute” such that it is not embodied by the Apple Devices, it does not press its lack of inventive step case at all;
(d) if the court construes “accessibility attribute” such that it is not embodied by the Apple Devices, it also does not press its lack of novelty case based on any of Scott, Mathiassen or the iPAQ Reference Guide;
(e) if the court construes “transmitter sub-system” and “receiver sub-system” such that they are not embodied by the Apple Devices, it does not press its lack of novelty case based on the iPAQ Reference Guide;
(f) if the Court construes the “series feature” such that it is not embodied in the Apple Devices, it does not press its lack of novelty case at all in respect of the 293 patent; and
(g) if the court construes “administrator signature” such that it is not embodied by the Apple Devices, it does not press its lack of novelty case based on Scott, Hamid, Wuidart or the iPAQ Reference Guide in respect of claims 3 or 6 of the 168 patent or claim 41 of the 293 patent.
469 Furthermore, in its closing written submissions Apple indicated that it did not press its case based on lack of manner of manufacture if the court rejected CPC’s construction of accessibility attribute, transmitter sub-system and receiver sub-system, as used in the asserted claims.
470 My findings in section 6 of these reasons are that the Apple Devices do not infringe the asserted claims because they do not contain the “accessibility attribute” feature, the “transmitter sub-system” and “receiver sub-system” features, the “series feature” or the “administrator signature” feature. The consequence is that, in light of these findings, much of the novelty and all of the lack of inventive step case fall away as well as the ground of invalidity based on lack of manner of manufacture.
471 Nevertheless, in the sections that follow I have considered it appropriate, out of an abundance of caution, to have regard to the lack of novelty case insofar as it concerns the disclosures of Scott, Hamid, Mathiassen and Wuidart, in the event that my construction of the contested terms is found to be incorrect. I have not succumbed to the temptation to take that course with the iPAQ Reference Guide. Nor have I considered it to be appropriate to evaluate the question of lack of inventive step against a construction that I have rejected. The same applies to the question of whether the asserted claims lack a manner of manufacture. Since I have considered the disclosure of Mathiassen, for the reason explained above, it has also been necessary to consider the question of deferred priority date.
8. DEFERRED PRIORITY DATE
8.1 Introduction
472 Apple contends that none of the claims of the 168 patent or the 293 patent are entitled to claim a priority date from the date of filing of the provisional specification on 13 August 2003, with the consequence that the deferred priority date (13 August 2004) applies. The disclosure of the following matters is relevant to this issue:
(a) a strongly encrypted wired path between the code entry module and the controller;
(b) an accessibility attribute; and
(c) the enrolment aspects of the claims.
8.2 Relevant law
473 I have noted earlier that the patents are pre-RTB Act. Accordingly, the provisions of the Patents Act as it stood before 2012 and the Patents Regulations 1991 (Cth) as they then were, apply. Pursuant to s 43 of the Patents Act and (in the case of the 168 patent) reg 3.12(1)(b) and reg 3.12(2)(a) of the Patents Regulations; and (in the case of the 293 patent) reg 3.12(1)(c) and reg 3.12(2C) of the Patent Regulations, as they existed before amendments by way of the RTB Act, each of the relevant claims will be entitled to the priority date if it is fairly based on the provisional specification.
474 Section 43(2) of the Patents Act provides that:
(2) The priority date of a claim is:
(a) the date of filing of the specification; or
(b) where the regulations provide for the determination of a different date as the priority date—the date determined under the regulations.
475 Relevantly, reg 3.12 of the Patent Regulations provides:
(1) Subject to regulations 3.13 and 3.14 and subregulation (2), the priority date of a claim of a specification is the earliest of the following dates:
(a) the date of filing of the specification;
(b) if the claim is fairly based on matter disclosed in 1 or more priority documents, the date of filing the priority document in which the matter was first disclosed;
(c) if the specification is a complete specification filed in respect of a divisional application under section 79B of the Act and the claim is fairly based on matter disclosed in the specification referred to in paragraph 79B (1) (a) of the Act — the date mentioned in subregulation (2C);
…
(2) For the purposes of paragraph (1)(b):
(a) if the application that relates to the specification containing the claim is a complete application — a provisional application that is associated with that complete application in accordance with section 38 of the Act is a priority document; and
…
(2C) The date for a specification to which paragraph 3.12 (1)(c) applies is the date that would have been the priority date of the claim if it had been included in the specification referred to in paragraph 79B(1)(a) of the Act.
476 The authorities refer to the analysis required by these provisions as “external fair basis” because it involves consideration of the claims of the patent as filed against the whole of the disclosure of the provisional specification to determine whether there is real and reasonably clear disclosure of the invention claimed, or whether the invention claimed travels beyond the invention described. Unlike the fair basis test under s 40(3) pre-RTB Act (being “internal fair basis”), it does not require an analysis of the claims against the balance of the specification.
477 In Coretell Pty Ltd v Australian Mud Company Pty Ltd [2017] FCAFC 54; (2017) 250 FCR 136 the Full Court (Burley J, Jagot and Nicholas JJ agreeing) relevantly said at [134]–[135]:
There is a nuanced difference between the test for fair basis arising under s 40(3) of the Act and the test for determining priority dates pursuant to reg 3.12(1) above. The latter requires that the claim be “fairly based on matter disclosed in the specification” and the former requires that the claim described be “fairly based on the matter described in the specification” (emphasis added). A Full Court of this Court succinctly stated the practical effect of the difference in Multigate Medical Devices Pty Ltd v B Braun Melsungen AG [2016] FCAFC 21; (2016) 117 IPR 1 at [189] (citations omitted; italics in original):
… There are two linguistic differences in the phrase used for external fair basis. First, the definite article is omitted. Second, the reference is to what is disclosed rather than what is described. So, the absence of the definite article makes it plain that external fair basis can arise if some part of the overall disclosure made in the prior specification discloses the relevant matter. … Further, the use of “disclosed” rather than “described” connotes greater flexibility in the test for external fair basis in terms of ascertaining from the prior specification the requisite disclosure.
Whilst one must bear in mind this nuance, otherwise, the test for external fair basis is essentially the same as that set out definitively in Lockwood Security Products Pty Ltd v Doric Products Pty Ltd [2004] HCA 58; (2004) 217 CLR 274 (Doric No 1), where the High Court held that the requirement that a claim or claims be fairly based on matter described in the specification within s 40(3) of the Act requires a “real and reasonably clear disclosure” of what is claimed. At [69] the High Court referred with approval to the following passage in the judgment of Gummow J in Rehm at 95:
The circumstance that something is a requirement for the best method of performing an invention does not make it necessarily a requirement for all claims; likewise, the circumstance that material is part of the description of the invention does not mean that it must be included as an integer of each claim. Rather, the question is whether there is a real and reasonably clear disclosure in the body of the specification of what is then claimed, so that the alleged invention as claimed is broadly, that is to say in a general sense, described in the body of the specification.
478 Where the question of disclosure concerns a provisional specification, it has been suggested that one should recognise that the invention may be in a fairly provisional or rough state such that the invention may be subsequently developed and refined. In Rescare Ltd v Anaesthetic Supplies Pty Ltd [1992] FCA 811; (1992) 111 ALR 205 at 37, Gummow J (sitting in the Federal Court) cited with approval Blanco White, Patents for Inventions (5th ed, 1983), a United Kingdom text, at [2-209]:
It should be noted that the question of “fair basing” upon a provisional specification is not altogether analogous to that of “fair basing” upon a complete specification… It has always been considered legitimate to develop an invention to some extent after filing a provisional specification, and the expression ‘fairly based’ in the present context allows for such development.
479 The Full Court in Anaesthetic Supplies Pty Ltd v Rescare Ltd [1994] FCA 304; (1994) 50 FCR 1 differed from Gummow J in its construction of the provisional specification in suit and found that the claims of the standard patent subsequently granted were not fairly based but agreed with the application of the notion identified in Blanco White as set out above, and expanded it saying at 20 (Lockhart J, Wilcox and Shepherd JJ agreeing):
See also Terrell on the Law of Patents (13th ed, 1982), op cit, pp 63-4, where the learned authors state that the primary object of the provisional specification is to enable the inventor to improve and perfect the invention during the period of “provisional protection”. See also Coopers Animal Health Australia Ltd v Western Stock Distributors Pty Ltd (1987) 11 IPR 20 at 436 and Rehm Pty Ltd v Websters Security System (International) Pty Ltd (1988) 11 IPR 289; Interact Machine Tools (NSW) Pty Ltd v Yamazaki Mazak Corp (1993) 27 IPR 83.
All that the provisional specification needs to do is describe generally and fairly the nature of the invention, and not to enter into all the minute details as to the manner in which the invention I to be carried out. It is a mode of protecting an inventor until the time of filing the final specification. It is not intended to be a complete description of the invention, but simply to disclose the invention fairly, though in its rough state…
480 It has been suggested that when the authorities are examined, including the facts in Rescare, it is not possible to discern any material difference of approach between fair basing for the purpose of internal fair basis as compared to external fair basis on a provisional specification. Bodkin C, Patent Law in Australia (4th ed, Thomson Reuters, 2024) remarks as follows at [22690]:
Hence the determination of fair basis, whatever its context, requires a comparison of the claim or claims in dispute with the description provided by the relevant document (including any drawings that it may contain). The only difference there may be merely arises because the description in a provisional specification could be less detailed than in a complete specification, but that is a difference in the descriptions that are to be compared rather than in the approach to determining fair basis.
481 However, to the extent that these observations conflict with those in Rescare, they must be set to one side. They have been followed by this Court as correct; Leonardis v Sartas No 1 Pty Ltd [1996] FCA 449; (1996) 67 FCR 126 (Burchett, Hill and Tamberlin JJ), Britax Childcare Pty Ltd v Infa-Secure Pty Ltd (No 4) [2015] FCA 651; (2015) 113 IPR 280 at [266] (Middleton J); Apotex Pty Ltd v ICOS Corporation (No 3) [2018] FCA 1204; (2018) 135 IPR 13 at [620] (Besanko J).
8.3 The disclosure of the provisional specification
482 The provisional specification begins with a description of the “Field of the Invention” and the “Background” in materially the same terms as the patents as set out in section 3.1 above. Figure 1 of the provisional specification is a more rustic version of Figure 1 contained in the patents in suit and is as follows:
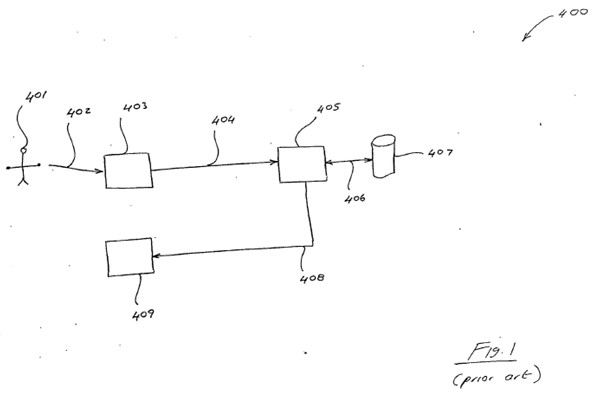
483 Figure 1 is described, on page 1 lines 6 to 22, to involve a user (401) making a request (402) typically by way of secure code such as a sequence of secret numbers or a biometric signal (such as a finger print) directed to a code entry module (403) such as a keypad or a biometric sensor typically mounted on the external jamb of a secure door. The code entry module conveys the request by sending a corresponding signal (404) to a controller (405) which is typically situated in a remote or inaccessible place. The controller authenticates the security information by interrogating (406) a database (407). If the user is authenticated and has the appropriate access privileges, the controller sends an access signal (408) to a device (409) in order to provide the desired access. The device can be, for example, the locking mechanism of a secure door or an electronic lock on a personal computer which the user desires to access.
484 The provisional specification then identifies problems with the prior art arrangement so described as follows (page 1 line 25 to page 2 line 10):
Although the request 402 can be made secure, either by increasing the number of secret digits or by using a biometric system, the communication infrastructure in Fig. 1 is typically less secure. The infrastructure 400 is generally hardwired, with the code entry module 403 generally being mounted on the outside jamb of a secured door. In such a situation, the signal path 404 can be over a significant distance in order to reach the controller 405. The path 404 represents one weak point in the security system 400, providing an unauthorised person with relatively easy access to the information being transmitted between the code entry module 403 and the controller 405. Such an unauthorised person can, given this physical access, decipher the communicated information between the code entry module 403 and the controller 405. This captured information can be deciphered, replayed in order to gain the access which rightfully belongs to the user 401, or to enable modification for other subversive purposes.
(Emphasis added)
485 In light of the above, the “Summary” concludes by identifying the key aspects of the invention the subject of the provisional specification (page 3 lines 3 to 6):
Disclosed are arrangements which seek to address the above problems by replacing the vulnerable wired path 404 with a strongly encrypted wireless path between the code entry module and the controller, and by incorporating biometric authentication at the code entry module 403.
486 The provisional specification provides a statement of the invention (or consistory clause) as follows (page 3 lines 7 to 13):
According to a first aspect of the present invention, there is provided a system for providing secure access, the system comprising:
a biometric sensor for authenticating the identity of a user;
a transmitter for transmitting information using a secure wireless signal dependent upon a request from the user and the authentication of the user identity; and
a control panel for receiving the information and for providing the secure access requested.
487 In the “Detailed Description”, the invention is described by reference to figure 2 which is as follows:
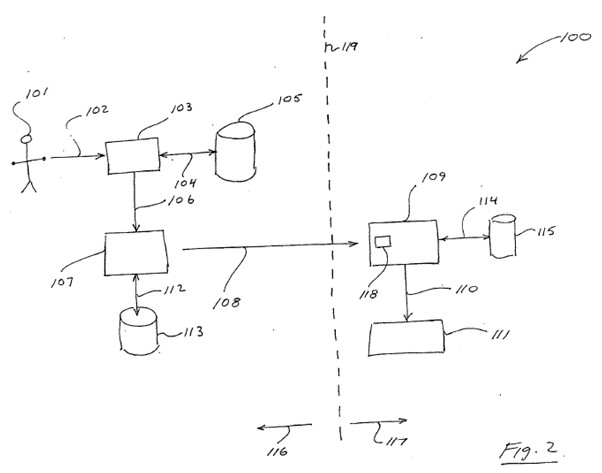
488 Figure 2 is described, at page 4 lines 8 to 26, as an arrangement for providing secure access where the user (101) makes a request (102) to a code entry module (103). The code entry module is a biometric sensor and the request takes a form which corresponds to the nature of the sensor. The code entry module interrogates (104) a user identity database (105) which contains biometric signatures for authorised users against which the request can be authenticated. If successful, the code entry module sends a signal (106) to a controller/transmitter (107) that checks (112) the current rolling code in database (113) and then updates the code and sends it (108) to a controller (109) in the receiver sub-system side. The controller (109) tests the rolling code against the most recent rolling code stored in a database (115) and, if legitimate, then sends a command (110) to a controlled item (111).
489 In relation to access privileges of the user, the provisional specification provides (page 6 line 25 to page 7 line 8):
In addition to authenticating the user 101 the biometric sensor 103 in conjunction with the controller 107 can also check other access privileges of the user 101. These access privileges can be contained in the database 105 which be located either locally in the remote key fob, or in the sub-system 117 as previously described. In one example, Tom Smith can firstly be authenticated as Tom Smith using the thumb press by Tom on the biometric sensor panel (not shown). After Tom’s personal biometric identity is authenticated, the sub-system 116 can check if Tom Smith is in fact allowed to use the particular door secured by the device 111 on weekends. Thus the security screening offered by the described arrangement can range from simple authentication of the user’s identity, to more comprehensive access privilege screening.
(the Tom Smith example)
490 Towards the conclusion of the provisional specification, at page 10 lines 16 to 22, notes as follows:
Accordingly, existing systems as are described in Fig. 1 can be upgraded by replacing the code entry module 403 and the transmission path 404, leaving the other components of the system 400 (ie., the controller 405, the code database 407 and the controlled item 409, together with existing wiring 408 and 406) largely intact. Minor modifications might however be necessary. When upgrading systems in this manner, the sub-system 116 can either be used in a remote fob configuration or can be placed in a secure housing on an external door jamb.
491 The provisional specification contains 8 claims. Claim 1 is the only independent claim. It provides as follows:
A system for providing secure access, the system comprising:
a biometric sensor for authenticating the identity of a user;
a transmitter for transmitting information using a secure wireless signal dependent upon a request from the user and the authentication of the user identity; and
a control panel for receiving the information and for providing the secure access requested.
8.4 The submissions
492 Apple first contends that the invention disclosed in the provisional specification requires the transmitter sub-system to transmit signals to the receiver sub-system wirelessly, and to the extent that the asserted claims are not confined to wireless transmission there is no real and reasonably clear disclosure of the invention claimed. Apple submits that the essence of the disclosure of the provisional specification is that the vulnerable wired path of the prior art systems is replaced with a strongly encrypted wireless path between the code entry module and the controller. This is the “weak point” identified in the prior art as providing an unauthorised person with relatively easy access to the information being transmitted between the code entry module and the controller. As a result, because none of the asserted claims require the use of a wireless path, none is fairly based on the provisional specification.
493 CPC disputes this characterisation. It submits that the provisional specification broadly discloses an invention relating to secure access systems and is not limited to wireless systems, none of the embodiments being limiting embodiments. CPC also contends that the “vulnerable wired path” of the prior art is not the path of the secure access signal between the transmitter sub-system and the receiver sub-system but rather the path (404) in the prior art between the code entry module (403) and the controller (405) along which the biometric signal is sent. It submits that the experts accepted that the provisional specification indicated that the path between the transmitter sub-system and the receiver sub-system (108 in figure 2 and 408 in figure 1) being the communication path of the secure access signal, could remain and be wired.
494 Apple next submits that the provisional specification does not disclose an accessibility attribute of the type set out in the claims of the patents. In answer, CPC relies on the Tom Smith example as providing a disclosure, contending, first, that properly construed the accessibility attribute does not impose any requirement that it only concern conditions that specifically arise from the matching outcome as opposed to “pre-conditions”, nor must the condition be specified by the particular biometric signature. Secondly, CPC submits that even if it did, the Tom Smith example would amount to sufficient disclosure because it does not only concern “pre-conditions” as the question of whether Tom Smith is allowed to use a particular door on weekends occurs after a biometric match has occurred. Apple submits that the checking of access privileges described in the Tom Smith example is only a check of preconditions to access and does not fulfil the requirements for the issue of an accessibility attribute.
495 Apple also submits that the provisional specification is silent as to enrolment, including what components are required to perform it, who is entitled to do so, how the system determines when it is appropriate to enrol someone, how the system enters enrolment mode and the interactions with the system required to perform enrolment. Apple asserts that the patents in suit contain extensive disclosure of the matters pertaining to enrolment, which it says is reflected in the asserted claims, in particular: (a) the requirement that the transmitter sub-system enrol signatures in the database in all asserted claims; (b) the administrator signature integer in claims 3 and 6 of the 168 patent and claims 29 and 41 of the 293 patent; and (c) the series feature as it appears in all of the asserted claims of the 293 patent. It submits that there is no disclosure of any of those features in the provisional specification.
496 CPC accepts that the provisional specification does not explicitly refer to enrolment, administrator integers or the series feature, but submits that this does not of itself mean that the claims including those features lack disclosure. It submits that the fact that the transmitter sub-system performs an enrolment function may be inferred based on the fact that there is a matching process against registered signatures necessarily means that there must also be a process whereby those signatures are registered by a biometric sensor. It submits that there is an implicit disclosure of the administrator integer features in the Tom Smith example, because that passage, together with figure 2, includes the possibility of an administrator providing access privileges for different individuals via a discrete system, citing the evidence of the experts. In relation to the series feature, it submits that it is implicit from the disclosures in the provisional specification that the invention discloses a process of enrolment and that it was common general knowledge to obtain multiple fingerprint scans to ensure the samples were of sufficient quality and that those samples cold then be dealt with in a number of different ways. Finally, CPC submits that the fact that the provisional specification may be silent on these matters does not mean that the asserted claims lack fair basis. These matters are implicitly covered by the disclosure of the provisional specification and the fact that the claims of the provisional specification are more limited in scope than the disclosure of the provisional specification will not result in a finding of lack of fair basis.
8.5 Consideration
497 In relation to wireless communication, the debate between the parties concerns whether or not there is a real and reasonably clear disclosure within the provisional specification of a transmitter sub-system that communicates via any mode of transmission other than wireless transmission. There is no dispute that each of the asserted claims is sufficiently broad to encompass transmission that is wired as well as wireless.
498 The “Field of the Invention” described in the provisional specification is “in particular” to systems using wireless transmission of security code information. Such language does not preclude systems using communication means other than wireless transmission.
499 I have summarised above the “Background” supplied in the provisional specification. It concludes, at page 3 lines 1 to 6, with a passage that was the subject of some debate in the evidence which is as follows:
It is an object of the present invention to substantially overcome, or at least ameliorate, one or more disadvantages of existing arrangements.
Disclosed are arrangements which seek to address the above problems by replacing the vulnerable wired path 404 with a strongly encrypted wireless path between the code entry module and the controller, and by incorporating biometric authentication at the code entry module 403.
(Emphasis added)
500 This passage was the subject of expert evidence and debate between the parties. It is awkwardly worded but conveys two concepts. The first is that the invention addresses a problem of the prior art systems by replacing the vulnerable wired path (404) with a strongly encrypted wireless path between the code entry module and the controller. The second is to incorporate biometric authentication at the code entry module (403).
501 The second concept is exemplified in figure 2, where the database of biometric signatures (105) for checking against the user’s biometric signal is part of the transmitter sub-system (116) and connected to the code entry module (103) by communication pathway (104). By such an arrangement, the invention dispenses with the “weak point” identified in the “Background”, being that “signal path 404 can be over a significant distance in order to reach the controller 405” by incorporating biometric authentication at the code entry module (103) within the transmitter sub-system. As the experts agreed, in this arrangement there is no longer path (404) transmitting the biometric signal and no need to replace signal path (404) with a wireless path. Dr Dunstone and Associate Professor Boztas further agreed that where the database is located inside the transmitter sub-system the teaching of the provisional specification is that the connection between the two can be wired.
502 The first concept speaks of a strongly encrypted wireless path between the code entry module (403) and the controller (405) of the prior art (depicted in figure 1). Taken in context, this must be a reference to the wired path (404) between the equivalent of the transmitter sub-system (where the code entry module (103) is situated in the system of the invention described by reference to figure 2) and the receiver sub-system, which receives the signal by controller (109). That interpretation is supported by the language in the next passage, which is the consistory clause for claim 1 which provides for “a transmitter for transmitting information using a secure wireless signal dependent upon a request from the user ... and a control panel for receiving the information…”. So understood, the requirement that the signal be wireless is directed to what may be identified as pathway 108 in the embodiment in figure 2.
503 However, a later embodiment described on page 10 of the provisional specification provides at lines 16 to 23:
Accordingly, existing systems as are described in Fig. 1 can be upgraded by replacing the code entry module 403 and the transmission path 404, leaving the other components of the system 400 (ie., the controller 405, the code database 407, and the controlled item 409, together with existing wiring 408 and 406) largely intact. Minor modifications might however be necessary. When upgrading systems in this manner, the sub-system 116 can either be used in a remote fob configuration, or can be placed in a secure housing on an external door jamb.
(Emphasis added)
504 The experts agreed that this passage teaches, having regard to figure 1, that one way to put the invention into practice is to put the authentication process into the transmitter sub-system in so doing, the connection 408 may be wireless or be retained as a wired connection.
505 Having regard to these matters, I consider that there is sufficient disclosure in the provisional specification of a wired communication between the transmitter sub-system and the receiver sub-system. This aspect of Apple’s argument fails.
506 The dispute about accessibility attribute concerns whether there is a real and reasonably clear disclosure in the provisional specification of an accessibility attribute as claimed in the asserted claims.
507 I have found that within the asserted claims, the step of matching a biometric signature and conveying a positive match will not of itself amount to an accessibility attribute. The asserted claims generally require an accessibility attribute to be provided only in response to the receipt of a “legitimate” or “authenticated” biometric signal. In other words, after a positive biometric match, the transmitter sub-system must provide or output an accessibility attribute that conveys (“establishes”) whether and under which conditions access to the controlled item should be granted to a user.
508 The Tom Smith example does not provide a disclosure of an accessibility attribute. It identifies that the biometric sensor can authenticate the user and also check other access privileges of the user, such as whether Tom Smith is able to use the particular door secured by the device on weekends. However, no reference is made to the provision or output of an attribute meeting the definition that goes both to whether and under which conditions access to the controlled item should be granted to a user.
509 CPC submits that the Tom Smith example provides a disclosure sufficient to constitute a real and reasonably clear disclosure even if its definition of “accessibility attribute” is not accepted. It relies on a passage of Dr Dunstone’s evidence where he accepted that the system disclosed in the provisional specification would have the “capacity” to determine a level or condition of access, depending on who the person was.
510 However, in my view this can be no more than a hindsight acceptance that something more may possibly yet come. It does not amount to a real and reasonably clear disclosure of an accessibility attribute within the asserted claims in the sense required by the authorities to which I have referred above.
511 In relation to enrolment, all of the asserted claims require that the transmitter sub-system enrol biometric signatures into a database in what may be called a generic enrolment function. Claims 3 and 6 of the 168 patent and claims 29 and 41 of the 293 patent additionally involve the more specific administrator signature integer discussed in section 4.8 above. All asserted claims of the 293 patent additionally involve the series feature discussed in section 4.9 above. Apple contends that the provisional specification includes no disclosure of any form of enrolment and that accordingly, the asserted claims are not fairly based.
512 In considering the generic enrolment question, it is relevant to note that the common general knowledge summary describes that enrolment in biometric secure access systems is a process whereby new users were required to provide a sample of a biometric attribute. It typically required the biometric attribute (e.g. a fingerprint) to be presented to the scanner several times and could take place according to one of two known arrangements. First, by using the same biometric sensor for enrolment and matching. This was the case in standalone secure access systems. Secondly, by using one biometric sensor at a central server for enrolment and one biometric sensor for matching at each secure access point. This was more common in networked systems with multiple users and multiple doors. The location of the biometric sensor relative to the database depended on the size and scale of the biometric system, with the sensor, processor, enrolment and matching software, and database located in the same unit in standalone systems.
513 I accept that the fact that there is a matching process against registered signatures in the database described in the provisional specification means that for every occasion where a biometric matching process takes place, there must necessarily have been a process whereby those signatures were registered by means of the biometric sensor. The person skilled in the art reading the provisional specification would necessarily understand that some form of enrolment function takes place.
514 The teaching of the provisional specification is that the request (102) made by the user (e.g. a thumb press on a fingerprint sensor) is supplied to the code entry module (103) which then interrogates the user identity database (105) containing biometric signatures for authorised users against which the request can be authenticated.
515 CPC submits that the mere fact that the location of the enrolment function is not specified does not mean that the claims lack fair basis. It submits that the person skilled in the art would read the disclosure and understand that enrolment may take place in either the transmitter sub-system or the receiver sub-system with the consequence that the disclosure of the provisional specification is broader than that of the claims of the patents. I accept that submission.
516 The absence of any explicit disclosure of this integer does not, in my view, mean that there is not a real and reasonably clear disclosure in a general sense of a generic enrolment function (or that it may take place in the transmitter sub-system), as claimed by the asserted claims of the patents.
517 In relation to the administrator signature feature, the requirement of the relevant asserted claims (claims 3 and 6 of the 168 patent and claims 29 and 41 of the 293 patent) is exemplified by reference to claim 3 of the 168 patent, where integer (7) requires “storing a biometric signal received by the transmitter sub-system in the database as an administrator signature”.
518 CPC submits that there is an implicit disclosure of the administrator signature integers because the passage on page 6 line 25 to page 7 line 8 of the provisional specification (set out in section 8.3 above), together with figure 2, includes the possibility of an administrator providing access privileges for different individuals via a discrete system. CPC also contends that the fact that the provisional specification does not expressly disclose how the system identifies the user as an administrator does not give rise to a lack of fair basis.
519 Having regard to the passage on pages 6 and 7 that CPC relies upon, Dr Dunstone accepted in his oral evidence that whilst not described, it was a “possibility” that the invention disclosed by the provisional specification would permit the entry of access privileges for different individuals by an administrator, Whilst I accept that this is a possibility, it is unrealised. The expert evidence in this respect did not rise above hindsight speculation about what may be possible, it is not based on what is disclosed by the provisional specification. I do not consider there to be a real and reasonably clear disclosure in the provisional specification of the administrator signature feature of claims 3 and 6 of the 168 patent and 29 and 41 of the 293 patent.
520 In respect of the series feature (contained in each of the asserted claims of the 293 patent), the requirements are exemplified by integers (6) to (8) of claim 1 of the 293 patent:
(5) means for enrolling relevant signatures into the database using the biometric sensor; wherein the means for enrolling relevant signatures into the database of biometric signatures comprises: (6) means for receiving a series of entries of the biometric signal, said series being characterised according to at least one of the number of said entries and a duration of each said entry; (7) means for mapping said series into an instruction; and (8) means for enrolling relevant signatures into the database according to the instruction;
(Emphasis added)
521 As a matter of construction, contrary to the submissions advanced by CPC, the series feature is not directed to a means for ensuring quality biometric signatures but rather it provides a specific way by which enrolment of signatures into the database may be effected (see section 4.9 above). On that basis, I consider that the provisional specification does not disclose the series feature integers.
522 In conclusion, having considered the disclosure of the provisional specification, in my view the provisional specification does not meet the test for external fair basis in relation to:
(a) all of the asserted claims by reason of insufficient disclosure of an “accessibility attribute”;
(b) claims 3 and 6 of the 168 patent and claims 29 and 41 of the 203 patent by reason of insufficient disclosure of the administrator signature feature; and
(c) all of the asserted claims of the 293 patent by reason of insufficient disclosure of the series feature.
Accordingly, the asserted claims cannot claim priority from the filing date of the provisional specification.
9. NOVELTY
9.1 Introduction
523 The lack of novelty case advanced by Apple is largely, but not entirely, contingent upon the outcome of the various construction arguments identified earlier in these reasons. CPC has identified the integers of the asserted claims that it contends are not disclosed in the prior art novelty documents relied upon. Both parties prepared novelty claim charts identifying their respective positions in relation to the integers. The outcome of some of the novelty arguments depends on the outcome of questions of construction, although as I note below, each depends upon an understanding of the disclosure of the prior art document, which was often the subject of dispute between the experts and the parties.
524 In their closing written submissions, the parties have proceeded by using relevant disputed terms (“accessibility attribute”, “transmitter sub-system” and so on) as shorthand for an integer in which the term appears in the asserted claims. The novelty claim charts demonstrate that the parties rely on the same arguments regarding the disclosure of the relevant prior art document and its correlation with the disputed claim term for multiple integers within the asserted claims. The consequence is that the parties have proceeded on the basis that a finding in relation to the presence of one particular integer may be carried into other integers containing that feature. That is an efficient way to proceed, and I adopt it in these reasons.
9.2 Relevant law
525 Section 18(1)(b)(i) of the Patents Act requires that an invention, so far as claimed in any claim, when compared to the prior art base, be novel.
526 The touchstone for lack of novelty is whether a prior publication anticipates a claimed invention. In General Tire at 485-486, the English Court of Appeal said:
When the prior inventor’s publication and the patentee’s claim have respectively been construed by the Court in the light of all properly admissible evidence … the question whether the patentee’s claim is new … falls to be decided as a question of fact. If the prior inventor’s publication contains a clear description of, or clear instructions to do or make, something that would infringe the patentee’s claim if carried out after the grant of the patentee’s patent, the patentee’s claim will have been shown to lack the necessary novelty, that is to say, it will have been anticipated. The prior inventor, however, and the patentee may have approached the same device from different starting points and may for this reason, or it may be for other reasons, have so described their devices that it cannot be immediately discerned from a reading of the language which they have respectively used that they have discovered in truth the same device; but if carrying out the directions contained in the prior inventor’s publications will inevitably result in something being made or done which, if the patentee’s patent were valid, would constitute an infringement of the patentee’s claim, this circumstance demonstrates that the patentee’s claim has in fact been anticipated.
If, on the other hand, the prior publication contains a direction which is capable of being carried out in a manner which would infringe the patentee’s claim, but would be at least as likely to be carried out in a way which would not do so, the patentee’s claim will not have been anticipated, although it may fail on the ground of obviousness. To anticipate the patentee’s claim the prior publication must contain clear and unmistakable directions to do what the patentee claims to have invented … a signpost, however clear, upon the road to the patentee’s invention will not suffice. The prior inventor must be clearly shown to have planted his flag at the precise destination before the patentee.
527 In considering the question of whether a prior publication anticipated the claims of a patent, the Full Court in AstraZeneca AB v Apotex Pty Ltd [2014] FCAFC 99; (2014) 226 FCR 324 at [299]–[300] (Besanko, Foster, Nicholas and Yates JJ) referred to the reverse infringement test in Meyers Taylor Pty Ltd v Vicarr Industries Ltd [1977] HCA 19; (1977) 137 CLR 228 at 235 (Aickin J) and also the observations in Flour Oxidizing Company Ltd v Carr & Co Ltd [1908] 25 RPC 428 at 457 (Parker J) to the effect that it is not enough to prove that an apparatus described in an earlier specification could have been used to produce a result, it must also be shown that the specification contains clear and unmistakable directions to do so. In that context their Honours in AstraZeneca said at [301]:
These observations are the wellspring of a long line of cases that recognise that, in order for a prior art document to be anticipatory, there must be (to adopt the language in General Tire) a clear description of, or clear instructions to do or make, something that would infringe the patentee’s claim if carried out after the grant of the patentee’s patent. In Bristol-Myers Squibb Company v F H Faulding & Co Limited (2000) 97 FCR 524 (“Bristol-Myers”), Black CJ and Lehane J reviewed the relevant authorities and concluded (at [67]):
What all of those authorities contemplate, in our view, is that a prior publication, if it is to destroy novelty, must give a direction or make a recommendation or suggestion which will result, if the skilled reader follows it, in the claimed invention. A direction, recommendation or suggestion may often, of course, be implicit in what is described and commonly the only question may be whether the publication describes with sufficient clarity the claimed invention or, in the case of a combination, each integer of it. …
(Emphasis added)
9.3 Scott
528 Apple relies on the disclosure in Scott as an anticipation only in the event that CPC’s construction of various integers is accepted.
529 CPC contends that Scott does not disclose a secure access system that has integers containing: (a) an accessibility attribute; (b) a secure access signal; (c) a transmitter sub-system; (d) the series feature; and (e) the administrator signature feature.
9.3.1 The disclosure
530 Scott is entitled “personal identification system”.
531 The “Background of the Invention”, in summary, states that some security systems such as home security systems, require users to enter a fixed code into a device at a host facility before allowing them access to the facility, while others such as automatic teller machines (ATMs) require users to submit an authorised card and enter the associated fixed code. Car alarms and garage door openers can be operated by pressing a button on a remote device to transmit a signal to a receiving unit in the car or garage. Each of these security systems is said to be inherently insecure because access is granted based on possession of the code, card or transmitting device. Where absolute security is required, some host facilities employ a biometric sensor to measure a biometric trait of the person requesting access which is then compared with stored biometric data associated with the identified person and, if there is a match, access is granted. The specification identifies, as follows, a problem with systems of this nature (column 1 lines 32 to 44):
In presently available biometric systems, each authorized person registers with the host facility by providing a sample of the biometric trait, for example, by having his fingerprint optically scanned into a host system data base. Each host facility must have a biometric sensor, access to the database of registered persons’ biometric trait registration data, and a processing system capable of quickly searching the database and conducting the comparison to verity a person’s identity. However, if the set of authorized persons is large, such a system would require a huge database to store the fingerprint images of all the authorised persons and the identification process would become slower as the set of authorized persons increases.
532 The “Summary of the Invention” commences as follows (column 1 lines 46 to 61):
According to one aspect of the invention, a portable personal identification device for providing secure access to a host facility includes a biometric sensor system capable of sensing a biometric trait of a user that is unique to the user and providing a biometric signal indicative thereof. A processing circuit responsive to the biometric signal is adapted to compare the biometric signal with a stored biometric data representative of the biometric trait of an enrolled person that is indicative of the identity of the enrolled person. The processor provides a verification signal only if the biometric signal corresponds sufficiently to the biometric data to verify that the user is the enrolled person or the device. A communication unit, including a transmitter circuit, is adapted to transmit the verification signal to a remote host system.
533 The Summary then describes that the communication unit is preferably adapted for remote communication with a host system via a wireless medium and provides details of the types of biometric sensors. Several embodiments and additional aspects of the invention are described.
534 Scott describes an embodiment of the security system 2A by reference to figure 2 (extracted below), in which a battery powered portable identification device (PID) (6A) is used to communicate (via the communication unit (8A)) with a host facility (4A), such as a garage door, to gain access.
535 In column 8 lines 1 to 14, Scott says:
The embodiment illustrated in FIG. 2. will typically be employed with systems such as garage door openers, automobile security systems, door locks and the like. As such PID communication module 24A will have a longer transmission range than communication module 24 in FIG. 1.
Encoder 23A includes an ID code, which may be a serial number of encoder 23 or PID 6A. Encoder 23A also includes a synchronization counter, an encryption key and an encryption algorithm that employs the encryption key. Host system 4A must “learn” the ID code and the synchronization counter for each PID 6A which is used to access a function of host system 4A. Host system 4A must also know the encryption key.
536 Associate Professor Boztas considered that the synchronization counter is “very similar” to the rolling code described in the patents.
537 An embodiment of a PID (6D) described, at column 8 lines 45 to 55, by reference to figure 6 (not reproduced) illustrates that the PID may include at the top of its housing three function buttons which for an automobile security system could be a driver door button, a trunk button and an alarm button. They can be adapted for use with other host systems having different functions.
538 A process of enrolment is described at column 9 lines 54 to 64, as follows:
An owner of PID 6 must first “enroll” into the unit. Enrollment is the process of scanning a finger to create an image which is stored as a fingerprint template in memory 20. The user enrolls on the unit by removing the “packing” cover and placing a thumb or finger on platen 15. PID can be configured to automatically start the enrolment routine with this action. Enrollment takes approximately 7 seconds. The resultant template is stored in memory 20. Ideally, PID 6 is configured to enable a user to enroll one finger on each hand so that, if the user injures the finger they usually use for verification, an alternate image is available.
539 Scott describes, at column 10 lines 14 to 28, the process of verification (i.e. biometric matching) undertaken by the PID:
Verification is carried out when a user places his finger on platen 15, or presses a verify button if included in PID 6. In the embodiment illustrated in FIG. 4A, the verify button can be a dedicated button, such as the # button 55, or could be any other button or sequence of buttons. Each time the user places his or her finger on platen 15 (or presses the verify button and places their finger on platen 15) the optics unit 12 creates a fingerprint signal indicative of the fingerprint image of the user's finger on platen 15. The fingerprint signal is compared to the stored fingerprint template. If the two are significantly similar, the user's identity is verified to be the enrolled person. Verification takes about 1 second or less once the fingerprint template has been retrieved from storage. The user's fingerprint is always verified with the fingerprint template to allow the use of the encryption key.
540 Scott goes on, at column 10 lines 29 to 34, to explain that verification in programmable PIDs can be set at various threshold levels to account for users who may have very fine, worn or damaged fingers. In this case, the ease of use can be enhanced by reducing their verification threshold, which can be set at the time of enrolment.
541 The specification then provides at column 10 lines 36 to 39:
Once the owner or person controlling the unit is enrolled, the unit can then be “registered” with numerous organizations. The host organization is only interested in knowing the ID code and the public encryption key.
542 The process of accessing a host facility with a PID is described by reference to Figure 8:
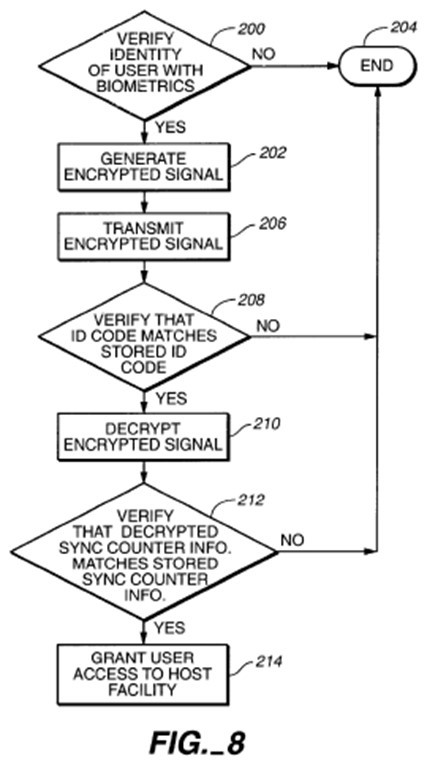
543 The specification explains as follows (column 12 lines 29 to 59):
Referring to FIG. 8, to obtain access to host facility 4A, the user activates PID 6A by placing a finger on platen 15. PID 6A performs a user verification from the internally stored fingerprint template (200). If the verify succeeds, processing unit 16A causes encoder 23A to generate an encrypted signal (202). If not successful, the process ends (204). The encrypted signal includes the unencrypted ID code of PID 6, encrypted synchronization counter information and unencrypted function button information. The encryption employs the encryption key resident in encoder 23A. Transmitter unit 28 then transmits the encrypted signal to host facility 4A (206). Host facility 4A then passes the encrypted signal to host processing unit 32A, which checks the ID code for a match with the ID code of a registered user (208). Typically, there will be only a small number of registered users for car lock and garage door systems, and each may have the same ID code and encryption key. If there is no match, then the process ends (204). If there is a match, host processing unit 4A retrieves the stored encryption key and decrypts the encrypted portion of the received encrypted signal (210). Host processing unit then verifies that the synchronization counter information in the decrypted signal matches stored synchronization counter information in memory 36 (212). If the synchronization counter information does not match the stored information, then the process ends (204). If the synchronization counter information matches the stored information, then the user is granted access to host facility 4A (214). The access granted is determined by the function button information contained in the encrypted signal.
(Emphasis added)
9.3.2 The submissions
544 CPC submits that Scott relates to a fundamentally different invention to the patents because the determination of whether and under which conditions access should be granted is ascertained in the receiver sub-system not the transmitter sub-system. It submits that the signal which is sent to the host facility is a signal which verifies that the person is associated with the unique ID and the signal also includes identification of that unique ID. The host facility does not grant access simply because it gets a signal. The host first checks whether the unique ID in the signal matches one of its registered IDs and only then does the host determine that access should be granted. Accordingly, CPC contends that there is no accessibility attribute, secure access signal or transmitter sub-system that outputs or provides an accessibility attribute. Secondly it submits that there is no disclosure of the administrator signature integers. Thirdly, it contends that the series feature is absent.
545 Apple submits first, that the function button information (being an unlock door or unlock trunk command or the like) is an accessibility attribute within CPC’s definition of that term because it provides access to part of the vehicle and a separate interaction using a different function button may provide access to another part. Apple points out that, in his oral evidence, Associate Professor Boztas rejected the notion that Scott discloses an accessibility attribute within the patents, because the system disclose only involves checking preconditions to access in order to grant or refuse access to a driver’s door, rather than imposing conditions on the grant of access, but notes that Associate Professor Boztas’ view is inconsistent with his position on accessibility attribute in the context of infringement. Secondly, if the function button information is, or is part of an accessibility attribute, then the encrypted signal transmitted by the PID, which incorporates the synchronisation counter information, the ID code and the function button information, is a secure access signal. Thirdly, Apple accepts that Scott does not in terms disclose that a fingerprint is recognised by the system as providing administrative rights and so this feature is not disclosed on its construction of that term. However, on CPC’s approach, those features are disclosed because the first user is permitted to enrol their own fingerprints and may also enrol somebody else’s by presenting the device to them. Fourthly, Apple submits that Scott also discloses user class signatures for the purposes of claim 29 of the 293 patent. Finally, in relation to the series feature, it submits that on CPC’s construction this integer, the feature is inherently present in any system, and on that basis is disclosed.
9.3.3 Consideration
546 Apple does not contend that Scott amounts to a novelty defeating disclosure if its construction of the accessibility attribute (and by extension, the secure access signal), administrator signature and series feature integers of the asserted claims are accepted. It submits, however, that if I construe these terms in the manner contended for by CPC, then Scott should be found to anticipate the claims. I proceed below on the hypothesis that CPC’s construction, as summarised in section 4 above, is correct.
547 CPC’s first contention is that because the determination of whether and under which conditions access should be granted is ascertained in the receiver sub-system, not the transmitter sub-system, Scott discloses a completely different system to that disclosed in the patents. It submits that this analysis results in the consequence that Scott does not disclose an accessibility attribute or a secure access signal.
548 It will be recalled that CPC submits that where a user seeking access identifies a condition of access sought, the recording of a match (i.e. authentication) of the biometric signature would be sufficient to amount to the provision or output of an accessibility attribute by the transmitter sub-system (see section 4.4.1). This, it submits, satisfies the requirement of whether and under which conditions access is granted. For the reasons set out in section 4.4.2 above, I have rejected that contention. However, if I am wrong in that regard, I consider that Scott discloses the accessibility attribute integer on CPC’s construction.
549 Scott discloses, by reference to figure 8, that a user places a finger on the PID which performs a user verification from the internally stored fingerprint template. In order to obtain access to the host facility such as a car (which, if I had accepted CPC’s construction, would amount to a “controlled item”) the following steps are required to take place, as described in column 12 lines 29 to 59 (extracted above).
550 First, if the PID – a transmitter sub-system – verifies the biometric received, it generates an encrypted signal. This signal includes: (a) the unencrypted ID code of the PID; (b) encrypted synchronisation counter information and (c) unencrypted function button information. Dealing with each of these three in turn: the unencrypted ID code is a unique identifier of the PID. The synchronisation counter information is, as Associate Professor Boztas confirmed, the equivalent of a rolling code. The unencrypted function button information may be a selection by the user of what they want to gain access to within the host facility, such as a car boot (trunk), or driver door.
551 Secondly, the PID sends the signal to the host facility which, via the host processing unit, checks the ID code for a match with the ID code of the registered user.
552 Thirdly, if there is a match of the ID code, the host processing unit retrieves a stored encryption key and decrypts the encrypted portion of the signal. The host processing unit then verifies that the synchronisation counter information in the decrypted signal matches that stored in its memory.
553 Finally, if it does, the user is granted access to the host facility, the particular access granted being determined by the function button information contained in the encrypted signal sent from the PID.
554 CPC submits that the determination of access is conducted in the receiver sub-system (the host facility) and that accordingly Scott discloses no accessibility attribute or secure access signal. It may be recalled that in section 4.4.2 I found that the accessibility attribute must be output or provided within the transmitter sub-system, meaning that the transmitter sub-system determines the nature of the access to be granted, notwithstanding that further verification or authentication steps may occur in the receiver sub-system. In my view, the disclosure of Scott is that it is the function button information, contained within the signal generated and sent by the PID that determines access. Accordingly, I reject CPC's submission that the relevant determination takes place in the receiver sub-system (host facility).
555 I otherwise find that the function button information sent from the PID to the host facility is an accessibility attribute within CPC’s construction of that term because the information conveyed as a result of selecting a function button (e.g. “open driver’s door”) establishes whether to grant access to the controlled item (on CPC’s construction) such as a car and it establishes conditions of access because access may be granted to only a portion of the car (e.g. the trunk).
556 Turning to the requirement of claims 5 and 6 of the 168 patent and all of the asserted claims of the 293 patent that the transmitter sub-system has “means for emitting a secure access signal conveying information dependent upon said accessibility attribute”, the question is whether, upon CPC’s construction, that integer is disclosed in Scott. In my view it does. The signal incorporates the function button information (along with other information) and is encrypted and accordingly “secure”.
557 In relation to the administrator signature integers, CPC submits that there is no disclosure of a “means for determining if the database of biometric signatures is empty” (see for example integer (11) of claim 6 of the 168 patent) or any administrator functionality. The mere fact that two different people could enrol a fingerprint on the device does not of itself mean that the first person to enrol is an administrator with administrator privileges. Apple accepts that Scott does not disclose that a fingerprint is recognised by the system as providing “administrative rights” but contends that on CPC’s construction of these integers, they are disclosed because the first user of the device is permitted to enrol their own fingerprints and also someone else’s.
558 Had I accepted CPC’s submissions as to this construction of the administrator signature (which I have not), then it would be difficult to resist the proposition that Scott anticipates this aspect of the patents. As Associate Professor Boztas accepted in his oral evidence by reference to the passage on at column 9 lines 54 to 64 (extracted above), the passage provides that the first user of the PID is permitted to enrol their fingerprints and that person has privileges associated with being the first enrolled. He also accepted that the owner (first user) could enrol one of their own fingers and then, in relation to a second finger, present the device to a second person to enrol their finger. By parity of reasoning with CPC’s argument, such a person would be considered an administrator.
559 In relation to the series feature, Apple contends that this feature is present on CPC’s construction of this integer. CPC submits that the series feature is directed to obtaining a quality biometric signature and requires there to be a sufficient number of entries and duration of each entry to obtain a sufficient quality scan that can be mapped into an instruction. However, CPC observes that enrolment is addressed in the passage cited in column 9 lines 54 to column 10 line 13 (of which the key portion is extracted above), which, whilst providing that a finger must be placed on the sensor at least once, for some unknown period of time, there is no indication that this involved placing the finger on the sensor a sufficient number of times, and for a sufficient duration, to obtain a quality series of entries that could be mapped onto a mathematical representation. I accept CPC’s submission that this is not sufficient disclosure. Accordingly, this integer is not disclosed.
9.3.4 Conclusion in relation to Scott
560 For the reasons set out above, I consider that on CPC’s construction of “controlled item”, Scott discloses an “accessibility attribute”, “secure access signal” and “administrator signature” (within CPC’s construction of both of those terms). However, I have found that there is no disclosure of the series feature (on CPC’s construction).
9.4 Hamid
561 Apple contends that Hamid is an anticipation of the asserted claims of the patents, regardless of which construction of the “accessibility attribute” integer is adopted. However, it does not press a contention that claims 3 or 6 of the 168 patent or claim 41 of the 293 patent are anticipated by Hamid, having regard to my finding that the “administrator signature” feature is not embodied by any of the Apple Devices.
562 CPC disputes that Hamid discloses a secure access system that has: (a) an accessibility attribute; (b) a secure access signal; (c) the administrator signature integers; and (d) the series feature.
9.4.1 The disclosure
563 Hamid is entitled “security access method and apparatus”.
564 The field of the invention is described to be “machine automated security for permitting access to a service or a predefined area by a designated person or persons” and particularly relating to “a portable security device being responsive to a biometric characteristic of the designated person for communicating with a facility for permitting access.”
565 The “Background of the Invention” refers to different known means of ensuring access to a particular area or facility, limited to only those who are authorised. The means for gaining access range from physical key-operated locks to combination locks and electronic locks using coded key cards that have their codes on a microchip or magnetic strip. Within these is the use of an electronic lock which grants access after a computer identifies a person desiring access by comparing the unique features of a biometric characteristic (such as fingerprint) with one stored in its memory. One instance given of such a system involves providing users with a hand-held portable fingerprint recognition and transmission device that includes a scanner that encodes a fingerprint and sends the encoded fingerprint, via an infrared or radio frequency transmitter, to a receiver in the secure item, facility or area. A disadvantage of that system is said to be that it is necessary to have a central computer that analyses the encoded fingerprint to allow recognition and authorisation of an individual. The scanner functions in conjunction with a keypad on the device with several push buttons for selecting specific operations, for example, in combination with an acceptable fingerprint, one button will open all doors of a car while another opens only the car’s trunk. Hamid says that the hand-held devices of this type are relatively bulky (as compared to a key or coded card) and may be misplaced and, from a manufacturers view, reliability of the keypad is difficult to achieve economically. It is said to be an object of the invention to enable a person to unlock any one portal, exclusive of other portals, by choosing which of their personal biometric characteristics is presented to a portable biometric device.
566 The “Summary of the Invention” provides, at [0017] to [0018], as follows:
A portable biometric device, in accordance with the invention, is for use by a designated person in combination with a secure entity and or a secure service, which is accessible via a plurality of portals, each of which is exclusively operable in response to a wireless transmission of a corresponding authorization code which is selected by the designated person choosing which of a plurality of their predesignated biometric characteristics is presented to the portable biometric device.
A portable biometric device in accordance with an aspect of the invention is used by a designated person in combination with a secure entity and or a secure service, which is accessible via a plurality of portals, each of which is exclusively operable in response to a corresponding authorization code. The portable biometric device includes a biometric sensor for reading a biometric characteristic of a person dependent upon the person presenting said biometric characteristic to the biometric sensor; a digital encoder for encoding a reading of the biometric characteristic, from the biometric sensor, to provide an encoded description of the biometric characteristic; a processor responsive to the encoded description of the presented biometric characteristic for determining if the biometric characteristic is predesignated for access via a predesignated one of the plurality of portals, and if so, selecting the authorization code for unlocking said predesignated one of the portals and a wireless transceiver for transmitting the selected authorization code to the secure entity and or service; whereby said designated person, exclusive of an other person, is able to choose which of the plurality of portals is to be unlocked for their access.
567 Hamid provides a description of exemplar embodiments by reference to a number of drawings. In figure 2a (extracted below) the portable fingerprint device is housed in a wristwatch that includes a transparent platen (42) carrying a biometric sensor for sensing biometric characteristics of a user’s fingers. A processor (not depicted) analyses the fingerprint and may cause an “authorization signal” to be transmitted through the infrared port (44).
568 Figure 3 is a block schematic diagram illustrating an example of the functional electronic components of the portable fingerprint security device shown in figure 2a:
569 The specification describes, at [0063], that the sensor array or scanner unit (52) is coupled with a scan / sensor buffer (51) which is responsive to a processor (50) for operating the unit (52). The scan / buffer receives an analogue signal representation of a fingertip pattern and after transfers the captured signal to an encoder (53) which digitises or otherwise converts the analogue signal into a signal format which provides an encoded description of the biometric characteristic, suitable for processing. Hamid continues at [0063]:
In one example the fingertip pattern is delivered from the scan unit 52 in an analog raster scan format of rows and columns. The encoder 53 digitizes the signal differentially. That is to say that as a row signal is sampled, the first sample is encoded as a zero. If the next sample is the same or less it is encoded as a zero but if it is more it is encoded as a one. The next sample is also encoded as a one unless it is less than the previous sample. The result is in binary code which is received by and stored in a data buffer 54, preparatory to signal processing by the processor 50. The processor 50 operates as directed by an instruction set maintained in a random access memory (RAM) 56. The RAM 56 has also been written with a record of a finger print characteristic of the intended user. In operation the processor 50 fetches a segment representative of a central row portion of the finger print characteristic from the RAM 56 and progressively compares the segment with a serial non-destructive row by row readout from the data buffer 54. The processor 50 keeps a running record of where in the serial readout any substantial matches are found. Subsequently in reference keyed to a position of either the best substantial row match or as an alternative the most central of a plurality of substantial row matches, the finger print characteristic from the RAM 56 is compared row segment after row segment from beginning to end with the binary code stored in a data buffer 54 to recognize any apparent corresponding segments. This process may be repeated several times, each by passing the binary code stored in a data buffer 54 keyed with a different apparent reference position until in any one such pass a sufficient number of row segments with apparent matches are realized to warrant a transmission of a predetermined authorization signal. If there are an insufficient number of apparently matching segments, transmission of an authorization signal is unwarranted…
570 In relation to enrolment, Hamid says that the portable fingerprint security device must be pre-authorised for use with a particular security system and personalised for use by a particular person. It says at [0064] and [0065]:
…Prior to operation the portable fingerprint security device is initialized by an administrator with the assistance of either a central computer or a personal computer. When the processor 50 is initially activated by the application of power as for example can be supplied from a watch battery…it is receptive to receiving instructions via a transceiver 58 coupled via an input output port 57. In this example the processor is caused to supervise the loading of the instruction set into the RAM 56. Then the pattern or print of a finger print laid over the platen 42 where it is scanned or otherwise captured to provide a predefined data representative of a predesignated one of a user’s biometric characteristic. The initial capture of the user’s print occurs in response to an interrupt signal on the lead 59 which is generated when the user or the administrator presses the push switch 46. The digitized result is segmented by the processor and the segments are stored in a sequence of addressable locations in the RAM 56 and serves as the predefined data.
One or a plurality of the predefined data representing different ones of the user’s digits are captured in this manner, that is during the initialization. Each of the predefined data is assigned a distinct security access function. FIG. 4 shows doors 1, 2, and 3 having locks L1, L2 and L3 respectively…A portable fingerprint security device 30a has been initialized to be responsive to 3 different finger print patterns of the user for transmitting distinct authorization signals. Each of the locks L1, L2 and L3 is exclusively responsive to receiving the corresponding authorization signal to release for a time convenient for the user to open the door. In another example, not shown, each of a multitude of locked portals can be individually accessed, each of the associated door locks is responsive to a distinct authorization signal each of which is generated upon a combination of two or more digit patterns. Each combination of digit patterns is entered at the time of initialization in session with the administrator.
571 Another embodiment of the invention is disclosed by reference to figures 5 and 5a:
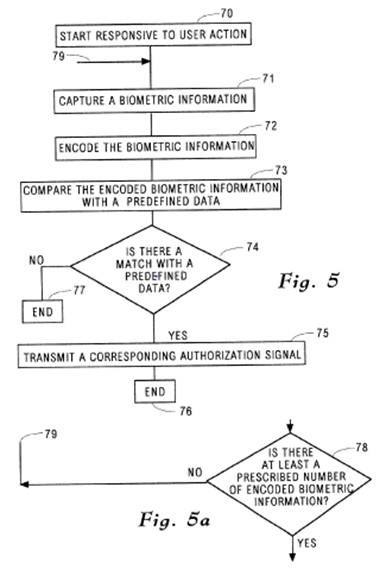
572 At [0066], Hamid describes the embodiment as follows:
The flow diagram in FIG. 5 summarize[s] a method of operation of the portable fingerprint devices illustrated in FIGS. 2 and 2a used in conjunction with the security system in FIG. 4 after the appropriate initialization procedure has been performed. A function block 70 starts the processing response, for example, to a touch of the user’s digit to the platen 32 in FIG. 2 or the platen 42 in FIG. 2a. The process starts by capturing the user’s biometric information as shown in a function block 71. As indicated in a function block 72 the biometric information is encoded and then, as stated in a function block 73, it is compared with one or more predefined data. One example of a method of comparison has been disclosed in the discussion of FIG. 3. If a substantial match is realised in accord[ance] with a decision block 74, the process ends at a block 77 [sic, 76]. In a variation wherein a plurality of fingerprints are expected from the user a decision block 77 [sic, 78], as shown in FIG. 5a, is inserted between the blocks 72 and 73 in FIG. 5. In this example only after the required number of finger prints has been sensed will the comparison function commence.
(Emphasis added)
573 In a further broad embodiment of the invention, explained by reference to figure 6 (not shown), a simplified flow diagram, the specification at [0069] says:
A user is provided with a number of functions each accessible by transmission of a unique access code for executing that function. As described above, typical functions include unlocking of doorways where each function unlocks a different doorway. That said, functions may include turning on and off lights, engaging security systems, checking email, checking voicemail, logging into a computer system, locking doors, unlocking a car, and so forth. Some functions are secure functions – requiring security operations – while others are optionally general access functions like turning a light on or off. The user associates each function with a biometric information. Thus, turning on a light may be associated with left index finger-left index finger, logging into a computer with left thumb-left index finger, and so forth. Each fingerprint is a biometric characteristic of the user.
574 Hamid, at [0072], goes on to say:
Alternatively, a single sequence of biometric characteristics is associated with more than one function. For example a store owner may associate one sequence with opening the store in the morning effecting system start-up, turning on lights, unlocking doors, disabling the alarm and so forth. Another sequence is associated with locking the store at the end of the day effecting system shut-down, turning out the lights, enabling the alarms, etc.
9.4.2 The submissions
575 CPC submits that Hamid does not disclose an accessibility attribute within the scope of the asserted claims because the accessibility attribute must be output or provided within the transmitter sub-system, meaning that it is the transmitter sub-system and not the receiver sub-system which establishes (that is, determines) the nature of the access to be granted. That is not disclosed by Hamid, which is indifferent in its disclosure as to whether or not processing of the biometric data occurs in the transmitter sub-system or the receiver sub-system. CPC submits that Hamid does not disclose, or clearly disclose, what the “authorization code” or “authorization signal” is or what occurs upon its transmission to the secure entity (being the receiver sub-system), such that it is not clear whether it amounts to an accessibility attribute within the meaning of the claims. Accordingly, there is no clear and unmistakable disclosure of an accessibility attribute as required.
576 In relation to the secure access signal, CPC submits that Hamid, for the following reasons, does not disclose the relevant integer: (a) it follows from CPC’s contention that Hamid does not disclose an accessibility attribute; (b) Hamid discloses sending three separate secure access signals to three separate receivers at different locations. As a result, there is not “a” signal as required by the asserted claims, nor is there a single receiver sub-system; and (c) there is no disclosure of the sending of a “secure” access signal, as required by the asserted claims.
577 In relation to the administrator signature integers, CPC contends that the disclosure is not sufficiently clear on its construction of the integer. It also contends that the particular requirements of the series feature are not present.
578 Apple submits that, on its construction of the term “accessibility attribute”, Hamid is not relevantly distinguishable from the patents in suit because the use of a legitimate biometric input to execute multiple functions such as unlocking the doors and disabling the alarm, as disclosed in Hamid at [0072], comprises more than simply determining whether access is to be granted, but also imposes conditions relevant to the access granted. On CPC’s construction of the term, Apple submits that the authorisation code of Hamid meets CPC’s definition of an accessibility attribute because it is a transmission that provides access to part of the functionality of a device, but not another part. Accordingly, on both constructions Hamid anticipates this aspect of the patents. It disputes that Hamid does not disclose the processing of the biometric data in the transmitter sub-system. Apple further contends that the authorisation signal or information signal disclosed in Hamid is the secure access signal within the meaning of the asserted claims and that each of the administrator signature integers and series feature are present in the disclosure.
9.4.3 Consideration
579 In relation to the accessibility attribute, CPC emphasises in its submissions that there is no clear disclosure in Hamid of an accessibility attribute because it is unclear if the question of whether and under what conditions access should be granted is determined in the portable biometric device (that is, the transmitter sub-system) or if that determination takes place in the secure entity (being the receiver sub-system). This is significant, because all of the asserted claims require that the relevant determination take place in the transmitter sub-system. In particular, CPC submits that further processing could take place in the secure entity to establish whether and under what conditions access should be granted after the signal is received.
580 I have found in section 4.4.2 above that, in the context of the asserted claims, whilst it is the transmitter sub-system that must establish whether and under which conditions access is granted following the receipt of a legitimate biometric signal, further authentication and decryption processes may occur within the receiver sub-system to enable the requisite access to be provided. It is in this context that it is relevant to first consider this argument advanced by CPC by reference to the disclosure of Hamid.
581 The embodiment disclosed at [0018] of Hamid is a portable biometric device that is used in combination with a secure entity or secure service (a receiver sub-system) which provides access to a plurality of portals (for example, doors) each of which is able to be accessed in response to a corresponding “authorization code”. In operation, the sensor within the biometric device takes a reading of the user’s biometric characteristic and its processor, “responsive to the encoded description of the presented biometric characteristic”, determines if the characteristic is predesignated for access via a predesignated one of the plurality of portals, and if so, selects “the authorization code for unlocking said predesignated one of the portals”. The device then transmits the selected “authorization code” to the secure entity or secure service thereby enabling access. This indicates that the biometric comparison and issue of an authorisation code to open one or more doors in the secure entity takes place in the portable biometric device. That was the view of the experts, as is apparent from the following evidence of Associate Professor Boztas (by reference to figure 5):
MR LANG: And then at 74, you see – is there a match with predefined data, and that may output the positive match indicated by the yes there.
ASSOC PROF BOZTAS: Okay.
MR LANG: And then if the match is yes, then we go to 75, namely, transmit to corresponding authorisation signal. Do you see that?
ASSOC PROF BOZTAS: Yes.
MR LANG: And just breaking down what’s happening there, assume that the relevant action for this fingerprint is [unlock door] A.
ASSOC PROF BOZTAS: Okay.
MR LANG: Then, first, the portable device will make that positive match determination which we’ve just seen. Is that right?
ASSOC PROF BOZTAS: Yes.
MR LANG: And then, as a result, it generates a command to unlock door A.
ASSOC PROF BOZTAS: Yes.
MR LANG: And then that command needs to be transmitted over the airwaves.
ASSOC PROF BOZTAS: Yes.
MR LANG: And so the unlock door command will need to be encoded in a way suitable for physical transmission.
ASSOC PROF BOZTAS: Correct.
MR LANG: And the integrated circuit in the portable door control will perform those functions.
ASSOC PROF BOZTAS: Okay.
MR LANG: And then that will produce the authorisation signal in block 75.
ASSOC PROF BOZTAS: Yes.
MR LANG: And so in that way the authorisation signal is derived from the positive match result and the unlock door command.
ASSOC PROF BOZTAS: Okay.
(Emphasis added)
582 CPC submits that Hamid does not use the term “unlock door command” deployed in the cross examination above and submits that there is no clear disclosure in Hamid that the authorisation signal conveys whether and under which conditions access may be granted. It submits that further processing of the signal may be required in order to establish these matters after it is received by the secure entity. However, in my view the interpretation accepted by Associate Professor Boztas – with which Dr Dunstone agreed – accords with a sensible reading of Hamid. The portable biometric device produces an “authorization code” (as described at [0018]) after a biometric comparison is made and then that is sent as an “authorization signal” which is derived from the positive match. Accordingly, based on CPC’s construction of “controlled item” a biometric match results in the provision of an “authorization code” that establishes whether and under which conditions access is granted to the secure entity (e.g. one or more doors opened). That is communicated via an “authorization signal” to the secure entity (the receiver sub-system).
583 Apple submits that an accessibility attribute is disclosed in an embodiment described at [0069] to [0073] in Hamid on the construction of that term that I have found to apply. It submits that the disclosure concerning multiple functions involves the use of a legitimate biometric input to produce a combination of unlocking the doors and disabling the alarm, relying in particular on [0069], [0070] and [0072].
584 At [0069], the embodiment is described by reference to figure 6 (not reproduced) in which a user is provided with “a number of functions each accessible by transmission of a unique access code for executing that function”. Those functions include unlocking doorways where each function unlocks a different doorway and may include things like turning on or off lights and engaging security systems. The user “associates each function with a biometric information source or with a sequence of provided biometric information”. At [0072], Hamid provides that a single sequence of biometric characteristics may be associated with more than one function, providing as an example that a store owner may associate one sequence with opening the store in the morning effecting system start-up, turning on lights, unlocking doors, disabling the alarm and so forth. An example of a sequence given is to provide the biometric characteristics of left thumb–left index finger.
585 In my view, however, whilst the entry of a biometric signal here may result in the production of an authorisation code that grants access to a controlled item (e.g. the lock on a secure door), there is no disclosure that a separate condition of access (e.g. whether or not to turn on the lights) is provided by reference to the same biometric signal. Accordingly, the definition of accessibility attribute that I have preferred is not met.
586 Apple contends that the authorisation signal disclosed in Hamid is a secure access signal within the claims. It cites a passage from the oral evidence of Associate Professor Boztas in support. I consider that upon Apple’s construction of “secure access signal” (which I have rejected) this integer is disclosed. However, on the basis of the construction advanced by CPC (which I have accepted), it is not sufficient that the access signal be a signal sent from within a secure system. It must also be a secure signal. Hamid makes no clear disclosure of a basis upon which it may be concluded that the signal is so secure.
587 In relation to the administrator signature integers, on the basis of the construction that I have preferred, as Apple accepts, this element of the claims is not present. However, were I to have accepted the construction for which CPC contends, then in my view, the disclosure of Hamid would be sufficient to meet the requirements of these integers. Paragraph [0064] discloses an administrator and, where an administrator is initialising their own portable biometric device, they would enrol their own signatures into the database. They could enrol multiple of their own signatures or present the device to another person to enrol theirs (see Hamid at [0065]).
588 In relation to the series feature, Apple accepts that on the construction that I have preferred, the integer is absent but submits, in the alternative, that, on CPC’s construction, this integer is inherently disclosed in any biometric security system. Having regard to the specificity of the requirements of the series feature, even were I to have accepted CPC’s construction of this integer, I would not conclude that it was disclosed in Hamid.
9.4.4 Conclusion in relation to Hamid
589 For the reasons set out above I have found Apple has succeeded in establishing that those claims where the only disputed integer concerns the presence of an “accessibility attribute” are anticipated on the basis that CPC’s construction is accepted (but not on the construction of accessibility attribute that I have preferred). I have otherwise found that the secure access signal feature is present on Apple’s construction (which I have rejected), that the administrator feature is present on CPC’s construction (which I have rejected) and that on CPC’s construction of the series feature (which I have rejected) the series feature is not disclosed.
9.5 Mathiassen
590 As I have found in section 8.5 above, none of the asserted claims are entitled to an earlier priority date based on the provisional specification and instead may only claim priority from the deferred priority date. Accordingly, Mathiassen is a relevant prior art disclosure.
591 Apple relies on the disclosure in Mathiassen as an anticipation only on the basis of its alternative case, that CPC’s construction of accessibility attribute is accepted.
592 CPC contends that the embodiments described in the Mathiassen patent do not disclose the invention claimed and that in particular no embodiment discloses integers containing: (a) an accessibility attribute; (b) a secure access signal; (c) the administrator signature features; and (d) the series feature.
9.5.1 The disclosure
593 Mathiassen is entitled “portable or embedded access and input devices and methods for giving access to access limited devices, apparatuses, appliances, systems or networks”.
594 The abstract and opening paragraphs describe a portable or embedded device for allowing authorised users to access a secure apparatus, device, network or system. The device comprises an integrated circuit (IC) that enables biometric authentication of a user’s fingerprint locally on the device and provides secure communication with the apparatus, device, network or system regardless of whether it is local or remote to the device. Mathiassen identifies a number of embodiments, but in closing submissions Apple focussed upon an embodiment where the invention is applied to car security systems (car security system embodiment).
595 The automotive application of the invention is explained by reference to figures 2b (not extracted), a diagram of an integrated circuit, and figures 8 and 9, being illustrations of the invention applied in a portable door control unit and embedded in a gear stick or steering wheel:
596 In this respect Mathiassen provides at [0147] to [0149]:
The door control (central locking system) is outlined in FIG. 8. The door control, being a portable device (20), comprises an external housing (20) which contains a fingerprint sensor (5) coupled to a miniature printed circuit board (21) on which is mounted the IC (1). The remote control (20) further comprises a battery (25) for power supply retained in the housing (20) by a removable lid (26). The battery (25) is connected to the PCB (21) by wires. The remote control is also equipped with a wireless 2-way transceiver (27), and all the active components are connected to the IC (1) by cables (23) via the PCB (21). This remote control for the car doors can be made very compact, where the size of the housing (20) is determined by the size of the battery (25). Thereby the physical size of the housing may be compressed to the size of a key-ring holder.
Inside the car is mounted another embedded device (15) (refer FIG. 6) e.g. mounted on the gear stick (71) or on the steering wheel (72) for ignition control of the engine.
These two elements; the portable remote door control (20) and the embedded ignition control (15) are both connected to a central computer in the car. The connection of the portable remote door control (20) is by 2-way wireless transceiver (27), while hard wires to the central computer (not shown) of the car connect the embedded ignition control (15).
597 Mathiassen describes at [0150] to [0162] how a dealer sets up the “protected mode” of the car system when a car is sold, which involves the dealer downloading the seed for the SKG (or “secure key generation”), which is a reference to a type of encryption-based security measure utilised in the portable door control and the embedded ignition control.
598 Mathiassen then describes, at [0164] to [0165], how the owner of the car enrols their fingerprint on the door control:
Then the car owner will enrol one or more of his fingers on the portable door control unit (20). This involves successful capturing of a minimum of images (say three) reduced to master minutiae tables by the pre-processing block (5C) and the central processor (2) of the IC (1) on the portable device (20). These master minutiae tables will be stored in the non-volatile memory (7A) of the IC (1).
This first person to enroll his fingerprint on the portable door control (20) becomes the “owner” of the car, in the sense that he becomes the system administrator. When he has successfully enrolled on the portable door control (20) he will countersign by his fingerprint to authorize and initiate encryption of his master minutiae table(s) from the IC (1) on the portable door control (20) via the door locks and the central car computer (not shown) to the IC (1) of the embedded ignition control (15) of the car.
599 Mathiassen then, in detail, describes how the master minutiae table(s) are sent from the portable door control to the embedded ignition control via the central computer (at [0166] to [0173]).
Such transfer of authorised master minutiae will start with retrieving the unique seed of the car from non-volatile memory of the IC of the portable door control (20). The seed will be fed to the secure key generation SKG block (8A) of the IC (1) to generate a valid password.
This password will then be fed to the encryption block (8B or 8C) of the IC (1) at the portable door control (20), initiating encryption of the master minutiae tables of the “owner’s” finger(s). The encrypted message will be transmitted wirelessly from the portable door control (20) by means of two-way wireless transceiver (27) via the door locks to the central computer of the car. Note that such enrolment is the only event when encrypted tables are transmitted from the portable door unit. At normal opening of the door matching minutiae will only be used to authorize encryption and transmission of straight commands, such as “open door” or “lock door”.
If the central computer of the car is capable of successfully decrypting the message from the portable door control it will forward the encrypted message to the embedded ignition control (15). Failure by the central computer of the car to decrypt the message (e.g. by non-matching temporary pseudo-random password) will terminate the communication procedure.
When the encrypted message containing the master minutiae tables of the car owner reaches the embedded ignition control (15) it will be decrypted.
The unique seed of the car will be fetched from the non-volatile memory (7A) of the IC (1) of the embedded ignition control (15).
The seed will be inputted to the secure key generation SKG block (8A) to generate a pseudo-random temporary password.
The pseudo-random temporary password will be fed to the encryption block (8B or 8C) of the IC (1) to start decryption of the encrypted message.
The "owner's" master minutiae tables of his finger(s), as retrieved from the decrypted message, will be stored in the non-volatile memory (7A) of the IC (1) of the embedded ignition control (15).
600 Mathiassen goes on to describe how the car owner accesses the car by reference to the following steps.
601 The owner swipes a finger across the sensor (5) of the portable door control (20), which triggers a signal from the sensor to the wake-up circuit (5B) of the IC (1), powering up the IC. The pre-processing block (5C) will reduce the fingerprint image to a reduced intermediate format, feeding it to the processor (2). The processor will then reduce the captured and processed fingerprint image to “compact master minutiae format”.
602 The next steps are described, at [0180] to [0188], as follows:
The processor (2) will then compare this access minutiae table with the master minutiae table(s) pre-stored at time of enrolment in non-volatile memory (7).
In case of a match the process will be allowed to continue. If no match, the process will be aborted.
Provided the processor (2) established a match between the access attempt and one of the resident master minutiae tables, the processor will proceed to open (or lock) the car doors.
The processor (2) will fetch the seed from the non-volatile memory (7A) and feed it to the SKG block (8A).
The SKG block will generate a valid, and temporary, password that will be input to the encryption block (8B or 8C).
The processor will issue the “open door” command to the encryption block (8B or 8C) that in turn will encrypt it based on the valid, and temporary password from the SKG block (8A).
The encrypted “open door” command will then be wirelessly transmitted by the transceiver (27) from the portable door control (20) to the embedded ignition control (15) via the transceivers of the door locks and the central car computer.
The encrypted message will be decrypted by the embedded ignition control (15) by its processor (2) on its resident IC (1) fetching the seed from the non-volatile memory (7A). The seed will be entered into the SKG block (8A) to generate the identical, and temporary password fed on to the encryption block (8B or 8C). If the decrypted message confirms a valid and authenticated “open door” command, a similar encrypted command will be relayed to the door locks by the car computer.
Alternatively, the decryption and authentication algorithms may be performed on the central car computer control instead of on the embedded ignition control.
603 The specification then notes at [0189]:
The important part is that an authenticated fingerprint triggers the portable door control (2) and the embedded ignition control (15) to generate encrypted communication procedures, involving handshake procedures, fully compatible with the communication procedures of the central computer of the car, and the door locks. The benefit of the invention is that no fingerprints have to be transmitted between the car system security components (except for enrolment), but triggers the prevailing, secure communication protocols.
9.5.2 The submissions
604 Apple’s written submissions contend that three embodiments described in Mathiassen anticipate the asserted claims, however, its oral submissions focussed only upon the car security system embodiment.
605 CPC submits that in Mathiassen it is unclear what precise system the car security system embodiment discloses and that, on its construction of the term, there is no relevant disclosure of an accessibility attribute. Although Mathiassen discloses a car with a door control and another embedded device for ignition control (mounted on the gear stick or steering wheel, for example), it fails to disclose whether authentication is required for ignition control and, if so, how it is achieved. As such, Mathiassen does not disclose multiple conditions of access to a controlled item because it does not disclose a system that provides access to the vehicle but not to ignition activation. CPC further submits that there is no disclosure of what happens after matching has occurred and, therefore, whether there is a provision of an accessibility attribute.
606 CPC also submits that there is no disclosure of a system that emits a secure access signal, the administrator integers are absent and the series feature is not disclosed.
607 Apple disputes each of these propositions and contends that on CPC’s construction each of the accessibility attribute, secure access signal, administrator signature and series feature integers is disclosed.
9.5.3 Consideration
608 Mathiassen explains the car security system embodiment by reference to two different versions of hardware, first, a key to the doors (central locking system), and secondly, for ignition control (or blocking). The disclosure indicates that both would be connected to a central computer in the car. It is apparent that the description of the operation of the biometrics system set out from [0150] to [0188] applies to both.
609 In operation, both the remote door control (depicted in figure 8 at (20)) and the embedded ignition control (depicted in figure 9 at (15)) are connected to a central computer in the car.
610 The steps required for the “owner” to obtain access to the car are set out at [0175] to [0188]. This involves the portable door control sensor taking an image of a fingerprint, reducing it to “compact master minutiae format” and comparing the access minutiae table with the pre-stored master minutiae table(s) created at the time of enrolment. Where there is a match, the steps at [0182] to [0185] describe how the “open door” command is prepared for transmission to the central car computer. In short, if a match is established, the portable door control processor obtains the unique identifier (“seed”) of the car and feeds it to the SKG block which leads the processor to issue the “open door” command to the encryption block that will in turn encrypt it based on the temporary password from the SKG block.
611 The steps at [0186] and [0187] then indicate that the “open door” command is transmitted to the embedded ignition control, which is responsible for decryption of the command, so that it can be relayed by the central car computer to the car locks. The passage at [0188] clarifies that, whatever the role of the embedded ignition control in one embodiment may be, in an alternative embodiment the decryption and authentication algorithms may be performed on the central car computer instead. That must be understood to mean that the “open door” command is executed by the central car computer rather than the embedded ignition control.
612 Apple first relies on the communications mentioned above to demonstrate that the “open door” command produced as a result of the biometric match in the portable door control results in the opening of the car door. This, it submits satisfies the first limb of the accessibility attribute definition, on CPC’s construction, because it provides access to a secured item. Secondly, it submits that the second limb is satisfied based on CPC’s construction as access is only provided to part of the functionality of the secured item – here the car – because in order to obtain access to the ignition of the car, an additional biometric match is required. It relies on a passage in the oral evidence of Associate Professor Boztas in this regard, where he accepted that activating the ignition was a separate process requiring use of the fingerprint sensor contained in the embedded device in the vehicle, with which Dr Dunstone agreed.
613 These views accord with the disclosure of the separate ignition control device. Although in his oral evidence Dr Dunstone accepted that one interpretation of the embodiment was that once the car doors are unlocked nothing further is required to be done to access the ignition, in my view, the better view is that each of the unlock door and ignition control functions have separate work to do. This is supported by a reading of the disclosure as a whole, particularly by reference to the description of the drawings at [0189]. It was, as I understand it, the preferred view of the experts in their oral evidence. As a consequence, on CPC’s construction of “controlled item” and “accessibility attribute”, the integer is disclosed.
614 I also accept that the transmission of the encrypted “open door” command satisfies the requirements of a secure access signal (on CPC’s construction of that term).
615 In relation to the administration signature integer, the disclosure at [0165] conveys that the first person to enrol a fingerprint on the portable door control becomes the “system administrator”. I have in section 4.8.2 noted that the term “administrator” formed part of the common general knowledge and described someone with the access privileges needed to perform administrative functions, such as enrolling new users. CPC submitted that an “administrator” is simply an individual who has been granted special privileges to oversee or manage the system and that the claims do not limit the way in which the system may recognise a signature as one belonging to an administrator. On that basis, the disclosure in Mathiassen is sufficient to meet this integer.
616 In relation to the series feature, Apple accepts that this integer is not disclosed on its construction of the term but contends that it is disclosed on CPC’s construction. While Mathiassen discloses at [0164] that enrolment involves “successful capturing of a minimum of images (say three) reduced to master minutiae tables”, there is no disclosure that the user’s finger be placed on the sensor a sufficient number of times, and for a sufficient number duration, to obtain a quality series of entries that could be mapped onto a mathematical representation. Accordingly, I reject the contention that this integer is disclosed.
617 Although not addressed in its oral submissions, Apple in its written submissions relies on two further embodiments in support of its contention that the “accessibility attribute” integer is disclosed. For brevity, I provide my short form conclusion in relation to each below.
618 The first involves the use of a USB dongle, which is connected to a personal computer for accessing a remote intranet server (network embodiment) and is disclosed in Mathiassen at [0059] to [0107]. The USB dongle includes a fingerprint sensor. It may be inserted into a USB port and the user may apply their finger to the sensor to obtain an image that is then processed and transferred to the central processor via a high-speed bus. The central processor then compares the processed representation of the image obtained with pre-stored fingerprint representations to establish whether there is a positive match. If a positive match is identified, the central processor calculates a secure key, which is input into an encryption block for encryption of a message / communication consisting of several elements: a device number and IP address of the USB dongle, SKG (Secure Key Generation) key number, the secure key number, the user ID and optionally a “PKI verification”. Each of those elements, save for the device number and SKG key number, are encrypted. A signal including the target IP address and the encrypted message / communication will be sent to an external unit, network or system (being the “target server”) through a communication interface. When the information is received by the target server, it decrypts the message and (broadly), if a relevant match is achieved, generates a key. Depending on the profile of the user, access is granted to the whole of or part of the intranet server.
619 There is no dispute that the USB dongle represents the transmitter sub-system and that the target server is the receiver sub-system. The signal generated in response to biometric authentication from the IC (within the USB dongle) and conveyed to the target server will grant partial or complete access to the intranet (being the controlled item). On the basis of the construction advanced by CPC, an accessibility attribute is provided by the transmitter sub-system and received by the receiver sub-system. The message so sent is encrypted, and thereby additionally discloses the requirement of the asserted claims that it contain a secure access signal. Apple does not advance a submission that either the administrator signature integers or the series feature is disclosed in this embodiment.
620 The second further embodiment involves a medicine cabinet, access to which requires biometric authentication as described at [0122] to [0143]. Although Apple submits that this embodiment discloses an accessibility attribute on CPC’s construction of that term, Apple accepts that this embodiment can only anticipate the asserted claims if CPC’s contention that the transmitter sub-system and receiver sub-system can overlap in one device is also accepted. As I have rejected this premise, anticipation would require me to assume yet further aspects of construction that I have rejected, which I decline to do.
9.5.4 Conclusion in relation to Mathiassen
621 I have found that Mathiassen discloses in the car security system and network embodiments the features required in the “accessibility attribute” and “secure access signal” integers of the asserted claims, on CPC’s construction of those terms. Additionally, I have found that Mathiassen also discloses – on CPC’s construction of the terms – the “administrator signature” integers by the car security system embodiment, but not the series feature.
9.6 Wuidart
622 Apple relies on the disclosure in Wuidart as an anticipation both on its preferred construction of the term “accessibility attribute” and also on CPC’s construction.
623 CPC disputes that the integer is disclosed on either construction and also disputes that Wuidart discloses integers containing: (a) a secure access signal; (b) means of providing conditional access to a controlled item; (c) the series feature; and (d) the administrator signature features.
9.6.1 The disclosure
624 Wuidart is entitled “security system” and concerns security systems that have what it describes as a “fixed terminal” and a “portable unit” that delivers a signal to the fixed terminal, an example of the former being a vehicle and an example of the latter being a portable fob or key for opening the vehicle.
625 The “Background of the Invention” describes how in prior art systems the portable unit generally transmitted a lock or unlock signal to the fixed terminal and typically includes a fixed or changing code that must be recognised as valid by the fixed terminal in order for the signal to prompt the locking or unlocking of the doors of the vehicle. Whilst this provides some security, mere physical possession of the portable unit is generally sufficient to effect the unlocking of the vehicle. To overcome this problem, a security system can be associated with its authorised user or users so that only they can unlock the vehicle. For example, the system can include means for measuring a biometrical signature of an authorised user, such as a fingerprint, iris of an eye or audiometrical spectrum of a voice. While this provides some advantages over prior art systems, there remains a risk that the vehicle will be accidentally unlocked. For example, when the authorised user inadvertently uses a word or series of words that prompts the unlocking of the vehicle.
626 To overcome these drawbacks, the “Summary of the Invention” provides that the portable unit include a detector, a measurement device and a signal generator. The detector generates an activation signal when active intervention by a user is detected and the measurement device measures a biometrical signature of the user. When the activation signal and a measurement signal are both produced within a specified temporal window, the signal generator generates the lock or unlock signal if the measured biometrical signature corresponds to that of an authorised user.
627 The “Detailed Description of the Preferred Embodiments” identifies various examples of the system of the invention. It explains that the portable unit is designed to be carried and operated by the authorised user and other authorised users can use the same portable unit or another portable unit that is assigned to them for the same function.
628 The operation of the system is primary described by reference to figures 2 and 3, which are as follows:
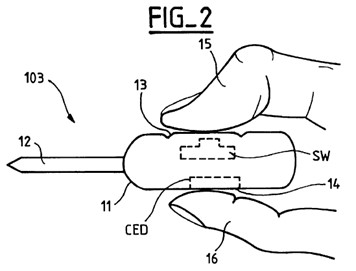
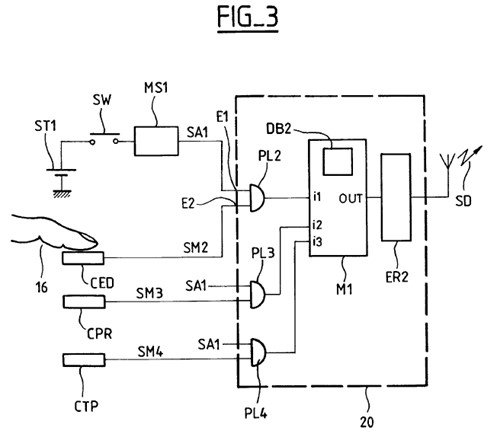
629 The portable unit (103) and control circuit (20) in one embodiment are described as follows (column 4 line 25 to 48):
Additionally, the portable unit includes measurement means CED, preferably in the form of a fingerprint sensor, for measuring a biometrical signature of the user and delivering a measurement signal SM2. The portable unit also includes generation means for generating the unlock signal SD when the activation signal SA1 and the measurement signal SM2 are produced within a specified temporal window and the measured biometrical signature corresponds to an authorized user….
The control circuit 20 also includes a microcontroller M1 that has a memory DB2 in which biometrical signatures of one or more authorized users are stored (e.g., the fingerprint of the thumb, index finger, or any other finger). Preferably, each biometrical signature is stored as a matrix of binary data and the biometrical signatures of each authorized user are stored in distinct areas of the memory DB2 that are referenced by a user number. For example, five distinct areas could be reserved for storing the biometrical signatures of five different authorized users (e.g., the members of a family) with each user being fictitiously associated with a user number (e.g., 1, 2, 3, 4 or 5)…
630 A further embodiment is later described at column 5 line 54 to column 6 line 12:
In one embodiment of the present invention, the unlock signal SD includes an impersonal code to identify the authorized user whose biometrical signature has been measured and recognized to be valid. The impersonal code can simply be the corresponding user number (e.g., 1, 2, 3, 4, or 5 as described above). By transmitting the impersonal code, selected convenience functions in the vehicle can be activated when the unblock signal SD is received. For example, such functions could include the adjusting of the positions of the seats and the positions of the rearview mirrors, the setting of a selected temperature of the onboard thermostat, the tuning of the radio to a particular station, and so on according to predefined values corresponding to the preferences of one of the users.
In such embodiments the portable unit transmits an impersonal number such as 1, 2, 3, 4, or 5 that merely identifies one of the authorized users from among the set of authorized users, and not information relating to the user’s biometrical signature (hence the expression “impersonal code”). Thus, the data elements pertaining to the authorized user’s biometrical signature cannot fall into the hands of an ill-intentioned third party that intercepts the unlock signal SD. Preferably, the unlock signal SD also includes a code for identifying the vehicle associated with the portable unit so that a specified portable unit can be associated with a single vehicle.
631 Wuidart goes on, at column 6 lines 13 to 26, to address the fixed terminal:
The exact structure, features, and operation of the fixed terminal (e.g., a centralized door locking and unlocking unit) are not critical to the present invention and can conform to conventional fixed systems. At the least, the selection and design of the fixed terminal are within the scope of one of ordinary skill in the art so the fixed terminal will not be described in greater detail. Furthermore, the lock/unlock signal can also include a standard type of open-ended code (i.e., a code whose value changes with each transmission). Such a code can be used to hinder fraudulent attempts at picking up and recording (with appropriate electronics) the lock/unlock signal when it is normally transmitted by an authorized user and then subsequently and fraudulently reproducing the signal to unlock the vehicle.
9.6.2 The submissions
632 CPC submits that Wuidart does not disclose an accessibility attribute for several reasons. First, there is no disclosure or delineation of how the fixed or changing code, once transmitted from the portable unit, is dealt with by the fixed terminal to effect the unlocking, nor where the relevant determination of access takes place such that it may take place at the receiver sub-system, rather than, as required by the asserted claims, at the transmitter sub-system. Secondly, two signals (being the activation signal and measurement signal) are required to be output before the unlock signal is generated, rather than simply biometric authentication. Thirdly, there is no disclosure that the unlock signal contains material as to whether and under which conditions access should be granted rather than simply being a binary “lock/unlock signal”. Further, CPC contends that, for the same reason, there is no form of “conditional access” within the meaning of that term as it appears in claims 1, 39 and 41 of the 293 patent. CPC also submits that there is no disclosure of either the administrator signature integers or the series feature.
633 Apple contends that the accessibility attribute is disclosed on both its preferred construction of that term and on CPC’s construction. It says that on its construction, the unlock signal in combination with the user number amounts to an accessibility attribute because it establishes both whether access is granted and imposes conditions applicable to the access granted (by adjusting the thermostat, seats, and mirrors to specific settings according to the user number). It accepts that the administrator signature integers are not disclosed but contends that the series feature is disclosed if CPC’s construction of that term is accepted.
9.6.3 Consideration
634 The primary area of contention in relation to Wuidart is whether it discloses a system in which there is an accessibility attribute within the meaning of the asserted claims.
635 In one example of operation described in columns 4 and 5, the portable unit includes a switch (SW) which may be activated by the user’s thumb (15) press and which subsequently activates a timer (MS1) to output the activation signal (SA1). The timer holds the activation signal in the active state for a specified period during which the fingerprint sensor (CED) in the portable unit must measure the biometric signature of the user and deliver a measurement signature (SM2) to the microcontroller (M1) in that unit. As illustrated in figure 3, the activation signal and the measurement signal must be generated within a specified temporal window to enable the microcontroller to assess, as against the signatures stored in memory (DB2) whether there is a biometric match. A successful match will result in the transmission of the unlock signal (SD) from the control circuit to the fixed unit.
636 In the embodiment described in the passage at column 5 line 54 to column 6 line 12, Wuidart discloses that a person whose biometric signature has been measured and recognised to be valid will generate as unlock signal (SD) containing an “impersonal code” that identifies the user as against other authorised users, without needing to convey the user’s biometric information.
637 In these embodiments, the portable unit will be the transmitter sub-system and the fixed terminal – described in Wuidart as, for example, a centralised door locking and unlocking unit – will be the receiver sub-system.
638 In relation to accessibility attribute, CPC first contends that Wuidart does not sufficiently disclose whether the transmitter sub-system alone determines whether and on which conditions access should be granted, such that it could be said to produce an accessibility attribute.
639 However, the receiver sub-system disclosed by Wuidart, being the fixed terminal, receives the unlock signal from the portable unit and then decodes it – including any encryption – to give effect to the unlock command. I do not consider that the fact that the receiver sub-system must take steps to decrypt or otherwise interpret an “accessibility attribute” that is provided by the transmitter sub-system will take it outside the scope of the claims.
640 CPC next contends that the disclosure of Wuidart requires two signals to be produced before the unlock signal is generated (an “activation signal” and a “measurement signal”) instead of only biometric authentication, which it suggests means that no accessibility attribute is disclosed. The difficulty with this submission is that the embodiment in Wuidart that I have described above makes plain that the transmission of the unlock signal is dependent upon receipt of a legitimate biometric signal. The fact that the unlock signal is also dependent upon the legitimate biometric signal being received within a specified time does not take the disclosure beyond the requirements of the integer.
641 Apple contends that where the unlock signal includes an “impersonal code”, as described in the passage at column 5 line 54 to column 6 line 12, Wuidart describes an “accessibility attribute” within the construction of that term that I have accepted. It submits that this is because such an unlock signal establishes both whether access is granted and at the same time imposes conditions applicable to the access granted, such as by adjusting the thermostat, seats and mirrors to specific settings according to the user number. CPC contends that these matters are not relevant to “access” and cannot be regarded as a “condition” of access to the controlled item (here, a vehicle), such that there is no disclosure that the unlock signal contains material also relating to the conditions of access. The correctness of that submission depends on what amounts to a condition of access.
642 It will be recalled that the patents define “accessibility attribute” as establishing “whether and under which conditions access to the controlled item 111 should be granted to the user”. Examples of “access attributes” are then given in the specification, at page 14 line 20 to page 15 line 1, that include “a duress attribute (granting access but with activation of an alert tone to advise authorities of the duress situation), alert attribute (sounding a chime indicating that an unauthorised, but not necessarily hostile, person is seeking access) and a telemetry attribute, which represents a communication channel for communicating state information for the transmitter sub-system to the receiver sub-system such as a ‘low battery’ condition”. Each of these provides conditions referable to the grant of access.
643 I see no difference in principle between a condition of access that sounds a chime indicating that a person of a certain type has entered and a condition that would turn on the lights or another feature of the building. In the context of the definition provided in the specification of “accessibility attribute” and the examples provided on page 14 of the specification of the patents in suit, both fall within the meaning of “conditions of access”.
644 Accordingly, I accept Apple’s submission that Wuidart discloses an invention that includes an accessibility attribute within the definition of that term that I have accepted and also, in the alternative, the definition propounded by CPC. In that context, having regard to the meaning of the term “conditional access” that appears in integer (13) of claim 1 of the 293 patent (where there is a receiver sub-system comprising; “(12) means for receiving the transmitted secure access signal; and (13) means for providing conditional access to the controlled item dependent upon said information”) and the equivalent integers in claims 39 and 41 of the 293 patent, I also find that the requirement of conditional access is met.
645 Apple accepts that the administrator signature integers are not disclosed in Wuidart. It submits that although the series feature is not expressly disclosed in Wuidart, on CPC’s construction of the integer, its presence may be implied. However, for the reasons given in relation to the equivalent argument made in relation to the disclosure of Hamid, I reject that submission.
9.6.4 Conclusion in relation to Wuidart
646 For the reasons given above, I find that Wuidart anticipates all of the claims that include the accessibility attribute integer on both my preferred construction and also the construction of that term as advanced by CPC. I find, however, that none of the claims including the administrator signature integers and/or series feature is anticipated.
10. LACK OF INVENTIVE STEP
647 The case based on lack of inventive step advanced by Apple in closing submissions was premised wholly on the basis that the Apple Devices infringed the patents having regard to the construction of accessibility attribute. I have found that the Apple Devices do not infringe the patents, in part because the accessibility attribute integer is absent from the devices. Having regard to the position adopted by Apple, it is unnecessary for me to address the inventive step case advanced.
11. MANNER OF MANUFACTURE
648 Apple pleads, in its cross claim, that the alleged invention so far as claimed in each of the asserted claims is not a patentable invention within s 18(1)(a) of the Patents Act on the basis that it is not a manner of manufacture within s 6 of the Statute of Monopolies (1623) (21 Jac 1, c 3). In its particulars, Apple contends that the alleged invention is, in substance, an abstract idea, mere scheme, mere intellectual information, computerised business method and/or an idea for a computer program that involves no contribution of a technical nature or no technical advance over the prior art.
649 In its closing submissions, Apple emphasises that this ground depends entirely upon the Court accepting CPC’s construction of the transmitter sub-system, receiver sub-system and accessibility attribute integers. Apple submits that, considered as a matter of substance, the invention so claimed is a mere scheme or idea for a secure access system in an uncharacterised or generic electronic processing device which does not give rise to patentable subject matter, citing various authorities including in particular Encompass Corp Pty Ltd v InfoTrack Pty Ltd [2019] FCAFC 161; (2019) 372 ALR 646 at [88], [101], [107]–[108]. Apple submits that the construction advanced by CPC is such that: (a) the invention disclosed and claimed is untethered to any particular or discrete components; (b) the entire secure access system can exist within a single computer system; and (c) the transmitter sub-system and receiver sub-system have no physical or finite hardware or software components and are merely characterised by their functionalities such that the transmitter sub-system and receiver sub-system may have overlapping components and functions. So construed, the invention does not involve a manner of manufacture as the claims merely require that the secure access system be “suitably programmed” to implement the functionality described.
650 CPC contends that, regardless of the construction adopted, the invention claimed in the asserted claims does not fall within the category of cases identified as a “mere scheme” but rather are for a manner of manufacture, citing Technological Resources Pty Limited v Tettman [2019] FCA 1889; (2019) 375 ALR 185 at [143]–[150] (Jagot J). CPC submits that there is evidently a physical effect (for example, the use of a biometric sensor), which gives rise to a useful result (enrolling signatures into a database and/or providing secure access to a controlled item).
651 I have in sections 4 and 6 addressed CPC’s construction arguments, first in the context of the asserted claims alone and later in the context of its infringement case. In each of those sections I have rejected the contentions advanced by CPC as to the meaning of transmitter sub-system, receiver sub-system and accessibility attribute. Apple advances no submission to the effect that, on the basis of the construction of the claims that I have preferred, the asserted claims do not amount to a manner of manufacture. Having regard to these matters, in my view, it is not necessary to consider, on an hypothetical alternative construction, whether the claims lack a manner of manufacture.
12. SECTION 40 CHALLENGES TO VALIDITY
12.1 Fair basis
652 Apple pleads, in its cross claim, that the asserted claims are not fairly based within the requirements of s 40(3) of the Patents Act on four bases, each of which is addressed below.
653 Section 40(3) provides:
The claim or claims must be clear and succinct and fairly based on the matter described in the specification.
654 As I noted in Merck Sharp & Dohme Corporation v Wyeth LLC (No 3) [2020] FCA 1477; (2020) 155 IPR 1 at [496], fair basis involves a comparison between the claims made in the patent and what is disclosed in the specification in order to determine whether there is a real and reasonably clear disclosure of the invention claimed, or whether the invention claimed travels beyond the invention described: Bitech Engineering v Garth Living Pty Ltd [2010] FCAFC 75; (2010) 86 IPR 468 at [39]. The enquiry as to the disclosure of the body of the specification is whether broadly, in a general sense, it describes the invention as claimed: Lockwood No 1 at [69]. This involves consideration of what the specification discloses as a matter of substance.
655 In Lockwood No 1 the High Court identified, at [68]–[69], what has become the seminal test for lack of fair basis:
Erroneous principles. The comparison which s 40(3) calls for is not analogous to that between a claim and an alleged anticipation or infringement. It is wrong to employ “an over meticulous verbal analysis”. It is wrong to seek to isolate in the body of the specification “essential integers” or “essential features” of an alleged invention and to ask whether they correspond with the essential integers of the claim in question.
“Real and reasonably clear disclosure”. Section 40(3) requires, in Fullagar J’s words, “a real and reasonably clear disclosure.” But those words, when used in connection with s 40(3), do not limit disclosures to preferred embodiments.
“The circumstance that something is a requirement for the best method of performing an invention does not make it necessarily a requirement for all claims; likewise, the circumstance that material is part of the description of the invention does not mean that it must be included as an integer of each claim. Rather, the question is whether there is a real and reasonably clear disclosure in the body of the specification of what is then claimed, so that the alleged invention as claimed is broadly, that is to say in a general sense, described in the body of the specification.”
Fullagar J’s phrase serves the function of compelling attention to the construction of the specification as a whole, putting aside particular parts which, although in isolation they might appear to point against the “real” disclosure, are in truth only loose or stray remarks.
(Footnotes omitted)
656 First, Apple contends that claims 27, 29 and 37 of the 293 patent are not fairly based because they contain no reference to any receiver sub-system, nor do they require any cooperation between a transmitter sub-system and receiver sub-system in order to provide access to the controlled item, yet the substantive disclosure in the specification of the invention necessarily includes a receiver sub-system. It submits that the disclosure of the specification includes descriptions of the function of receiving the transmitted secure access signal, ascertaining the accessibility attribute information transmitted and providing access to the controlled item. It submits that the only system disclosed in the 293 patent is one where there is both a transmitter sub-system and a receiver sub-system where the receiver sub-system performs the abovementioned functions. Accordingly, a claim without a receiver sub-system involves an entirely different structure to that disclosed in the specification, such that it travels beyond the disclosure and is not fairly based.
657 These submissions advanced by Apple may be examined by reference to claim 27 of the 293 patent, which for convenience I repeat below:
(1) A method for providing secure access to a controlled item, the method comprising the steps of: (2) enrolling, by a transmitter sub-system, relevant signatures into a database using a biometric sensor, by receiving a series of entries of the biometric signal, (3) said series being characterised according to at least one of the number of said entries and a duration of each said entry, (4) mapping said series into an instruction, and (5) enrolling relevant signatures into the database according to the instruction; (6) receiving, by the transmitter sub-system, a biometric signal; (7) matching, by the transmitter sub-system, the biometric signal against members of the database of biometric signatures to thereby output an accessibility attribute if the matching is authenticated; (8) emitting, by the transmitter sub-system, a secure access signal conveying information dependent upon said accessibility attribute; and (9) providing conditional access to the controlled item dependent upon said information.
658 It may be seen that the claim defines in some detail a method for providing secure access to a controlled item involving the steps of enrolling signatures via a transmitter sub-system as described in integers (2) to (5), matching, by the transmitter sub-system a biometric signal received against a database of biometric signatures, as described in integers (6) and (7), and emitting, via the transmitter sub-system a secure access signal conveying information dependent on the accessibility attribute as described in integer (8). Unlike the other asserted claims, save for claims 29 and 37 of the 293 patent, claim 27 does not require a receiver sub-system, instead including as integer (9) a broad requirement that the method provide “conditional access to the controlled item dependent upon said information”.
659 CPC submits that it should be inferred from the language of integer (9) that there must be a receiver capable of receiving the information that is conveyed by the transmitter sub-system.
660 This submission appears to me to be correct. Integer (9) requires that conditional access be provided to the controlled item “dependent upon” the information contained in the secure access signal. That information (in the form the secure access signal) must be received from the transmitter sub-system. The functional necessity of the claim is such that the information must be received and interpreted prior to access to the controlled item being granted. Such information must be received by something meeting the functional definition of a receiver.
661 Secondly, Apple contends that the disclosure of the patents is limited to a system in which the transmitter sub-system and the receiver sub-system are distinct pieces of hardware. If, contrary to this position, the transmitter sub-system and receiver sub-system do not need to be separate from each other, nor be in physically distinct hardware, the claims are not fairly based.
662 Several passages in the specification identify that the invention may be implemented not only using a physical mechanism, but also by the provision of logical access such as in the case of a personal computer. On page 26 from lines 3 to 13 (set out in section 3 above) the specification identifies that the secure access methods are preferably practiced using a computer system arrangement and may be implemented as software. Having regard to these disclosures, I am not persuaded that the claims lack fair basis for the reason advanced by Apple.
663 Third, Apple contends the disclosure of the patents in suit is limited to a system in which, in response to a particular biometric signal, the transmitter sub-system produces an accessibility attribute which must establish whether to provide access and which conditions are imposed. It submits that CPC’s position on construction appears to be that an accessibility attribute can “arise” where, in the “context” of the system as a whole, access is provided to only part of a device, and on that construction, contends there is no disclosure in the specification that an accessibility attribute might be provided in that manner, or how it might be done.
664 I have addressed the meaning of “accessibility attribute” and “controlled item” elsewhere in these reasons. Having regard to my construction of these terms the submission advanced by Apple does not arise.
665 Fourth, Apple submits that on CPC’s construction of the series feature, it relates to presenting a fingerprint or other biometric to the sensor multiple times in order to produce multiple scans, the information from which is combined into a template. If that construction is adopted, Apple submits that the claim is not fairly based.
666 I have, in section 4.9 above, declined to adopt the construction of the series feature integer advanced by CPC and accordingly it is also unnecessary to address this ground further.
12.2 Insufficiency
667 In a faintly raised objection, Apple contends that the patents lack sufficiency within s 40(2)(a) of the Patents Act as the specification does not fully describe the invention as claimed in each of the asserted claims. In closing submissions, this ground distilled to the contention that because Associate Professor Boztas appeared to suggest that he may have encountered technical difficulty in implementing the concept of an accessibility attribute and that, as the specification of the patents do not resolve that difficulty, the claims are insufficient.
668 The faint suggestion was made in JER1 in the context of considering a prior art document. It was not followed by any oral evidence, and no oral evidence to similar effect was led by Dr Dunstone. Indeed, Dr Dunstone’s evidence was that it was obvious to implement the invention as claimed. I am not satisfied that this ground of invalidity is made out.
12.3 Lack of clarity
669 Section 40(3) of the Patents Act also requires that the claims of a patent be clear and succinct.
670 Apple contends that the asserted claims are invalid for lack of clarity having regard to the CPC’s construction of the term “accessibility attribute” which, it submits is an abstract concept said to arise from the context of a system rather than being an identified element provided by an identified transmitter sub-system.
671 I have considered the construction of that term earlier in these reasons. No contention is advanced that, having regard to the construction that I have adopted, the claims are invalid for lack of clarity. Accordingly, this ground does not arise.
13. CONCLUSION
672 For the reasons set out above, I have concluded that CPC has failed to establish that any of the Apple Devices fall within the asserted claims and that accordingly its infringement case must be dismissed. Apple’s cross claim was, in large part, advanced defensively and so was dependent upon findings, contrary to its primary case, that its devices were found to fall within the scope of the asserted claims. My findings that the Apple Devices do not fall within those claims leads to the conclusion that most, but not all, of the Apple cross claim has failed.
673 I will direct that the parties confer and produce draft short minutes of order giving effect to these reasons and providing for timetabling of next steps in the proceedings including in relation to the question of costs and confidentiality issues. The parties are also directed to identify the portions of these reasons for judgment over which confidentiality is claimed so that a redacted form of the judgment suitable for publication may be produced.
I certify that the preceding six hundred and seventy-three (673) numbered paragraphs are a true copy of the Reasons for Judgment of the Honourable Justice Burley. |
Associate:
Dated: 15 May 2025
SCHEDULE OF PARTIES
NSD 998 of 2021 | |
Cross-Claimants | |
Second Cross-Claimant: | APPLE INC. |




