Federal Court of Australia
Hytera Communications Corporation Ltd v Motorola Solutions Inc [2024] FCAFC 168
Appeal from: | Motorola Solutions, Inc. v Hytera Communications Corporation Ltd (Liability) [2022] FCA 1585 |
File number: | NSD 675 of 2023 |
Judgment of: | BEACH, O'BRYAN AND ROFE jJ |
Date of judgment: | 18 December 2024 |
Catchwords: | PATENTS – indirect infringement – appellant found to have infringed respondent’s patent (Australian Patent No 2005275355) relating to digital mobile radios (DMRs) using Time Division Multiple Access (TDMA) technology to divide frequency channel – appeal against finding of infringement – disputed issues of construction – appeal against finding of validity – whether the invention claimed involved an inventive step – whether the invention claimed is useful – whether the invention claimed is a manner of manufacture – appeal dismissed PATENTS – validity – respondent’s patent (Australian Patent No. 2006276960) relating to DMRs using TDMA technology found to be invalid by reason that the invention claimed did not involve an inventive step – cross-appeal against that finding dismissed – cross-contentions concerning manner of manufacture and infringement also dismissed COPYRIGHT – indirect infringement - respondent owner of Australian copyright in 11 computer programs in source code – appeal against finding of infringement by the importation into Australia of DMR devices containing firmware in object code, where firmware compiled from appellants’ source code in China and installed into DMR devices in China, and where appellants’ source code developed using respondent’s source code – whether the appellants copied a substantial part of the respondent’s copyright works – whether fact that copied parts of the respondent’s copyright works derived from earlier versions of the respondent’s computer renders them not original for the purposes of infringement, such that the copied parts are not a substantial part – whether appellants otherwise copied a substantial part of the respondent’s copyright works – the correct approach to assessing the copying of a substantial part – where appellants deliberately deleted source code to suppress evidence which might assist in a copyright infringement suit – application of the maxim omnia praesumuntur contra spoliatorem (all things are presumed against the wrongdoer) – primary judge’s approach to assessing the copying of a substantial part shown to be in error COPYRIGHT – requirement of knowledge for the purposes of ss 37 and 38 of the Copyright Act 1968 (Cth) (Copyright Act) – whether relevant executives who undertook or supervised copying were acting within the scope of their authority – principles concerning attribution of knowledge to a corporation – no error shown COPYRIGHT – award of additional damages under s 115(4) of the Copyright Act – discretionary decision – no error in the exercise of discretion shown |
Legislation: | Copyright Act 1968 (Cth) ss 10, 13(1), 14, 31(1), 32, 36(1), 37, 38, 115(4), 126 Copyright Amendment Bill 1984 (Cth) Evidence Act 1995 (Cth) ss 81, 136 Federal Court of Australia Act 1976 (Cth) ss 27 Patents Act 1990 (Cth) ss 7(3), 18(1), 117 |
Cases cited: | Aequitas Ltd v AEFC Leasing Pty Ltd (2001) 19 ACLC 1,006 Aktiebolaget Hässle v Alphapharm Pty Limited (2002) 212 CLR 411 Albert v S Hoffnung & Co Ltd (1921) 22 SR (NSW) 75 Aldi Foods Pty Ltd v Moroccanoil Israel Ltd (2018) 261 FCR 301 Allen v Tobias (1958) 98 CLR 367 Alphapharm Pty Ltd v H Lundbeck A/S [2008] FCA 559 Apotex Pty Ltd v Warner-Lambert Co LLC (No 2) [2016] FCA 1238 Aristocrat Technologies Australia Pty Ltd v Commissioner of Patents (2022) 274 CLR 115 Aristocrat Technologies Australia Pty Ltd v DAP Services (Kempsey) Pty Ltd (in liq) (2007) 157 FCR 564 Autodesk Inc v Dyason (No 2) (1993) 176 CLR 300 Beach Petroleum NL v Johnson (1993) 43 FCR 1 Berry v CCL Secure Pty Ltd (2020) 271 CLR 151 Brambles Holdings Ltd v Carey (1976) 15 SASR 270 Branir Pty Ltd v Owston Nominees (No 2) Pty Ltd (2001) 117 FCR 424 CA Inc v ISI Pty Ltd (2012) 201 FCR 23 Caporaso Pty Ltd v Mercato Centrale Australia Pty Ltd [2024] FCAFC 156 Commissioner of Patents v Aristocrat Technologies Australia Pty Ltd [2021] FCAFC 202 Commissioner of Patents v Microcell Limited (1959) 102 CLR 232 Commissioner of Patents v Rokt Pte Ltd (2020) 277 FCR 267 Commonwealth Bank of Australia v Kojic (2016) 249 FCR 421 Data Access Corporation v Powerflex Services Pty Ltd (1999) 202 CLR 1 Davies v Lazer Safe Pty Ltd [2019] FCAFC 65 Designers Guild Ltd v Russell Williams (Textiles) Ltd [2000] 1 WLR 2416 Director of Public Prosecutions (Vic) Reference No 1 of 1996 [1998] 3 VR 352 Farrow Finance Company Ltd (in liq) v Farrow Properties Pty Ltd (in liq) [1999] 1 VR 584 Fox v Percy (2003) 214 CLR 118 Fuchs Lubricants (Australasia) Pty Ltd v Quaker Chemical (Australasia) Pty Ltd (2021) 284 FCR 174 Grimaldi v Chameleon Mining NL (No 2) (2012) 200 FCR 296 Hyperion Records Ltd v Sawkins (2005) 64 IPR 627 IceTV Pty Limited v Nine Network Australia Pty Limited (2009) 239 CLR 458 Interlego AG v Croner Trading Pty Ltd (1992) 39 FCR 348 International Business Machines Corporation v Commissioner of Patents (1991) 33 FCR 218 IPC Global Pty Ltd v Pavetest Pty Ltd (No 3) [2017] FCA 82 JR Consulting & Drafting Pty Ltd v Cummings [2016] FCAFC 20 Katsilis v Broken Hill Pty Co Ltd (1977) 18 ALR 181 Krakowski v Eurolynx Properties Ltd (1995) 183 CLR 563 Ladbroke (Football) Ltd v William Hill (Football) Ltd [1964] 1 WLR 273 Lennard's Carrying Co. Ltd. v. Asiatic Petroleum Co. Ltd. [1915] AC 705 Lockwood Security Products Pty Ltd v Doric Products Pty Ltd (No 2) (2007) 235 CLR 173 Meridian Global Funds Management Asia Ltd v Securities Commission [1995] 2 AC 500 Mylan Health Pty Ltd (formerly BGP Products Pty Ltd) v Sun Pharma ANZ Pty Ltd (formerly Ranbaxy Australia Pty Ltd) [2019] FCA 28 N V Philips Gloeilampenfabrieken v Mirabella International Pty Limited (1995) 183 CLR 655 Nichia Corporation v Arrow Electronics Australia Pty Ltd [2019] FCAFC 2 Oxworks Trading Pty Ltd v Gram Engineering Pty Ltd [2019] FCAFC 240 Productivity Partners Pty Ltd (trading as Captain Cook College) v Australian Competition and Consumer Commission [2024] HCA 27 Raben Footwear Pty Ltd v Polygram Records Inc (1997) 75 FCR 88 Re Hampshire Land Company [1896] 2 Ch 743 Repipe Pty Ltd v Commissioner of Patents [2021] FCAFC 223 Research in Motion v Samsung Electronics Australia Pty Ltd (2009) 176 FCR 66 SW Hart v Edwards Hot Water Systems (1985) 159 CLR 466 Tesco Supermarkets Ltd v Nattrass [1972] AC 153 The Ophelia (1916) 2 AC 206 UbiPark Pty Ltd v TMA Capital Australia Pty Ltd (No 2) [2023] FCA 885 University of Sydney v ObjectiVision Pty Ltd [2019] FCA 1625 Venus Adult Shops Pty Ltd v Fraserside Holdings Ltd (2006) 157 FCR 442 Warren v Coombes (1979) 142 CLR 531 |
Division: | General Division |
Registry: | New South Wales |
National Practice Area: | Intellectual Property |
Sub-areas: | Copyright and Industrial Designs |
Number of paragraphs: | 923 |
Date of last submission: | 18 December 2023 |
Date of hearing: | 27, 28, 29 and 30 November 2023 |
Counsel for the Appellants and Cross-Respondents: | C Dimitriadis SC and J S Cooke SC with J Ambikapathy and M Evetts |
Solicitors for the Appellants and Cross-Respondents: | Spruson & Ferguson Lawyers Pty Ltd and Minter Ellison |
Counsel for the Respondent and Cross-Appellant: | C A Moore SC with P L Arcus and N L Gollan |
Solicitors for the Respondent and Cross-Appellant: | Herbert Smith Freehills |
ORDERS
NSD 675 of 2023 | ||
| ||
BETWEEN: | HYTERA COMMUNICATIONS CORPORATION LTD First Appellant HYTERA COMMUNICATIONS (AUSTRALIA) PTY LTD ACN 165 879 701 Second Appellant | |
AND: | MOTOROLA SOLUTIONS INC. Respondent | |
AND BETWEEN: | MOTOROLA SOLUTIONS INC. Cross-Appellant | |
AND: | HYTERA COMMUNICATIONS CORPORATION LTD First Cross-Respondent HYTERA COMMUNICATIONS (AUSTRALIA) PTY LTD ACN 165 879 701 Second Cross-Respondent | |
order made by: | BEACH, O'BRYAN AND ROFE JJ |
DATE OF ORDER: | 18 December 2024 |
THE COURT ORDERS THAT:
1. The First and Second Appellants’ Amended Notice of Appeal dated 8 November 2023 be dismissed.
2. The Cross-Appellant’s Amended Notice of Cross-Appeal dated 27 November 2023 be allowed in part, in respect of grounds 2 and 3, and otherwise dismissed.
3. The Cross-Appellant’s Amended Notice of Cross-Appeal dated 27 November 2023 be listed for case management before this Court at 10.15 am on Friday 7 February 2025 for the making of timetabling orders for the further hearing and determination of the copyright infringement claims that arise on the appeal in accordance with the reasons accompanying these orders.
4. Pursuant to ss 37AF(1)(b) and 37AG(1)(a) of the Federal Court of Australia Act 1976 (Cth), until further order of the Court, access to and disclosure (by publication or otherwise) of the unredacted text of the reasons for judgment delivered today be restricted to the legal representatives of the parties and those persons to whom access is allowed under the terms of the confidentiality regimes agreed between the parties on 10 April 2018 and/or the confidentiality regime agreed between the parties on 24 May 2019.
5. Nothing in Order 4 or any other earlier order of the Court prevents any party from publishing the covering pages of these reasons for judgment up to and including these orders and paragraphs 1 to 21 and 918 to 923 of the reasons.
6. By 31 January 2025, the legal representatives for the parties exchange highlighted versions of the reasons for judgment identifying any parts of the reasons that are claimed to contain information confidential to their respective clients for redaction.
7. By 14 February 2025, the legal representatives for the parties confer on the proposed redactions and, if the parties are able to agree on the proposed redactions, provide to chambers an agreed form of the reasons for judgment with the proposed redactions highlighted, together with an agreed redacted form of the reasons for judgment that is suitable for publication.
8. In the event the parties are unable to agree on the proposed redactions, by 21 February 2025 the legal representatives for the parties provide chambers with:
(a) a version of the reasons for judgment which identifies the redactions which have been agreed and those which are in dispute; and
(b) a short written submission addressing the areas of disagreement.
Note: Entry of orders is dealt with in Rule 39.32 of the Federal Court Rules 2011.
REASONS FOR JUDGMENT
THE COURT:
A. Introduction
1 This appeal concerns digital mobile radios (DMRs) supplied in Australia by Hytera Communications Corporation Ltd (Hytera) and its Australian subsidiary, Hytera Communications (Australia) Pty Ltd (Hytera Australia), including the computer firmware incorporated within the devices. In these reasons, Hytera and Hytera Australia are referred to collectively as ‘Hytera’ unless there is a reason to refer to Hytera Australia specifically.
2 A DMR is a digital two-way radio device that can both receive and transmit signals from other radio devices operating on the same radio frequency. DMRs can be mobile (e.g. affixed to a vehicle which moves) or portable (e.g. carried around by a person). An individual DMR can communicate directly with another DMR and, when it does so, the two devices are said to be communicating in ‘direct mode’. However, DMRs are frequently deployed with fixed base stations, or ‘repeaters’, through which they communicate with each other and by which means their range is extended. In contrast to mobile telephones, two-way radios are focussed on group call communications which are also known as one-to-many communications and are designed to be used in sectors such as government, industry and emergency services. Two-way radio systems may use analogue or digital systems. Analogue radio systems use electrical signals which, at least conceptually, resemble sound waves to deliver voice audio over a radio frequency. Digital radio systems, by contrast, process sounds into patterns of numbers (in binary code) which are then transmitted over a radio frequency. Digital two-way radios can allow users to transmit data as well as audio and they are also more secure than analogue radios.
3 In April 2005, the European Telecommunications Standards Institute (ETSI) published a standard for a digital two-way radio system (2005 DMR Standard). The purpose of the 2005 DMR Standard was to reduce channel interference and to increase radio spectrum efficiency. The 2005 DMR Standard concerned the division of a frequency band within the radio spectrum (a channel) into timeslots so that more than one person may use the same channel at the same time. This is known as Time Division Multiple Access (TDMA).
4 Motorola Solutions Inc (Motorola) began work on a DMR project in earnest in 2003. The software development for this project was called the ‘Matrix’ project. The development of the Matrix software continued until February 2007. Motorola began selling its DMR devices in the United States and Canada in the first quarter of 2007. Those devices utilised the initial version of the firmware resulting from the Matrix project which was known as ‘Release 1’.
5 From about 2005, Hytera was also seeking to develop a DMR device. The design task had been given to Professor Sun within Hytera. By September 2007, Hytera’s development of a DMR device had proceeded as far the creation of a prototype. However, by the end of 2007, Hytera’s DMR project was confronted with two significant problems. The first was that it was going to result in a product which would not be competitive with Motorola’s device. The second was that it would take at least until the end of 2009 before the process of commercialisation of the product could begin, and a product launch would not occur before the middle of 2011. By the end of 2007, Hytera’s development of its DMR device was in disarray. Hytera had wasted three years getting to that position and its competitor, Motorola, was already in the market.
6 The President and Chief Executive Officer of Hytera, Mr Chen, recruited Mr GS Kok from Motorola, commencing mid-February 2008. Mr GS Kok was a senior employee within Motorola on the Matrix project. At Hytera, Mr GS Kok was put in charge of the DMR team, replacing Professor Sun. Very soon after his arrival at Hytera, Mr GS Kok provided Mr Chen with a negative assessment of the state of Hytera’s DMR project and proposed the recruitment of additional engineers from Motorola who had worked on the Matrix project. Over the ensuing months, Mr GS Kok recruited 12 engineers from Motorola.
7 At trial, Hytera did not dispute that Mr GS Kok and certain of the other ex-Motorola engineers brought with them to Hytera, without authorisation from Motorola, Motorola documents and computer code relating to Motorola’s DMR device and made use of some of these materials, including the computer code, in the development of Hytera’s firmware for its DMR device. That in itself is a damning admission, but the primary judge’s ultimate findings were even stronger. His Honour found that the ex-Motorola engineers took with them to Hytera all of the computer source code for Motorola’s DMR device to provide themselves with a resource for the purposes of writing Hytera’s source code for its DMR device. His Honour characterised Hytera’s actions as a “substantial industrial theft” and found that (Motorola Solutions, Inc. v Hytera Communications Corporation Ltd (Liability) [2022] FCA 1585 (the primary judgment or PJ) at [1576]):
There is no doubt that Hytera’s software engineers engaged in industrial scale harvesting of Motorola’s source code and that they set out to make this as difficult to detect as possible.
8 The Hytera DMR devices were brought to market in March 2010. The primary judge found that Hytera benefitted from the actions of the ex-Motorola engineers in at least two ways: first, it got to market with devices which were commercially competitive with Motorola’s products where otherwise it would not have done so; and secondly, it got to market by at least 15 months earlier than it otherwise would have. From September 2013, Hytera began distributing its DMRs in Australia.
9 In March 2017, Motorola commenced proceedings against Hytera in the United States alleging patent infringement and breach of confidence. In July 2017, Motorola commenced proceedings (the subject of the primary judgement) in Australia alleging infringement of Australian Patent No 2005275355 (355 patent), Australian Patent No. 2006276960 (960 patent) and Australian Patent No. 2009298764 (764 patent) under the Patents Act 1990 (Cth) (Patents Act). Each of those patents are methods which refine the efficiency of TDMA. Motorola alleged that Hytera infringed the Australian patents by distributing in Australia Hytera’s DMR devices without Motorola’s license. By cross-claim, Hytera challenged the validity of the Australian patents.
10 Following the discovery by Hytera of its source code for its DMR products for the purposes of the patent proceeding, Motorola added a claim for infringement of copyright in its own source code, first in the United States proceeding (in August 2018) and then in the proceeding before the primary judge (in December 2018). Substantially complete particulars of Motorola’s copyright claim were provided to Hytera in June 2019. Motorola alleged that Hytera infringed its Australian copyright in the ‘Release 1’ version of its computer source code for its DMR devices by, first, importing into Australia Hytera DMRs containing firmware which was a reproduction or an adaptation of the whole or a substantial part of Motorola’s source code and, second, making that firmware available for download in Australia from its website portal. Those claims were made under the Copyright Act 1968 (Cth) (Copyright Act).
11 In 2018, Hytera reprogrammed its DMR devices to remove or disable functionalities relevant to the patents in suit. Then, on 17 May 2019, Hytera gave undertakings to Motorola not to exploit devices installed with non-reprogrammed firmware, not to make available the non-reprogrammed firmware and to refrain from reversing the reprogramming unless this Court found that the non-reprogrammed firmware did not infringe Motorola’s patents. By 20 November 2019, Hytera had taken sufficient steps by way of reprogramming to prevent further patent infringement.
12 In June 2019, after receiving particulars of Motorola’s copyright claim, Hytera began to rewrite the firmware for its DMR devices relevant to the copyright claims. From 22 November 2019, Hytera deployed rewritten firmware in its DMR devices. On 9 April 2020, Hytera gave undertakings to the Court not to import or sell in Australia DMR devices with the allegedly infringing firmware. On 12 June 2020, Hytera gave undertakings to the Court not to make the allegedly infringing firmware available for download in Australia from its website portal.
13 The trial of the proceeding occurred in two stages. The patent issues were heard in July and August 2019 over a period of 13 days. The copyright issues were heard between July and October 2020 over a period of 23 days. The evidence was voluminous and the subject matter of the proceeding was technical and complex.
14 The primary judge delivered judgment on 23 December 2022. In respect of the claims for patent infringement, his Honour concluded that Hytera had infringed claims 1, 2, 3, 4, 5, 6 and 10 of the 355 patent in respect of the distribution of its DMR devices before 20 November 2019, that Hytera had not infringed the 764 patent, and that the 960 patent was invalid. In respect of the claims for copyright infringement, his Honour concluded that Hytera had infringed Motorola’s copyright in six of the eleven works (comprising computer software) in respect of which Motorola made claims.
15 The primary judge granted declaratory and injunctive relief in respect of the above conclusions, but deferred the question of compensatory relief (damages or an account of profits) pending any appeal. His Honour also found that Motorola was entitled to an award of additional damages in respect of Hytera’s copyright infringement, but not in respect of Hytera’s patent infringement.
16 By its amended notice of appeal, Hytera challenges all of the findings of patent and copyright infringement made against it and the conclusion that Motorola was entitled to an award of additional damages in respect of Hytera’s copyright infringement. By its amended notice of contention on Hytera’s appeal, Motorola contends that the primary judge’s findings on patent infringement and copyright infringement which are challenged by Hytera should be affirmed on additional grounds.
17 By its amended notice of cross-appeal, Motorola challenges the findings that the 960 patent is invalid and the scope of the findings that Hytera infringed Motorola’s copyright (contending that the scope of the infringement was wider than as found by the primary judge). By its amended notice of cross-contention, Hytera contends that the primary judge’s findings challenged by Motorola should be affirmed on additional grounds.
18 The grounds of appeal and contentions raised by the parties on this appeal are extensive. A number of the grounds and contentions raise significant matters of legal principle. Other grounds and contentions challenge respectively findings of fact, the drawing of inferences and the overall evaluation undertaken by the primary judge. In undertaking its appellate function on this appeal, the Court has kept in mind the well-established principles that guide appellate review in this Court. The appeals are by way of rehearing: s 27 of the Federal Court of Australia Act 1976 (Cth). The Court’s review of the primary judge’s findings of fact and inferences drawn from those facts are subject to the principles stated in Fox v Percy (2003) 214 CLR 118 (Fox v Percy) and Warren v Coombes (1979) 142 CLR 531 (Warren v Coombes). The principles applicable to appellate review of evaluative judgments (such as a finding that a substantial part of a work has been copied) have been discussed in a number of cases. In Aldi Foods Pty Ltd v Moroccanoil Israel Ltd (2018) 261 FCR 301, the Full Court affirmed the principles as stated in Branir Pty Ltd v Owston Nominees (No 2) Pty Ltd (2001) 117 FCR 424 (Branir). On such appeals, the Court must first make up its own mind on the facts, observing the “natural limitations” that exist in the case of any appellate court proceeding wholly or substantially on the record, as explained in Fox v Percy. Having determined the facts, the Court must undertake itself the required evaluative assessment. As also explained by Allsop J in Branir (at [28]-[30]), while the appeal court has a duty to make up its own mind, it does not deal with the case as if trying it at first instance. Appellate intervention requires the demonstration of error on the part of the trial judge. Those principles were recently reaffirmed by the Full Court in Caporaso Pty Ltd v Mercato Centrale Australia Pty Ltd [2024] FCAFC 156 which reiterated that the standard of appellate review in the context of evaluative judgments is the “correctness standard” (at [133]).
19 In relation to the case concerning patent infringement, the Court has concluded that the grounds of appeal advanced by Hytera (on its appeal) and by Motorola (on its cross-appeal) should be rejected.
20 In relation to the case concerning copyright infringement, the Court has concluded that Motorola’s grounds of appeal should be upheld, whereas Hytera’s grounds of appeal should be rejected.
21 It follows that Hytera’s appeal is dismissed. With respect to Motorola’s cross-appeal, ground 1 is rejected while grounds 2 and 3 are upheld. However, the Court will not make final orders with respect to Motorola’s cross-appeal. Although the Court has upheld grounds 2 and 3 of Motorola’s cross-appeal by finding that the primary judge erred in certain respects to the approach taken to the determination of copyright infringement, to this point the Court is not able to determine whether Motorola’s claim of copyright infringement should succeed in whole or in part. Relevant factual findings have not been made that would enable this Court to determine finally the copyright infringement case applying the methodology that the Court considers is correct. The Court considers that the appropriate course is to conduct a further hearing at which the parties will be given an opportunity to advance further submissions in respect of the copyright infringement claims that arise on the appeal in accordance with the Court’s reasons. The hearing will be a continuation of Motorola’s cross-appeal. The Court will list the matter for case management to make timetabling orders for the conduct of the further hearing.
B. Patent validity and infringement
B.1 Introduction to the 355 patent appeal and the 960 patent cross-appeal
22 It is appropriate to begin with some introductory remarks relating to Hytera’s appeal concerning the 355 patent and Motorola’s cross-appeal concerning the 960 patent.
23 In the proceedings before the primary judge, Motorola alleged that Hytera’s DMRs infringed three of its Australian standard patents. As noted earlier, these patents relate to TDMA technology which permits a frequency band within the radio spectrum (that is, a channel) to be divided into timeslots so that more than one person may use the same channel at the same time. The asserted claims of the three patents involve methods which are said to refine the efficiency of TDMA.
24 The 355 patent is a method and system which improves the time taken to scan a TDMA channel to determine whether there is activity on that channel. It has a priority date of 26 July 2004.
25 The 764 patent is a method for efficiently synchronising to a desired timeslot in a TDMA communication system.
26 The 960 patent is a method and system for accessing a base station which has been de-keyed, a concept which is explained below. It has a priority date of 28 July 2005.
27 At first instance Motorola alleged that Hytera had imported into Australia DMRs which infringed the methods of the three patents and it sued for secondary infringement. Hytera disputed Motorola’s construction of each of the patents and contended in each case that, even if the asserted claims of the patents were to be construed as Motorola suggested, each patent was invalid for various reasons.
28 The primary judge concluded that Motorola’s construction of the 355 patent was correct and that the challenges to its validity such as a lack of inventive step and there being no manner of manufacture failed. His Honour concluded that Motorola’s infringement case in relation to the 355 patent largely succeeded although he accepted that Hytera did not infringe the patent after November 2019 when it took steps to ensure that existing mobile stations were upgraded before reprogrammed base stations were supplied to end users.
29 The primary judge rejected Motorola’s infringement case on the 764 patent. His Honour rejected Motorola’s construction of that patent, but said that even if it had been correct, he would have concluded that the patent was invalid as it would not have been fairly based. His Honour’s findings concerning the 764 patent have not been challenged before us and we need say nothing further about that patent or the proceedings at first instance concerning it.
30 As to the 960 patent, the primary judge held that Motorola’s construction of the 960 patent was correct, but he held that the patent was invalid for want of an inventive step. His Honour rejected Hytera’s contention that no manner of manufacture was involved.
31 Hytera’s appeal challenges the primary judge’s findings and determination concerning the 355 patent. Motorola has filed a notice of contention on one aspect concerning construction.
32 Motorola’s cross-appeal challenges the primary judge’s findings and determination concerning the 960 patent. Hytera has filed a notice of cross-contention on aspects concerning construction and infringement if the 960 patent is held to be valid. It has also sought to re-agitate the manner of manufacture question.
33 Before dealing with the specific grounds of appeal and cross-appeal, it is necessary to set out some of the technical background.
B.2 Background — two-way radio communications and relevant technology
34 To understand the issues which have arisen before us, it is necessary to say something concerning the electronic engineering underpinning two-way radio communications. We have gratefully drawn from aspects of the primary judge’s detailed technical description that are relevant to the grounds of appeal and cross-appeal before us.
General
35 Radio is a method of transmitting electromagnetic energy across distance without using a direct, wired connection. The electromagnetic energy takes the form of radio waves which have a certain frequency. Radio waves are generated and sent out through a transmitter and are then received by a radio receiver using antennas. Depending upon their length, radio waves may travel by line of sight, by being reflected off buildings or other objects, in which case the communications will not travel beyond the horizon, and by being reflected off the ionosphere, in which case they can return to earth beyond the horizon. Different radio frequencies (RFs) are used for these different reflective requirements.
36 As stated above, radio communications can be transmissions of audio (analogue transmissions) or of data (digital transmissions). Where a transmission is an analogue transmission, the whole of the voice transmission can be sent and decoded without any additional information being transmitted. Contrastingly, where a digital communication is involved, the decoding of the message requires the use of overheads. Overheads are the bits of digital information that are not associated with the substantive transmission, being the payload. So, digital transmissions are made up of two kinds of information being the overhead and the payload.
37 One of the overheads in a digital communication arises from the need to achieve synchronisation between the devices which is achieved using a synchronisation pattern. Another relates to the scanning of channels which involves the use of information to identify the devices to which a payload is to be delivered. This kind of information is referred to as control information. The more of the radio transmission that is consumed by transmitting control information, the less of it is available to transmit payload.
The radio spectrum
38 The radio portion of the electromagnetic spectrum, which radio communications are transmitted on, is divided into three sub-categories known as frequency bands. These bands are the high frequency band (3,000 kHz to 30 MHz), the very high frequency band (30 MHz to 300 MHz) and the ultra-high frequency band (300 MHz to 3 GHz). Each of these bands is further separated into bandwidth channels which radio users use to transmit communications. These channels reflect the frequency range occupied by a carrier signal and are separated by a space known as channel spacing.
39 The size of the bandwidth channel and the size of the channel spacing between each channel is determined in Australia by the Australian Communications and Media Authority. In 1999, ACMA determined that two-way radios would use channel bandwidths of 12.5 kHz, meaning each channel may occupy a range of frequencies in the radio spectrum which are no wider than 12.5 kHz. The size of this bandwidth limits the number of frequencies that can be defined inside a relevant band. Generally, the wider the channel bandwidth, the better the audio fidelity or the higher the data rate will be.
The components of radio devices
40 A two-way radio is a device that can both receive and transmit signals from other radios operating on the same RF. There are two kinds of two-way radio devices being half-duplex devices and full-duplex devices. A half-duplex radio is one which permits the user to talk or to listen but not to do both at the same time. Contrastingly, a full-duplex radio has the ability to send and receive transmissions at the same time. It does so by sending transmissions on one frequency and receiving them on another.
41 In the case of a half-duplex two-way radio, the user presses a Push-To-Talk (PTT) button which activates the transmitter. When the PTT button is not pressed, the device’s radio receiver is activated. Half-duplex radios may also function by using what is referred to as simplex communication. Where this occurs, the transmission and reception occurs on a single RF. In other words, the radio switches between the transmit and receive functions, transmitting on one frequency and then switching to receive any incoming transmissions using the same frequency.
42 To be able to transmit and receive at the same time, full-duplex radios may use two different frequencies. Typically, this means that one frequency is assigned for the radio to transmit and another is assigned to receive communications. Together, the two frequencies are known as a frequency pair or a physical channel. Alternatively, a full-duplex radio may use what are called frequency sharing methods. In a digital system this involves breaking the communications up into digital packages and transmitting the packages sufficiently frequently such that the underlying process is not audible.
Terminal equipment
43 Mobile stations are typically vehicle based installations that allow for communication to other local terminal equipment, say, between police cars. These are also referred to as radios or subscriber units. They may communicate in either direct mode or repeater mode. A direct mode transmission occurs between two mobile stations without the use of a repeater and usually takes place on the same transmit and receive frequencies, that is, with each radio switching between transmitting and receiving communications. A direct mode communication is possible so long as both mobile station users are not too far apart and there is no obstruction between the sender of the communication and the receiver.
Repeater equipment
44 Repeaters, which are also referred to as base stations, are devices which relay transmissions from terminal equipment, and so extend the coverage of those terminals. They are typically located above terminals such as on top of a mountain or building, and utilise a hard-wired power source. So, where a repeater is used, the sender of the communication will transmit the message from their terminal and once the transmission reaches the base station, the base station will then repeat the message to the intended receiver. In a trunked system, a repeater also repeats the transmissions which it receives from a control station.
45 Relatively simple two-way radio systems only include a single repeater. Multiple repeaters, however, may be interconnected to increase the coverage area (a cell) and to enable direct links to control stations. Repeaters typically receive and transmit on two different RFs, known as the uplink and the downlink. Terminals transmit information such as voice calls through the uplink towards the repeater. The repeater then retransmits or repeats the information through the downlink towards another repeater or terminal. In its most simple form, a repeater is therefore two terminal devices connected together, with one operating as the uplink and one operating as the downlink. The downlink is essential to the processes of de-keying and re-keying which are relevant to the 960 patent.
46 In many two-way radio systems, the repeater is designed to de-key after a transmission. When a repeater de-keys, it turns off the downlink. This means that the repeater cannot transmit information using the downlink unless it re-keys. Further, terminals listening to the repeater’s downlink frequency will not receive transmissions from that repeater. A common reason why a repeater will de-key is because there is no active terminal using the repeater’s cell. As the radio spectrum is a limited and shared resource, repeaters are often programmed to de-key in order to ensure that they are not powered on when they are not in use and to allow other repeaters to use the frequency.
47 Repeaters often have a fixed timer, for example, 10 seconds which starts when the repeater detects that there is no activity on the repeater’s uplink frequency. This will occur when there is no transmission being sent from any of the terminal devices. This timer is often referred to as the hangtimer. One of the purposes of the hangtimer is to ensure that the recipient has sufficient time to respond to a communication before the repeater de-keys. When the hangtimer expires, the repeater de-keys.
48 If a mobile station wants to utilise a de-keyed repeater for transmissions, it must first wait for the repeater to re-key. When the repeater re-keys, it reactivates the downlink and can send outgoing transmissions again. Although a de-keyed repeater’s downlink is deactivated, its uplink is still monitored and is able to receive transmissions. This allows a de-keyed repeater to receive messages from terminals, enabling it to re-key. But the process of re-keying can take time and delay transmissions. This can be a problem for users, such as members of the emergency services who need to relay a communication quickly.
Control stations and control channels
49 Control stations facilitate communication and signalling to remote terminal equipment. They may be positioned in a control centre or a depot. A simple control station may consist of a speaker, a microphone and a PTT switch. A more complex control station may include several networked computers and remotely accessible data bases. Control stations are a common feature of trunked systems. A control channel is a channel in a trunking system where network access is requested and assigned. They are used by radio users to be assigned to a traffic channel to begin a voice transmission.
Modems
50 Modems facilitate the transfer of data using RFs. Prior to July 2004, some analogue two-way radio systems included modems as an optional component. This is because their presence allowed analogue systems to transmit data, as opposed to just voice, over the analogue signal. By allowing data to be transmitted in this way, control information could therefore be transmitted even though the system was not digital. Examples of the kind of control information that could be transmitted included information identifying a particular terminal, information identifying groups of terminals to be included in a communication, and information as to which channels were to be used for what. The word “terminal” is used interchangeably with “subscriber unit” or “mobile station”.
51 In analogue systems, modems were a physical component of the radio device, that is, hardware in the terminals and the repeaters, which turned converted data into an analogue, that is, audio signal. But in digital systems, modem functionality was incorporated into the software of the devices and no physical modem was needed.
Two-way radio functionality
52 Cellular communication systems such as mobile phones are designed for one-to-one communications and so are usually used by individual consumers. By contrast, two-way radios are designed to be used by professionals in sectors such as government, industry, and emergency services and so are focused on group call communications which are also known as one-to-many communications. As a result, two-way radios utilise a feature known as talkgroups. Mobile phones are typically smaller, have lower power levels and are full-duplex devices, that is, they can communicate and receive at the same time. Two-way radios are larger devices with a relatively higher power level and may be full-duplex or half-duplex, in which case they cannot transmit and receive at the same time.
53 Two-way radios can engage in direct mode between themselves, or in repeater mode via a repeater. Mobile phones do not have a direct mode and only communicate through network infrastructure.
Talkgroups
54 A talkgroup is a way of organising multiple individual radio devices into groups of users who can all communicate with each other. Each talkgroup has its own group identity which is programmed into the memory of each individual radio device. When a radio device that is a member of a specific talkgroup transmits, all the other members of the talkgroup are able to hear and respond to that transmission. The use of talkgroups allows for private communications between members of a particular talkgroup by excluding radio users that are not part of that group. It also facilitates effective communication, in that one user can communicate to a group with a single transmission.
Scanning
55 Mobile and portable radio users tune into specific channels in order to transmit or receive communications. Users can select a channel either manually, and usually through a dial or buttons, by selecting an appropriate channel, or by using the radio automatically to scan channels. The 355 patent is concerned with scanning.
56 The process of scanning involves the receiver radio searching multiple channels (a scan group) to find a valid transmission. A scan group consists of a group of frequencies that may be of interest and is stored in the memory of the radio. When the radio determines that it has found a valid transmission, it will stop and lock onto that channel and then send the communication to the radio’s speaker. A valid transmission is a communication which meets specific conditions, such as having certain talkgroup or address information. The conditions which will make a transmission valid are programmed into the radio device. If the receiver radio decodes the message and identifies that all of the relevant conditions are present, the transmission will be deemed valid and will be broadcast through the speaker. If the transmission does not meet all of the programmed conditions, however, it will be ignored. In the example of the firefighter above, for instance, the radio device could be programmed such that a transmission addressed to one or more of the three talkgroups would be a valid transmission.
57 There are various ways to program a radio’s scanning capabilities. One way in which a radio’s scanning capabilities might be programmed is called priority scanning, which enables the radio to scan important channels more frequently. Automatic scanning, such as priority scanning, can be advantageous because it can take time for a user manually to select channels and users may miss transmissions if they are on the wrong channel. Various systems existed for automatic scanning prior to the priority date for the 355 patent.
Different types of two-way radios
58 Two-way radio systems are generally split into analogue and digital systems. The main difference between them is the way that signals are transmitted and received. Analogue radio systems use electrical signals which, at least conceptually, resemble sound waves to deliver voice audio over an RF. Digital radio systems, by contrast, process sounds into patterns of numbers which are then transmitted over an RF. Digital two-way radios can allow users to transmit data as well as audio. They are also more secure.
59 Early two-way radio systems transmitted voice messages using analogue methods over RFs. Communication was either direct from one terminal to another on a simplex channel, that is, on a single frequency, or it was transmitted between terminals via a repeater on different transmit and receive frequencies.
60 Without the inclusion of the repeater, the coverage of a radio system is dependent on the power of the terminal. Since terminals are often portable and therefore powered by a battery, the power of early terminals was relatively low. However, since early analogue two-way radio systems could be used in both direct mode and repeater mode, that is, with or without a repeater, simple analogue two-way radio systems often included a single repeater to relay communications between connected terminals. The coverage of such a system is restricted by the power of the single repeater. This type of system was very common in Australia before the 1980s.
61 Larger two-way radio systems include multiple repeaters that enable the system to cover a larger area. While this type of system allowed for extended coverage, a problem was that all of the connected repeaters were required for a single transmission. This meant that only one transmission could take place using connected repeaters in the system at a time.
Scanning in analogue two-way radio systems before 26 July 2004
62 Early two-way radio systems required radio users, such as the user of a mobile station in a vehicle, manually to change the channel to scan the system for relevant transmissions. This meant that when a user was moving around they would need to know the channel which was associated with the closest repeater and then select that channel on the mobile station in order to receive the transmission.
63 Automatic scanning functionality was then developed in around the 1980s to allow for users moving between different repeaters to automatically receive communications from different repeaters. In early analogue systems, this was achieved by a list of frequencies, each of which was associated with a different repeater, being saved in the memory of the terminal devices. When set to scan automatically, the terminal device would then step through the list of frequencies and lock onto each to determine if a transmission was taking place.
64 A problem with this automatic scanning methodology, however, was that there was no assessment of signal strength when the terminal device stepped through the list of frequencies. As a result, terminals often locked onto a repeater that was not the closest repeater to them, with the consequence that they had low signal strength.
65 Automatic voting was thus developed to ensure that signal strength was taken into account when a terminal automatically scanned RFs. Automatic voting was similar to automatic scanning in that the terminal would automatically scan through a list of frequencies saved to memory in the terminal. However, automatic voting required the terminal device to assess the signal strength of each frequency stored in memory in the terminal before deciding which frequency, that is, which repeater to lock onto. This type of system often included a control station that was independent of the repeaters. That control station would re-key the repeaters every minute or so to produce a burst of energy for a length of time that was sufficient for each terminal to complete the automatic voting function and record their local site, that is, the local repeater with the strongest signal strength.
66 Techniques were also developed before 26 July 2004 that enabled analogue terminals to automatically scan frequencies for specific types of communications, for example, communications to a specific talkgroup. One example of this kind of technique was what was known as the Code Tone-Coded Squelch System (CTCSS). The CTCSS adds a low frequency tone to a voice communication. Terminals included in their memory a list of CTCSS tones that were associated with, for example, a talkgroup. This enabled the terminals to listen for a specific CTCSS tone. If the tone for a talkgroup which was saved to the terminal’s memory was heard on a channel while it was automatically scanning, then the terminal would stay on the channel. Otherwise, the terminal would continue scanning the other channels saved in its scan list. As we have indicated, the concepts of scanning and staying on a channel are relevant to the 355 patent.
67 A well-known problem with both automatic scanning and automatic voting in early analogue two-way radio systems was the length of time that it took for a terminal to complete the process. This limitation was a physical limitation which was inherent in analogue two-way radio systems. It was caused by the fixed amount of time that it took the terminal to perform the automatic scanning and automatic voting processes because it involved a number of steps. First, the radio would find an RF carrier. Second, using the example of CTCSS tones, although other methods might be used, it would decode the CTCSS in a hardware chip or in software. Third, it would “qualify” the channel and then, if all the relevant criteria were met, it would remain on the channel to start receiving communications. What is meant by “qualify” is that having detected the relevant CTCSS tone, the device had to be sure that it had done so and that what had occurred was not a random appearance of a tone frequency. This is consistent with the explanation that automatic scanning and voting in analogue two-way radios required the device to receive a certain number of radio wave cycles before the device could qualify the radio signal. As a result of the CTCSS tone being of such a low frequency, the time spent scanning and voting was determined by the period of the waveforms. For example, a two-way radio might have to wait for five cycles of the CTCSS waveform before it could complete the process and start receiving transmissions. The primary judge accepted that this problem was a well-known problem prior to the late 1980s. One solution to the problem was to limit the number of frequencies to be scanned.
De-keying and re-keying in analogue two-way radios prior to 26 July 2004
68 Prior to 26 July 2004, analogue repeaters included a hangtimer which prevented a repeater from de-keying immediately after a transmission. This hangtimer ensured that the recipient had sufficient time to respond before the repeater de-keyed. Where a repeater de-keyed it would result in the repeater releasing the downlink frequency to allow for other system users to begin a transmission. When it re-keyed the repeater would, before selecting a frequency upon which to broadcast, check to see that that frequency did not already have a CTCSS tone on it. If it did have such a tone, the repeater would re-key to a different frequency.
Digital two-way radios
69 Digital two-way radios were introduced in around the 1990s. In digital two-way radios, voice (and data) is transmitted using binary digits (bits) over RFs. The use of the binary system allows for error correction embedded signalling and control information to be included in each transmitted packet. Each packet contains an assembly of bits. Digital radios also introduced two other relevant innovations.
70 First, the software in a digital radio contains an algorithm which understands the difference between voice audio and background noise. As a result, unwanted background noise is not transmitted to the radio’s speaker and digital radios provide users with enhanced voice capacity and higher-quality coverage.
71 Second, digital two-way radio technologies introduced the ability to divide single-call RF channels. What is meant by a single-call RF channel is that the frequency is devoted to the carrying of a single communication. In a digital radio communication, the fact that the transmission is made up of packets of data means that with appropriate timing protocols in place, more than one communication can be carried at one time on the same frequency. This means that multiple users could access a single channel at one time. The first digital two-way radio systems were the MPT1327 (analogue voice with digital control messaging), APCO P25 (digital voice and data) and Terrestrial Trunked Radio (TETRA) (digital voice and data).
72 A transmission from a radio user in a digital system comprises two key elements, being the payload and embedded signalling information, which is also known as control information.
Payload
73 Payload is the term used to describe the part of a transmission that contains the substantive communication as opposed to, for example, the control information. It is a type of data that is transmitted in large blocks made up of many bits and usually relates to voice based or data based transmissions. When voice is being transmitted it is typically referred to as voice payload. Similarly, when data is being transmitted it is referred to as data payload.
Embedded signalling (control information)
74 After a process referred to as synchronisation, the receiving station needs to determine what sort of transmission is in progress. This is performed using embedded signalling which is also known as control information. Control information is decoded messages which consist of bits or words, which are groups of bits. These messages give information about certain parts of the transmission. For example, the control message could give information about the payload type by differentiating between voice or data, the source of the transmission, that is, which radio device the message has come from, or the recipient of the message which could be a single radio, a talkgroup or a colour code. Colour codes may be understood as referring to the geographical area covered by a particular base station.
Data frames
75 Control information is contained within what are called data frames. A data frame is the frame in a digital communication system which the bits that are used to carry voice and data are packaged into. A frame is a unit of repeating structure and typically includes a specific number of bits. Bits relating to specific functions, for example, the payload, frame synchronisation, and control messages, are assigned a specific location within a frame. A set frame structure is important as the receiving device needs to be able to decode the bits within a frame. For example, the receiving device needs to know which series of bits provide the payload portion of the received frame.
Frame synchronisation
76 In order for these data frames to be transmitted, the sending and receiving stations must be in synchronisation. Synchronisation is important for what are referred to as multiple access communications systems. The present matter is concerned with such systems.
77 Synchronisation is important in multiple access communications systems because the receiving device needs to determine which portion of the data on an RF is intended for that receiving device. When in use, a receiving device receives a constant stream of bits during the digital transmission. Frame synchronisation enables a receiving device to differentiate between the different portions of the constant stream of data so that it can determine the portion of the data that corresponds to the payload. In a data frame, if different groups of bits are assigned for different purposes, the receiving device must be able to know which part of the stream it is looking at. If a data frame is 216 bits in length, for example, and the first bit of the frame signals some particular meaning such as whether the channel is active, then this meaning will be lost if the receiving device does not know where the frame starts.
78 To enable frame synchronisation, digital terminal and repeater devices include a crystal. The crystal is an electronic element made from quartz crystal which is used to generate an internal timing reference like an internal clock. The purpose of frame synchronisation is to synchronise the internal clock of the receiving device such as a terminal with the internal clock of the transmitting device such as a repeater. The purpose of this clock synchronisation is so that the receiving device is then able to recognise the start and end of the data frames. Once the receiving device knows this, it can locate specific portions of the incoming data within each frame.
79 To synchronise with a transmitting device, a receiving device locates what is known as a synchronisation pattern or synchronisation word. A synchronisation pattern or synchronisation word is a known data sequence that is transmitted at certain times or intervals during a transmission. This synchronisation pattern is a series of bits that form a word and is a specific sequence of 1s and 0s that the receiving device will recognise. The two devices do not need to have been synchronised in order for the synchronisation pattern to be recognised. That is, the synchronisation pattern can be transmitted asynchronously.
80 Recognition of the synchronisation pattern allows for frame synchronisation between a receiving and transmitting device. Typically, the synchronisation pattern is located at the start or the middle of the data frame. Once a device locates the recurring synchronisation pattern, which is recurring because it is located in each repeating frame, the receiving device is able to determine where the pattern is in the data stream and is then able to decode the incoming frames to obtain relevant information.
Frame synchronisation in repeater mode
81 Terminals operating in repeater mode, that is, where they are communicating through a repeater, synchronise to the reference timing set by the repeater. The repeater sets the reference timing, being the timing of the repeating frames, and as such, the timing of the synchronisation patterns. This ensures that all of the terminals that are connected to the repeater are working to the timing reference and are synchronised to the repeater without conflicting with one another. This is important where multiple channels are included on the one frequency. Communications which are received out of synchronisation are ignored by a repeater unless the signal is a wake-up message.
82 Terminals can lose synchronisation for a variety of reasons. A loss of signal is generally referred to as a signal drop-out or a loss of carrier. Drop-outs can be short such as a few milliseconds, or long such as several seconds. Longer drop-outs may occur when the terminal moves too far away from the repeater or during periods of interference, such as when a terminal moves underground or under a bridge and is unable to maintain a signal with the repeater.
83 A phenomenon referred to as “Rayleigh fading” causes short term drop-outs in two-way radio systems. Fading may occur due to radio waves reflecting off buildings or other objects which cause an interference to radio signals. In this circumstance, signal strength may drop down to zero and then return very quickly, say, within milliseconds.
84 In digital two-way radio systems, terminals communicating in repeater mode may temporarily maintain data synchronisation or reference timing during short periods of interference. But this is typically a short period of time because the reference timing being maintained by the terminal will begin to drift from the timing which was being provided by the repeater before the interference occurred. The period of time that a terminal is able to maintain frame synchronisation for when there is an interference is dependent on a range of factors including the quality of the terminal’s hardware such as the crystal. For example, the period of time for which a terminal is able to maintain adequate frame synchronisation may be less than one second. When the period of interference ends and the terminal again receives data from the repeater’s downlink including the synchronisation pattern, it will adjust its timing, if required, to ensure that synchronisation with the repeater remains in place.
85 The eventual drift between a terminal’s reference timing and the repeater’s timing means that after a period of time without receiving transmissions from the repeater, the terminal may then need to resynchronise with the repeater once again to receive and transmit data.
Examples of systems using frame synchronisation
86 An example of a two-way radio system that includes frame synchronisation is a system called APCO P25. In P25 systems, a special sequence of 48 bits (a synchronisation pattern) is located at the beginning of a frame. In a P25 system, frame synchronisation occurs at the beginning of every message and is inserted every 180 msec throughout the voice message. MPT1327 devices also rely on frame synchronisation in order to decode messages. In TETRA systems, the repeater sends out frames in a repeating structure at constant intervals. The receiving device recognises that the synchronisation pattern is being received at every interval and will set its own clock to match the intervals of the synchronisation pattern. The terminal can then decode the incoming data frames to obtain relevant information such as the control information or payload. Also inbuilt into the system is a feature that is called forward error correction which is designed to compensate for a small percentage of lost data stream, which can occur if the user goes out of range.
Scanning in digital two-way radio systems
87 P25 terminals are able to automatically scan frequencies in a conventional two-way radio system. Transmissions between repeaters and terminals include embedded control messaging that allows for the late entry into conversations, such as talkgroup conversations, by scanning terminals.
88 TETRA terminals also automatically scan. However, TETRA terminals scan control channels rather than traffic channels. This occurs periodically to determine if a control channel with an improved signal strength can be identified. Prior to 26 July 2004, being one of the priority dates, the length of time it took to automatically scan frequencies in analogue systems was a well-known problem. Prior to that date, the known digital two-way radio systems provided little improvement on the length of time it took to automatically scan frequencies.
De-keying and re-keying in digital two-way radios
89 Similar to analogue repeaters, digital receivers have a hangtimer which prevents the repeater from de-keying immediately after a transmission. This ensures that the receiving user has sufficient time to respond to a communication before the repeater de-keys.
90 In conventional digital two-way radio systems, repeaters require a wake-up message in order to re-key. The repeater’s uplink continues to monitor the frequency so that the repeater is able to receive transmissions from terminals. This allows terminals to transmit a wake-up message to the repeater, enabling it to re-key. Although the specific type of wake-up message differs between two-way radio systems, every digital system will look for a valid transmission in order to successfully re-key.
91 Terminals are able temporarily to maintain data synchronisation or reference timing during short periods of interference. A short period of interference has the same effect as a condition where a repeater initially de-keys. In both circumstances, the terminal will no longer receive any data from the repeater’s downlink. As such, in both circumstances, the terminal will temporarily maintain data synchronisation without requiring data such as the repeating synchronisation pattern to be received from the repeater’s downlink.
92 An issue which exists in conventional digital two-way radio systems is that communications could be lost when a repeater’s downlink is initially deactivated. This can occur because of the inability of a receiving terminal to maintain reference timing in a temporary data synchronisation state. When this occurs, it is possible that the terminal transmitting a communication may not recognise that the repeater has de-keyed. This presents an issue because the terminal may continue to transmit communications which are then not repeated to the intended receiver.
Multiple access methods
93 There are three well-known and generally accepted methods implemented to utilise the limited RF spectrum more efficiently in two-way radio wireless communications. These methods aim to increase the number of users communicating within a specific portion of the radio spectrum. They are:
(a) frequency division multiple access (FDMA);
(b) as described above, time division multiple access (TDMA); and
(c) code division multiple access (CDMA).
94 CDMA was not used for two-way radio systems before 2004 and was instead used in cellular telecommunications systems.
FDMA
95 FDMA separates RF channels by frequency. For instance, for two-way radio communications, FDMA may split a 12.5 kHz channel into two, smaller, 6.25 kHz channels on which communications can each be transmitted. FDMA was introduced into digital two-way radio systems in the 1990s. It has been implemented into both digital and analogue two-way radio systems such as the P25 digital radio system. An illustration of FDMA channel splitting given by the primary judge is the following:
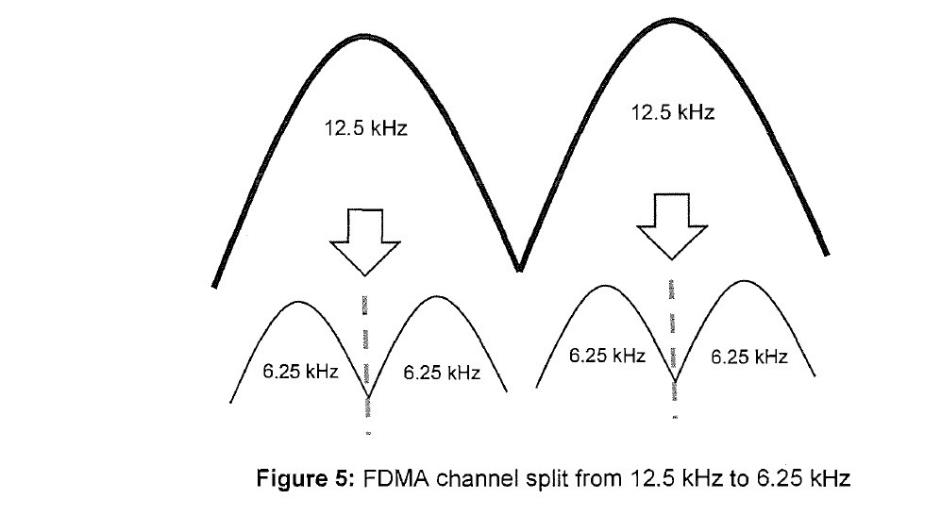
96 Using FDMA, a conversation occupies a whole channel exclusively, meaning there is one user and one conversation at a time per channel. To increase the number of channels it is necessary to increase the number of frequencies. However, it can be difficult and costly to obtain channel assignments from the regulator. For example, using FDMA, four users each of whom wishes to communicate at the same time would need access to four 6.25 kHz channels, which would be split from the two 12.5 kHz channels.
TDMA
97 TDMA was introduced in or around 1979 as a common multiple access technique for wired networks. It was first introduced to digital two-way radio systems in the 1990s and is still currently implemented into digital two-way systems. TETRA was the first system to implement TDMA in two-way radios.
98 TDMA separates RF channels into different timeslots while preserving the width of the 12.5 kHz channel. Timeslots are a defined period of time, usually a very short period of time, during which the sender’s communication is transmitted. TDMA allows several users to share the same channel. As a user transmits, their communication will be inserted into a timeslot of a very short, fixed period such as 50 msec or one twentieth of a second. Usually, a mobile station operating in repeater mode will be allocated to a timeslot by a repeater whereas a mobile station operating in direct mode is able to transmit in a free timeslot which is available on the frequency.
99 Users transmit in rapid succession which gives each user the impression that they have exclusive use of the channel and that their communication is being broadcast in real time. For example, in a two-timeslot TDMA system, two users can share one frequency at the same time. The distinction between FDMA and TDMA systems was illustrated by the primary judge using the following diagram:
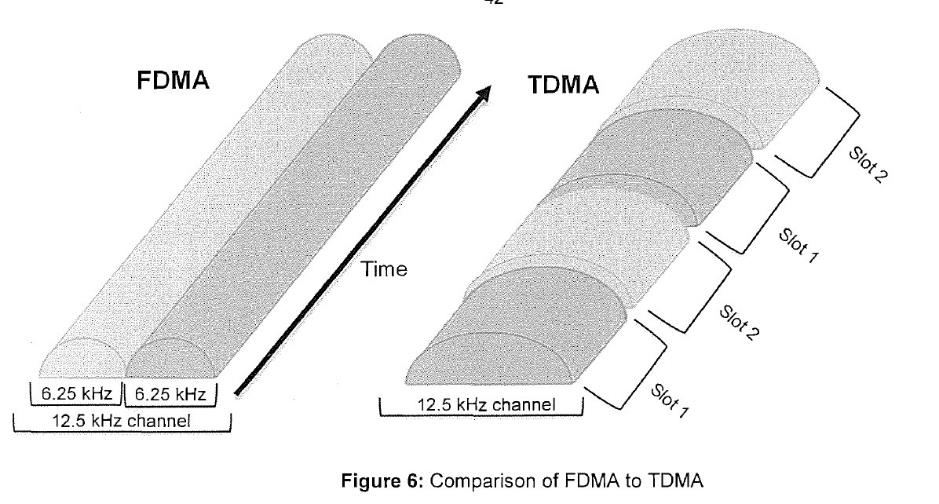
100 In a TDMA system, User 1 utilises the frequency for the first timeslot (slot 1 in the above diagram) then User 2 transmits for the next fixed period of time (slot 2). The channel then reverts back to User 1 who transmits for the next fixed period of time. The channel then reverts back to User 2 who transmits for the next time period and so on. The process occurs so quickly that neither user is aware that they are sharing a channel and neither experiences a delay in transmission. However, if more than two users wish to transmit, additional radio channels are needed. For example, in a two-timeslot TDMA system, four users who wished to communicate at the same time would require two 12.5 kHz frequencies.
101 TDMA introduced the ability to divide the physical channels (e.g. the 12 kHz channel) into logical channels. A logical channel is a channel which has the appearance and functionality of a channel but which is, at a technical level, actually made up of quite different constituent elements. For example, a user could select a logical channel designated as channel 1. This logical channel consists of one slot on the transmit frequency and a corresponding slot on the receiving frequency. Although the communication is happening over two frequencies, those two frequencies constitute, so far as the user is concerned, a channel called 1.
102 A half-duplex radio device cannot transmit and receive at the same time. However, using TDMA, such a device can constantly tune between the transmit and receive frequencies which has the effect of simultaneously transmitting and receiving for the user. This is possible for mobile stations operating in either repeater mode or direct mode.
B.3 Well-known digital radio systems before 26 July 2004
103 At this point we will identify various digital radio systems used before 26 July 2004, being the priority date of the 355 patent, as they are relevant to some of the issues that we will address concerning common general knowledge.
The MPT1327 standard and systems
104 One of the first trunked two-way radio systems was the MPT1327 standard. This is a standard which was developed by the United Kingdom Ministry of Posts and Telecommunications in the mid-1980s. It is a hybrid digital/analogue radio communication system in that it transmits both data to set up a call and analogue voice communications. It includes a trunked system controller that retains information including a list of terminal devices that are subscribed to the network, a record of the location of the terminals subscribed to the network, and the configuration of repeaters connected to the network. Each repeater in the network is connected to the traffic system controller with several cables, including a data cable for the dedicated control channel and physical cables for each of the repeaters that have traffic channels. MPT1327 systems include sites that each typically include several connected repeaters. One of the repeaters in each site operates as the dedicated control channel and the remaining repeaters are associated with the traffic channels.
105 Terminals connected to an MPT1327 network communicate with the dedicated control channel in order to set up and receive calls. Unless the system includes a time shared control channel, system users are typically allocated a traffic channel on the site that they are connected to in order to communicate with another system user. In a time shared MPT1327 system, the control channel can also be allocated as a traffic channel.
106 Terminals in an MPT1327 system automatically scan the control channels associated with repeaters in the network on a regular basis to determine if a site with increased signal strength is able to be located. To enable the automated scanning process, the terminals include a list of frequencies associated with control channels as well as associated repeater identifications in the network that are saved to memory in the terminal.
107 MPT1327 terminals typically included more frequencies saved to the memory to which the terminal is subscribed.
108 The repeater associated with the control channel for each site transmits control messages on the control channel to perform an action, such as setting up calls. The control messages included information such as the identification of a source terminal, the identification of a talkgroup, the identification of a site and the identification of a repeater. The primary judge set out in some detail the various types of control messages used. We do not need to set out that detail for present purposes.
109 MPT1327 used fast frequency shift keying to transmit data over the control channel. Such shift keying implements a technique that allows for digital data to be transmitted using an analogue signal. An electromagnetic carrier wave is used to carry the digital data over a distance and connect repeaters with terminals in remote locations. In such shift keying, the repeaters transmit data on the control channel by modulating the carrier frequency between two discrete values. Each of the discrete values correspond to a zero or a one. The terminals are able to receive and decode the digital data corresponding to control messages then perform the desired functions.
110 MPT1327 terminals are not able to communicate with each other in direct mode but use repeaters to transmit. Similar to conventional analogue two-way radio systems, the repeaters in trunking two-way radio systems such as MPT1327 de-key when the downlink associated with the repeater is not in use. At the end of a transmission, terminals leave the traffic channel that was being used for a communication. A message is then sent to the traffic system controller, indicating that the conversation is complete. After certain conditions are met, such as after the expiration of a timer, the traffic system controller sends a message to the repeater associated with the traffic channel that is no longer in use and instructs the repeater to de-key.
APCO P25 standards and systems
111 APCO P25 is a set of digital two-way radio standards that were produced by the Association of Public Safety Communications International in the United States in the 1990s. P25 is an open architecture that defines a digital radio communications system for public safety organisations. P25 was implemented by various manufacturers and organisations including Motorola. The P25 standards define the interfaces, operation and capabilities of P25 radio systems.
112 Before 26 July 2004, P25 systems were both conventional and trunked digital two-way radio communication systems that transmitted data using FDMA methods. These systems are now referred to as “Phase 1 P25”. Phase 1 systems operate using a 12.5 kHz frequency bandwidth and use Continuous 4 Level FM, a type of frequency shift keying modulation to transmit data. P25 systems implement a vocoder to encode speech into a digital data stream.
113 P25 transmissions include a link control (LC) message that forms part of voice transmissions to provide signalling information to terminals. The LC message is referred to as an LC word. Examples of LC words are shown in the P25 standards and include a message to specify the LC word’s content (LCF), the manufacturer’s identification (MFID), the talkgroup identification (TGID), the source identification (Source ID), the destination identification (Destination ID), and an emergency indicator.
114 P25 terminals are able to automatically scan frequencies that are saved to memory in the terminals. P25 transmissions between repeaters and terminals included embedded control messaging that allowed for the late entry into conversations by scanning terminals.
115 A sequence of bits provides frame synchronisation which allows for the messages which follow to be decoded. For P25 transmissions, frame synchronisation messages are located at the start of every voice and data transmission and within transmissions, which are spaced at 180 msec intervals as provided for in the P25 standards, to allow for late entry by terminals. Once a terminal has synchronised to a transmission, it is then able to determine if the transmission is relevant by interrogating the LC message, that is to say, the LC word. This might occur to determine if an LC message indicates that the transmission is for a talkgroup to which the scanning terminal is subscribed.
116 The LC word is included in the Logical Link Data Units (LDU1 and LDU2) that are transmitted during a voice call. In order to receive LDU1 and LDU2 while scanning, a P25 terminal needs to decode all of the data being transmitted, including the data associated with the error correction algorithm. This was a known limitation with P25 systems and meant that it was slow to lock onto a channel.
117 An additional associated limitation with P25 systems was that a P25 terminal required several messages within a data stream to be decoded and then interrogated for the required information. So, automatically scanning for incoming transmissions in a P25 system was a slow process as terminals were required to decode large parts of the data stream and perform error correction of the data to allow the terminal then to interrogate the data stream for conditional requirements before locking onto a particular channel. If the transmission was a voice call, most of the packets of data were allocated to the payload being transmitted and the address information would only be transmitted every ninth frame, which was every 180 msec. This meant that terminals needed to wait until the relevant information was received and decoded before the terminal was able to make a decision with respect to remaining on a channel. As a result, P25 did not provide much improvement to the well-known scanning problem with reference to analogue systems. This was a well-known limitation of P25.
118 P25 two-way radio systems can be used in conventional direct mode and repeater mode. Terminal devices also may include a button that allowed for users to toggle between the different modes. Similar to conventional analogue two-way radio systems, the repeaters in P25 systems keyed and de-keyed when the downlink associated with the repeater was not in use such as when the talk channel is released. Also, similar to conventional analogue two-way radio systems, the repeaters in P25 systems on occasion included a timer to prevent the repeater from de-keying immediately after a transmission.
TETRA
119 TETRA is a digital trunking system that was standardised by ETSI in the mid-1990s. It was first introduced commercially in the early 2000s. TETRA is a digital system that implements TDMA to transmit communications between terminals and repeaters. Each TDMA frequency of 25 kHz is separated into four timeslots to allow for several communications to take place on a single frequency.
120 TETRA systems implement a vocoder to encode speech into a digital data stream. TETRA terminals are able to communicate directly with one another, without using a repeater. This is referred to as direct mode operation. Devices which implement TETRA perform frame synchronisation to transmit communications.
121 TETRA is similar to MPT1327 in that it includes a dedicated control channel. But unlike MPT1327, because the system implements TDMA, a single repeater can be used for both a control slot and multiple talk slots. This means one timeslot can be used to communicate control messaging and the remaining timeslots can be used to communicate voice and data between terminals. TETRA implements a form of phase-shift keying (differential quadrature phase-shift keying) to transmit data between connected repeaters and terminals. Phase-shift keying is a method of conveying data by modulating the frequency. It is not necessary here to explore the nature of phase-shift keying. However, similar to MPT1327, the repeater associated with the control channel for each site transmits on the control slot to perform actions such as setting up calls. As also occurs in MPT1327, the control messages include information such as the identification of a source terminal, the identification of a talkgroup, the identification of a site, and the identification of a repeater.
122 Scanning in TETRA occurs on control channels, rather than on traffic channels. The scanning issues which existed in other systems, such as P25, still exist in TETRA. However, the use of control channels means it is not as noticeable to the user as the delays occur in the background. As a trunked system, in TETRA, the network is responsible for orchestrating scanning. As a user communicates on one channel, the network operates behind the scenes continually to scan for an alternative, improved channel. The issue of timing thus still applies to TETRA trunked systems but is far less relevant to users.
123 Finally, colour coding was first introduced in TETRA two-way radio systems. Colour coding is a system in digital mobile radios which allows for the separation of groups of users (such as different service providers or systems) who are sharing the same frequency or channel. Colour coding prevents radios from one group from mistakenly crossing into another group which uses the same frequencies and so stops interference within a channel. The purpose of colour codes is to differentiate multiple receivers that are within a geographical area using the same frequency. Colour coding is assigned by the system administrator and differentiates each group by their colour code. Each colour code is represented by a number (e.g. red equals one). Colour coding information is contained within control messages.
The draft DMR protocol
124 In evidence before the primary judge was a document titled “Draft Agenda Narrowband TDMA DMR Protocol” which the parties and his Honour referred to as the draft DMR protocol and was dated 26 April 2004. It described a digital two-way radio system that implements TDMA methods. It is the precursor to the 2005 DMR Standard that was formalised by ETSI in April 2005. The draft DMR protocol was discussed during a working group meeting at ETSI during the development of the 2005 DMR Standard. His Honour accepted that if a person had been tasked with designing a method for scanning in a digital two-way radio system in July 2004, that person would have located a copy of the draft DMR protocol in order to understand what had already been done in this area.
B.4 Well-known digital radio systems before 28 July 2005
125 In the field, each of the above two-way radio systems (that is, MPT1327, P25 and TETRA) were part of the common general knowledge prior to 28 July 2005, being the priority date of the 960 patent. Further, by 28 July 2005 the 2005 DMR Standard was known by those working in the field of two-way radio communications.
126 The purpose of the 2005 DMR Standard was to standardise digital radios worldwide, to reduce channel interference, and to increase radio spectrum efficiency. Systems which operate using the 2005 DMR Standard implement a vocoder to encode speech into a digital data stream. The 2005 DMR Standard evolved from an earlier Digital Interchange of Information and Signalling (DIIS) specification for a two-way radio system. DIIS, which ETSI also attempted to standardise, was developed in the early 2000s. However, DIIS was not embraced by the two-way radio community. Many of the principles from DIIS were then incorporated into the 2005 DMR Standard.
127 DMR standard compliant systems operate using two-slot TDMA to transmit communications. That is, each TDMA frequency is separated into two timeslots to allow two communications to take place on a single frequency. DMR compliant systems can operate in either simplex or duplex mode meaning that mobile stations operate on either one or two frequencies. Duplex DMR compliant systems have one frequency for transmitting and a separate frequency for receiving, which is known as a frequency pair or physical channel. So, use of TDMA in the DMR compliant standard means that physical channels could be divided into logical channels.
128 Similar to previous digital and analogue two-way radio systems, the 2005 DMR Standard allowed for direct mode communications between terminals. The purpose of this was to allow for systems that required less infrastructure because no repeater is required for direct mode communications, or for when a repeater is unavailable.
B.5 Appeal concerning the 355 patent
129 We now turn to Hytera’s appeal concerning the 355 patent. The primary judge dealt with the 355 patent questions principally at [125] to [421] of his reasons.
Description of the 355 patent
130 The 355 patent is entitled “Method and system of scanning a TDMA channel” and, as noted earlier, has a priority date of 26 July 2004. It is appropriate to make some observations concerning the specification including aspects that the primary judge drew attention to.
131 The patent describes the field of the invention as relating generally to “wireless communications systems and more specifically to scanning in a time division multiple access (TDMA) system”, and describes the background of the invention in the following terms:
A wireless communications system may generally comprise a set of “subscriber units,” typically subscriber units are the endpoints of a communication path, and a set of “base radios,” (also known as “repeaters”) typically stationary and the intermediaries by which a communication path to a subscriber unit (SU) may be established or maintained. One such type of system is a time division multiple access (TDMA) communication system where the radio medium (or RF frequency) is divided into time slots to carry the communications of the system. Because the communication system carries many communications at one time, a subscriber unit may want to monitor other communications in the system. Scan is a feature that allows a subscriber unit to monitor other communications in the system.
SUs of the wireless communications system utilize a feature termed “scan” where an SU locks on to specific RF frequencies in a preprogrammed list in the SU. The RF frequencies in the scan list may be associated with more than one wireless communications system. For example, an SU may have RF frequencies from the Schaumburg fire department and the Rolling Meadows fire department in its scan list. If the preprogrammed scan list is very long and has many RF frequencies, then the scan feature takes a long time. Further, in the usual case, when many of the RF communications are normally of no interest to the scanning SU, the scanning SU spends a lot of time listening to communications that are of no interest to it. For example, this occurs when an RF frequency is included in the preprogrammed scan list, but the current communication is addressed to a SU or group of SUs that are of no interest to the scanning SU.
Accordingly, there exists a need for scanning a TDMA channel which improves the amount of time that an SU spends scanning.
132 The following summary of the invention is then given:
According to one aspect of the present invention there is provided a method for scanning a TDMA channel by a subscriber unit in a wireless communications landscape, wherein the subscriber unit is operationally connected to at least one base radio over a plurality of channels, the method including the steps of:
locking onto a channel of the plurality of channels by the subscriber unit wherein a subset of the plurality of channels is preprogrammed in a list in the subscriber unit;
transmitting from at least one base radio a control message to the subscriber unit wherein the control message has a first information which informs the subscriber unit of activity present on the channel of the plurality of channels;
receiving and decoding the control message for the first information by the subscriber unit; and
if the first information indicates that activity is present on the channel of the plurality of channels, then
determining whether the activity is of interest to the subscriber unit by comparing a second information in the control message with a third information preprogrammed in the subscriber unit and
if the activity is of interest to the subscriber unit, then remaining on the channel of the plurality of channels to receive the activity present on the channel.
According to a further aspect of the present invention there is provided in a TDMA system whereby the TDMA system includes a plurality of subscriber units and a plurality of base radios, a method for scanning, the method including the steps of:
locking onto a channel preprogrammed in a list of a subscriber unit whereby the channel carries activity on one timeslot of the TDMA system;
receiving an activity update message from a base radio of the plurality of base radios wherein the activity update message indicates in a first information the activity on the channel and indicates in a second information at least one characteristic of the activity on the channel;
determining whether the activity is of interest to the subscriber unit by comparing the at least one characteristic with preprogrammed third information in the subscriber unit; and
if the activity is of interest, then remaining on the channel to receive the activity; otherwise moving to the next channel in the list.
133 Under the heading “Brief Description of the Figures” there appears references to three figures in these terms:
An illustrative embodiment of the invention is now described, by way of example only, with reference to the accompanying figures in which:
FIG. 1 is a block diagram of an example wireless communications landscape in accordance with an embodiment of the invention.
FIG. 2 is a flow diagram of an example method for providing channel access for voice transmissions.
FIG. 3 is an example of a specific Common Announcement Channel message called an Activity Update.
…
134 The three figures are then explained in the remaining body of the specification under the heading “Detailed Description”.
135 Figure 1 is as follows:
136 Figure 1 is described in the following terms at p 2 line 18 to p 3 line 20:
Referring now to FIG. 1, there is shown an example of the method and apparatus of the present invention as it may be employed and incorporated into a typical wireless communications landscape 100 having system 110, system 120, and system 130. The illustrated example has three systems 110, 120, 130 whereby a system is comprised of a multiplicity of communication resources of RF frequencies, base radios (BRs) and subscriber units (SUs) optionally managed by system controllers (not shown) whereby the SUs send and receive communications with BRs (also known as “repeaters”).
System 110 comprises a plurality of cells, each with a BR 3, 5, 7, 9, 11, 13 typically located at the center of the cell, and a plurality of SUs 12, 14, 16, 18, 20, 22 all of which are communicating on RF frequencies assigned to system 110. The SUs 12, 14, 16, 18, 20, 22 in system 110 may include all the RF frequencies associated with the BRs 3, 5, 7, 9, 11, 13 in system 110 in their preprogrammed scan lists. System 120 comprises a plurality of cells, each with a BR 26, 28, 30 typically located at the center of the cell, and a plurality of SUs 34, 36, 38 all of which are communicating on RF frequencies assigned to system 120. The SUs 34, 36, 38 of system 120 may include all the RF frequencies associated with BRs 26, 28, 30 in their preprogrammed scan lists. Further, SU 36 may include RF frequencies associated with the BRs in system 110 and with the BR in system 130 since the SU 36 is sufficiently close to all three systems 110, 120, 130. System 130 comprises a cell with a BR 24 and SUs 32, 40 all of which are communicating on RF frequencies assigned to system 130. Further, BRs 3, 13, 24, 28 may all be operating on the same RF frequency, but using a different color code since the BRs are separated by great geographical distance.
A BR preferably comprises fixed equipment for communicating data/control and voice information to and from the SUs for facilitating communications between the SUs in the wireless communication landscape 100. A subscriber unit (SU) preferably comprises mobile or portable devices (such as an in-car or handheld radios or radio telephones) capable of communicating with a BR using time division multiple access (TDMA) or time division duplex (TDD) techniques as further described herein, in which specified time segments are divided into assigned time slots for individual communication. As is known in the art, each RF frequency in the system carries time slots whereby each time slot is known as a "channel." Thus, for the BRs shown in FIG. 1, each BR has two channels associated with the coverage area.
137 The description then turns to an illustrative embodiment of the invention. The first part of this is at p 3 line 21 to line 29:
In an illustrative embodiment of the present invention, the wireless communications landscape 100 assumes a two slot TDMA communications system; however, other slotting ratios may be used in the TDMA communications system and still remain within the spirit and scope of the present invention. In an illustrative embodiment, the SU determines time slot numbering by decoding a TDMA channel field in a Common Announcement Channel (CACH) burst whereby the CACH burst is used for signaling information in the wireless communications landscape 100. In the illustrative embodiment of a two slot TDMA communications systems, the CACH burst is common to timeslot 1 and to timeslot 2.
138 By the priority date for the 355 patent, the 2005 DMR Standard had not yet come into effect and would not come into effect until 2005. The standard prescribed a two timeslot TDMA system. The illustrative embodiment proceeded on the same basis.
139 An aspect of this paragraph is its reference to the Common Announcement Channel (CACH) burst, which is used for signalling information and, in the illustrative embodiment, is common to both channels. The illustrative embodiment proceeds on the basis that the CACH burst is the same for both channels. As the primary judge said, an implication of this, borne out later in the description, is that the CACH burst carries signalling information for both channels.
140 The description then continues at p 3 line 30 to p 4 line 9:
As is known in the art, “color code” is a common identifier used by a group of SUs which utilize the same BR. For example, as shown in FIG. 1, SUs 12, 14, 22 are in one color code because they utilize the same BR, namely BR 9. Further, a color code field may be present in an embedded signaling message and a general data burst to provide a means of addressing a radio network or a specific repeater so that co-channel interference may be rejected. Further known in the art, a “talkgroup” is a group of SUs that share an RF frequency and timeslot and have the same color code. In an illustrative embodiment, a talkgroup is identified by a 16-bit talkgroup identifier (TGID and an individual subscriber unit is identified by a 24-bit subscriber unit identifier (SUID). Thus, in an illustrative embodiment, SUs that share a color code are further subdivided into talkgroups so that SUs in one talkgroup do not hear SUs in another talkgroup.
141 Here there are references to the concepts of the Talkgroup Identification (TGID) and Subscriber Unit Identification (SUID). In the illustrative embodiment, these are 16 bit and 24 bit fields respectively.
142 The description then continues at p 4 line 10 to line 21:
As used herein, the terms “communication” and “transmission” are used interchangeably and refer to contiguous TDMA bursts emanating from one radio in one timeslot. As such, transmissions may generically refer to voice, data or control information relating to the wireless communications landscape 100. The term “call” refers to related voice transmissions between SUs in the wireless communications landscape 100.
As is known in the art, the term “burst” refers to the smallest standalone unit of a TDMA transmission. In an illustrative embodiment, for a burst found in a Motorola Low Tier Digital system, a defined transmission is 216 bits of payload and 48 bits of synchronization or embedded signaling. The defined transmission takes 27.5 msec to transmit and may be followed by 2.5 msec of guard time or the CACH burst. Thus, a “burst” in such a Motorola Low Tier Digital system is 30 msec.
143 The defined transmission used in the illustrative embodiment is 264 bits in length. It takes 27.5 msec to transmit. It is followed by a period of 2.5 msec which can be used as guard time or for a CACH burst. The CACH burst is used for signalling information and is transmitted on both slots 1 and 2. The total burst is therefore 30 msec. Later in the description there is a discussion of a particular kind of CACH message known as an activity update message which is transmitted by means of four CACH bursts. What this means is that the activity update message is transmitted in the last 2.5 msec in each of four 30 msec bursts.
144 As the primary judge pointed out, it is not clear from the description at this stage whether these bursts are successive or whether other signalling information is conveyed by means of the CACH bursts. But later in the description it is apparent that more signalling information in the form of seven CACH bursts, known as the full LC message, also utilise this 2.5 msec portion. It may be noted that, in the illustrative embodiment, the activity update message is itself 28 bits in length.
145 It may be surmised from Figure 3 that each of the four CACH bursts occurs as the last 2.5 msec of the burst, that three of the four bursts contain 8 bits, and that one of the bursts contains 4 bits. We will set out Figure 3 shortly.
146 Further, recorded at p 6 line 24 to 27 is that the activity update message, which is transmitted by means of the four CACH bursts, is “used to assist in identifying whether there is an active transmission (also termed “activity”) on the channel”. It also “provides information that indicates whether the scanning subscriber unit (SU) should dwell on the channel or should resume scanning”. Determining that there is no active transmission on the channel would be a good reason for resuming scanning. But as the primary judge noted, even if there is activity on the channel, the information contained in the activity update message may indicate to the subscriber unit that the activity is not of interest to it. Part of the controversy before the primary judge concerned the nature of the information contained in the activity update message.
147 The illustrative embodiment proceeds on the basis that the activity update message both indicates whether there is activity on the channel and also provides unspecified (at this stage) information to determine whether to “dwell” on the channel or move to the next channel. The word “dwell” does not appear in the claims. One of the debates between the parties concerned whether the decision to dwell is a permanent decision or whether the subscriber unit, once confronted with further information, might decide to stop dwelling on the channel and move on to scanning for the next channel. Hytera’s construction case is that this is not permissible.
148 The description then continues to discuss the nature of scanning at p 4 line 22 to 28:
In an illustrative embodiment, a scan is performed in at least one of three situations: 1) when the SU powers on where the receiver automatically changes "channels" in a set order with a list preprogrammed in the SU, 2) when a user of the SU manually taps a button or turns a dial to manually step through frequencies preprogrammed in the SU, and 3) when a user of the SU sets the SU to scan mode where the receiver automatically changes frequencies in a set order with a list preprogrammed in the SU.
149 At p 4 line 29 to p 5 line 14, a connection is made, in the case of the illustrative embodiment, between scanning and the concept of a characteristic of a communication:
Further, there may be different types of scanning that a SU performs. An SU may be programmed to perform scan based upon a characteristic of the active transmission such as whether the active transmission is voice, data, group, individual, emergency, and non-emergency. For example, a scanning SU may be programmed to scan for channels only carrying voice transmissions. Further, a scanning SU may be programmed to scan for channels only carrying data transmissions. Further yet, a scanning SU may be programmed to scan for channels carrying voice transmissions that are addressed to individual SUs and not voice transmissions that are addressing talkgroups. Further yet, a scanning SU may be programmed to scan for channels carrying data transmissions that are addressed to individual SUs and not data transmissions addressing talkgroups. Another example, a scanning SU may be programmed to scan for channels carrying any emergency transmissions regardless of the group that the active transmission is associated with. Yet another example, a scanning SU may be programmed to scan for channels carrying only non emergency transmissions regardless of the group that the active transmission is associated with. As can be imagined, there are numerous examples combining the characteristics to program a scanning SU to only search for specific active transmissions and the examples listed above are only illustrative and not exhaustive.
150 The description then introduces Figures 2A and 2B. Figure 2A is concerned with how the illustrative embodiment processes a voice transmission and Figure 2B deals with a data transmission. They are as follows:
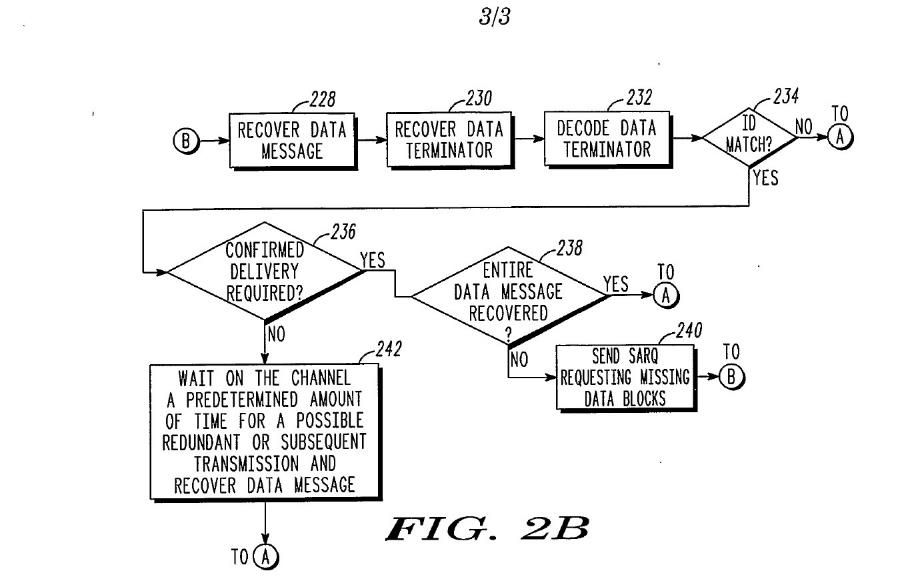
151 Figure 2A is connected to Figure 2B at Block 226.
152 The explanation of Figure 2A begins at p 5 lines 15 to 30:
Referring to FIG. 2, in operation, an SU performs the function of scanning by tuning to a specified channel enumerated in a scan list preprogrammed in the scanning SU (Block 202). As is known in the art, a channel is also known as a “personality” where a personality is typically a radio frequency (RF) with additional qualifying information. The scanning SU pauses on the selected personality for a specified time period and tests whether an RF carrier is detected (Block 204). In one embodiment, a scanning SU which is programmed to scan only for voice transmissions pauses for 25 msecs before continuing.
As is known in the art, the specified time period depends upon the type of signal expected to be received by the scanning SU such as analog voice, FDMA digital, and TDMA digital. Further, the specified time period may depend upon the type of scan being performed. As mentioned above, the type of scan may depend upon a characteristic of the active transmission such as whether the active transmission is voice, data, group, individual, emergency, and non-emergency. For example, if the scanning SU is programmed to scan for channels only carrying data transmissions, then it may wait for 65 msecs before continuing.
153 The description then continues at p 5 line 31 to p 6 line 12:
If an RF carrier is present, then the scanning SU remains on the selected personality and performs synchronization (Block 206). In an illustrative embodiment, performing synchronization between the BR and the SU involves waiting a predetermined period of time for detecting a time slot synchronization signal. The time slot synchronization signal is a 48 bit (also known as 24 symbols) frame sync word. The time slot synchronization signal identifies the center of a TDMA burst and the type of communication present on the TDMA channel so that a receiver in the scanning SU may be able to receive transmissions on the TDMA channel. Performing synchronization is complete upon detection of the time slot synchronization signal within a predetermined period of time. In one embodiment, the scanning SU must receive the time slot synchronization signal within 335 msecs. If the communication between the SU and the BR is in synchronization or the SU is successfully able to perform synchronization between the BR and the SU, then the SU determines a color code for the active transmission on the channel (Block 208).
154 The description then continues at p 6 lines 13 to 20:
As is known in the art, regardless of whether a carrier is detected (Block 202), a scanning SU that receives a frame synchronization message further decodes the personality. Thus, if frame synchronization is performed, then the scanning SU remains on the personality an additional amount of time to determine whether there is a match of the color code for the active transmission on the channel (Block 208). If there is not a match of the color code (Block 208), frame synchronization (Block 206), or carrier detect (Block 204), then the scanning SU tunes to the next channel in the preprogrammed scan list (Block 220).
155 At least for the illustrative embodiment, a failure to establish the presence of a carrier on the RF, or if having done so, if frame synchronisation is not achieved or, if it is achieved, if the colour associated with the communication does not match the colour of the subscriber unit, has the consequence that it moves to the next channel. But if all of those matters are, on the other hand, satisfied then it follows that the subscriber unit has detected a carrier signal, has achieved frame synchronisation, and has determined that the subscriber unit and the base radio sending the communication are part of the same colour group. In this circumstance, the illustrative embodiment then decodes what it refers to as an “activity update message”. This appears from p 6 lines 21 to 27:
If there is a match of the color code for the active transmission on the channel, then the scanning SU remains on the channel and decodes a specific CACH message termed an “activity update” message 300 (Block 210). In an illustrative embodiment, the activity update message 300 is a 4-burst CACH message used to assist in identifying whether there is an active transmission (also termed “activity”) on the channel. The activity update message 300 provides information that indicates whether the scanning SU should dwell on the channel or should resume scanning.
156 The nature of the four CACH bursts is described later. The description then continues to describe the activity update message used in the illustrative embodiment in more detail. It does so by reference to Figure 3 which is as follows:
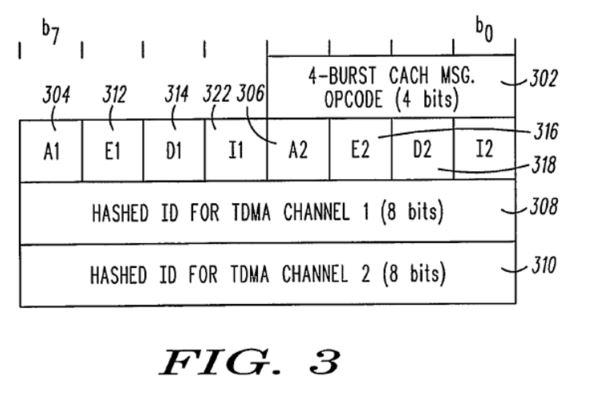
157 The primary judge found that this diagram was not easy to follow. However, it is reasonably clear that its four horizontal layers represent the four CACH bursts which are either 8 or 4 bits in length (or 2.5 msec). Although the description of the illustrative embodiment explains the lower three horizontal layers in terms which are clear, this is not so in relation to the first layer. It is not clear, for example, what the “4-BURST CACH MSG. OPCODE (4 bits)” is. Since it is an opcode, the primary judge was inclined to conclude that it is an instruction to the subscriber unit to receive the following three CACH bursts as data. The view that the opcode is part of an instruction set is supported by an observation appearing later in the description where it is contrasted with the balance of the activity update message which is said to be data (“besides the opcode field 302, the rest of the activity update message 300 is considered to be data”: p 7 lines 19 to 20).
158 As to the explanation of Figure 3, the description continues in these terms at p 6 line 28 to p 7 line 15:
As shown in FIG. 3, the activity update message 300 includes an activity field 304, 306 specific to each timeslot that indicates whether the channel is presently supporting a call or transmission on either of the timeslots. For example, as shown in FIG. 3, one-bit field 304 indicates whether timeslot one is supporting a call or transmission and one-bit field 306 indicates whether timeslot two is supporting a call or transmission where a value of “0” indicates that the timeslot is not active and “1” indicates an active transmission on the time slot. If there is an active transmission on the timeslot (Block 211), then the scanning SU determines whether the active transmission is of interest to the scanning SU. Otherwise, the scanning SU moves to the next personality in the preprogrammed scan list (Block 220).
Further, if an active transmission is present, then the activity update message 300 also has other information to identify the type of transmission. For example, the transmission may be voice, data, an emergency, talkgroup or individual transmission as shown in FIG. 3. As shown in FIG. 3, a voice or data transmission is signaled by one-bit fields 314, 318 where a value of “0” indicates that the active transmission is a voice transmission and “1” indicates that the active transmission is a data transmission. As shown in FIG. 3, an emergency or non emergency is signaled by one-bit fields 312, 316 where a value of “0” indicates that the active transmission is a non emergency transmission and “1” indicates that the active transmission is an emergency transmission. …
159 The primary judge made the following observations with respect to Figure 3 and its description.
160 First, the second row contains 8 bits marked as A1, E1, D1, I1, A2, E2, D2 and I2. The illustrative embodiment concerns a two timeslot TDMA system. The first four bits concern timeslot 1 and the second four concern timeslot 2. The bits A1 and A2 (the “activity indicators”) indicate whether activity is present on timeslot 1 and 2 respectively, 1 signifying activity and 0 signifying no activity. The bits E1 and E2 signify the presence of an emergency broadcast if set to 1 or no emergency broadcast if set to 0. The bits D1 and D2 signify a data communication if set to 1 or a voice communication if set to 0. The bits I1 and I2 indicate whether the transmission is intended for an individual if set to 1 or a talkgroup if set to 0.
161 Second, the decoding of the four burst CACH message and the rendering of these 8 bits is unlikely, except perhaps in the case of the emergency bit, to provide enough information to the subscriber unit to ascertain that the communication to which the activity update message relates is, in fact, a communication which the subscriber unit wishes to receive. What most of them do is to operate either in a negative fashion to indicate that the communication is not one in which the subscriber unit is interested, or alternatively, in a provisional fashion, to indicate that the communication could be of interest. For example, if the activity bit is set to no activity then the subscriber unit may move on to the next channel. Similarly, if the subscriber unit is not interested in data transmissions the fact that the D1 bit is set to 1 provides the subscriber unit with sufficient information to know to move on to the next channel.
162 Third, the activity bit has the consequence that the subscriber unit will not continue scanning on a timeslot which is indicated to be inactive. The other bits in the second row in Figure 3 in various ways signify the presence or absence of communications with certain characteristics. The primary judge said that it is possible to think of these separate signifiers as a form of information. It is also possible to think of the activity indicator as a form of information. In that regard, it is noted that the claims in the 355 patent speak in terms of a “first information”, signifying whether activity is present on a timeslot, and the existence of a “second information”, which signifies whether the communication is of interest to the subscriber unit.
163 Fourth, there is an implication flowing from the inclusion of the activity update message in the 2.5 msec interval at the end of each 30 msec burst. The activity indicator is useful for saving the subscriber unit from wasting time scanning an inactive timeslot. The other bits (E, D and I) perform a similar although less dramatic purpose. In terms of the signal architecture in the illustrative embodiment, the 2.5 msec is used not just to signal activity but also to convey other information about the communication. As his Honour noted, whether this is a feature of the invention as claimed, as opposed to a feature of the illustrative embodiment, is an issue between the parties.
164 The description then continues at p 7 lines 19 to 23:
Further, besides the opcode field 302, the rest of the activity update message 300 is considered to be data and is populated by information from a full Link Control (LC) message for a voice transmission and from a data header for a data transmission. For example, the emergency one bit fields 312, 316, the group one bit fields 320, 322, and the addresses 308, 310 are recovered from the LC message or a data header.
165 It appears from this that in the illustrative embodiment, the data in the activity update message is populated by information from a full LC message for a voice transmission or from a data header for a data transmission. The description does not explain at this point what a full LC message or a data header is. However, it would appear that it contains at least all of the information which is in the activity update message.
166 The description then continues at p 7 line 24 to p 8 line 2:
If an active transmission is present and if the scanning SU is programmed to check the active transmission (Block 222) for a transmission addressed to a SU of interest, then the scanning SU determines whether the active transmission is addressed to a SU of interest (Block 212). Otherwise, the scanning SU checks to see if the scanning SU is programmed to receive the active transmission (Block 224). For example, the scanning SU may be programmed to receive all emergency calls regardless of identification (ID) of the source or destination of the active transmission. If the active transmission is of interest to the scanning SU, then the speaker is unmuted and audio is rendered to the user of the scanning SU (Block 218). Otherwise, the scanning SU moves to the next personality in the preprogrammed scan list (Block 220).
167 This passage and Blocks 222, 212 and 224 are, at first blush, a little obscure. However, the primary judge said that they were important. First, Block 222 is only reached after it has been determined at Block 211 that there is an active transmission on the timeslot. Translated back into Figure 3, this means that bit A1 (or if timeslot 2 is involved, bit A2) has been set to 1. Second, Block 222 reflects the programming of the subscriber unit. It will either be programmed to check for identification or it will not. Third, if it is programmed to check for identification, then the subscriber unit proceeds to Block 212. Fourth, if the subscriber unit is not programmed to check for identification then it proceeds to Block 224 and checks to see if the transmission is nevertheless of interest. This it does by checking the remaining bits in the same row of Figure 3. As the description notes, if the subscriber unit is programmed to receive emergency transmissions and the emergency bit is set in the second row then the speaker is unmuted and the audio rendered (Block 218).
168 The primary judge then discussed the process of identification if the subscriber unit has been programmed to receive transmissions addressed to a subscriber unit of interest. The process of identification does not take place at Block 222 which instead just reflects a programming choice which has been made in the subscriber unit. If it is programmed to see if the transmission is from a subscriber unit of interest, then the actual process of identification occurs at Block 212. Of this process the description then continues in these terms at p 8 lines 3 to 15:
Further yet, if an active transmission is present, the activity update message 300 also identifies the SUID or TGID of the active transmission. As shown in FIG. 3, the identification field 308, 310 is an 8-bit hashed field as shown in FIG. 3. Further, because there are a limited number of bits in the activity update message 300, the ID field 308, 310 is hashed. For example, if the active transmission on timeslot 1 is directed to SU 16 and SU 16 is identified by a 24 bit SUID, then the ID field 308 is hashed to 8 bits. Another example is an active transmission on timeslot 2 directed to an SU in a talkgroup, e.g. SU 12, where the talkgroup is identified by a 16 bit TGID. Thus, the ID field 310 is hashed from the TGID of 16 bits to 8 bits. As is known in the art, there are many algorithms that can be used to perform the function of hashing and one such well known algorithm is a CRC-8 checksum with a generating polynomial of g(x)=x8+x2+x+1. With an input of a 16 bit TGID or a 24 bit SUID, the output is an 8 bit CRC hashed ID field 308, 310 as shown in FIG. 3.
169 This takes one back once again to Figure 3. The third and fourth rows of Figure 3 are 8 bits in length. The bottom row is for Channel (timeslot) 2 and the second from the bottom row is for Channel (timeslot) 1. The activity update message is sent across both timeslots. To that extent it contains redundant information, for the information in bits b0 to b3 concern timeslot 2 in the row which indicates the characteristics of the transmission whilst those at b4 to b7 concern timeslot 1. Similarly, the two 8 bit “hashed IDs” are each only relevant to one of the two timeslots.
170 The primary judge then said that the immediate problem facing the illustrative embodiment is that the SUID is 24 bits long and the TGID is 16 bits long. But the two ID fields in the activity update message are only 8 bits long. The passage effectively teaches that the SUID and TGID are to be subject to a compression algorithm which will reduce them in length to an 8 bit structure. The expression “hashed ID” therefore refers to a compressed form of the SUID and the TGID. An ID match at Block 212 does not definitively determine that the transmission is for the subscriber unit of interest. This is because the compression algorithm can cause more than one subscriber unit identified by a 24 bit SUID to have the same 8 bit hashed ID. A similar problem affects subscriber units identified by a 16 bit TGID. It is therefore necessary for a complete ID check to be done. This is apparent from Blocks 213, 226 and 214 if the transmission is a voice transmission, and from Blocks 213, 226 and, in Figure 2B, Blocks 228, 230, 232 and 234, if the transmission is a data transmission. The description returns to these matters, but before it does so it notes that the activity update message may be received before the colour code of the active transmission is known.
171 Once it has been determined from the hashed IDs in rows 3 and 4 of Figure 3 that the transmission is of interest to the subscriber unit, the subscriber unit then asks whether the transmission is voice or data (Block 226). This it can do from the D bits in row 2 of Figure 3 which provide that information.
172 So, the flow chart in Figure 2A uses all four of the characteristic bits in row 2 of Figure 3. The activity bit (A bit) is used at Block 211 to determine whether there is activity on the channel or not. The emergency bit (E bit) is used at Block 224 to determine, if the transmission is not directed to a subscriber unit of interest, whether it is an emergency transmission or not and, if it is an emergency transmission, unmutes the speaker. The individual bit (bit I) is used at Block 224 to determine whether the transmission is directed to an individual or a talkgroup. Finally, the data bit (D bit) is used at Block 226 to determine, after identification at the level of the hashed IDs has occurred, whether the transmission is voice or data. The illustrative embodiment therefore deploys all four of the characteristic bits in the second row of the activity update message as well as the hashed IDs, and does so in respect of both timeslots.
173 This understanding of the invention depicted in Figure 2A is important for the construction issue between the parties. The language of claim 1 requires the invention to determine whether the activity is of interest to the subscriber unit and if it is, to remain on the channel to receive the activity.
174 Hytera submitted that the determination of whether the activity is of interest can happen only once and cannot be, as Block 212 suggests it can be, provisional. Put another way, under Hytera’s construction, the subscriber unit cannot decide that the transmission might be of interest and then carry out further acts to determine whether it actually is of interest.
175 It will be apparent that in Figure 2A, this is not what is happening except in the case of an emergency transmission. In that case, the determination that the transmission is an emergency transmission (because the E bit is set to 1) leads the subscriber unit to receive the audio. However, leaving aside the position of the activity bit itself, which fits into claim 1 in a different way, all of the other information in the activity update message leads to determinations which are at best provisional.
176 So, the matching of the hashed IDs at Block 212 requires two further determinations to be made before any audio is received: a determination using the D bit (data or voice) that the transmission is a voice communication (Block 226) and a further determination that there is a full ID match after decoding the full LC message (Block 214).
177 The information in the D bit in the activity update message also requires further determination. If the transmission is voice (Block 226), then the full LC message must be received and an ID match performed (Block 216). On the other hand, if the transmission is data (Block 226), then the subscriber unit must go through the process in Figure 2B which involves several steps including potentially an ID match at Box 234.
178 In any event, only in the case of the E bit does the invention in Figure 2A operate in accordance with claim 1 construed as Hytera would have it. Everything else in Figure 2A is outside claim 1 construed in that fashion.
179 The description then continues at p 8 line 26 to p 9 line 11 in these terms:
If the active transmission is data (Block 226), then the scanning SU remains on the channel to recover the data message (Block 228) and waits until the end of the data transmission to receive a data terminator (Block 230). In an alternative, the scanning SU remains on the channel to receive embedded qualifying information. Continuing, the data terminator is decoded to identify addressing identification (or an “ID”) (Block 232). If the ID is of interest to the scanning SU (Block 234), then the data message is further processed. Otherwise, the scanning SU tunes to the next channel in the preprogrammed scan list (Block 220). Continuing, the scanning SU determines whether confirmed delivery is requested (Block 236) for the data message. If confirmed delivery is requested, then the data message is processed until the entire data message is recovered (Block 238). In one embodiment, recovering an entire data message is performed by sending Selective Automatic Repeat Request (SARQ) messages to the BR. When the entire data message is recovered, the scanning SU tunes to the next channel in the preprogrammed scan list (Block 220). If confirmed delivery is not requested, then the scanning SU waits on the channel a predetermined amount of time for a possible redundant or subsequent transmission (Block 242). At the expiration of the predetermined amount of time, the scanning SU tunes to the next channel in the preprogrammed scan list (Block 220).
180 These relate to what occurs if the transmission is a data transmission.
181 The description then continues at p 9 lines 12 to 27:
If the active transmission is voice (Block 226), then the scanning SU remains on the channel to perform a full link control (LC) qualification of the active transmission by decoding an LC message which identifies whether the active transmission is addressed to an individual SU or a talkgroup, an emergency or non emergency, and the source and destination of the active transmission (Block 214). In an illustrative embodiment, the LC message is a 7-burst CACH message. Performing full LC qualification means that the scanning SU waits for a LC message on the timeslot of interest and decodes an ID field of the LC message to determine whether the active transmission is of interest to the scanning SU. In an illustrative embodiment of the wireless communications landscape 100, because LC messages are available once every 360 msec, having to wait to decode a full LC message is time consuming for the scanning SU. If the ID field of the LC message is an ID of interest to the scanning SU (Block 216), then the speaker is unmuted and audio is rendered to the user of the scanning SU (Block 218). If the ID field of the LC message is not of interest to the scanning SU (Block 216), then the scanning SU tunes to the next channel in the preprogrammed scan list (Block 220).
182 Now the full LC message at least includes the information in the activity update message. From this it also appears that it contains the full SUID or TGID. Consequently, it is apparent that the full LC is larger than the activity update message. This is confirmed by the fact that whereas the activity update message is transmitted as four bursts of 2.5 msec duration (at the end of each 30 msec burst), the full LC is transmitted in seven bursts (presumably of 56 bits). The statement that the full LC message is available every 360 msec suggests that it is available after 12 bursts (recalling that the bursts take 30 msec). The activity update message takes four bursts and the full LC message takes seven bursts. This suggests, but it is unclear, that the activity update message bursts and the full LC message bursts alternate at the end of the 30 msec block, i.e. one burst uses the 2.5 msec for the next burst of the activity update message and the following burst uses the 2.5 msec for the next burst of the full LC message. In any event, it is clear from what the description says in the next paragraph that the activity update message is received in full more often than the full LC message.
183 The description then continues at p 9 line 28 to p 10 line 3:
If the ID field 308, 310 of the activity update message 300 does not contain an id that is of interest to the scanning SU (Block 212), then the scanning SU moves to the next channel in the preprogrammed scan list. In such a case, the scanning SU does not have to wait for a LC message. Because the LC message only is sent once every 360 msec, not having to wait for a LC message improves the time that the scanning SU spends during the function of scanning. By not having to wait for a LC message, the scanning SU is able to quickly determine that the active transmission is not of interest and the scan function is improved.
184 So, the activity update message operates as a rapid negative criterion of exclusion and is faster than waiting for a full identification through the full LC message.
185 The description then continues at p 10 lines 4 to 12:
As is known in the art, the timing of events relating to color code, the activity update message 300, and the LC message may occur in any order. For example, the activity update message 300 may be received by the scanning SU before 1) the color code of the active transmission is known or 2) the full LC message is received. Also, a full LC message may be received before 1) the activity update message 300 is received by the scanning SU or 2) the color code of the active transmission is known. Further, as shown in FIG. 2, the color code of the active transmission may be known before 1) the activity update message 300 is received by the scanning SU or 2) the full LC message is received.
186 So, where the subscriber unit actually receives the full LC message before the activity update message, it can use the full LC message.
187 The description then continues at p 10 lines 13 to 26:
In any case, determining whether to remain on the channel and render audio to the user of the scanning SU is based upon whether the received information is of interest to the user. Specifically, a match of the color code and the full LC message stops the function of scanning and renders audio to the user of the scanning SU. A match of the color code and ID field 308, 310 of the activity update message 300 stops the function of scanning but requires a match of the full LC message before rendering audio to the user of the scanning SU.
In an illustrative embodiment, a match of the ID field 308, 310 indicates that the active transmission may be of interest to the scanning SU. In such a case, the scanning SU remains on the channel and performs Link Control (LC) qualification of the active transmission before committing itself to remaining on the channel and rendering audio to the subscriber unit user. Alternatively, if there is not a match of the ID field 308, 310 then the scanning SU continues to scan with the next personality in the scan list.
188 This passage highlights the difference between the full LC message and the activity update message. The matching of colour codes relates to whether the subscriber unit is associated with the base radio which has sent the transmission. A matching of the “ID field 308, 310” is a reference to a matching of the hashed ID codes in the activity message, that is, the last two rows of Figure 3. What appears from the last sentence reflects the fact that by compressing the SUID and TGID using a compression algorithm, a certain amount of information is lost in the process so that a match between the compressed 8 bit SUID or 8 bit TGID in the activity update message and the 24 bit SUID or 16 bit TGID which the subscriber unit is programmed to be interested in, does not entail with certainty that the SUID and TGID actually match. Only when the full LC message is received and decoded can a match be carried out using the full 24 bit SUID or 16 bit TGID. It is only then, according to this paragraph, that audio is rendered to the user.
189 Hytera submits that on its proper construction, the expression in claim 1 “determining whether the activity is of interest to the subscriber unit” entails a decision making process that is once and for all. So, once the subscriber unit has determined that the activity is of interest to it, that is the end of the process and nothing more remains to be done but to remain on the channel to receive the communication. But the use of the activity update message as described in this paragraph, and more generally in the illustrative embodiment, does not accord with such a construction. The determination that the activity is of interest because there is a match in the hashed IDs is inherently provisional in this paragraph and there remains the further steps of checking the full LC message before the subscriber unit commits to remaining on the channel to receive the activity. The primary judge said that this paragraph uses the expression “is of interest to the user” (at p 10 lines 14 to 15) in a way which suggests that “interest” may be a provisional state of affairs.
190 The description then continues at p 10 lines 27 to p 11 line 5:
By utilizing an activity update message 300 in the wireless communications landscape 100, the time spent while scanning is reduced. For example, in the embodiment described, a scanning SU is able to identify an active transmission of no interest on average in 152 msec. In a worst case, a scanning SU takes up to 335 msec to identify an active transmission of no interest. Without the use of an embodiment of the present invention, experimentation has shown that in an average TDMA system, a scanning SU is able to identify an active transmission is of no interest on average in 512 msec and in the worst case in 695 msec. Further, without the use of an embodiment of the present invention, experimentation has shown that in an average FDMA system, a scanning SU is able to identify an active transmission is of no interest on average in 360 msec and in the worst case in 540 msec.
191 This passage explains the point of the activity update message and confirms that its advantage lies in its ability to more rapidly conclude that a transmission is not of interest. The illustrative embodiment is able to determine that a transmission is not of interest on average in 152 msec whereas without the use of the activity update message this takes on average 512 msec. So, the illustrative embodiment shows that the use of the activity update message allows the subscriber unit to ascertain that a transmission is not of interest more than twice as fast.
192 The description then continues at p 11 lines 6 to 12:
Further yet, by utilizing an activity update message 300 in the wireless communications landscape 100, a SU that is a party to a call may quickly join the call if the SU is not currently a party to the call. Such an SU is called a late entry SU. For example, in the embodiment described, a late entry SU may join a call in a minimum of 120 msec. In a worst case, the late entry SU may join in about 300 msec. Without the use of an embodiment of the invention, experimentation has shown that a late entry SU takes about 360 msec and in the worst case about 720 msec to join a call.
193 This is a reference to the problem of late entry subscriber units.
194 Finally, the description concludes at p 11 lines 13 to 21 in these terms:
While the invention has been described in conjunction with specific embodiments thereof, additional advantages and modifications will readily occur to those skilled in the art. The invention, in its broader aspects, is therefore not limited to the specific details, representative apparatus, and illustrative examples shown and described. Various alterations, modifications and variations will be apparent to those skilled in the art in light of the foregoing description. Thus, it should be understood that the invention is not limited by the foregoing description, but embraces all such alterations, modifications and variations in accordance with the spirit and scope of the appended claims.
195 As to the claims, it is convenient here to set out claims 1 to 7 and 10, although only claims 1 to 6 and 10 are asserted:
1. A method for scanning a TDMA channel by a subscriber unit in a wireless communications landscape, wherein the subscriber unit is operationally connected to at least one base radio over a plurality of channels, the method including the steps of:
locking onto a channel of the plurality of channels by the subscriber unit wherein a subset of the plurality of channels is preprogrammed in a list in the subscriber unit;
transmitting from at least one base radio a control message to the subscriber unit wherein the control message has a first information which informs the subscriber unit of activity present on the channel of the plurality of channels;
receiving and decoding the control message for the first information by the subscriber unit; and
if the first information indicates that activity is present on the channel of the plurality of channels, then
determining whether the activity is of interest to the subscriber unit by comparing a second information in the control message with a third information preprogrammed in the subscriber unit and
if the activity is of interest to the subscriber unit, then remaining on the channel of the plurality of channels to receive the activity present on the channel.
2. The method of claim 1 further comprising the step of rendering audio of the activity present on the channel to a user of the subscriber unit if the activity is of interest.
3. The method of claim 1 or 2 further comprising the step of determining whether the activity is a voice transmission or a data transmission.
4. The method of claim 1, 2 or 3 further comprising the step of tuning to the next channel in the list that is preprogrammed in the subscriber unit.
5. The method of any one of the preceding claims wherein the activity is of interest if the control message indicates that the activity is targeted for the subscriber unit.
6. The method of claim 5 wherein the second information indicates a characteristic of the activity wherein the characteristic is chosen from the group consisting of identification, voice, data, group, individual, emergency, and non emergency.
7. The method of claim 6 further comprising the steps of:
if the activity is a voice transmission, then
recovering and decoding a link control message for identification information; and
determining the link control message is of interest to the subscriber unit
by comparing the identification information with a fourth information preprogrammed in the subscriber unit, and if the link control message is of interest then remaining on the channel to receive the activity present on the channel; and
if the activity is a data transmission, then
recovering a data message and a data terminator;
decoding the data terminator to identify address identification; and
determining the data message is of interest to the subscriber unit
by comparing the address identification with a fifth information preprogrammed in the subscriber unit, and if the data message is of interest then remaining on the channel to further process the data message.
…
10. In a TDMA system whereby the TDMA system includes a plurality of subscriber units and a plurality of base radios, a method for scanning, the method including the steps of:
locking onto a channel preprogrammed in a list of a subscriber unit whereby the channel carries activity on one timeslot of the TDMA system;
receiving an activity update message from a base radio of the plurality of base radios wherein the activity update message indicates in a first information the activity on the channel and indicates in a second information at least one characteristic of the activity on the channel;
determining whether the activity is of interest to the subscriber unit by comparing the at least one characteristic with preprogrammed third information in the subscriber unit; and
if the activity is of interest, then remaining on the channel to receive the activity; otherwise moving to the next channel in the list.
Infringement of the 355 patent – grounds of appeal 8, 9 and 10
Overview
196 Hytera has challenged various aspects of the primary judge’s findings on infringement which for the most part turn on a question of construction. We will address these grounds of appeal first before turning to the grounds of appeal concerning invalidity.
197 As the 355 patent defines a method and system involving the operation of DMR devices, Motorola’s case against Hytera was one of indirect or secondary infringement. Claims 1 to 6 and 10 were asserted by Motorola. It is sufficient to focus primarily on claim 1, as the primary judge did.
198 Motorola alleged that by supplying certain subscriber units and base stations in Australia, Hytera had infringed the 355 patent pursuant to s 117 of the Patents Act.
199 The primary judge held that Motorola had established infringement for certain Hytera devices, but that there was no infringement after 20 November 2019 because of steps taken by Hytera including reprogramming its subscriber units to remove the functionality that was subsequently held to give rise to infringement. The conclusion that Hytera infringed in the period prior to the reprogramming turned upon his Honour’s construction of the claims of the 355 patent. However, his Honour also held that the infringement continued for a period of several months after the reprogramming took effect, by reason of Hytera’s supply of reprogrammed base stations which could be used by customers who had previously purchased “unreprogrammed” subscriber units.
200 Hytera says that the primary judge’s conclusion of infringement was in error. In particular, it says that his Honour erred in his construction of the 355 patent, with the result that the finding of infringement in relation to Hytera’s unreprogrammed subscriber units was in error. It also says that his Honour erred in finding that Hytera’s supply of base stations, both before and after it had reprogrammed its subscriber units, gave rise to infringement.
The proper construction of claims 1 to 6 and 10
201 It is appropriate at this point to address how the primary judge dealt with construction. For the moment it is sufficient to focus on claim 1. Claims 2 to 6 are dependent on claim 1. Claim 7 is said by Motorola to be relevant to the construction of claim 1 although it was not sued on. Claim 7 is dependent on claim 6. Claim 10 is an independent claim.
202 Claim 1, identifying its integers with his Honour’s convenient numerical parentheses, is as follows:
1. A method for scanning a TDMA channel by a subscriber unit in a wireless communications landscape, wherein the subscriber unit is operationally connected to at least one base radio over a plurality of channels, the method including the steps of:
[1] locking onto a channel of the plurality of channels by the subscriber unit wherein a subset of the plurality of channels is preprogrammed in a list in the subscriber unit;
[2] transmitting from at least one base radio a control message to the subscriber unit wherein the control message has a first information which informs the subscriber unit of activity present on the channel of the plurality of channels;
[3] receiving and decoding the control message for the first information by the subscriber unit; and
[4] if the first information indicates that activity is present on the channel of the plurality of channels, then
[5] determining whether the activity is of interest to the subscriber unit by comparing a second information in the control message with a third information preprogrammed in the subscriber unit and
[6] if the activity is of interest to the subscriber unit, then remaining on the channel of the plurality of channels to receive the activity present on the channel.
203 The disagreement between the parties at trial involved the construction of integers 5 and 6 and in particular about the meaning of the phrases:
(a) “determining whether the activity is of interest to the subscriber unit”; and
(b) “remaining on the channel … to receive the activity”.
204 Motorola submitted at trial that the first expression, “determining whether the activity is of interest…”, was a reference to an assessment that the activity is of relevance or utility to the subscriber unit, in the sense of having some bearing on a subsequent communication step. It involved evaluating that the activity was of interest based on satisfaction of the test appearing in the fifth integer of claim 1, that is, “by comparing a second information in the control message with a third information preprogrammed in the subscriber unit”. It did not, however, exclude the possibility of further steps including a further confirmation.
205 Contrastingly, at trial Hytera said that both phrases were clear and prescriptive and require a determination to be made as to whether the activity is of interest to the subscriber unit and, if it is, that the subscriber unit must remain on the channel to receive the activity. On this view of claim 1, the method does not include the possibility that the determination of whether the activity is of interest to the subscriber unit may happen more than once. This involved a once and for all determination. The effect of Hytera’s construction was that once a determination was made, the process was concluded.
206 The primary judge considered that the debate between the parties was best illustrated by reference to one of the preferred embodiments referred to in the specification and the figure with which it is accompanied. The relevant figure is Figure 2A. Figure 2A is described at p 2 lines 7 to 8 of the detailed description as “a flow diagram of an example method for providing channel access for voice transmissions”. What was key were Blocks 212, 216 and 222 in Figure 2A, which is set out again for convenience:
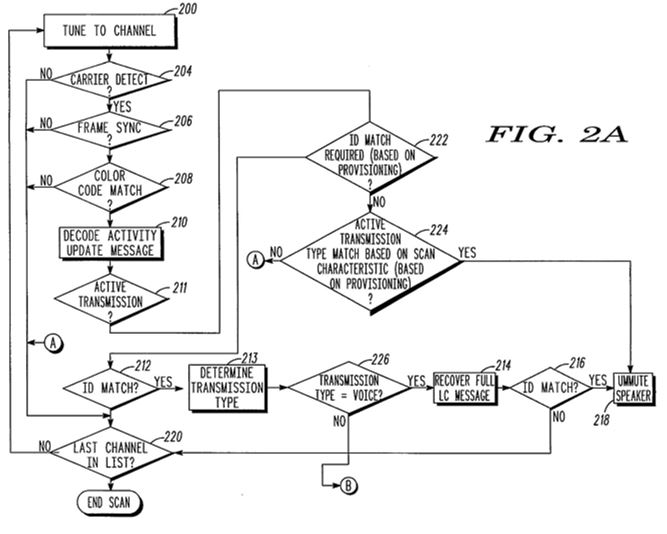
207 The “ID Match” appears at Blocks 212, 216 and 222 although in Block 222 the wording is slightly different. And in the order specified by the flow chart, the blocks are addressed in the order 222, 212 and 216. At trial the parties agreed that the reference to ID Match at 212 is a reference to that part of integer 5 of claim 1 which refers to “determining whether the activity is of interest to the subscriber unit”. They also agreed that the reference to ID Match at Block 216 is an example of a determination of whether the activity is of interest to the subscriber unit. But they disagreed on whether this second reference is within claim 1. So the question became whether “determines” means determined once and for all, as Hytera contended, or whether it does not exclude the possibility of further subsequent determination, as Motorola contended.
208 The primary judge said that if Motorola’s construction is correct, then both Block 212 and Block 216 may be a “determination” within the meaning of claim 1. On the other hand, if Hytera is right, then the fact that it is not in dispute that a “yes” answer to Block 212 is a determination within the meaning of claim 1 necessarily implies that Block 216 cannot be a determination within the meaning of claim 1.
209 At trial and on appeal, Motorola emphasised that claim 1 is to be interpreted in the context of the specification as a whole, including in light of the nature and purpose of the invention disclosed, and the common general knowledge in the field. The presence in the preferred embodiment illustrated in Figure 2A of two steps involving a determination that the activity was of interest to the subscriber unit was said to support its construction.
210 On the other hand, Hytera emphasised at trial and on appeal that it is the language of the claims which must be construed and that it is not legitimate to expand the boundary of the monopoly as fixed by the words of claim 1 by adding a gloss drawn from the preferred embodiment illustrated in Figure 2A or the description of that embodiment in the specification.
211 As the primary judge said, both statements of principle are correct. And as his Honour saw it, the main question therefore was whether what Motorola was putting forward was a legitimate contextual construction of the word “determine” or an impermissible attempt to gloss claim 1 by reference to one of the preferred embodiments.
212 At trial, Motorola submitted that Block 212, and the preferred embodiment it illustrated, showed that the determination could be non-conclusive. Block 212 is non-conclusive and the primary judge accepted Motorola’s submission that the preferred embodiment and Block 212 involve a determination of whether the activity is of interest to the subscriber unit which is not on a once and for all basis. His Honour also accepted that Block 216 involves another step where it is determined whether the activity is of interest to the subscriber unit. He also accepted Motorola’s submission that the word “determines” when used in the part of the description of the preferred embodiment corresponding to Block 212 must bear a meaning which encompasses the possibility of a subsequent determination at Block 216. The relevant part of the specification was at p 7 lines 24 to 27:
If an active transmission is present and if the scanning SU is programmed to check the active transmission (Block 222) for a transmission addressed to a SU of interest, then the scanning SU determines whether the active transmission is addressed to a SU of interest (Block 212).
213 Further, at trial Motorola submitted in relation to integer 6 of claim 1 that there was a distinction between “remaining on the channel”, which are the words used, and committing itself to remain on the channel. This distinction was also to be found in the preferred embodiment. The primary judge accepted this. The relevant portion of the description of the preferred embodiment was at p 10 lines 20 to 24:
In an illustrative embodiment, a match of the ID field 308, 310 indicates that the active transmission may be of interest to the scanning SU. In such a case, the scanning SU remains on the channel and performs Link Control (LC) qualification of the active transmission before committing itself to remaining on the channel and rendering audio to the subscriber unit user. Alternatively, if there is not a match of the ID field 308, 310 then the scanning SU continues to scan with the next personality in the scan list.
214 The reference to fields 308 and 310 takes one again to Figure 3. Figure 3 is described at p 2 lines 9 to 10 as “an example of a specific Common Announcement Channel [CACH] message called an Activity Update”.
215 Figure 3, which we will set out again for convenience, is as follows:
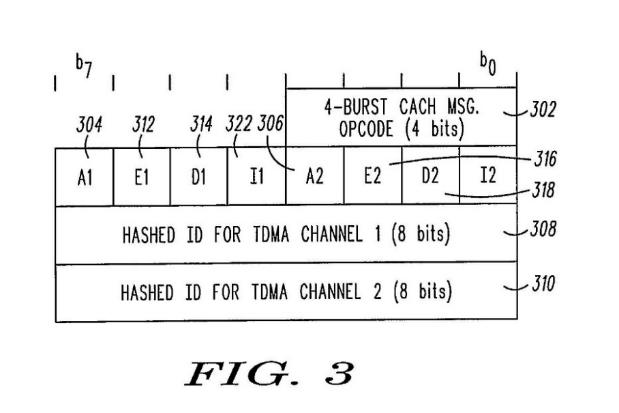
216 Further, the primary judge accepted that this is a discussion of what occurs in the preferred embodiment when there is a match of the “hashed ID”. His Honour accepted that this shows that the subscriber unit would remain on the channel until committing itself to remain on that channel.
217 The primary judge did not accept Hytera’s submission that the reference in p 10 line 21 to “may” alters this analysis. Hytera contended that what was happening at p 10 line 21 when the question was posed whether the activity “may be of interest” was not relevant to the construction of integer 6 of claim 1 because the expression there used was “is of interest”. What the preferred embodiment did when the activity “may be of interest” threw no light on that issue. On this view, the kind of commitment to remain on the channel required by integer 6 only occurred when the comparison with the full ID field in the full LC message took place (at p 10 lines 22 to 24). But the primary judge did not accept this submission. His Honour said that the passage at p 10 lines 20 to 24 clearly contemplates a situation where remaining on the channel has a contingent quality about it at one time and a definitive quality at another. His Honour also did not accept Hytera’s submission that its position is supported by the reference to “is of interest” at p 10 lines 14 to 15. The following sentence shows that two determinations take place before that occurs, that is, colour matching and the full LC message.
218 The primary judge therefore accepted that this portion of the description of the preferred embodiment observes a distinction between remaining on the channel and committing to remain on the channel. The question, however, is whether this distinction accords with the meaning of “remaining on the channel” in integer 6 of claim 1. In his Honour’s view, “remaining on the channel” was what happened after it was determined that the activity was of interest to the subscriber unit.
219 Motorola also placed reliance on claim 7. Motorola did not assert claim 7 in its infringement suit but rather said that claim 7 offered support for its construction of claim 1. Claim 7 was dependent on claim 1. Claim 7 refers to a process of recovering and decoding an LC message for identification information and determining whether the LC message is of interest to the subscriber unit by comparing the identification information with a fourth information preprogrammed in the subscriber unit. If there is such a match then the subscriber unit is to remain on the channel to receive the activity present on the channel. Motorola’s point at trial was that claim 7 necessarily assumed that the determination in claim 1 cannot be once and for all and that the “remaining on the channel” it contemplates need not be permanent either. Motorola submitted that if claim 1 had the meaning as Hytera contended, then claim 7 could never be enlivened. The primary judge agreed that if Hytera’s construction is correct, this would mean that claim 7 could never be enlivened.
220 But Hytera contended at trial that there were limits on the extent to which a dependent claim such as claim 7 can inform issues of the claim upon which it depends. It contended that if the plain meaning of a claim has the effect that one or more dependent claims are redundant then the consequence of redundancy would not drive the construction of the claim itself. Hytera cited Davies v Lazer Safe Pty Ltd [2019] FCAFC 65 (Davies) at [65] and Nichia Corporation v Arrow Electronics Australia Pty Ltd [2019] FCAFC 2 (Nichia) at [41]. The primary judge distinguished these cases.
221 The situation before the primary judge was that the construction of claim 1 for which Hytera contended has the effect that there can never be an invention embodying claim 7 because the criteria of operation for claim 7 is inimical to claim 1 on which it depends. This is not a case of redundancy, but rather inconsistency. His Honour accepted that the effect of the inconsistency is that claim 7 can never have any work to do. But to describe the problem in that way would be to obscure the textual significance of the fact that claim 7 takes as its point of departure an operation for claim 1 which is contrary to that contended for by Hytera.
222 Motorola also submitted at trial that its interpretation was more consistent with the “function of the patent” as a whole. By the phrase “function of the patent”, we understand Motorola to be referring to the function of the invention described and claimed in the patent. Motorola said that the patent was to be seen as primarily concerned with a method by which a subscriber unit could make faster decisions that activity on the channel was of no interest before moving on to the next channel. On this view of the invention, the critical determination was the determination to move on to the next channel or alternatively to remain on the current channel. Textual support for this understanding of the “function of the patent” (that is, the invention) was to be found in two passages in the description of the invention. These were at p 10 lines 1 to 3 and p 10 line 27 to p 11 line 2. These passages are as follows:
By not having to wait for a LC message, the scanning SU is able to quickly determine that the active transmission is not of interest and the scan function is improved.
…
By utilizing an activity update message 300 in the wireless communications landscape 100, the time spent while scanning is reduced. For example, in the embodiment described, a scanning SU is able to identify an active transmission of no interest on average in 152 msec. In a worst case, a scanning SU takes up to 335 msec to identify an active transmission of no interest. Without the use of an embodiment of the present invention, experimentation has shown that in an average TDMA system, a scanning SU is able to identify an active transmission is of no interest on average in 512 msec and in the worst case in 695 msec.
223 Hytera said that the advantage identified was an advantage obtained by the subscriber unit moving on to the next channel where a transmission was not of interest. Further and by extension, Hytera submitted that its construction took account of that claimed advantage because where a determination was made that the activity was not of interest, the subscriber unit would not remain on the channel.
224 The primary judge did not accept Hytera’s submissions. His Honour said that where multiple determinations are possible, the determination based on the information which is then available that the activity is not of interest causes the scan to move to the next channel. Hytera’s construction requires that to be done only once so that all of the information must be unpacked. In this way, Hytera’s construction detracts from, rather than supports, the advantage which claim 1 confers.
225 Hytera further submitted that many of the embodiments described in the specification were within claim 1 on Hytera’s construction and to the extent that they were not within claim 1, they were within claim 11. In response to this, Motorola submitted that a claim like claim 11 would ordinarily be understood as narrower in scope than all of the other claims and would not have the effect of broadening an invention or replacing an integer.
226 The primary judge considered that aspects of Motorola’s submissions were problematic. But in any event, his Honour did not accept Hytera’s argument. Claim 1 is to be construed in light of the specification as a whole, which includes the examples and drawings. The elements of claim 1 of present relevance, being the subscriber unit “determining” that an activity is of interest and “remaining on the channel”, are elements that can readily be seen to be depicted in Figure 2A once they are understood in the way that Motorola suggests. This is therefore a construction of claim 1 which makes sense in light of the specification including the drawings.
227 The primary judge accepted Motorola’s submission that its construction was more consistent with the “function of the patent” as a whole. Motorola’s construction is consistent with the statement under the heading “Background to the Invention” at p 1 lines 31 to 32 where the problem which the patent was intended to solve was identified: “Accordingly, there exists a need for scanning a TDMA channel which improves the amount of time that an SU spend scanning”. His Honour also accepted that Motorola’s construction of “determining” and “remaining” would achieve that purpose.
228 In summary, the primary judge considered that Motorola’s construction was preferable for two reasons. First, it was consistent with the “function of the patent” whilst Hytera’s construction is not. Second, claim 7 is drafted in a way which assumes that claim 1 does not operate as Hytera submits.
229 We now turn to Hytera’s submissions in support of its grounds of appeal.
Hytera’s submissions
230 Hytera says that the primary judge erred in construing claim 1 of the 355 patent and, as a result, in finding that Hytera had infringed by the supply of certain subscriber units before Hytera reprogrammed them, and by the supply of certain base stations which could be used with those subscriber units. Hytera says that his Honour failed to give effect to the plain words of the claim, construed in the light of the specification as a whole.
231 Hytera says that claim 1 of the 355 patent defines a “method for scanning a TDMA channel by a subscriber unit” including a series of steps. The method involves, in general terms, the subscriber unit receiving a control message from a base station; and using information in that control message to assess whether “activity”, that is, voice or data content, is present on the channel and “is of interest” to the subscriber unit. Relevantly, the steps defined by the claim include “determining whether the activity is of interest to the subscriber unit” and “if the activity is of interest … then remaining on the channel … to receive the activity”. Hytera says that these words are clear and prescriptive. They require the subscriber unit to use information in the control message to determine if activity on the channel is of interest. And importantly, if it is, the subscriber unit must remain on the channel to receive the activity, that is, the voice or data content being transmitted.
232 Hytera says that there was no dispute that its subscriber units did not operate in this way. In the operation of those devices, a match with the Hashed Address ID contained in the “Short LC message”, which was said by Motorola to equate to the “control message” of claim 1, did not involve any determination that the activity on the channel “is of interest”, and did not lead to the subscriber unit “remaining on the channel … to receive the activity”. Hytera says that in order for that to occur, if it did occur, a further process was required. That process involved the receipt of a “Full LC message” and a positive determination based on a comparison with the Full Address ID contained in that message.
233 Hytera says that, notwithstanding the plain words of the claim, the primary judge accepted Motorola’s contention that the claim did not exclude the possibility of further steps including a further confirmation to be carried out by the subscriber unit before determining whether it would receive the activity on the channel. Hytera says that the effect of this was to read the claim words “determining whether the activity is of interest” as though they referred to activity that “could be of interest”, or to encompass a determination that was “provisional” in nature. Hytera says that this failed to give effect to the claim words “remaining on the channel … to receive the activity”, by allowing a scenario where the subscriber unit might remain on the channel but never receive the activity.
234 The primary judge referred to the concept of “remaining on the channel” as having a “contingent quality” about it, but Hytera says that that disregards the defined purpose, “to receive the activity”, and was contrary to principle. Whilst a specification is to be read as a whole, the words of the claim define the scope of the monopoly. Further, a preferred embodiment cannot properly be used to add a gloss so as to limit the clear words of a claim. His Honour gave two reasons for adopting his construction. First, it was consistent with the “function of the patent”. Second, dependent claim 7 was drafted in a way which assumes that claim 1 does not operate as Hytera submits. But Hytera says that neither reason supports the construction his Honour adopted.
235 The primary judge considered that Motorola's construction was more consistent with the function of the 355 patent, which concerned the need to improve scanning time. But Hytera says that this conclusion was misplaced. The relevant passages of the 355 patent deal with the advantage obtained by a subscriber unit in moving on to the next channel where a transmission is not of interest: p 10 lines 1 to 3 and p 10 line 27 to p 11 line 2 (which we have already set out). Hytera says that its construction takes account of that asserted advantage, and does not detract from it. Where a determination is made that the activity is not of interest, the subscriber unit does not remain on the channel.
236 Further, on Hytera’s construction, various aspects of the embodiments described in the specification fall within claim 1. The primary judge rejected Motorola's contention that Figure 2A did not embody claim 1 as construed by Hytera. So, a subscriber unit could be programmed to scan for all transmissions in a given category, such as emergency or non-emergency transmissions as the “activity of interest”, and to remain on the channel to receive that activity being the transmissions in that category upon the relevant determination. The individual bits depicted in Figure 3 would operate as the “second information” of claim 1 in such cases: p 4 line 29 to p 5 line 11, p 7 lines 6 to 18, and Figure 3.
237 Hytera says that to the extent that some aspects of the embodiments described do not fall within claim 1 on its construction, this is a reflection of the different language used. So in one passage, the description refers to an indication that activity “may be of interest”, in which case a further operation is performed; claim 1, on the other hand, requires a determination that activity “is of interest”, in which case the subscriber unit remains on the channel to receive it: p 10 lines 20 and 21. Similarly, the description refers to a subscriber unit “dwell[ing]” on a channel rather than “remain[ing] on the channel to receive the activity”: p 6 lines 26 and 27. The contrast in language here is significant. To import features or requirements from the preferred embodiment is contrary to established principles of construction.
238 Finally, to the extent that some aspects of the embodiments described are not within claim 1 on Hytera’s construction, they are within claim 11. As such, on Hytera’s construction, the claims as a whole are commensurate with the description.
239 The primary judge considered that dependent claim 7 would be inconsistent with claim 1, and thus redundant, on Hytera’s construction. But Hytera says that this was misplaced. There are limits on the extent to which a dependent claim can properly inform the construction of an independent claim. Hytera says that if the plain meaning of a claim has the effect that one or more dependent claims are redundant, the consequence of redundancy, or even inconsistency, does not necessarily drive the construction of the claim itself. Hytera referred to Davies at [65] and Nichia at [41], which authorities had been discussed by the primary judge. Hytera says that his Honour was wrong to put these authorities aside on the basis that they did not involve the relevant kind of redundancy. It also referred to UbiPark Pty Ltd v TMA Capital Australia Pty Ltd (No 2) [2023] FCA 885; 177 IPR 254 at [137] to [139].
240 In any event, Hytera says that the primary judge was wrong to find that any redundancy or inconsistency arose from Hytera’s construction of claim 1. Motorola’s argument, as accepted by his Honour, was that “claim 7 necessarily assumes that the determination in claim 1 cannot be once and for all and that the ‘remaining on the channel’ it contemplates need not be permanent either” (PJ [209]). But Hytera says that this is incorrect. Claim 7 can be understood as providing for additional routes along-side that in claim 1 by which the subscriber unit might “remain on the channel … to receive the activity”. A subscriber unit programmed to implement each of those routes in appropriate cases would be within dependent claim 7.
241 Further, Hytera says that the claim does not contemplate the prospect that the determination may be merely provisional in character, or that following such a determination, the subscriber unit might remain on the channel but never in fact receive the activity.
242 Motorola attempts to deal with these issues through the analogy of a person waiting at the bus stop who, despite doing so, might never actually catch the bus. But Hytera says that this goes against the purpose of the invention as understood by the primary judge, being to provide an improvement in scanning time by allowing a subscriber unit to determine more quickly that an activity is not of interest and move on to the next channel. It also fails to take account of the requirement of the claim that the subscriber unit must determine whether the activity “is of interest”.
243 On Hytera’s approach, the words “determining once and for all to the exclusion of any other process” do not need to be read into the claim. The claim does not refer to any other process. It defines the process that must give rise to the relevant determination, involving comparison of the “second” and “third information” referred to in the claim. Further, the stated result of “remaining on the channel … to receive the activity” excludes any determination that is “provisional” in character.
244 On Hytera’s construction, the claims as a whole including claims 1 and 11 are commensurate with the embodiments in the specification, and thus the function of the 355 patent.
245 Further, Hytera says that there is no reason why the steps of claim 7 must be read as following the final step of claim 1. It says that claim 7 is properly understood as adding further intermediate steps, which lead up to, but do not follow, a determination that activity “is of interest”.
246 Hytera says that the primary judge was right not to give weight to Motorola’s overly literal parsing of the phrase “to receive”. The claim refers to the subscriber unit “remaining on the channel … to receive the activity”. This entails that it will both remain on the channel and receive the activity, not merely the former without the latter. It would be meaningless to state a “purpose” of receiving the activity if what was intended was that the subscriber might never in fact do so.
Consideration
247 We have set out claim 1 and its six integers earlier. The contested integers are integers 5 and 6 as we have indicated.
248 As Motorola correctly points out, there are two tests or checks contemplated or embraced in claim 1. The first test or check is the first information, which indicates whether activity is present on the channel. And as explained in the specification, if the first information does not indicate that activity is present on the channel, then the subscriber unit can move on to the next channel. Otherwise, it moves to the next step. The second test or check is the step of comparing a second information with a third information programmed in the subscriber unit. So, if the second information is an identity number, the subscriber unit can check whether the identity number matches the pre-programmed identity number being the third information.
249 By reference to an illustrative embodiment depicted in Figure 3, the specification provides examples of the first information and the second information in the claimed method. An example of the first information in the claimed method is activity bits denoted as A1 and A2 of Figure 3, because they indicate whether activity is present on the channel. If the bit is 0, that indicates that activity is not present and the device can move to the next channel. An example of the second information is hashed IDs, which are depicted in the bottom 2 rows of Figure 3 and which comprise a compressed form of the SUID and TGID. The subscriber unit can compare them with the SUID or TGID pre-programmed in the subscriber unit, that is, the third information, in order to determine whether the activity is of interest to the subscriber unit. If there is no match (that is, it is not of interest), the subscriber unit can quickly move on to the next channel.
250 Further, the compression algorithm can cause more than one subscriber unit identified by a 24 bit SUID to have the same 8 bit hashed ID. A similar position applies to the 16 bit TGID. Therefore, when using a hashed ID, although a positive match would cause the subscriber unit to stop scanning and to remain on the channel as a channel of interest to the subscriber unit, there may need to be a further step to check the full ID to confirm definitively that the activity is directed to the particular subscriber unit. The specification of the 355 patent explains, in an embodiment, that this can be done by the subscriber unit decoding the Full Link Control (Full LC) message, which is transmitted less frequently than the activity update message.
251 As to determining whether the activity is of interest to the subscriber unit, integer 5 involves evaluating whether the activity is of interest based on satisfaction of the test appearing in the preceding integer, that is, by comparing a second information in the control message with a third information preprogrammed in the subscriber unit as the primary judge found (PJ [186]). The determination in this integer, for example by an ID match, did not exclude the possibility of further confirmatory steps being taken. Contrastingly, Hytera contended that integer 5 required a once-and-for-all determination to be made, with no possibility of a subsequent step.
252 As to “remaining on the channel … to receive the activity”, the subsequent integer did not require the subscriber unit to permanently remain on the channel and render audio or the data message, that is, there was no requirement that the activity subsequently be received. Contrastingly, Hytera’s construction was that this integer operated as if the words “and receives the activity” were included.
253 We agree with the primary judge that Motorola’s construction is consistent with the function of the invention described and claimed in the 355 patent and the description in the embodiment and that dependent claim 7 was drafted in a way which assumed that claim 1 did not operate as Hytera submitted. Correspondingly, we reject Hytera’s contention that this involves reading down the plain meaning of claim 1 by reference to glosses drawn from the specification or by reference to the meaning of claim 7. Hytera’s contention assumes that integers 5 and 6 of claim 1 have some plain meaning that is inconsistent with the approach of the primary judge. But that is incorrect.
254 Further, Hytera’s approach involves adding the words “and receives the activity” to claim 1. But those words are not present. Likewise, the subscriber unit is “remaining on the channel” when it does not move on to the next channel and instead remains on the particular channel following the determination in integer 5, for example, an ID match. In such an example, once there is a match with the hashed ID, the subscriber unit is “remaining on the channel… to receive the activity”. In some cases, it will not ultimately receive the transmission because a further check will reveal that the transmission is not intended for the subscriber unit.
255 Likewise, “determining whether the activity is of interest” is a reflection of what the subscriber unit does. As Motorola points out, if the subscriber unit receives an ID match then, rather than passing on to the next channel, the subscriber unit determines that the activity on the channel is of interest by the means available to it at that time, and remains on the channel. The fact that the subscriber unit may undertake a subsequent process does not detract from this.
256 We also agree with Motorola that the primary judge’s interpretation is consistent with the nature of the invention, which is to speed up scan time, including by speeding up the time taken to pass on to the next channel if there is activity on the current channel that is not of interest. Not only is the ordinary meaning of the language of claim 1 consistent with the primary judge’s interpretation, but it is also consistent with the specification and the other claims. Contrastingly, Hytera’s construction is inconsistent with the patent specification considered as a whole.
257 The primary judge rightly concluded that the specification uses the expression “is of interest to the user” in a way which suggests that “interest” may be a provisional state of affairs. His Honour said, correctly in our view, at PJ [179]:
… As alluded to above, Hytera submits that on its proper construction, the expression in claim 1 ‘determining whether the activity is of interest to the subscriber unit’ entails a decision making process that is once and for all; or, to put it another way, that once the subscriber unit has determined that activity is of interest to it, that is the end of the process and nothing more remains to be done but to remain on the channel to receive the communication. It is not necessary to say anything about the correctness of this argument at this stage, but it will be noted that the use of the activity update message as described in this paragraph (and more generally in the illustrative embodiment) does not accord with such a construction. The determination that the activity is of interest because there is a match in the hashed IDs is inherently provisional in this paragraph and there remains the further steps of checking the full LC message before the subscriber unit commits to remaining on the channel to receive the activity. For present purposes, what should be taken away from this paragraph is that it uses the expression ‘is of interest to the user’ (at p 10 lines 14 to 15) in a way which suggests that ‘interest’ may be a provisional state of affairs.
258 Hytera’s construction is also inconsistent with claim 7 and does not merely render claim 7 redundant. Claim 7 includes each step of claim 1, with additional steps set out therein.
259 Hytera submits that on its construction of claim 1, the steps of claim 7 stand along-side the steps of claim 1 as providing for an alternate route by which the subscriber unit might determine that the link control message or data message is of interest and remaining on the channel to receive the activity. We reject this submission for the following reasons, which largely accord with what was submitted by Motorola.
260 First, claim 1 is directed to the determination of whether “the activity is of interest to the subscriber unit”, which determination is made by reference to a first information and second information of a control message, and a third information that is pre-programmed into the subscriber unit. The first information of claim 1 “informs the subscriber unit of activity present on the channel”. An example of the first information in the claimed method is activity bits because they indicate whether activity is present on the channel. Further, the “activity update message” of the illustrative embodiments includes an activity field, which indicates whether activity is present on the channel. Accordingly, the control message of claim 1 cannot be the Full LC message, given that such a message would not contain first information. Contrastingly, claim 7 in the case of a voice transmission for example is directed to a method by which the “link control message”, which is another term used to refer to the Full LC message, is decoded for identification information. Accordingly, we agree with Motorola and the primary judge that claims 1 and 7 do not operate along-side each other. Instead, claims 1 and 7 involve the interrogation of two different types of messages, with claim 1 involving a control message which contains the first information and second information, and claim 7 involving the link control message which contains identification information. This distinction is also made clear in the illustrative embodiment in Figure 2A, which depicts the decoding of the activity update message (being an embodiment of the control message in claim 1) at Block 210 and following, and the subsequent recovery of the Full LC message, that is, the link control message in claim 7, at Block 214 and following.
261 Second, claim 7 is drafted as further comprising the steps of recovering and decoding the link control message and comparing that with the identification information pre-programmed in the subscriber unit. So, the methods of claims 1 and 7 are not expressed as operating in parallel. Indeed, the language used in claim 7 indicates that it comprises further steps to the steps of claim 1 and so must follow the steps of claim 1. This is consistent with claim 1, which does not exclude the possibility of further confirmatory steps being taken.
262 Moreover, Hytera’s construction is inconsistent with the words of claim 7, which state that it is “[t]he method of claim 6 further comprising the steps of”. As Motorola points out, if the steps of claim 7 occur in parallel with the steps of claim 1, it would be inappropriate to use the term “further comprising the steps of”.
263 Further, claims 1 and 7 cannot operate in parallel on Hytera's construction. Claim 7 on Hytera's construction can only operate when there is a determination that there is no activity of interest, in circumstances where claim 1 already requires a determination that there is activity of interest. In our view there is insufficient support for Hytera’s construction in the language of the claims construed in the context of the specification.
264 In summary, we agree with the primary judge that Hytera’s proposed construction of claim 1 does not render claim 7 redundant. Rather, Hytera’s construction results in a scenario where claim 7 is inconsistent with the operation of claim 1.
265 The final matter to address is Motorola’s notice of contention. Motorola submitted that the primary judge’s acceptance of Motorola’s construction of integer 6 of claim 1 should be upheld on an additional basis, which was rejected by the primary judge. Motorola advanced a submission at trial concerning integer 6, but the primary judge rejected Motorola’s approach to construction that placed weight on the grammatical function of the infinitive “to receive”. His Honour said at [201]:
Thirdly, Motorola submitted (in relation to integer 6 of claim 1) that the expression ‘remaining on the channel … to receive the activity present on the channel’ was an example where the use of the infinitive ‘to receive’ connoted a purpose or function. It followed that so parsed, integer 6 of claim 1 did not have as one of its elements the actual receipt of the activity. Whilst I accept the grammatical parsing, on balance, I regard this consideration as of little weight as it appears to involve giving considerable significance to the use of the infinitive as the expression of a function or purpose. Whilst I would accept that such reasoning would be appropriate in the construction of a statute (see, e.g. Sunchen Pty Ltd v Federal Commissioner of Taxation [2010] FCAFC 138; 190 FCR 38 at 55 per Jessup J) it would appear to be the kind of ‘meticulous verbal analysis’ which the authorities counsel against in the construction of patents: Catnic Components Limited v Hill & Smith Limited [1982] RPC 183 at 242-243 per Diplock LJ.
266 Motorola says that its point was different to that attributed to it by the primary judge, in that it emphasised the ordinary meaning of the words “to receive” in integer 6 as connoting a purpose or function.
267 Whilst the primary judge indicated that he accepted the grammatical parsing, his Honour gave the argument little weight on the basis that it involved giving considerable significance to the use of the infinitive as the expression of a function or purpose and thereby involved “meticulous verbal analysis” ([201]). We consider there is no error in the primary judge’s reasoning. We therefore reject ground 1 of Motorola’s notice of contention.
268 For the foregoing reasons, ground of appeal 8 is rejected. It also follows that ground of appeal 9, by which Hytera sought to overturn the infringement findings which flowed from the primary judge’s acceptance of Motorola’s construction, must be rejected.
Infringement by supply of base stations – ground of appeal 10
Hytera’s submissions
269 Hytera says that there are additional reasons why the primary judge erred in finding that Hytera had infringed claims 1 to 6 and 10 of the 355 patent by the supply of certain base stations, both before, and for a period of several months after, the reprogramming of Hytera’s subscriber units. The basis of his Honour’s finding was that the base stations could be used with “unreprogrammed” subscriber units sold before 25 March 2019. Hytera says that his Honour’s approach involved a significant overreach, and a misapplication of the principles of indirect infringement.
270 Hytera says that as claim 1 defines a “method for scanning a TDMA channel by a subscriber unit”, the functionality defined by the claim is implemented in substance by the subscriber unit. It says that the scanning is undertaken in relation to a control message transmitted by a base station, but the steps of the method are performed by the subscriber unit. In these circumstances, Hytera says that the supply of a base station which simply transmits a control message does not provide an adequate foundation for a finding of indirect infringement on any of the bases accepted by the primary judge. It says that a base station cannot fairly be characterised as a product “the use of [which] would infringe” the 355 patent under s 117(1). Similarly, it says that the supply of a base station which simply transmits a control message does not give rise to authorisation or joint tortfeasance. Hytera says that the primary judge erred in putting aside these considerations.
271 Hytera says that it is also significant that in order to comply with the 2005 DMR Standard, Hytera’s base stations must transmit the control message which the primary judge concluded gave rise to infringement. Hytera says that its use of this control message is therefore covered by the EP licence between the parties, which provided for cross-licences of certain “standards essential” technology. Hytera says that the effect of the EP licence is to ensure that each party and its affiliates can supply devices using the functionality that is required to comply with the 2005 DMR Standard, without risk of infringing the other party’s patents. Hytera says that it was and still is obliged to program its base stations so that they transmit the control message in order to comply with the 2005 DMR Standard. Hytera says that if that is the basis upon which Hytera’s supply of base stations would otherwise infringe the 355 patent, then it had a licence to do so from Motorola.
Consideration
272 The primary judge found that Hytera was liable for indirect infringement in respect of its reprogrammed base stations (that is, base radios) on the basis that those base stations could be used with unreprogrammed subscriber units, up until Hytera took certain steps in November 2019 to reduce the risk of such use. As we have said, Hytera challenges this conclusion on the basis that the functionality defined by the claim is implemented in substance by the subscriber unit. But this is a distorted perspective.
273 Claim 1 claims a “method for scanning a TDMA channel by a subscriber unit in a wireless communication landscape, wherein the subscriber unit is operationally connected to at least one base radio”. Further, an essential integer of claim 1 is “transmitting from at least one base radio a control message to the subscriber unit wherein the control message has a first information which informs the subscriber unit of activity present on the channel of the plurality of channels”. Clearly, infringement involves the use of a combination of base radios and subscriber units. The reprogrammed base radios continued to transmit the short LC, being a control message including the first information (activity indicator) and the second information (hashed ID).
274 The primary judge found that a significant portion of end users would have had unreprogrammed subscriber units, and Hytera countenanced end users using unreprogrammed subscriber units with the reprogrammed base stations. By supplying reprogrammed base stations which transmitted the short LC message, Hytera did more than facilitate the infringement of the patent by end users when reprogrammed base stations were used with unreprogrammed subscriber units. As his Honour correctly found on the evidence, Hytera encouraged users to use base stations with subscriber units in circumstances where a significant portion of the end users would be deploying unreprogrammed subscriber units. In our view, on the basis of his findings, the primary judge was correct to find secondary infringement.
275 Hytera was not required by the 2005 DMR Standard to act in a way which resulted in infringement of the 355 patent. So, Hytera’s conduct prior to November 2019 did not fall within the scope of the EP licence.
276 For the foregoing reasons, ground of appeal 10 is rejected.
277 We now turn to Hytera’s grounds of appeal concerning invalidity.
Inventive step – ground of appeal 11
Hytera’s submissions
278 By ground 11, Hytera contends that the primary judge erred in finding that the invention claimed in claims 1 to 6 and 10 of the 355 patent involved an inventive step in light of the common general knowledge before the priority date, alternatively, in light of the common general knowledge with the draft DMR protocol that was accepted as a s 7(3) document.
279 As we have said, the claims of the 355 patent require a control message which has a first information which informs the subscriber unit of activity present on a timeslot, and determines whether the activity is of interest to the subscriber unit by comparing a second information in the control message with a third information preprogramed in the subscriber unit.
280 Hytera has drawn our attention to the following findings of the primary judge that are relevant to the question of inventive step. First, his Honour accepted that the 355 patent makes no stipulations about control message size, the size of synchronisation patterns or the extent of forward error correction, and that the claims were in no way limited by such features. Second, his Honour accepted that each of the integers of the claims were part of the common general knowledge, and that it was obvious as part of a scanning method to use a first information to indicate the presence of activity, and it was obvious to use a second information of the kind which appeared in the full LC message. Third, his Honour accepted that the draft DMR protocol disclosed the first information. Further, Professor Rangan, a professor of electrical and computer engineering called by Motorola, gave evidence that he would have considered using a first information as part of a scanning method to indicate the presence of activity. Fourth, his Honour accepted that Mr Kuhrt, an electronics engineer called by Hytera, proposed a methodology that was workable, was within the scope of the claims, and would have provided an improvement in scanning time.
281 The primary judge nevertheless held that the claims were inventive for the following reasons.
282 First, his Honour reasoned that whilst it was obvious to use the first and second information, a person of ordinary skill would not have done so because it would have led to a reduction in synchronisation patterns and forward error correction, which was inconsistent with the draft DMR protocol and hence with the direction in which the industry was heading.
283 Second, his Honour thought that Mr Kuhrt was asked the wrong question because the question posed to him required an improvement in scan time without this being done in the context of the design of an overall system. Moreover, his Honour thought that in the case of Mr Kuhrt’s revised methodology, this was the result of an implausible technical task combined with the views of one of the other expert witnesses in this case.
284 Third, the primary judge was not satisfied that Mr Kuhrt’s methodology was not to some extent affected by hindsight.
285 Hytera says that none of these matters provided a proper basis for concluding that the claims of the 355 patent were inventive.
286 As to the first matter, Hytera said that the primary judge erred in finding that the reduction in synchronisation patterns and forward error correction would have led the skilled addressee away from the invention in circumstances where the claims made no stipulations about control message size, the size of synchronisation patterns or the extent of forward error correction. Hytera says that those limitations did not form part of the invention, and could not be taken into account on the question of inventive step. And Hytera says that it is only within the features claimed that an inventive step might lie.
287 Further, Hytera says that the development of the 2005 DMR Standard and its publication shortly after the priority date confirms that the solution was obvious. In April 2005, less than a year after the priority date, ETSI released the 2005 DMR Standard. The 2005 DMR Standard included the Activity Update Short LC message, being a scan message, which included the two types of information defined in claim 1 of the 355 patent. Hytera says that in contrast to the primary judge’s findings that Mr Kuhrt’s proposed use of a scan message was inconsistent with the draft DMR protocol and hence with the direction in which the industry was heading, the industry was heading in that direction.
288 As to the second matter, Hytera says that the question posed to Mr Kuhrt was appropriate. The question was directed to the development of a conventional two-way radio system that improved the amount of time a radio spends scanning channels. Hytera says that the primary judge had accepted that a well-known problem with both automatic scanning and automatic voting in early analogue two-way radio systems was the length of time that it took for a terminal to complete the process. Hytera says that having established that the problem addressed was itself common general knowledge, such knowledge or information could be attributed to the skilled addressee for the purpose of assessing obviousness. Hytera says that the mere fact that other aspects of conventional two-way radios might also have required further development is irrelevant. The question was directed to the development of a conventional two-way system and was not in the abstract.
289 Further, Hytera says that Mr Kuhrt’s revised methodology was not, as the primary judge said, the result of an “implausible technical task combined with the views of one of the other expert witnesses in this case” (PJ [323]). Rather, it reflected an alternative methodology that Mr Kuhrt confirmed he would have taken in response to the problem. In that regard, Hytera referred to what Nicholas J said in Mylan Health Pty Ltd (formerly BGP Products Pty Ltd) v Sun Pharma ANZ Pty Ltd (formerly Ranbaxy Australia Pty Ltd) [2019] FCA 28 (Mylan Health); 138 IPR 402 at [193]:
… Merely because one pathway to an invention is shown to be obvious, does not mean that another such pathway might not also be obvious. Two or more pathways may be obvious, even though some of them might be more obvious than others.
290 In any event, Hytera says that Mr Kuhrt’s original solution also met the requirements of the relevant claims.
291 As to the third matter, Hytera says that the primary judge erred in reasoning that Mr Kuhrt’s methodology was affected by hindsight. His Honour accepted Mr Kuhrt’s evidence that he had only answered the question he was asked with the knowledge he had at the priority date. Hytera says that the fact that Mr Kuhrt had been exposed to the 2005 DMR Standard is irrelevant in circumstances where his Honour did not doubt Mr Kuhrt’s evidence that he had only used the knowledge he had available as at the priority date. Further, it is said that this was only one matter for the primary judge to take into account in assessing the evidence of Mr Kuhrt and the evidence generally.
292 Hytera says that the evidence as a whole including Professor Rangan’s evidence supported a finding that the claims of the 355 patent lacked an inventive step. Hytera says that his Honour failed to apply the principle that a claim is bad if it includes subject matter that is obvious, in circumstances where his Honour found that both Professor Rangan’s and Mr Kuhrt’s proposed solutions were within the scope of the claim on his Honour’s construction.
293 Before turning to an analysis of Hytera’s arguments, it is worth recalling aspects of the primary judge’s analysis.
The primary judge’s analysis
294 Hytera’s case at trial on obviousness was that the invention disclosed in the claims to the 355 patent was obvious in light of the common general knowledge. Alternatively, Hytera said that the invention disclosed by the claims was obvious in light of the common general knowledge, together with two other documents being the Telecommunications Industry Association’s “Project 25: FDMA – Common Air Interface” Standard (P25 standards), and the draft DMR protocol. As it was accepted at trial that these two documents were s 7(3) documents, the primary judge did not need to determine whether they also formed part of the common general knowledge.
295 Hytera’s case on obviousness had two main limbs.
296 In the first limb, and as the primary judge found, it was part of the common general knowledge that in TDMA systems, control information was sent to identify whether a physical channel was presently supporting a call or transmission on each timeslot. Hytera characterised this kind of control information as the first information referred to in claim 1. Hytera submitted that it was common general knowledge at the priority date that scanning messages could include identification information. Hytera submitted that this kind of information was the second and third information referred to in claim 1. Consequently, the invention disclosed in claim 1 was an obvious combination of two elements which already existed in the common general knowledge. The first information was just an example of the use of information to identify activity on a channel. The second information was the kind of information found in LC messages such as those used in the P25 standard. To make good this point, Hytera relied on the evidence of Mr Kuhrt.
297 In the second limb, Hytera argued at trial that the LC word disclosed in the draft DMR protocol had all of the integers in claim 1 apart from the first information. However, given that it was common general knowledge that TDMA systems used control information which identified whether a physical channel was presently supporting a call or transmission on a timeslot, it followed that the first information in claim 1 was part of the common general knowledge. Consequently, the invention disclosed in claim 1 was an obvious combination of these two matters such that the 355 patent lacked an inventive step. To make good this point, Hytera relied on the evidence of Professor Rangan.
298 At trial, Motorola denied that the combination of the first information with the second information in claim 1 was obvious and therefore not inventive and said that Mr Kuhrt’s evidence that it was obvious ought not to be accepted. Further, Motorola denied that the combination of the LC word in the draft DMR protocol with the first information, which was common general knowledge, meant that the invention was obvious. It said that Professor Rangan’s evidence did not establish to the contrary.
299 Mr Kuhrt had been asked to identify what scanning method he would have proposed if asked to develop a conventional digital two-way radio system that improved the amount of time a radio spent scanning channels before July 2004. In his first affidavit, Mr Kuhrt identified such a scanning method. In his second affidavit, he gave further evidence that his method fell within claims 1 to 6 and 10 of the 355 patent. He also gave evidence that no ingenuity on his part had been required in formulating his method. Mr Kuhrt’s method was subsequently criticised by Professor Rangan. Mr Kuhrt then clarified and revised his method to address each of Professor Rangan’s concerns. This revised method, he claimed, also fell within the claims of the 355 patent and similarly involved no ingenuity.
300 Motorola proposed its own formulation of what the inventive step of the invention was.
301 In that context the primary judge made reference to a passage from Lockwood Security Products Pty Ltd v Doric Products Pty Ltd (No 2) (2007) 235 CLR 173 (Lockwood Security Products (No 2)) (at [111], footnotes omitted) that:
… Practical and technical issues can affect the means by which a concept may be implemented in respect of an already known vendible product, and scepticism can inhibit recognition of the utility of applying a concept or idea to a known set of integers. These are matters within the knowledge of relevant witnesses. …
302 At trial, Motorola emphasised this negative aspect of the common general knowledge as having particular aptness in a field such as wireless communications systems because the standards environment imposed practical and technical constraints on the developments in the relevant technology.
303 As at the priority date, the only TDMA system in existence was the system embodied by TETRA. ETSI was considering introducing a TDMA standard and did so the following year in the form of the 2005 DMR Standard. As at the priority date, it did not exist, although it was in preparation. A draft of the standard, the draft DMR protocol, was available to those in the industry. So, as at the priority date, there was no standardised TDMA system although it was apparent that one was soon to be forthcoming.
304 Accepting that in a field such as wireless technology the standards environment can impose practical and technical constraints on development, the primary judge said that such restrictions are those which can be discerned from the 1998 TETRA standard and the draft DMR protocol. Mr Kuhrt’s initial proposed method of scanning was not compatible with either of these. When Professor Rangan pointed this out, particularly in relation to the draft DMR protocol, Mr Kuhrt revised aspects of his method which to an extent, although not completely, would have brought it within the draft DMR protocol.
305 The primary judge accepted that the question of obviousness is not to be addressed by asking whether each integer or step is obvious. The question is rather whether the combination of integers as a whole is obvious in the requisite sense. His Honour found that Mr Kuhrt was aware of the 2005 DMR Standard which was published in April 2005. That standard included within it a scan message which used an activity indicator bit and ID information. Although Mr Kuhrt was asked to formulate his method before being shown the 355 patent, his Honour said that it must be borne in mind that Mr Kuhrt already knew that the 2005 DMR Standard used an activity indicator bit and identification information. In assessing Mr Kuhrt’s proposed revised method, the primary judge said that it was to be borne in mind that in a sense Mr Kuhrt had already seen the solution in the 355 patent because it was the solution in the 2005 DMR Standard. Whilst his Honour did not doubt that Mr Kuhrt genuinely believed that he put himself in the position he would have been in as at July 2004, that is, that he knew nothing except for pre-existing standards, such as the P25 standard, the 1998 TETRA standard and the draft DMR protocol, it was doubted by his Honour whether it was reasonably possible to put out of one’s mind the existence of the 2005 DMR Standard.
The common general knowledge
306 It is convenient at this point to highlight some findings of the primary judge concerning common general knowledge as at the priority date.
307 As at July 2004, the standardised two-way radio systems that were known to persons working in the field of two-way radios in Australia included the TETRA, P25 and MPT1327 systems. TETRA implemented TDMA as the multiple access method. The 2005 DMR Standard, which became a standardised TDMA two-way radio system, was known to be in its draft stage.
308 Two-way radio systems utilise control messaging for scanning purposes. The use of control messages allows scanning mobile stations to determine information about the transmission taking place on a channel. Analogue two-way radios implement frequency tones as a form of control message for scanning purposes. Analogue mobile stations often included in their memory a list of frequency tones that were associated with, for example, a talkgroup. When the frequency tone is detected during scanning, the station would stay on that relevant channel emitting that tone.
309 Digital two-way radio systems implement control messages in the form of embedded signalling within a data stream for scanning purposes. These messages may be contained within the transmission itself (conventional systems) or separately transmitted on a control channel (trunked systems). In digital systems, control messages are used to provide information about transmissions on a traffic channel.
310 MPT1327 two-way radio systems utilise digital GTCM as a form of control messaging for scanning purposes. The GTCM is transmitted by a repeater on the control channel to broadcast control information to connected terminals about transmissions on traffic channels. Similarly, TETRA two-way radio systems also utilise digital control messages that are transmitted on a dedicated control channel to broadcast information about transmissions on traffic channels. However, unlike MPT1327, because TETRA implements TDMA, a single repeater can be used for both control slots and multiple talk slots. APCO P25 two-way radio transmissions include LC messaging that forms part of a digital voice transmission to provide signalling information to scanning mobile stations in a conventional (non-trunked) system.
311 The control messages used for scanning purposes in MPT1327, TETRA and APCO P25 systems included addressing information such as TGID and/or SUID information. The inclusion of addressing information allows for a scanning mobile station to determine if it is an intended recipient of an active transmission by comparing the addressing information in the control message with addressing information stored in its memory. Control messages used in FDMA two-way radio systems do not require signalling information that indicate timeslot activity since timeslots are not used in FDMA systems.
312 Hytera submitted before the primary judge that TDMA systems require control information indicating timeslot activity because one frequency can carry several concurrent transmissions on different timeslots. It submitted that it was within the common general knowledge that control information was generally sent in control messages which could be split over multiple bursts to reduce the amount of overhead used in a single burst, that is, in a 30 msec burst, the more of the burst that is devoted to the transmission of control information, the less of it that is available for the delivery of the substantive payload.
313 At trial, Hytera relied on three items of evidence to support its position which the primary judge discussed. We do not need to set out this discussion. The three items related to the written evidence of Professor Rangan and some evidence given under cross-examination of him. The primary judge also considered some evidence given by Mr Kuhrt under cross-examination.
314 As the primary judge recognised, Hytera sought to make good its case on this point based on the evidence of Motorola’s expert, Professor Rangan, whilst Motorola sought to make good its case based on the evidence of Hytera’s expert, Mr Kuhrt.
315 Professor Rangan said that the prior art did indicate the use of information to indicate whether activity was present on a timeslot, but Mr Kuhrt thought that nothing in the prior art had used a single bit to indicate timeslot activity. It was not clear to the primary judge that Mr Kuhrt was speaking of the use of control information to indicate activity on a timeslot as part of a scanning method. Since the draft DMR protocol did include the use of control information in which a bit is used outside a scanning method to indicate timeslot activity, his Honour was inclined to understand Mr Kuhrt’s answer as a statement that the prior art did not indicate a method of scanning in which an activity bit was used as part of a scanning methodology. So, his Honour therefore found that there was no prior art scanning method which included the use of an activity indicating first information as part of a control message.
316 The primary judge found that the prior art did include the use of information in a control message to indicate whether there was activity on a timeslot. In the draft DMR protocol, this took the form of an activity bit. However, this use of activity indicating first information did not form part of a scanning method.
317 His Honour accepted that although the P25 standard was s 7(3) information, its significance would appear only to be that it involved the use of an LC message.
318 In terms of the draft DMR protocol, his Honour made the following observations.
319 The draft DMR protocol was discussed during a working group meeting at ETSI during the development of the 2005 DMR Standard. The document was not confidential and was thereafter shared and discussed in the industry. Both Mr Kuhrt and Professor Rangan thought that the draft DMR protocol was a prior work which would have been located and read by a skilled addressee in order to understand what had already been developed in the field of two-way radios. Because it was a draft, the primary judge accepted that it could not be regarded as part of the common general knowledge, but it was s 7(3) information.
320 The relevance of the draft DMR protocol arose from section 10 in these terms:
10 LC Words
Two example LC words are shown in Figure 10-1. Actual LC words will vary with circumstance and application.
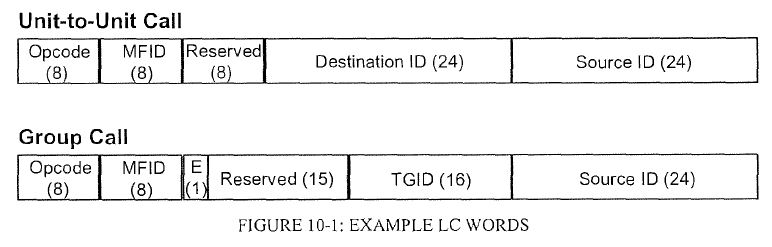
MFID (Manufacturers ID) – This is asserted when non-standard features are included in the voice message by the manufacturer
E – Emergency indicator.
Source ID – This identifies the transmitting subscriber unit
Destination ID – This identifies the receiving subscriber unit in cases where the destination is a single subscriber.
TG1D (Talkgroup ID) – This identifies the talk-group for the message in cases where the transmission is addressed to a group.
321 The example LC words are both 72 bits in length. Professor Rangan thought that a person of ordinary skill would have considered using the LC word discussed here for scanning purposes. However, he did not think that it met the requirements of claim 1 since it did not have a “first information”, that is to say, it did not include an activity indicator. Professor Rangan was cross-examined about this and he accepted that the LC word in the draft DMR protocol had all of the features of claim 1 apart from the first information.
322 At this point we should say something about Mr Kuhrt’s evidence before his Honour. His Honour made the following observations.
Mr Kuhrt’s initial method
323 Mr Kuhrt explained in his first affidavit that he had been asked by Hytera’s instructing solicitors to explain what, if any, scanning method he would have proposed if, at 26 July 2004, he had been asked to develop a conventional two-way radio system that improved the amount of time a radio spends scanning channels. At the time of his first affidavit, Mr Kuhrt had not been provided with the 355 patent.
324 In Mr Kuhrt’s initial method, a repeater would regularly transmit a message (or burst) on the downlink frequency which would be received by the mobile station. The burst would contain a synchronisation pattern that enabled the mobile station to synchronise to the transmission. The synchronisation pattern would be present in the middle or at the beginning of each timeslot (or data frame) that was transmitted from the repeater to the mobile station.
325 Mr Kuhrt would then carve out a portion of the payload in the latter half of the same burst and insert a scan message. The scan message would consist of the following. First, information that distinguished between an idle frequency and an active frequency such as a data bit which indicated if the frequency was currently being used for a transmission or was idle. Second, identification information such as data bits that indicated the transmission source identification details and/or the talkgroup identification details. Third, information that provided encryption information if required. Fourth, given a TDMA system, the design would also include information that indicates which timeslots on the frequency were active.
326 Mr Kuhrt thought that the scan message would speed up the automatic scanning process because it would provide the mobile station with all of the necessary information in a single burst. By doing so, the mobile station would not need to decode other bursts in the data stream to determine if it should remain on the frequency. The addition of a complete scan message, as part of every frame, would remove the need for mobile stations to wait on a frequency to receive additional bursts. The method would therefore be faster than a system which required the decoding of multiple messages in order to determine whether to remain on the frequency.
327 Mr Kuhrt would have located the scan message after the synchronisation pattern. Doing so would have permitted for both synchronisation and interrogation of the transmission to determine if it was valid within the same timeslot. As a result, after a mobile station received the synchronisation message, it would then be able almost immediately to locate and process the scan message. This would improve the amount of time that it took to scan frequencies automatically because it would avoid a scenario in which synchronisation occurred in one burst and where the mobile station would then have to wait for another burst to receive the scan message. Mr Kuhrt illustrated his method this way.
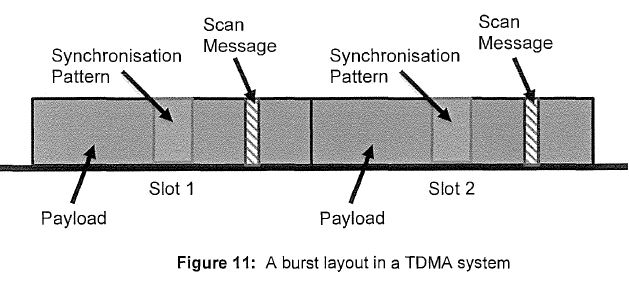
328 Mr Kuhrt thought this design was a simple solution to improve the speed and efficiency of automatic scanning. At the priority date, he would have expected that both he, and other engineers working in the field of two-way radios, could easily have implemented the method using routine software coding as only minimal software changes would be required.
329 In his second affidavit, Mr Kuhrt said that his design had all of the features of claims 1 to 6 and 10 of the 355 patent. He explained that he did not think that claims 1 to 6 and 10 of the 355 patent involved any ingenuity. In his view, it was well-known and accepted in the field as at 26 July 2004 that control messages were used in automated scanning to enable mobile stations to make determinations about whether channels contained active transmissions of interest to the terminal. He instanced the MPT1327 and APCO P25 systems as examples where this was the case. He also said that it was well-known and accepted that control messages could be used to inform a terminal whether there was activity on the channel.
330 Professor Rangan had four substantial criticisms of Mr Kuhrt’s initial method. His Honour made detailed findings concerning these criticisms. We do not need to set them out. Mr Kuhrt responded to these criticisms as follows.
331 First, Mr Khurt said that in his method he had not provided any details about the size of the payload or control messages. Since the draft DMR protocol was just a draft at the relevant point in time, the primary judge considered that Mr Kuhrt could not be criticised for not including such details. Indeed at the relevant point, there was, as yet, no standard. But his Honour did say that since it was known that the 2005 DMR Standard was in the pipeline, there may have been a certain degree of unreality in formulating a scan method which would have been incompatible with the draft.
332 Second, Mr Kuhrt noted that Professor Rangan had assumed that his control message was the same in length as the full LC message in the draft DMR protocol, that is, 128 bits, but Mr Kuhrt had not initially specified what was in his control message other than in general terms. But he explained in his third affidavit that his scan message would use 20 bits. It was as follows:
333 This message included a single bit to identify timeslot activity (TSA), a single bit to identify if the next timeslot was active (NSA), a single bit that identified whether the payload was encrypted (ENC), 9 bits that are used to provide address information (ADR), and 8 bits of error correction (CRC). The TSA and NSA bits provided information which distinguished between idle and active frequencies.
334 In relation to the 9 bits allocated to identification information, the draft DMR protocol provided 24 bits for the destination ID and 24 bits for the source ID for a total of 48 bits (for a unit to unit call), and 16 bits for TGID information where a group call was involved. Mr Kuhrt’s control message was therefore smaller than what at the relevant time was to be found in the draft DMR protocol. However, as Mr Kuhrt explained, 9 bits still provided for 512 unique identifiers or combination of bits (29=512). From this 512, he deducted one to be reserved for a broadcast function. Splitting the 511 remaining identifiers up, Mr Kuhrt reasoned that, for example, this could be configured for 31 talkgroups and 480 individual terminals (31+480=511). Mr Kuhrt noted that as at 26 July 2004, for a small to medium sized fleet with which he was familiar, the largest number of talkgroups was about 15 and the largest number of subscriber units was around 150. The primary judge inferred from this evidence that a 9 bit ID field may not have been sufficient for a large fleet. However, that it could not be used in a large fleet did not deny that it could be used in a small or medium sized fleet. According to his Honour, the existence of this possibility was relevant to assessing Motorola’s criticism that Mr Kuhrt’s solution was not practical.
335 Third, given Mr Kuhrt’s revised 20 bit scanning message, he did not think that deducting 20 bits from the payload in the draft DMR protocol was unacceptable. Mr Kuhrt noted that the control information for the draft DMR protocol was 72 bits. Using his 20 bit scanning message, this left 52 bits available for the remainder of the control information without in any way impinging on the payload. However, the draft DMR protocol also provided for there to be a synchronisation pattern of 48 bits within the control information. Mr Kuhrt now suggested that it was not necessary to use a synchronisation pattern of that size and that a 28 bit synchronisation pattern would suffice. His control message therefore consisted of 20 bits of scanning information and a 28 bit synchronisation pattern for a total of 48 bits. Even under the draft DMR protocol, this left 24 bits left over to be used for other purposes.
Conclusions on Mr Kuhrt’s revised methodology
336 The primary judge concluded that Mr Kuhrt’s revised methodology would have provided an improvement in scanning time which could have been used as a system suitable for small or medium size fleets. But it would not have been suitable for large fleets. It is evident that the system would have included less forward error correction and smaller synchronisation patterns. Although Mr Kuhrt’s initial method would have compromised call quality by reducing the payload, his revised methodology did not suffer from this vice.
337 The primary judge was unable to assess the impact of the decreased forward error correction and synchronisation patterns on the utility of Mr Kuhrt’s method. It was evident that Professor Rangan looked askance at this approach. But his Honour was unable to find that Mr Kuhrt’s revised method was unworkable for these reasons. There was no explicit evidence about the practical effect that these economies would have had on the operability of any such system.
338 The primary judge accepted that Mr Kuhrt’s revised methodology fell within the claims of the 355 patent and that the patent made no stipulations about control message size, the size of synchronisation patterns, or the extent of forward error correction. But having regard to the direction in which the draft DMR protocol was heading, Mr Kuhrt’s revised methodology struck his Honour as being a very unlikely solution as at July 2004. To solve the relatively lesser problem of scan time by coming up with a methodology with diminished forward error correction and reduced synchronisation patterns, which was radically inconsistent with the direction in which the industry appeared to be heading, his Honour thought was possible, but it was most unlikely that anyone would have actually embarked on the search for such a method.
339 Mr Kuhrt accepted that if he had been developing a new device at the priority date, he would have obtained the draft DMR protocol because it would have been instructive to him as to what was likely to become standardised in the future.
340 In his Honour’s view, the problem of scan time was not a major issue and not one which the skilled addressee would have regarded as justifying such an approach to forward error correction and synchronisation patterns.
Conclusions
341 The primary judge then drew the following conclusions.
342 According to his Honour, it was apparent that Hytera had shifted its position somewhat by the end of the trial. Whereas it had opened the case on the basis that Mr Kuhrt’s revised methodology showed that the invention was obvious, it had retreated from Mr Kuhrt somewhat by the close of the trial. Rather, by the end of the trial, its position was that Professor Rangan had accepted that the use of a control message, containing information indicating whether activity was present on the channel, was something which would have occurred to him at the priority date and had therefore accepted that the use of the first information in claim 1 was obvious. Further, he had accepted that the use of the second information was also obvious.
343 The primary judge did not accept Motorola’s objection that it was unclear what design Hytera was putting forward. Whilst it was open to Hytera to seek to prove the lack of an inventive step by reference to the method composed by Mr Kuhrt, this did not prevent it from also relying on the evidence of Professor Rangan, if it could, to show that the invention was obvious. Hytera bore the onus of proving that the invention was obvious. As a matter of trial procedure, it was not confined, in seeking to discharge that onus, to rely solely upon the evidence of Mr Kuhrt. If it wished, it was entitled to rely upon the evidence of Professor Rangan too.
344 More substantial was Motorola’s submission that Hytera’s submission glossed over the question of combining the first and second information in claim 1. Whilst it is true that Professor Rangan said that the full LC message had all the features of claim 1 apart from the first information, and that he would have considered using a first information as part of a scanning method, he also gave evidence that it would have been illogical to combine an activity indicator with the full LC message in the draft DMR protocol. Although it was obvious as part of a scanning method to use a first information to indicate the presence of activity, and it was obvious to use a second information of the kind which appeared in the full LC message, it was not obvious to give the full LC message an activity indicator because such a design would not have been logical. In re-examination, Professor Rangan explained why it would not be logical. The minimal increase in speed would be offset by the overhead from the extra bit. The primary judge accepted this evidence and that a person of ordinary skill would not have sought to combine an activity indicator bit with the full LC message. In his view, Hytera’s submission posed the risk of dividing the invention into integers and then addressing the question of whether each integer was of itself obvious, rather than as a combination.
345 So, whilst his Honour accepted that it was open for Hytera to rely upon Professor Rangan’s evidence to prove that the invention was obvious, he did not accept that his evidence did in fact do so.
346 This then directs attention to the question of whether Hytera had otherwise discharged its burden of proving that the invention was obvious. The only other way it sought to do this was through the evidence of Mr Kuhrt which it did not formally abandon even if its reliance upon it was somewhat muted. Whilst the primary judge accepted that Mr Kuhrt’s revised methodology did theoretically implement claim 1, there are several reasons why he did not accept that it demonstrated that claim 1 was obvious.
347 First, his Honour was not persuaded that Mr Kuhrt’s revised method is something which a person of ordinary skill would ever have put forward as a method of improving scan time. A solution which led to a reduction in synchronisation patterns and forward error correction, and which was inconsistent with the draft DMR protocol, is not something which anyone in the field of two-way radios would have contemplated as being sensible as at the priority date. Whilst his Honour accepted that Mr Kuhrt’s solution was viable, in the sense that it would actually work if anyone sought to implement it, he did not accept that it was plausible. As finally presented, it was a method which had the following problematic aspects.
348 It was a method that was inconsistent with the draft DMR protocol and hence with the direction in which the industry was heading. As Mr Kuhrt accepted, what was likely to be standardised in the future was relevant to the design task.
349 Further, it was a method that involved reductions in the size of the synchronisation patterns and forward error correction as the price to be paid for solving what Mr Kuhrt described as the “relatively minor issue” of scan speed. The fact that the scan speed problem was regarded as a relatively minor issue means that it would be most unlikely that a design solution would be reached which involved, as the price to be paid for that solution, reductions in forward error correction, synchronisation patterns and incompatibility with what was likely to become the standard.
350 Further, it was a method that was not suitable for large fleets.
351 Second, the primary judge observed that this unreality was itself a function of the fact that the question which Mr Kuhrt was asked was the wrong question. No person would have sought to create an improvement in scan time without this being done in the context of the design of an overall system. Indeed, Mr Kuhrt accepted that what he understood his task to be was to “create the ultimate scanning machine”. As such, Mr Kuhrt did not consider weighing up advantages of his method against the disadvantages it might pose to other aspects of the device’s performance. One consequence of this is Mr Kuhrt’s inevitable acceptance that the task he had been given was artificial and was not a task that he would be likely to have undertaken at the priority date. Mr Kuhrt would not have embarked upon this task and the primary judge was satisfied that no other person of ordinary skill working in the field of digital two-way mobile radios would have done so either.
352 Third, the primary judge considered that Mr Kuhrt’s revised methodology suffered from the further vice of not only resulting from the wrong initial question but also of being infected with the views of Professor Rangan as to the deficiencies of the first methodology. Mr Kuhrt’s final design was the result of an implausible technical task combined with the views of one of the other expert witnesses in the case. The first method would have resulted in reduced audio quality which makes it an unlikely candidate for something which the person of ordinary skill would have embarked upon. It is even less likely that having embarked on such a course the person of ordinary skill would, without the interposition of Professor Rangan’s criticisms, come up with the revised method.
353 Fourth, the primary judge was not satisfied that Mr Kuhrt’s scan methodology was not the result of his exposure to the 2005 DMR Standard. Whilst the primary judge did not doubt Mr Kuhrt’s honesty in saying that he had only answered the question he was asked with the knowledge he had at the priority date, his Honour was doubtful whether that was really possible.
354 Therefore, the primary judge was satisfied that Mr Kuhrt’s method was not something that a person of ordinary skill would ever have done.
355 Consequently, his Honour did not accept that Hytera had demonstrated that the invention disclosed in the 355 patent was obvious and therefore lacked an inventive step. This disposed of Hytera’s obviousness case. Neither Professor Rangan’s nor Mr Kuhrt’s evidence established that the invention was obvious.
356 Having set out part of the primary judge’s reasoning, albeit in some detail, it is convenient to now analyse Hytera’s challenge to his Honour’s findings.
Consideration
357 At trial, Hytera had the onus of proof and in that respect relied upon the evidence of its expert, Mr Kuhrt, albeit not exclusively. But there were difficulties with Mr Kuhrt’s evidence.
358 First, although Hytera primarily relied upon the evidence from Mr Kuhrt concerning the relevant hypothetical task, a considerable difficulty was that an activity update message of the type described in the 355 patent had been incorporated into the 2005 DMR Standard as the “Short LC message” in 2005. So it was therefore known to everyone. It was not credible that Mr Kuhrt could avoid the problem of hindsight bias, given that he had been exposed to the 2005 DMR Standard and the types of control messages used therein.
359 Hytera says that the primary judge erred in reasoning that Mr Kuhrt’s methodology was affected by hindsight, on the basis that the primary judge accepted Mr Kuhrt’s evidence that Mr Kuhrt had only answered the question he was asked with the knowledge he had at the priority date. But what the primary judge said was (at PJ [324]):
I am not satisfied that Mr Kuhrt’s scan methodology was not the result of his exposure to the 2005 DMR Standard. While I do not doubt for a moment Mr Kuhrt’s honesty in saying that he had only answered the question he was asked with knowledge he had at the priority date, I am doubtful whether that was really possible.
360 We agree with Motorola that this did not constitute a finding by the primary judge that Mr Kuhrt had only answered the hypothetical question with knowledge he had at the priority date. Moreover, as his Honour said at PJ [239], “Mr Kuhrt already knew (and had known for a long time) that the 2005 DMR Standard used an activity indicator bit and identification information”. Clearly, in assessing Mr Kuhrt’s evidence, the primary judge correctly took into account that Mr Kuhrt had already seen the solution in the 355 patent, in the sense of the incorporation of the embodiment of the activity update message.
361 Further, his Honour doubted whether it was reasonably possible to put out of one’s mind the existence of the 2005 DMR Standard. As he said (at PJ [239]):
In this case, as will be seen, Mr Kuhrt was aware of the 2005 DMR Standard which was published in April 2005. As I discuss below, that standard included within it a scan message which used an activity indicator bit and ID information. Although he was asked to formulate his method before being shown the 355 patent, it must be borne in mind that Mr Kuhrt already knew (and had known for a long time) that the 2005 DMR Standard used an activity indicator bit and identification information. In assessing his proposed revised method, it is to be borne in mind, therefore, that in a sense he had already seen the solution in the 355 patent because it was the solution in the 2005 DMR Standard. Whilst I do not doubt that Mr Kuhrt genuinely believed that he put himself in the position he would have been in as at July 2004, that is, that he knew nothing except for pre-existing standards (such as the P25 Standard, the 1998 TETRA Standard and the Draft DMR Protocol) at a remove of 14 years, it must be doubted in my view whether it is reasonably possible to put out of one’s mind the existence of the 2005 DMR Standard. …
362 Hytera has demonstrated no material error in the primary judge’s reasoning in this respect.
363 Second, it is significant that Mr Kuhrt originally proposed a method of scanning which would not have been compatible with the 1998 TETRA standard and the draft DMR protocol which existed at the priority date of the 355 patent. The primary judge observed (at PJ [235]):
As at the priority date, the only TDMA system in existence, as disclosed by the evidence, was the system embodied by TETRA. ETSI was considering introducing a TDMA standard and did so the following year in the form of the 2005 DMR Standard. As at the priority date, it did not exist, although it was in preparation. As I discuss later, a draft of the standard, the Draft DMR Protocol, was available to those in the industry. The point, for relevant purposes, is that as at the priority date, there was no standardised TDMA system although it was apparent that one was soon to be forthcoming. Accepting therefore Motorola’s submission that in a field such as wireless technology the standards environment can impose practical and technical constraints on development, such restrictions in this case are those which can be discerned from 1998 TETRA Standard and the Draft DMR Protocol. As will be seen, Mr Kuhrt’s initial proposed method of scanning would not have been compatible with either of these. When Professor Rangan pointed this out, particularly in relation to the Draft DMR Protocol, Mr Kuhrt revised aspects of his method which to an extent, although not completely, would have brought it within the Draft DMR Protocol. He was explicit in this exercise in doing this only as a response to Professor Rangan’s criticisms.
364 Quite correctly, the primary judge accepted that practical and technical issues could operate as what could be described as a negative aspect of the common general knowledge. So, in a field such as wireless communications systems, the standards environment imposed practical and technical constraints on the developments in the relevant technology. His Honour said (at PJ [234]):
In its written closing submissions, Motorola emphasised this negative aspect of the CGK as having particular aptness in a field such as wireless communications systems because the standards environment imposed practical and technical constraints on the developments in the relevant technology: at [33]. In Dyson Appliances Ltd v Hoover Ltd [2001] RPC 26 at [156], the English Patents Court recognised the negative aspects of the CGK when discussing how the skilled addressee might have approached the idea of cleaning air in a vacuum cleaner, not by means of bags, but instead by using cyclonic action alone:
In terms of its impact on the issue of obviousness, I believe that this negative thinking which as Mr Kitchin suggested amounted to prejudice, would at least have caused the addressee to regard modification to any of these prior art proposals with considerable reserve if not overt scepticism.
365 Carrying that question forward, the primary judge found (at PJ [292] and [293]) that Mr Kuhrt’s method was inconsistent with the draft DMR protocol, and that it was also incompatible with the 1998 TETRA standard.
366 To overcome this issue, and as his Honour noted, Mr Kuhrt subsequently revised aspects of his method which to an extent, although not completely, would have brought it within the draft DMR protocol (at PJ [235]). But the primary judge found that Mr Kuhrt’s revised methodology was also a very unlikely solution as at July 2004. He said (at PJ [297]):
That said, having regard to the direction in which the Draft DMR Protocol was heading, Mr Kuhrt’s revised methodology strikes me as being a very unlikely solution as at July 2004. To solve the relatively lesser problem of scan time by coming up with a methodology with diminished forward error correction and reduced synchronisation patterns (which was radically inconsistent with the direction in which the industry appeared to be heading) was possible, but it was most unlikely that anyone would have actually embarked on the search for such a method. Mr Kuhrt accepted that if he had been developing a new device at the priority date, he would have obtained the Draft DMR Protocol because it would have been instructive to him as to what was likely to become standardised in the future:
MR MOORE: Yes. And if you working in Australia were interested in developing some new device at that time, presumably, you would have obtained this standard because it would have been instructive to you as to what was likely to become standardised in the very near future?
MR KUHRT: Yes.
MR MOORE: And you would be very interested in what’s the technology being employed and how is that going to operate, and you would start thinking along those lines if you were going to be involved in any development task at that time?
MR KUHRT: Yes.
MR MOORE: Yes. And you mention in your opening paragraph there, there was little scope within the specifications to improve scan time. What you meant by that is that if you have a different mode of scanning it’s not going to be consistent with the scan mode in the specification?
MR KUHRT: Yes, if there was something that you’re proposing that would be outside what was planned in the specification. Yes.
MR MOORE: Yes. And you wouldn’t have been engaged in any task of departing from the specification in that way; correct?
MR KUHRT: Correct.
367 The primary judge concluded, rightly in our view, that a solution which led to a reduction in synchronisation patterns and forward error correction and which was inconsistent with the draft DMR protocol was not something which anyone in the field of two-way radios would have contemplated as being sensible at the priority date, particularly when these negative aspects would be incurred in pursuit of an improvement in the “relatively minor issue” of scan speed. His Honour said (at PJ [321]):
Whilst I accept that Mr Kuhrt’s revised methodology does theoretically implement claim 1, there are several reasons why I do not accept that it demonstrates that claim 1 was obvious. First, I am not persuaded that Mr Kuhrt’s revised method is something which a person of ordinary skill would ever have put forward as a method of improving scan time. A solution which led to a reduction in synchronisation patterns and forward error correction and which was inconsistent with the Draft DMR Protocol, is not something which anyone in the field of two-way radios would have contemplated as being sensible as at the priority date. Whilst I accept, as Hytera submitted at [98] of its closing written submissions, that Mr Kuhrt’s solution was viable, in the sense that it would actually work if anyone sought to implement it, I do not accept that it was plausible. As finally presented, it was a method which:
(a) was inconsistent with the Draft DMR Protocol and hence with the direction in which the industry was heading. As Mr Kuhrt accepted at T767.13-24, what was likely to be standardised in the future was relevant to the design task;
(b) involved reductions in the size of the synchronisation patterns and forward error correction as the price to be paid for solving what Mr Kuhrt described, at §33 of his third affidavit, as the ‘relatively minor issue’ of scan speed. The fact that the scan speed problem was regarded as a relatively minor issue means that it would be most unlikely that a design solution would be reached which involved, as the price to be paid for that solution, reductions in forward error correction, synchronisation patterns and incompatibility with what was likely to become the standard; and
(c) was not suitable for large fleets.
368 In our view, those findings were well open to his Honour on the evidence.
369 Further, as the primary judge was entitled to find, the task given to Mr Kuhrt was artificial and not one that Mr Kuhrt would be likely to have undertaken at the priority date. His Honour said (at PJ [322]):
Secondly, this unreality is itself a function of the fact that the question which Mr Kuhrt was asked was the wrong question. No person would have sought to create an improvement in scan time without this being done in the context of the design of an overall system. Indeed, Mr Kuhrt accepted that what he understood his task to be was to ‘create the ultimate scanning machine’: T770.39. As such, he did not consider weighing up advantages of his method against the disadvantages it might pose to other aspects of the device’s performance: T770.30-34. One consequence of this is Mr Kuhrt’s inevitable acceptance that the task he had been given was artificial and was not a task that he would be likely to have undertaken at the priority date: T771.22-26. Mr Kuhrt would not have embarked upon this task and I am satisfied that no other person of ordinary skill working in the field of digital two-way mobile radios would have done so either.
370 Further, the primary judge was correct to find that given that Mr Kuhrt only arrived at his revised method in response to the comments made by Professor Rangan, it was very unlikely that a person skilled in the art would have come up with Mr Kuhrt’s revised method without prompting.
371 Hytera said that the primary judge erred in finding that the reduction in synchronisation patterns and forward error correction would lead the skilled addressee away from the invention in circumstances where the claims make no stipulations about control message size, the size of synchronisation patters or the extent of forward error correction. It is said that those limitations did not form part of the invention and so cannot be taken into account on the question of inventive step. But as the primary judge concluded, and with which we agree, a skilled addressee working at the relevant time would not embark upon a solution that degraded other aspects of the operation of the system merely to improve scan speed. As his Honour said, that was what Mr Kuhrt did only because he understood that the task that he was set was to “create the ultimate scanning machine” (PJ [322]) without regard for any trade-offs.
372 Whilst the issue of scan time was common general knowledge, the primary judge found that the hypothetical task that Mr Kuhrt was asked to address was inappropriate on the basis that the common general knowledge also established that no person would have sought to create an improvement in scan time without this being done in the context of the design of an overall system. We see no difficulty with such reasoning.
373 Third, Hytera sought to bolster its case by reference to Professor Rangan’s acceptance that the use of activity indicating information in a control message as part of a scanning method was obvious. Hytera sought to combine this with other evidence of Professor Rangan to the effect that a person of ordinary skill in the art would have thought to use the LC message in the draft DMR protocol for scanning, and that the LC message had all the features of the control message of claim 1 except the “first information”. But the primary judge found that in so seeking to combine these two pieces of Professor Rangan’s evidence, Hytera ignored part of Professor Rangan’s evidence. The primary judge explained (at PJ [316]):
More substantial is Motorola’s submission that Hytera’s submission skated over the question of combining the first and second information in claim 1. Whilst it is true that Professor Rangan said that the full LC message had all the features of claim 1 apart from the first information, and that he would have considered using a first information as part of a scanning method, he also gave evidence that it would have been illogical to combine an activity indicator with the full LC message in the Draft DMR Protocol. Following the exchange between Professor Rangan and Mr Burgess extracted above at [312], Professor Rangan stated at T824.42-43:
PROF RANGAN: It would – it would then – it would then – it would likely satisfy the claim. It wouldn’t be a logical design, but it would likely satisfy ..... the claims.
374 Given such evidence, in our view the primary judge was correct to find that (at PJ [317]):
… Although it was obvious as part of a scanning method to use a first information to indicate the presence of activity, and it was obvious to use a second information of the kind which appeared in the full LC message, it was not obvious to give the full LC message an activity indicator because such a design would not have been logical. In re-examination, Professor Rangan explained why it would not be logical in these terms:
MR MOORE: Professor Rangan, you were asked some questions a few minutes ago about the link control message possibly supplying the second information on the claims, call that, and the possibility of adding a first information to the link control message and in answer to the question you said it wouldn’t be a logical design. Can you explain why you say it would not be a logical design?
PROF RANGAN: Because while – if you took the current link control as the baseline and – we refer to, let’s say, in the draft DMR or in the P25 standard and you added the first information, there would be potentially small benefit in reduction in scan time simply because you could process the – the message slightly quicker, but there would be no – that would be outweighed by the increase in overhead from adding that one bit because you already have the full information with the ID and other fields to determine all the characteristics about the activity of interest, so you’re not getting the benefit of this. In fact, even – so there would – you would be kind of torn away – or maybe I shouldn’t say torn away, but any reasonable designer would not choose to put in that bit at that time.
MR MOORE: Yes, thank you. Mr Kuhrt, I don’t know whether you were following that, but do you agree with that answer?
MR KUHRT: Yes, you would – adding the extra bit would make it – message longer and therefore you wouldn’t get any benefit of a - - -
MR MOORE: Yes, thank you. I have no further questions, your Honour.
375 Further, as the primary judge noted (at PJ [318]):
That is to say, the minimal increase in speed would be offset by the overhead from the extra bit. I accept this evidence and that a person of ordinary skill would not have sought to combine an activity indicator bit with the full LC message. In my view, Hytera’s submission poses the risk identified in Alphapharm of dividing the invention into integers and then addressing the question of whether each integer was of itself obvious, rather than as a combination.
376 So, Hytera’s approach posed the risk of dividing the invention embodied in the relevant claim(s) into integers and then addressing the question of whether each integer was itself obvious, rather than properly addressing the combination. Such an atomistic approach was impermissible.
377 Further, as Motorola correctly submitted, Hytera’s approach proceeded from the false premise that the “scan message” proposed by Mr Kuhrt was the same as the Activity Update Short LC message later adopted by the 2005 DMR Standard. But Mr Kuhrt’s “scan message” had a different structure to the Activity Update Short LC. Further, the Activity Update Short LC when included in the 2005 DMR Standard was not specified for use in a scanning method, let alone the particular method of scanning claimed by the 355 patent. Accordingly, Hytera’s assertion that the publication of the 2005 DMR Standard after the priority date of the 355 patent was an indication of obviousness is not maintainable.
378 For the foregoing reasons, we reject Hytera’s case concerning a lack of inventive step. Ground of appeal 11 is rejected.
Utility – ground of appeal 12
379 Hytera’s ground of appeal 12 challenges the primary judge’s findings on the question of utility. It is convenient in the context of this ground to begin with how his Honour dealt with the matter.
The reasons of the primary judge
380 At trial, Hytera’s point was that once it was accepted that claim 1 could be implemented without regard to the size of the control message or the payload, then it followed that the promise of the patent, being an improvement in the time taken for scanning, need not be delivered.
381 The primary judge accepted that it was true that claim 1 could be implemented in the way suggested by Hytera. And his Honour recognised that this was a consequence of Motorola not seeking to contend that any such limitations were present as a matter of construction. His Honour said (at PJ [347]):
Hytera’s point here was a short one. Once it was accepted that claim 1 could be implemented without regard to the size of the control message or the payload, then it followed that the promise of the patent – an improvement in the time taken for scanning – need not be delivered. I accept that it is true that claim 1 can be implemented in the way suggested by Hytera. This is a consequence of Motorola not seeking to contend that any such limitations were present as a matter of construction.
382 Hytera submitted before his Honour that the promise of the 355 patent was an improvement in the amount of time that a mobile station spends scanning a pre-programmed list of channels. And its case was that because claim 1 would permit the control message to be split over any number of bursts, including the 7 burst full LC message described in the body of the specification, there need not be any reduction in scan time at all.
383 The primary judge accepted that both Mr Kuhrt and Professor Rangan agreed that it would be perverse to implement claim 1 using a second information which was longer than the prior art full LC message.
384 In relation to Mr Kuhrt, his Honour recited his evidence under cross-examination. He said (at PJ [350]):
Motorola submitted that both Mr Kuhrt and Professor Rangan agreed that it would be perverse to implement claim 1 using a second information which was longer than the prior art full LC message. I accept this submission. In relation to Mr Kuhrt, he gave this evidence under cross-examination:
MR MOORE: And you wouldn’t understand claim 1 of the patent as specifying the use of information that is longer than the full LC message.
MR KUHRT: It depends on the construction. If it’s within the construction of the claim, then I would still read it that way.
MR MOORE: It’s not the point of the patent, as you understand it, is it, Mr Kuhrt?
MR KUHRT: It’s not the point of the patent.
MR MOORE: Yes.
MR KUHRT: I agree.
MR MOORE: And so you wouldn’t read claim 1 as referring to information that was longer than the prior art LC message, would you?
MR KUHRT: Again, it wouldn’t be the point of the patent.
MR MOORE: No, and that would be a perverse application of claim 1, wouldn’t it, to use information that’s longer than the prior art message?
MR KUHRT: It would be a pointless application.
MR MOORE: Yes.
MR KUHRT: Because it’s already there. Yes.
MR MOORE: Yes. And you would agree, wouldn’t you, that what the patent is disclosing to you is that whatever method or code word is used to convey full control information, including information about the message or about other control information, that you can use a shorter method by utilising particular criteria or particular information that is shorter than the full message.
MR KUHRT: Yes.
MR MOORE: And if you had this patent as at July 2004, you certainly wouldn’t implement claim 1 by selecting a second information that was longer than the prior art LC message, would you?
MR KUHRT: No, because you would be creating a system that would take longer to scan.
MR MOORE: Yes. Yes. And you would agree that would be a perverse way of implementing claim 1?
MR KUHRT: Yes.
385 His Honour recorded that Professor Rangan gave evidence that any reasonable embodiment of claim 1 would not increase the number of bursts over whatever the base system was from which the skilled addressee was commencing.
386 So, whilst the primary judge accepted that claim 1 on its proper construction did permit both a second information which is longer than the full LC message and the transmission of the second information in more bursts than existed in a base system, he did not accept that these would be reasonable implementations of the claim. As such, he did not accept that they were relevant to the question of utility. In his Honour’s view, this was a case where the qualifications and expedients necessary to make the article claimed work can be, and on a true construction of the claim are, left to the reader to supply for himself. Consequently, his Honour rejected Hytera’s challenge to validity on the basis of a lack of utility.
Hytera’s submissions
387 Hytera says that the primary judge erred in finding that the invention claimed in claims 1 to 6 and 10 of the 355 patent was useful.
388 Hytera acknowledges that the primary judge correctly accepted that the claims could be implemented in a way that did not achieve the promise of the invention, being to provide an improvement in scanning time. This was on the basis that the claims permitted the control message to be split over any number of bursts, including the 7 burst sequence used in the prior art, such that there may be no improvement in scanning time. Hytera also acknowledges that his Honour correctly accepted that the utility of the invention had to be assessed against the breadth of the claims. But Hytera says that having made these findings, his Honour erred in concluding (at PJ [353]) that the invention was useful on the basis that “the qualifications and expedients necessary to make the article claimed work can be, and on a true construction of the claim are, left to the reader to supply for himself”.
389 Hytera says that the primary judge (at PJ [352]) misapplied the reasoning in Apotex Pty Ltd v Warner-Lambert Co LLC (No 2) [2016] FCA 1238; 122 IPR 17 (Apotex) at [169] where it was said:
It is often said that the principle that a claim is bad if it is wider than what is useful is one that must be applied with great caution. As Blanco White explains at para 4–409:
It follows from what has been said that it is often a convenient test of the utility of the invention contained in a claim to consider whether the claim includes forms of the invention which are not useful, but that this test must be applied with very great caution. The function of a claim is to delimit the monopoly given by the patent, not to give instructions for the working of the invention, and it is consequently not necessary that the claim should contain these instructions; even the body of the specification is required to contain only those instructions that the reader cannot supply for himself. It would be unreasonable to expect the claims to contain more. A distinction should accordingly be drawn between cases in which the invention claimed is not useful unless an additional feature or features be added to those claimed (the claim then being invalid), and cases where the qualifications and expedients necessary to make the article claimed work can be, and on a true construction of the claim are, left to the reader to supply for himself. Since in cases where the reader can make the thing work the courts tend wherever possible to construe claims as requiring him to do so, it is not in practice enough to ask whether the claim includes things that are not useful; it is necessary to ask also whether there is anything in the language of the claim positively pointing to some useless construction. The successful utility attacks are nearly always in cases of that sort. Examples are: where a claim specifies two alternative processes or constructions of mechanism, of which only one is useful; or the claim specifies the use of any of a group of chemical compounds, and it is not substantially true that all will work; or the claim includes a series of constructions, and only certain members of the series are useful; or more generally, the claim contains a limitation directed to a particular feature and further limitation of that same feature is needed for utility; or the feature needed for effective working is expressly made optional-as when it is added by a subsidiary claim.
It does not follow that a broad claim is invalid merely because some subsidiary claim within it lacks utility: for the invention the subject of the subsidiary claim may be intended to attain some result additional to the main object to which the broader claim is directed.
(Footnotes omitted; TA Blanco White, Patents for Inventions, 5th ed. Stevens & Sons, London, 1983)
390 Hytera argues that, unlike that case, the present case is one in which an additional feature or limitation is needed in order to give the claims utility; for example, a limitation on the number of bursts over which the control information can be split. Hytera says that the question is ultimately one of the proper construction of the claim. Hytera relies on the statement in Alphapharm Pty Ltd v H Lundbeck A/S [2008] FCA 559; 76 IPR 618 at [468] where was said that:
… a claim is bad if it covers means that will not produce the desired result even if a skilful person would know which means to avoid …
391 The primary judge (at PJ [350]) relied on evidence given by Mr Khurt and Professor Rangan to the effect that “it would be perverse to implement claim 1 using second information which was longer than the prior art full LC message”. But Hytera says that even accepting that proposition, the claim encompasses methods in which the second information is split over the same number of bursts as the prior art, with no improvement in scanning time. Hytera says that there was no finding, and no evidence, that it would be “perverse” to implement claim 1 in this way, using the same number of bursts as were used in the prior art.
392 Hytera says that based on the description, an improvement in scanning time is achieved by allowing a subscriber unit to more quickly determine that an activity is not of interest and move on to the next channel. But the claim is not framed in that way. Instead, it requires the subscriber unit to determine that the activity is of interest, and to remain on the channel to receive the activity if that is so. So, Hytera says that, adapting the language of Blanco White, Patents for Invention (5th ed, Stevens & Sons) quoted in Apotex at [169], there is something “in the language of the claim positively pointing to some useless construction”. Hytera says that this case is akin to the examples of inutility given by Blanco White where the claim includes a series of constructions, and only certain members of the series are useful, or the claim contains a limitation directed to a feature and further limitation of that feature is needed for utility.
Consideration
393 In the context of not falling foul of s 18(1)(c), the claimed invention must do what it is intended by the patentee to do, and the end obtained must itself be useful. So, the invention as claimed must attain the result promised by the patentee. And it is not in doubt that this issue is to be tested against the breadth of the claim.
394 Hytera contends that because claim 1 would permit the control message to be split over any number of bursts, including the 7 burst full LC message of the prior art, claim 1 could be implemented in a manner which did not improve the scan time over the prior art. Hytera says that there was no evidence that it would be perverse to implement claim 1 using a message that was the same length as used in the prior art, and that the use of the same length is covered by the claims.
395 We agree with Motorola that Hytera’s position is problematic.
396 First, Hytera’s position does not properly reflect the evidence. The relevant transcript of Mr Kuhrt’s evidence was reproduced by the primary judge at PJ [350], which we have already set out. Mr Kuhrt accepted that the patent disclosed to him that, whatever method or code word is used to convey the full control information (that is, the full LC), one could use a shorter message by utilising information that is shorter than the full message. It was in that context that Mr Kuhrt agreed that it would be a perverse way of implementing claim 1 to select a “second information” that was longer than the prior art LC message, and that this was “not the point of the patent”. As Motorola correctly submits, the evidence taken as a whole makes clear that it would equally be a perverse application to use a second information that was the same length, because that was contrary to the point of the patent. We agree with Motorola that it is clear that no reasonable skilled addressee would adopt that approach in carrying out the invention.
397 Second, his Honour said at PJ [317], which we have already set out, that although it was obvious as part of a scanning method to use a first information to indicate the presence of activity, and it was obvious to use a second information of the kind which appeared in the full LC message, it was not obvious to give the full LC message an activity indicator because such a design would not have been logical. So, his Honour’s finding, which in our view was open to him, was that the skilled person would not have sought to combine an activity indicator bit with the full LC message, and claim 1 requires an activity indicator being the first information.
398 Third, the primary judge did not mis-apply the reasoning in Apotex. In Apotex at [169], Nicholas J referred to the need for great caution in making a finding of inutility, citing Blanco White at [4-409], which explained that “it is not in practice enough to ask whether the claim includes things that are not useful; it is necessary to ask also whether there is anything in the language of the claim positively pointing to some useless construction”.
399 For those reasons, we reject Hytera’s challenge concerning inutility. Ground of appeal 12 is rejected.
Manner of manufacture – ground of appeal 13
400 Hytera’s ground of appeal 13 challenges the primary’s findings on the question of manner of manufacture. It is convenient to begin with how the primary judge dealt with and rejected the manner of manufacture ground of potential invalidity.
The reasons of the primary judge
401 The primary judge recognised that it has been accepted in this Court that a computer-implemented invention will be patentable if, in substance, it constitutes an improvement in computer technology rather than a use of that technology (Commissioner of Patents v Aristocrat Technologies Australia Pty Ltd [2021] FCAFC 202; 163 IPR 231 (Commissioner v Aristocrat); Repipe Pty Ltd v Commissioner of Patents [2021] FCAFC 223; 164 IPR 1). And as his Honour recognised, Commissioner v Aristocrat did not depart from any of the authorities which preceded it. An appeal in that case to the High Court was dismissed by force of s 23(2)(a) of the Judiciary Act 1903 (Cth) when the Court split 3-3 (Aristocrat Technologies Australia Pty Ltd v Commissioner of Patents (2022) 274 CLR 115). As such, and as his Honour recorded, the High Court’s decision had no ratio decidendi and stood only for the proposition that the Full Court’s decision stands.
402 It was not in doubt that the 355 patent was a computer-implemented invention. The 355 patent concerned a method of scanning which could be used in a TDMA system to reduce the time required for completing scan operations.
403 At trial Hytera’s primary submission was that there could be no manner of manufacture where what is claimed merely involves the new use of a known thing for a purpose for which its known properties made it suitable (Commissioner of Patents v Microcell Limited (1959) 102 CLR 232 at 249 and 250; N V Philips Gloeilampenfabrieken v Mirabella International Pty Limited (1995) 183 CLR 655 at 663 and 664). Hytera argued at trial that the 355 patent, as a matter of substance, was to be seen as being in the nature of a scheme, working directions or directions for use, rather than as an “improvement in computer technology”. It did not involve or contribute to any new hardware or software. The patent was merely a method achieved by programming existing hardware to carry out specified steps. Hytera argued that there was no claimed ingenuity in the manner in which the methods were to be implemented in the subscriber units, and the patent gave no guidance on how such implementation was to be carried out. Hytera said that the claimed ingenuity lay in the steps identified in the claims which were no more than a scheme or set of directions.
404 The primary judge did not accept this submission. His Honour considered that the invention claimed was of the same quality as the curve drawing algorithm in International Business Machines Corporation v Commissioner of Patents (1991) 33 FCR 218. His Honour said (at PJ [358]):
I do not accept this submission. The invention claimed is of the same quality as the curve drawing algorithm in International Business Machines Corporation v Commissioner of Patents (1991) 33 FCR 218 (‘IBM’). The 355 patent improves the way a particular class of computers – base stations and subscriber units – scan frequencies. The problem of the scanning speed is a problem of computer programming and is relevantly indistinguishable to the problem in IBM of curve drawing on computers. Curve drawing on computers required the use of processing-expensive floating point arithmetic. This kind of floating point arithmetic was expensive in terms of system resources. The solution in that case – the deployment of an algorithm which removed the need to use floating point arithmetic – resulted in an improvement in computer technology. The same is true here. The problem which existed was the problem of how to improve scanning times in a TDMA system. The solution was the use of an activity indicating first information which could permit the abolition of the null ID and therefore permit compression of ID information in the second information. To my mind, these are conceptually indistinguishable. The 355 patent is plainly an improvement in computer technology.
405 The primary judge found that the 355 patent improved the way a particular class of computers, being base stations and subscriber units, scan frequencies. His Honour reasoned that the problem of the scanning speed is a problem of computer programming and is relevantly indistinguishable to the problem in IBM of curve drawing on computers. Curve drawing on computers required the use of processing-expensive floating point arithmetic. This kind of floating point arithmetic was expensive in terms of system resources. The solution in that case, being the deployment of an algorithm which removed the need to use floating point arithmetic, resulted in an improvement in computer technology. His Honour said that the same was true in the context before him.
406 His Honour said that the problem which existed was the problem of how to improve scanning times in a TDMA system. The solution was the use of an activity indicating first information which could permit the abolition of the null ID and therefore permit compression of ID information in the second information. His Honour said that these are conceptually indistinguishable and that the 355 patent is plainly an improvement in computer technology.
407 His Honour therefore rejected Hytera’s defence that the 355 patent as claimed did not disclose a manner of manufacture.
Hytera’s submissions
408 Hytera contends that the primary judge erred in finding that the invention claimed in claims 1 to 6 and 10 of the 355 patent was a manner of manufacture. Hytera says that his Honour misapplied the applicable principles by failing to focus on the claimed invention. In this regard, Hytera pointed out correctly that the question of manner of manufacture is to be assessed by reference to the invention “so far as claimed” (s 18(1)(a)). Hytera submitted that whatever might be said about the disclosure of the specification, the Patents Act requires that the invention “so far as claimed” be a manner of manufacture, and this is to be determined based on the proper construction of the claims (Commissioner of Patents v Rokt Pte Ltd (2020) 277 FCR 267 at [95]).
409 Hytera says that if a claim, properly construed, and considered as a matter of substance, not form, includes within its scope something that is not proper subject matter for letters patent, it fails for want of manner of manufacture.
410 Hytera says that the basis of the primary judge’s conclusion was that the solution provided by the 355 patent to the problem of how to improve scanning time was the use of an activity indicating first information which could permit the abolition of the null ID and therefore permit compression of ID information in the second information. But according to Hytera, this did not reflect the invention claimed in claims 1 to 6 and 10, which requires neither the abolition of the null ID nor the compression of any ID information.
411 Hytera says that the primary judge erred in deciding the issue solely by reference to the criterion of an improvement in computer technology, when this is only one touchstone referred to in the authorities, and in finding that the claimed invention here, as a matter of substance, involved such an improvement.
412 Further, Hytera says that the primary judge ought have found that the claimed invention involved the use of two types of existing information in an existing control message for scanning purposes, and was in substance an unpatentable abstract idea implemented using conventional two-way radio equipment.
413 Hytera says that the asserted claims of the 355 patent do not define any improvement in computer technology. Hytera says that the primary judge was in error in focusing on what the 355 patent “involves” or “discloses”, not what it claims. Hytera says that the claims do not define the technical solution disclosed in the 355 patent that results in an improvement to scanning time. And it is not enough that the use of an activity indicating first information could permit that result. In particular, the claims do not limit the nature of the second information, the size of the control message or the number of bursts over which it is applied. Generally, Hytera says that at the level of abstraction of the claim language used, the claims do no more than provide a list of steps to be implemented using conventional computer technology for its well-known and understood functions.
Consideration
414 The 355 patent involves an improvement in the technology for undertaking communications using two-way radios, being an improvement in efficiency by way of a reduction in the time taken to perform tasks. The 355 patent discloses an improvement in the operation of a computer device, being an improvement in scanning time. It is patentable subject matter.
415 The primary judge stated the applicable principles as follows (at PJ [355] and [356]):
Section 18(1)(a) of the Patents Act imposes a requirement that a claimed invention be a ‘manner of manufacture’ within the meaning of s 6 of the Statute of Monopolies 1623, 21 Jac 1 c 3. The general principles governing that question are set out in the High Court’s decision in National Research Development Corporation v Commissioner of Patents (1959) 102 CLR 252 at 276-277. More recently, the High Court has affirmed and expanded those principles in D’Arcy v Myriad Genetics Inc [2015] HCA 35; 258 CLR 334 at 351.
It has been accepted in this Court that a computer-implemented invention will be patentable if, in substance, it constitutes an improvement in computer technology rather than a use of that technology: CCOM Pty Ltd v Jiejing Pty Ltd (1994) 51 FCR 260; Research Affiliates LLC v Commissioner of Patents [2014] FCAFC 150; 227 FCR 378; Commissioner of Patents v RPL Central Pty Ltd [2015] FCAFC 177; 238 FCR 27; Encompass Corporation Pty Ltd v InfoTrack Pty Ltd [2018] FCA 421; 130 IPR 387; Commissioner of Patents v Aristocrat Technologies Australia Pty Ltd [2021] FCAFC 202; 163 IPR 231 (‘Aristocrat’); Repipe Pty Ltd v Commissioner of Patents [2021] FCAFC 223; 164 IPR 1. I do not read Aristocrat as departing from any of the authorities which preceded it. An appeal in that case to the High Court was dismissed by force of s 23(2)(a) of the Judiciary Act 1903 (Cth) when the Court split 3-3: Aristocrat Technologies Australia Pty Ltd v Commissioner of Patents [2022] HCA 29; 96 ALJR 837. As such, the High Court’s decision has no ratio decidendi and stands only for the proposition that the Full Court’s decision stands. As a single judge, I am bound by that decision. What the Full Court is to make of the High Court’s decision is another matter but the approach for a single judge is clear.
416 No error has been identified in those statements of principle.
417 Hytera has focused on a statement by the primary judge at PJ [358] as to one particular advantage revealed by the 355 patent and asserts that the claims are broader. But we agree with Motorola that the point goes nowhere. The 355 patent at its broadest discloses a method for improving scanning time. That is a manner of manufacture. It is not an abstract idea. The patent discloses and the relevant claims embody a technical means, utilising the structure of data frames by which communications are carried in a digital communications device, by which scanning time can be improved.
418 We consider that no error has been shown in the primary judge’s reasons. We therefore reject this ground of appeal.
B.6 Cross-appeal concerning the 960 patent
Overview of the issues at trial
419 Ground 1 of Motorola’s cross-appeal concerns the validity of the 960 patent which, as noted earlier, has a priority date of 28 July 2005. The primary judge dealt with the 960 patent at [553] to [736] of his reasons.
420 The primary judge found that the invention claimed in claims 1 to 5, 8 to 15, 17 and 18 did not involve an inventive step in light of the common general knowledge before the priority date, together with the 2005 DMR Standard which we have previously identified. Hytera submitted at trial that the 2005 DMR Standard formed part of the common general knowledge as at the priority date. But given that the 2005 DMR Standard was only three months old at that time, the primary judge doubted this. In any event his Honour treated the 2005 DMR Standard as a s 7(3) document.
421 Motorola’s case before the primary judge can be summarised as follows.
422 The invention the subject of the 960 patent is directed to a method of “accessing a base station in a conventional time division multiple access (TDMA) communications system”. In terms of the prior art approach to accessing a base station, each base station or repeater provided synchronization for mobile stations or subscriber units so that each mobile station could use a time slot within the spectrum for communications. We will discuss the subject matter of synchronisation and the use of synchronisation patterns later.
423 Because the spectrum is shared and a finite resource, in given circumstances the base station will de-key, that is, its transmitter will turn off and the downlink will be inactive while the base station uplink remains active and available to detect mobile station transmissions, so that others can use the spectrum. There may be different reasons for de-keying including regulatory requirements to de-key periodically, but one reason is if the base station has not received any transmission from any mobile station for a period. The base station does not notify the mobile station when it de-keys. Instead, the mobile station indirectly determines that the base station has de-keyed, such as by not detecting synchronization patterns from the base station.
424 Once the prior art base station de-keys, and thus stops transmitting synchronisation patterns, it will not retransmit any further transmission it receives from a mobile station because it is assumed the mobile station may not be in synchronisation. Rather, to re-establish an operational connection there are 3 steps that needed to be taken. First, the mobile station needs to send a wake-up message to the base station in order to have the base station re-key. Second, upon receipt of this wake-up message, the base station then sends timing information, that is, the synchronization patterns to the mobile station to allow the mobile station to synchronize to the base station. And third, it is only upon completion of this “wake-up” process that the mobile station can then send a synchronized transmission to the base station which the base station would then repeat.
425 An issue with the prior art, although not one that was considered a problem worth addressing at the time, is that the mobile station might make a transmission after the base station had de-keyed not knowing that the base station had de-keyed, and this transmission would not be repeated and would therefore be lost.
426 According to Motorola, the invention of the 960 patent is to create a new functionality in the base station, referred to in some embodiments as a “temporary de-keyed state”, which begins when the base station de-keys and lasts for a period of time delineated by a timer. During this time period, the base station is not transmitting but remains able to receive and repeat transmissions which it receives with “proper synchronization”, without needing to follow the “wake-up” process of the prior art. According to Motorola, “proper synchronisation” as used in the 960 patent does not mean precise synchronisation, but refers to receipt of the transmission within certain timing boundaries (a “timing window”), that is, received within a defined limit either side of where the transmission would be received if perfectly synchronised. If the transmission is received outside those boundaries, it may be a transmission from a mobile station that was not previously associated with the base station.
427 Motorola says that in an embodiment, the timing boundaries function as a means of determining which transmissions are to be retransmitted. If the temporary de-keyed time period ends without the base station receiving any transmissions with “proper synchronization”, then the base station will require the usual wake-up message and synchronisation process before it can repeat a message received on its uplink.
428 According to Motorola, Hytera’s evidence on inventive step from Mr Kuhrt suffered from a number of difficulties.
429 First, Mr Kuhrt accepted that the problem that Hytera’s solicitors had set for him to solve was not a problem the solution for which he would ever have embarked upon.
430 Second, by the question he was asked by Hytera’s solicitors, Mr Kuhrt was pointed in the direction of coming up with a solution which was concentrated upon the base station, whereas if simply asked to solve the problem of lost transmissions he would have opted for a solution which was based in the mobile station, and involved the mobile station playing a tone to warn the user that the transmission might not be received.
431 Further, the hypothetical task set for Mr Kuhrt incorporated a prompt to find a solution that involved the base station. The task was to develop a repeater for a digital conventional two-way radio system that reduced the risk of a transmission from a mobile station being lost when a repeater de-keys. But according to Motorola, that hypothetical task jumped over the question of whether there was a reason to undertake any improvement task in the first place, and also focused attention on making some improvement to the base station to capture transmissions which would otherwise have been lost because it has de-keyed. But Motorola says that this was a different paradigm from the prior art. Motorola says that this prompt was significant given that Mr Kuhrt would not have attempted to solve the hypothetical question he was asked in respect of the 960 patent, and for technical rather than commercial reasons.
432 Had Mr Kuhrt instead been asked a hypothetical question which was device agnostic, Motorola says that he would have solved the problem in a different way to the invention claimed in the asserted claims. Motorola says that had Mr Kuhrt consulted the 2005 DMR Standard as at the priority date he would have considered any risk of lost transmissions to have been low, because the duration of any such lost transmission would, in Mr Kuhrt’s view, likely be short and the loss could be recovered by implementing a solution in the mobile station, by which the device alerts the user by means of a tone alert, so as to prompt the user to make the transmission again within a short space of time. Motorola says that the 960 patent takes a different approach and instead implements a solution in the base station.
433 Third, Motorola says that even when prompted, Mr Kuhrt came up with a different solution, including the receipt of a mobile station identification code by the base station to identify whether the mobile station was a mobile station previously associated with the base station such that the base station should retransmit the transmission.
434 According to Motorola, the concessions made by Mr Kuhrt in cross-examination should have brought the inventive step case to an end. But the primary judge nevertheless concluded that the invention was obvious. Motorola says that his Honour was in error. First, he considered whether each integer was obvious, rather than the combination of integers. Second, there was a misunderstanding as to the nature of the invention and how it worked, and therefore a flawed conclusion that aspects of the invention were obvious. Third, there was the mixing up of the timing window and the timer. Fourth, there was a misapplication of some evidence given by Professor Wicker, a professor of electrical and computer engineering, who was called by Motorola.
435 We will address these arguments in more detail later.
The primary judge’s analysis of the 960 patent
The problem of the de-keyed base station
436 The primary judge found that, as at July 2005, a known problem concerned the situation which could arise when a base station de-keyed. A base station transmits to subscriber units which are using it on a channel known as the downlink. Apart from any substantive communications from the base station, that is, the payload, the transmissions on the downlink also include synchronisation patterns. A synchronisation pattern consists of a 48 bit sequence which is transmitted in a 5 msec interval contained in the middle of the burst in between payload transmissions. The subscriber units detect the synchronisation patterns and then use them to adjust the timing of their clocks to match that of the base station. By these means, the subscriber units and the base station are able to maintain the timeslot structure inherent in a TDMA system.
437 Because spectrum resources are limited, it is desirable that a frequency not be used if it is not necessary to do so. Accordingly, where a base station determines that there are no subscriber units transmitting to it on the uplink, it turns the downlink off. That is, the base station de-keys. The uplink, by which the base station receives communications from subscriber units, remains on and is able to receive transmissions. However, whilst the base station is de-keyed, it will not repeat any communications received from subscriber units.
438 The base station does not inform the subscriber units that it is about to de-key or even that it has de-keyed. Any subscriber unit which is synchronised to the base station will, in fact, only detect this fact after it notices that it has not received any transmission from the base station for some pre-determined period of time. Some finite period of time is necessary because an instantaneous cessation in transmission from a base station does not inevitably entail that the base station has de-keyed for its transmissions may be momentarily disrupted by a variety of other phenomena. For that reason, a subscriber unit waits some short but pre-defined period of time after it stops receiving transmissions from the base station before concluding that the base station has de-keyed.
439 Once a base station has de-keyed, a subscriber unit is no longer in receipt of the timing signal constituted by the synchronisation patterns. Therefore its clock can no longer confidently be regarded as being in synchronisation with the base station’s clock. This is a consequence of the phenomenon of clock drift. Further, because the base station has been de-keyed, it will no longer repeat any transmissions. A subscriber unit which wishes to initiate a transmission once the base station has de-keyed must bring this state of affairs to an end. It must both cause the base station to start sending synchronisation patterns again on the downlink, so it can synchronise with the base station’s clock, and it must cause the base station to start repeating any transmissions it receives on its uplink. To do this, the subscriber unit sends the base station a “wake-up message”. The wake-up message is what is known as an asynchronous message by which it is meant that it can be received by the base station even if the subscriber unit is not in synchronisation with it, which will be the case in the circumstance that the base station has de-keyed.
440 Once the base station receives the wake-up message, it changes its behaviour on both its downlink and its uplink. The downlink is switched back on and the base station begins to transmit bursts containing the synchronisation pattern but initially with no payload known as “hangtime messages” or “idle messages”. So far as the uplink is concerned, it changes its operating state from being one in which it repeats no transmissions received from a subscriber unit, to a new operating state in which it will repeat any transmissions received from a subscriber unit so long as they are in synchronisation with the base station. These combined steps are together known as re-keying the base station.
441 Once the subscriber unit begins to receive the synchronisation patterns again in the form of the hangtime messages, it is able to use those patterns to synchronise its clock to that of the base station. Once it has done so, it is then able to transmit a communication on the relevant timeslot which will in turn be received by the base station on its uplink and be repeated to other subscriber units on its downlink.
442 A known problem with this intricate arrangement is the possibility that a transmission by a subscriber unit may be lost. The circumstances in which this can occur in a TDMA system are limited. By definition, a base station will only de-key when it forms the view that there is no activity by subscriber units taking place on the relevant frequency. Once it de-keys and stops transmitting synchronisation patterns on the downlink, there is a finite period of time during which it is possible that a subscriber unit may initiate a transmission while it is unaware that the base station is no longer repeating any transmissions it receives on the uplink. This finite period of time is the time set in the subscriber unit after which a failure to receive any synchronisation patterns from the base station is taken to mean that the base station has de-keyed.
443 Once that time has passed the problem disappears because the subscriber unit now knows that the base station is not repeating its transmissions and sends a wake-up message to the base station to bring this state of affairs to an end.
444 Because TDMA systems involve breaking communications into payloads which are transmitted within 30 msec bursts, and because the devices alternatively transmit via the uplink and receive via the downlink, this problem does not persist for very long. In particular, whilst the user may speak into the subscriber unit and in that sense be said to be transmitting, the digital reality is that the subscriber unit is both receiving and transmitting in 30 msec bursts. The failure of the synchronisation patterns to arrive from the base station’s downlink will be detected when the first expected one fails to arrive. The failure of subsequent patterns to arrive will enable the subscriber unit to know quickly that the base station has de-keyed.
445 The 960 patent presented a solution to this problem in TDMA systems. It had three features.
446 First, as normal, when the base station de-keys, it turns off its downlink, and its uplink continues to receive any transmissions which might arrive from a subscriber unit.
447 Second, in doing this it confronts a problem. Because the subscriber unit will, by definition, no longer be receiving the synchronisation patterns from the base station, its clock will have begun to drift out of synchronisation. In the prior art, a transmission from a subscriber unit received on the uplink which was not in synchronisation was ignored. The 960 patent moves away from this. Instead of ignoring transmissions which are received out of synchronisation, the patent introduces an element of flexibility in the base station’s approach to such transmissions. It will receive and repeat transmissions from a subscriber unit on its uplink even after it has de-keyed and even if the transmissions are not precisely in synchronisation with the base station’s clock. It does so by permitting the transmissions to be repeated even if they arrive a little earlier or a little later than the time the base station’s clock would ordinarily expect them to arrive. The latitude implied by the concept of arriving a little early or a little later than the time dictated by the base station’s clock is referred to as a timing window.
448 Third, the base station does not remain in this state for long. Instead, it runs a timer for a period of time. When the timer runs out, the base station fully de-keys. Since the downlink has already been turned off, this is simply a matter of ceasing to repeat any transmissions received on its uplink and waiting instead only for the wake-up message.
449 The effect of these three features is to create what the patent refers to as the “temporary de-keyed” state. Whilst it is in that state, any transmissions from a subscriber unit which arrive are repeated even if they are out of synchronisation so long as they arrive within the timing window. At the same time, when this occurs the base station re-keys. In this way, transmissions from a subscriber unit which are commenced after a base station is de-keyed are not lost.
The 960 patent specification
450 It is convenient at this point to draw on some of the analysis of the primary judge concerning the complete specification for the 960 patent.
451 The field of the invention is described at p 1 lines 4 to 6 as relating generally to wireless communications systems and more specifically to accessing a base station in a conventional TDMA communication system. The specification then explains the background to the invention.
452 Base stations provide synchronisation patterns so that subscriber units can adjust their timing to that of the base station. The timing provided by the base station permits the subscriber units to process the digital communications sent by the base station to the subscriber units. It also permits them to send their transmissions in synchronisation so that the base station can receive them in a similar although not identical fashion. Precise timing permits the establishment of exact timeslots on a single frequency regardless of which kind of device is sending or receiving the transmission. Each timeslot is 30 msec in duration. It will be noted that in mobile stations, 2.5 msec of this 30 msec is dedicated to what is called “guard time” meaning it is not used for the transmission of payload or control information.
453 A “burst” has a total length of 30 msec and is inclusive of guard time (2005 DMR Standard, pp 10, 17). However, there is some ambiguity in the standard about the meaning of “timeslot”. One available view is that, like the burst, it is 30 msec in duration, but that it is in a fixed position that dictates the timing of the channels (2005 DMR Standard, p 12). Another view is that the timeslot is 27.5 msec in duration contained within the burst surrounded by and excluding the 1.25 msec of guard time at the beginning and end of each burst. Support for this view may be found at Figure 4.4 at p 18 of the 2005 DMR Standard which appears to label the substantive transmission of payload and overhead in each burst “Timeslot 1” and “Timeslot 2”. The difference in these two views is not material to the issues which arise, although the primary judge adopted the former view, as we will.
454 Base stations both transmit and receive. When they transmit they are said to do so on the “downlink” but when they receive they are said to do so on the “uplink”. Because the spectrum available is a limited and shared resource, it is desirable to avoid unnecessary transmissions by base stations. For that reason, in a variety of circumstances, base stations turn off their downlink and stop transmitting. One situation where a base station turns off its downlink is when it comes to the view that there are no subscriber units presently transmitting to it on the uplink. Doing so permits the frequency on which the downlink was transmitting to be used by other devices. Whilst the downlink is turned off, the uplink remains turned on so that the base station is still able to receive communications. However, it does not repeat any of the transmissions it receives on the uplink whilst the downlink is off.
455 The process of turning off the downlink when the base station comes to the view that there is no subscriber unit activity to receive is known as “de-keying”, and where a base station has “de-keyed” it is said to be in a “de-keyed” state. Once a base station has de-keyed, before it can transmit again, it must be turned back on. The turning back on of a de-keyed base station is known as “re-keying”. Re-keying occurs when a subscriber unit, realising that the base station is de-keyed, sends the base station a “wake-up message” on the uplink. A subscriber unit which finds it necessary to send a wake-up message necessarily will not have been receiving any transmissions from the base station. This means that it is likely that it will not be in synchronisation with the base station due to the phenomenon of clock drift.
456 The nature of the wake-up message, which is sent to the base station by the subscriber unit, is such that the subscriber unit does not need to be in synchronisation with the base station in order for it to be successfully received by the base station on the uplink. This kind of message is known as an asynchronous message. Synchronisation patterns are another example of asynchronous messages since they too can be detected by devices even if precise timing is not present.
457 Once the base station has received the wake-up message from a subscriber unit it then re-keys and begins to transmit on the downlink. That transmission will include, of course, synchronisation patterns and the subscriber units which receive these transmissions from the base station on the downlink will then be able to synchronise with the base station. Once that is done, communication between the subscriber unit and the base station may take place on the uplink and downlink. At the same time, once the base station has re-keyed, it will repeat transmissions received on the uplink if they are in synchronisation, but ignore them if they are not in synchronisation. The base station judges whether the transmission is in synchronisation by checking to see whether the synchronisation pattern embedded in the burst from a subscriber unit arrives at the time which, according to the base station’s clock, it should arrive. Thus both base stations and subscriber units send and receive synchronisation patterns to each other. However, the reasons they do so are different. The synchronisation pattern sent by a base station tells the subscriber unit what time to adjust its clock to and the subscriber unit obeys. The synchronisation pattern sent by a subscriber unit to a base station allows the base station to check to see whether the subscriber unit is in synchronisation with it. If it is not, then the base station ignores the transmission.
458 As the primary judge noted, this understanding of de-keying and re-keying was reflected in the 2005 DMR Standard which was published in April 2005. There may be some doubt as to whether the 2005 DMR Standard constituted part of the common general knowledge by the priority date of 28 July 2005 but it does not matter given that it is clear that the 2005 DMR Standard is a document to which s 7(3) applies.
459 The specification explained most of what has been set out and the nature of a particular problem which existed with such an arrangement at p 1 line 20 to p 2 line 28:
In a conventional TDMA communications system, each base station (BS) provides synchronization for the MSs, so that the MSs can utilize the spectrum for communication. Once synchronization between the BS and MSs is obtained, each MS can properly receive control signaling that identifies the temporal position of each time slot within the spectrum and the time slot of the spectrum each MS can utilize for communications. Because the spectrum is often shared, the BS normally de-keys when the spectrum is not in use. As is known in the art, de-key (and conjugations of “de-key”) means that the BS’s transmitter is turned off. Further known in the art, de-keyed means that the BS's downlink is inactive while the BS’s uplink remains active and available to detect MS transmissions. When the BS is de-keyed, even though the BS is able to detect transmissions from the MS, the BS may not be able to process the transmissions because the MS may not be in synchronization with the BS. Thus, when the BS is de-keyed, a MS can not utilize the BS for communications until a) the MS sends a wakeup message to the BS which causes the BS to re-key and b) the MS synchronizes to the BS to receive timing information about the BS. After the wakeup and synchronization processes are completed, then a MS may finally utilize the BS for communications.
If the MS believes that the BS is de-keyed (e.g. due to not timely receiving synchronization), then the MS transmits the wakeup message and attempts to synchronize, which takes extra time and thus is undesirable if the MS has to send a wakeup message prior to every transmission. If the MS believes that the BS is keyed (e.g. due to timely receiving synchronization), then the MS does not transmit the wakeup message. In a conventional TDMA communications system, the MS is not explicitly notified that the BS has de-keyed. That is, there is no message that is sent from the BS to the MS that notifies the MS that the BS is about to de-key, de-keying or is de-keyed. In a conventional TDMA communications system, the MS indirectly determines that the BS has de-keyed, such as by not detecting synchronization from the BS. However, there is a finite amount of time that passes before the MS realizes that the BS has de-keyed and during this finite amount of time, if the MS sends communications to the BS, then the communications sent to the BS are ignored by the conventional TDMA communications system since (as mentioned above) the BS requires that the wakeup and synchronization processes be completed before the MS may utilize the de-keyed BS for communications.
Ignoring communications is a problem because the user of the MS does not have knowledge that the communications have not been received by the intended recipient of the communications. For example, if an emergency communication is placed by emergency personnel, as a user of a MS, and the BS is de-keyed, then the emergency personnel is not aware that the emergency communication has not reached its intended recipient, e.g. emergency personnel at a police station. In any case, ignoring communications is a problem.
Accordingly, there is a need for an improved method of accessing a de-keyed base station in a conventional TDMA communications system.
460 So the problem is that the subscriber unit receives no direct notification that the base station has de-keyed and only works this out when, after a while, it has stopped receiving transmissions from the base station. During the period before the subscriber unit realises the base station has de-keyed, the subscriber unit may initiate communications to the base station without realising that the base station is no longer repeating its transmissions. The transmissions which are affected by this problem are only those which are initiated during this period. That they must be initiated follows from the fact that the base station has de-keyed precisely because there was no subscriber unit activity on the uplink. The sending of communications by a subscriber unit which unbeknownst to it are not repeated is undesirable.
461 The problem identified by the patent is the problem of accessing a de-keyed base station in a conventional TDMA communications system: p 2 lines 27 to 28. In essence, it is the problem of capturing transmissions which a subscriber unit makes after a base station has de-keyed but before the subscriber unit has realised that it has de-keyed.
462 Central to the dispute between the parties is the meaning of “proper synchronisation” in claims 1 and 13, which is referred to in the “detailed description” of the patent at p 8 lines 11 to 31 and Figure 3. These are as follows:
As used herein, proper synchronization means that the transmission is received within timing boundaries, also known as a window. Referring to FIG. 3, shown is a timeline 300 for the uplink of a BS. The timeline 300 shows two timeslots 314, 316 and windows of time (namely TEXPECTED) 302 that the BS expects to receive transmissions from the MS. In one embodiment, TEXPECTED is approximately 5 milliseconds. To compensate for delays in transmission, signal propagation delays between the MS and BS, and reference oscillator variability between the BS and the MS, the BS allows for transmissions to arrive earlier and later than the window 302 of TEXPECTED. In one embodiment, TEXPECTED is approximately 7.083 milliseconds. Also, in one embodiment, proper synchronization means that the transmission is received within the window 308 of time termed TWINDOW. In any event, if transmissions are received outside the window 308 TWINDOW, then the transmission is not received with proper synchronization and will not be processed (RxSyncOutOfWindow, Transition 214). For example, a transmission 310 that is received too early is not processed and a transmission 312 that is received too late is not processed where early and late means that the transmission is received outside the window 308 TWINDOW. The assumption is that the MS was not in synchronization with the BS before the BS de-keyed, so the BS does not need to process the transmission because the MS was not properly associated with the MS so the MS [sic: BS so the BS] does not need to re-key to process a transmission from an MS that is not properly associated with the BS.
463 Hytera’s contention is that “proper synchronisation” requires TWINDOW to be less than 7.5 msec.
464 Neither TWINDOW nor TEXPECTED are expressly required by the terms of the claims or the specification to have any particular duration. According to the primary judge, the passage above suggests different embodiments where TEXPECTED is in one case approximately 5 msec (p 8 lines 15 to 16) and in another, 7.083 msec (p 8 line 19). In no embodiment in the specification is there a suggestion for any particular value for TWINDOW. However, it is evident from page 8 lines 16 to 22 that TWINDOW is always longer in duration than TEXPECTED. Indeed, it is the point of TWINDOW to be longer in duration than TEXPECTED. This understanding of the relationship between TWINDOW and TEXPECTED is confirmed by Figure 3.
465 Page 8 lines 22 to 28 and Figure 3 also show that a base station in which the invention is implemented will cause a transmission containing a synchronisation pattern which is received inside TWINDOW to be repeated, but will not do so if the synchronisation pattern is received outside TWINDOW.
466 Although the patent does not refer to the 2005 DMR Standard, the primary judge found and we accept that a person skilled in the art implementing the invention would not do so in a way which did not comply with that standard. Under the 2005 DMR Standard, the structure of a standard TDMA burst was set out at p 18:
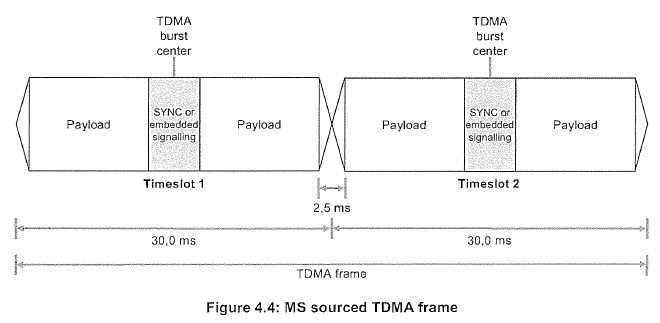
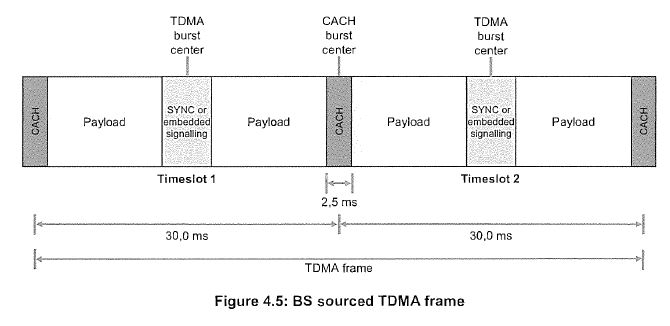
467 It is not in dispute that under the 2005 DMR Standard, the synchronisation pattern or the embedded signalling was contained in a 5 msec interval in the middle of each timeslot. It will be observed that each 30 msec burst consists of a transmission comprising payload and overhead, in the form of the synchronisation pattern, which is 27.5 msec in duration and that after the end and before the beginning of each transmission there is an additional 1.25 msec within the timeslot. When the 1.25 msec at the end of one timeslot is combined with the 1.25 msec at the beginning of the next, a period of 2.5 msec is created. However, the basic frame structure remains the 30 msec burst. Whilst it is true to say that 2.5 msec of each burst is not devoted to the transmission of payload or overhead, it is important to keep in mind that this is a 2.5 msec period split in half with 1.25 msec at the beginning and end of each burst. The practical effect is, however, to leave 2.5 msec between each transmission.
468 It will also be seen that where the transmitting device is a base station, the 2.5 msec is used for the transmission of the CACH message; see Figure 4.5. Figure 4.4 above does not explain what the 2.5 msec is used for in the case of a transmission from a subscriber unit. It was not in dispute however that where a transmission was made from a subscriber unit to a base station this 2.5 msec was used as “guard time”.
469 According to p 16 of the 2005 DMR Standard, the purpose of guard time was to allow for “Power Amplifier (PA) ramping” and “propagation delay”. These concepts are explained in the 2005 DMR Standard (pp 88 and 89). The former relates to the fact that as the transmitter on the subscriber unit is rapidly turned off and on, it takes a very short amount of time for the signal strength to reach an appropriate level. One purpose of the guard time is to allow an interval during which this may occur. The latter relates to the fact that the further away a subscriber unit is from a base station, the longer the radio signal takes to arrive. The timeslots which arrive from a subscriber unit 10 m from a base station will arrive sooner than the timeslots which arrive from a subscriber unit which is 150 km away. Another use of the guard time is to take account of this kind of delay.
470 At trial, Hytera submitted that under the 2005 DMR Standard a small amount of delay, drift or jitter of a transmission within a timeslot was allowed for as at July 2005 by the inclusion of the guard time between each burst. A transmission would remain within the timeslot boundaries if the delay, drift or jitter was less than the amount of the guard time. But the primary judge found that the reference to guard time between a burst was not correct. The guard time is at the end and beginning of each burst and forms part of it. Further, according to his Honour, the phrase “within a timeslot” in Hytera’s submission suggests that any drift occurred within the timeslot. His Honour said that the existence of the guard time as part of the burst structure soaks up any drift or jitter in the transmission. The point of the guard time is to accommodate the early or late arrival of a transmission by an amount up to the guard time.
471 The primary judge accepted, as Hytera had submitted, that the point of the guard time is to avoid the problem of the transmissions which are meant for different timeslots overlapping with each other. The guard time ensures that transmissions which arrive early or late by no more than 2.5 msec do not overlap. But his Honour made a clarification. The guard time is inserted into the burst by the subscriber units, not by the base station. The point of the guard time is to ensure that transmissions from two different subscriber units do not overlap. Although the base station needs to adjust its reality to the fact that the subscriber units are sending transmissions with guard time, so as to permit some drift or jitter, it is not the base station’s recognition of the existence of the guard time that is the cause of that phenomenon. The guard time is set by the subscriber units and not by the base station.
472 Further, as to Hytera’s suggestion that proper synchronisation means that a transmission is received within TWINDOW where TWINDOW is always less than 7.5 msec, the primary judge observed that the patent contains no such express stipulation. His Honour said that it follows that if there is a requirement that TWINDOW should be less than 7.5 msec, it must either arise as a matter of implication from the terms of the patent or as a requirement flowing from the 2005 DMR Standard. Hytera did not submit that the implication arises from the former. Instead, its argument is that it is a necessary incident of the 2005 DMR Standard.
Hytera’s contention that TWINDOW must be less than 7.5 msec in duration
473 The primary judge accepted Hytera’s submission that the purpose of the guard time is to prevent transmissions overlapping each other. The timeslots can be subject to slight drift or jitter. The purpose of the guard time is to ensure that this drift or jitter does not result in a transmission on timeslot 1 from one subscriber unit overlapping with a transmission on timeslot 2 from another. His Honour noted that the overlapping is prevented by the subscriber units transmitting their bursts such that guard time is included. The fact that the bursts transmitted by the subscriber units may arrive up to 2.5 msec early or late is therefore something which the base station must adapt to in deciding whether a transmission has been received in synchronisation. However, whatever criterion is imposed by the base station in that regard has no impact on whether overlapping occurs. In relation to the topic of overlapping transmissions by two subscriber units, the base station is a passive observer.
474 Hytera said that because under the 2005 DMR Standard the synchronisation pattern is 5 msec in duration, TWINDOW could not be permitted to have a value which would allow the transmissions in adjacent timeslots to overlap. Overlapping would occur if the size of TWINDOW exceeded the size of the guard time. Since the synchronisation pattern was 5 msec in duration and the guard time was 2.5 msec in duration, it followed that TWINDOW could never be more than the sum of these two timing intervals, that is to say, 7.5 msec.
475 Since proper synchronisation in claims 1 and 13 meant that a transmission had to be received inside TWINDOW and since TWINDOW had to be less than 7.5 msec by reason of the 2005 DMR Standard, it followed that a transmission would not be received with proper synchronisation within the meaning of claims 1 and 13 unless it was received in a window no larger than 7.5 msec.
476 The primary judge did not accept Hytera’s contention. His Honour reasoned as follows.
477 Under the 2005 DMR Standard the burst for a transmitting subscriber unit includes 2.5 msec of guard time. As the evidence of Professor Wicker showed, a transmission which arrives within the 27.5 msec allotted to it plus or minus the guard time of 2.5 msec is treated by the base station as being received within the timeslot boundaries. The implication of this is that such a transmission is treated as having been received in synchronisation. The concept of being in synchronisation under the 2005 DMR Standard therefore includes an allowance for drift or jitter by up to the amount of the guard time, at least according to Professor Wicker. If this were not so, then Professor Wicker’s evidence would not have made any sense. The guard time would serve no purpose if transmissions which have drifted or jittered by less than the guard time are not repeated. Professor Wicker did not intend to suggest otherwise. Moreover, no part of the 2005 DMR Standard rebutted Professor Wicker’s evidence about the significance of guard time from the base station’s perspective. In that circumstance, his Honour accepted Professor Wicker’s evidence.
478 The primary judge explained that the conclusion that under the 2005 DMR Standard a base station will treat as being in synchronisation a transmission which is up to 2.5 msec early or late is important for two reasons. First, the patent does not specify how large TEXPECTED must be. But in light of what has just been said, TEXPECTED must be 7.5 msec if the invention is to be implemented in accordance with the 2005 DMR Standard, the only possible way it would be implemented. Only if TEXPECTED is 7.5 msec can Professor Wicker’s observations about drift and jitter and the 2.5 msec of guard time be made to cohere with the fact that a synchronisation pattern is 5 msec in duration. Second, this spells the end of Hytera’s contention that the TWINDOW must be less than 7.5 msec. The one thing which is clear from the patent is that TWINDOW is always larger than TEXPECTED. If TEXPECTED must be 7.5 msec it must inevitably follow that TWINDOW must be greater than 7.5 msec. In fact, Hytera’s contention that there must be a 7.5 msec window of some kind is correct. What is erroneous about the contention is its identification of that window as being TWINDOW. In fact, it is TEXPECTED which is required by the 2005 DMR Standard to be 7.5 msec.
479 This left Hytera’s submission that, if this be so, then transmissions from different subscriber units will overlap. Subject to a minor correction, the primary judge accepted this submission but did not believe that it was material in the context of the invention disclosed in the patent.
480 The minor correction is that it is not inevitable that the transmissions will overlap if TWINDOW is greater than 7.5 msec. The context is two subscriber units which have both decided to initiate a transmission after the base station has entered the temporary de-keyed state but before either has worked out that this has occurred. Necessarily, because the base station has entered the temporary de-keyed state it has stopped transmitting synchronisation patterns. In this scenario, the timing of the base station is irrelevant because it does not exist. Any overlapping which occurs will rather be a consequence of the degree to which the clocks of the two subscriber units have drifted out of synchronisation with each other. The occurrence of the phenomenon of overlapping transmissions following the de-keying of a base station therefore involves a domain of discourse in which the clock of the base station is extraneous. All of this will be a function of whether the timing of the two clocks in the two subscriber units drift apart by more than the guard time. This is by no means inevitable. They may drift in opposite directions by an insufficient amount to exceed the guard time cumulatively. They may drift in the same direction.
481 Further, in the context of a de-keyed base station, these transmissions are the very transmissions which the invention disclosed in the patent is designed to catch. This point may be made in two steps. The first step concerns the position under the 2005 DMR Standard. Under the standard, the fact that the transmissions which occur after the base station has de-keyed may overlap with a transmission in an adjacent timeslot is irrelevant. The base station has de-keyed and is ignoring all transmissions which are not the wake-up message received on the uplink. The primary judge observed that, for all the base station cares, the subscriber units which have initiated a transmission after it has de-keyed may be playing the theme from the Pink Panther. If the transmissions overlap, the base station is stolidly indifferent. This underscores that any overlapping which occurs is driven by the behaviour of the subscriber units and is unrelated to the attitude of the base station.
482 The second step concerns the invention disclosed by the patent. Where two subscriber units initiate transmissions after the base station has entered the temporary de-keyed state their relative clock drift may, or may not, exceed 2.5 msec. Assuming that the drift does exceed 2.5 msec and therefore that overlapping occurs, it is difficult to see what the base station can do about this. In particular, a decision by a base station to assign a different value to the guard time from that which the subscriber units are using has no impact on the guard time they are using. More bluntly, if the base station was set so that it assumed the transmissions from the subscriber units included 5 msec of guard time this would have no impact on the subscriber units which would continue to transmit with 2.5 msec of guard time. All that would be present in that scenario would be an incorrect assumption.
483 Consequently, the primary judge did not accept the unstated assumption in Hytera’s submission that how the base station approaches the guard time has any impact on whether timeslots will overlap with each other.
484 For completeness, the primary judge rejected Hytera’s submission that a delayed transmission from a subscriber unit will result in the base station repeating that transmission in a delayed fashion. Any transmission received by a base station which it decides to repeat is retransmitted in accordance with its own timing and is by definition always in synchronisation.
485 Consequently, whilst the primary judge accepted that the fact that TWINDOW must be longer than 7.5 msec in duration may lead to situations where transmissions overlap, his Honour did not think that this amounts to any more than a wrinkle, as his Honour described it. The word “wrinkle” is appropriate because the circumstances in which an overlap can occur are confined by the necessity for several things to happen. First, the two subscriber units using the frequency have not transmitted on either timeslot for a sufficiently long period of time for the base station to conclude that there is no activity on the uplink. Second, the base station enters the temporary de-keyed state. Third, whilst in that state, both subscriber units initiate communications and send a transmission on each timeslot. And fourth, the time drift between their two clocks caused by the non-receipt of synchronisation patterns from the base station has developed sufficiently far in the time before the subscriber units realise that the base station has de-keyed, and in the correct direction by a sufficient amount of time, to cause their transmissions to overlap.
486 The primary judge was not taken to any evidence about how prevalent this problem would be. He inferred that it was a function of at least the size of TWINDOW. But TWINDOW itself is delimited in a practical sense by the time it takes for the subscriber units to work out that the base station has de-keyed, there being no point pursuing these transmissions once the wake-up message has been sent. An assessment of the magnitude of the problem would therefore require an assessment of how far two clocks can drift apart in that time. His Honour did not apprehend either party to make any factual submissions about this.
487 Consequently, whilst the primary judge accepted that having a value for TWINDOW which is greater than 7.5 msec may lead to an overlapping of transmissions from subscriber units, he was unable to conclude that this is anything other than a possible downside of the invention or a wrinkle.
488 The primary judge therefore rejected Hytera’s contention that for a transmission to be received with proper synchronisation in claims 1 and 13 it must be received within a 7.5 msec window.
Figure 3
489 In the primary judge’s view, Figure 3 established two propositions only. First, TWINDOW is always longer than TEXPECTED. Second, transmissions which are received where the synchronisation pattern falls within TWINDOW will be repeated but those which do not will not be repeated.
490 His Honour said that any further use of Figure 3 was inappropriate because it contained serious errors. First, the timeslot 314 is a different size to the timeslot 316 which is impossible in any TDMA system. Second, the bursts which are illustrated are different sizes, also an impossibility in any TDMA system. Third, Figure 3 suggests that TEXPECTED is the same size as the synchronisation pattern which, whilst possible in a vacuum, is not possible under the 2005 DMR Standard. A person implementing the invention in the patent would know that TEXPECTED had to be 7.5 msec wide to comply with the 2005 DMR Standard and that the invention could not be implemented as Figure 3 suggests. His Honour said that the first and second errors make any attempt to draw conclusions about timeslot boundaries from Figure 3 a forlorn escapade.
491 Hytera relied on the evidence of Professor Viterbo to suggest a redrawing of Figure 3 which Motorola then annotated with its own suggestions. But the primary judge said that both seemed to be hopeless enterprises. His Honour took, as he saw it, the better course of extracting from Figure 3 only matters which could be found in the text of the specification.
The reference to TEXPECTED being 7.083 msec
492 Finally, and related to the attempted redrawing of Figure 3 by Professor Viterbo, Hytera submitted at trial that the reference at p 8 line 19 to TEXPECTED being 7.083 msec was erroneous and should be taken to be a reference to TWINDOW.
493 Professor Wicker denied this. As he explained, if it were a reference to TWINDOW then what is at p 8 line 21 is out of sequence for it is only at that point that TWINDOW is defined.
494 In fact, the problem Hytera confronts with p 8 line 19 referring to TEXPECTED being 7.083 msec is that it draws attention to the fact that TEXPECTED need not be the same size as the synchronisation pattern and therefore invites attention to the question of whether, in the context of the 2005 DMR Standard, the guard time is to be accounted for in TEXPECTED or in TWINDOW. As his Honour said, Hytera is right that the guard time must be brought to account but wrong about where it is to be brought to account.
495 Finally, an implementation of the invention which complied with the 2005 DMR Standard would require TEXPECTED to be 7.5 msec. The reference to TEXPECTED being 7.083 msec in one embodiment would be an implementation of the invention which was non-compliant with the standard. The same may be said of the fact that Figure 3 suggests that TEXPECTED is the same size as the synchronisation pattern. The fact that the specification refers to embodiments which are not compliant with the standard does not impact on these conclusions.
The claims
496 Before proceeding further it is appropriate to set out claims 1, 2, 8 and 13:
1. In a conventional TDMA communications system, wherein the conventional TDMA communications system includes at least one base station and at least one mobile station, a method of accessing a de-keyed base station including:
de-keying a base station in the conventional TDMA communications system;
starting a timer in the base station when the base station de-keys;
receiving a transmission from a mobile station; and
re-keying and repeating the transmission, if the transmission is received with proper synchronization before expiration of the timer.
2. The method of claim 1 wherein proper synchronization comprises receiving the transmission within timing boundaries.
…
8. The method of any one of the preceding claims further comprising ignoring the transmission, if the transmission is received without proper synchronization before expiration of the timer.
…
13. In a conventional TDMA communications system, wherein the conventional TDMA communications system includes at least one base station and at least one mobile station, a method of accessing a de-keyed base station including:
at a base station in the conventional TDMA communications system:
entering a temporary de-keyed state;
remaining in the temporary de-keyed state for a period of time;
receiving a transmission from a mobile station while in the temporary de- keyed state; and
entering a repeat state, if the transmission is received with proper synchronization while in the temporary de-keyed state.
497 At trial Motorola placed some reliance on claims 2 and 8, but the primary judge did not think that claims 2 and 8 impacted on the construction issues. It is plain that claim 1 includes the concept of a timing boundary. The reference to timing boundaries in claim 2 is therefore otiose but this is not a problem. Likewise, his Honour regarded Motorola’s reliance on claim 8 as marginal at best. The concept of “without proper synchronisation” is the obverse of “with proper synchronisation”. He did not think it added to the picture.
498 We will return to questions of construction later.
The primary judge’s findings on common general knowledge
499 We now turn to the primary judge’s findings on the common general knowledge before July 2005.
Synchronisation and synchronisation patterns
500 It was known how subscriber units synchronised to keyed repeaters and that, without a timing signal (the synchronisation pattern) from a base station on the downlink, subscriber units would drift out of synchronisation. It was known that base stations have a clock and that this clock is used to set the timing boundaries of each repeating frame on the downlink.
501 Each TDMA frame is 60 msec in duration and is made up of two continuous 30 msec timeslots. Within the first timeslot was a 30 msec burst, 27.5 msec of which was a transmission made up of payload and overhead. The second transmission, also of 27.5 msec duration was contained in the second burst within the second 30 msec timeslot. At the beginning and end of each burst was 1.25 msec of guard time. In practical terms, therefore, the frame contained two transmissions separated by 2.5 msec of guard time. At the front and back end of the frame were two 1.25 msec intervals of guard time. When two consecutive frames are considered next to each other these 1.25 msec periods also mean that a transmission in one frame was separated from a transmission in the next frame by 2.5 msec.
502 In the middle of each 27.5 msec transmission there was a period of 5 msec which was used either for the synchronisation pattern or for embedded signalling information. The subscriber unit synchronises to the base station’s timing by recognising the synchronisation pattern that is embedded in the base station’s transmission on the downlink. The timing of the system was always dictated by the base station and never by the subscriber units. In this sense, the base station was the timing master. Subscriber units would synchronise with a base station but not vice versa. The effect of the base station being the timing master is that the subscriber units using the base station were operating with the same timing.
503 Nevertheless, where a subscriber unit in repeater mode transmitted a burst, it too would embed in each transmission a synchronisation pattern. The purpose of this pattern was not, however, to permit the base station to synchronise with the subscriber unit. Rather, it was used by the repeater to determine whether the subscriber unit’s transmission on the uplink was synchronised to that of the base station. The base station would do so by checking to see whether the synchronisation pattern was received within the period of time during which the base station’s clock dictated that it should arrive.
504 Hytera submitted at trial that it was part of the common general knowledge that the reason the base station checked the synchronisation pattern in this way was to ensure that subscriber units did not interfere with one another on the uplink when they simultaneously transmitted on it. The primary judge did not accept this submission. The evidence for it was said to consist of three elements.
505 The first element was some evidence of Professor Wicker and Professor Viterbo, which the primary judge set out. His Honour did not accept that this established that the reason the base station checks the synchronisation pattern is to ensure that the subscriber units do not interfere with each other on the uplink.
506 The second element was evidence given by Mr Kuhrt. Mr Kuhrt said that the repeater sets the timing and by these means ensures that the subscriber units are operating on the same timing reference without conflicting with one another. However, this is a statement about the purpose of the base station’s transmission of its synchronisation pattern on the downlink, not a statement about why the base station checks the synchronisation pattern on the uplink. His Honour did not accept therefore that this evidence made good Hytera’s submission.
507 The third element of evidence was said to be in Mr Kuhrt’s second affidavit. But the relevant paragraph did not contain any evidence to support Hytera’s submission.
508 The primary judge found that there was no evidence therefore to support the proposition that it was common general knowledge that the reason the base station checked the synchronisation pattern embedded in the subscriber unit’s transmission was to ensure that subscriber units did not interfere with each other by intruding on each other’s timeslots.
509 As the primary judge explained when dealing with the construction question, the receipt by the base station of transmissions on its uplink has no impact on the behaviour of the subscriber units which will continue to transmit until they become aware that the base station has de-keyed. During that period the subscriber units will transmit according to their own clock. If the clocks of two subscriber units have drifted sufficiently such that their timeslots are overlapping then that will occur. Nothing the base station does by receiving transmissions on its uplink during this period can have any impact on this because the base station is not transmitting a timing signal on the uplink (by definition because it is the uplink) and because, in this scenario, the downlink is turned off. His Honour therefore rejected Hytera’s contention.
510 On the other hand, the primary judge accepted that it was common general knowledge that if the subscriber unit’s transmission received on the uplink was synchronised with the base station’s clock, it would be repeated, otherwise it would be ignored. The purpose of the base station checking whether a transmission received on its uplink was in synchronisation was therefore to act as a criterion by which the base station would decide whether to repeat the transmission. In synchronisation transmissions would be repeated; out of synchronisation transmissions would not. Nor is it the case that the decision by the base station not to repeat transmissions can be seen as a mechanism which prevents the out of synchronisation message being repeated by the base station as a further transmission which is not in synchronisation. Where a base station repeats a transmission it does so in accordance with its own timing. The timing of that transmission has nothing to do with the timing with which it is received by the base station.
511 Consequently, the decision by a base station either to repeat or not repeat a transmission on the basis of its synchronisation status has nothing to do with ensuring that subscriber units do not transmit communications in such a way that transmissions in adjacent timeslots overlap with each other.
Drift
512 For various reasons, once a subscriber unit stops receiving transmissions from the base station on the downlink, its clock begins to drift out of synchronisation with the clock of the base station. How long it takes a subscriber unit to drift out of synchronisation depends on a range of factors. These include the quality of the hardware but other factors can affect it as well. The period involved may be less than a second but can be up to a few seconds.
The de-keying of a base station and the sending of wake-up messages to re-key it
513 Base stations may de-key for a number of reasons. One of those reasons is because no subscriber unit is presently transmitting on the uplink. When this occurs, the base station begins a fixed timer referred to as a “hangtimer”. If no transmissions are received by the expiry of the hangtimer then the base station de-keys.
514 The consequences of the base station being de-keyed are that the transmitting downlink is turned off, the base station’s clock continues to operate, and the base station’s uplink remains on and able to receive transmissions. However, whilst it remains able to receive transmissions, the base station does not repeat them. The only transmission which it will act upon is the asynchronous wake-up message prompting it to re-key. When the base station is re-keyed, the downlink is reactivated by turning it on and it begins to send transmissions, which contain synchronisation patterns. At the same time, the uplink will receive transmissions and repeat those which are in synchronisation.
515 A de-keyed base station is re-keyed when it receives a wake-up message from a subscriber unit. This is a message which can be received by the base station from a subscriber unit even though they are not in synchronisation. The wake-up message is sent by the subscriber unit when it has determined that the base station has de-keyed. It sends the message when it wishes to send a transmission. It cannot send that transmission until it has synchronised to the base station. Once the base station receives the wake-up message it turns its transmitter back on and starts sending transmissions which contain synchronisation patterns. Once the subscriber unit detects these synchronisation patterns it is then able to adjust its clock and having done that it may transmit to the base station in synchronisation. This method of re-keying a de-keyed base station formed part of the 2005 DMR Standard.
Timers
516 The base station used a timer (the hangtimer) to determine when it should de-key. The temporary de-keyed state disclosed in the patent involves the use of a timer as well. This timer determines how long the base station remains in the temporary de-keyed state before entering the fully de-keyed state. The use of a timer in this particular fashion was not part of the common general knowledge as at July 2005 and did not form part of the 2005 DMR Standard.
517 However, the use of timers in two-way digital radio mobile communications was well-known at this time. Timers were used, inter alia, to transition between states. The use of timers was a well-known building block for communications systems. One use of a timer is to bring to an end an algorithm. It is good engineering practice only to operate algorithms as long as they are needed. There were at least two reasons for this. First, an algorithm requires system resources to operate, as Mr Kuhrt explained in his evidence. The operation of an unneeded algorithm involves a waste of system resources. Second, the longer an algorithm runs, the more prone to error it is. Timers were a well-known way of terminating the operation of an algorithm and avoiding these problems.
The risk of ignored communications
518 It was also common general knowledge that there was a risk of a transmission made by a subscriber unit being ignored by a base station if it had de-keyed and the subscriber unit had not yet become aware of this fact. In a TDMA system, as opposed to an FDMA system, the risk was known to exist only for a finite period of time. This period of time began when the base station de-keyed and ended when the subscriber unit detected that the base station had de-keyed. It would detect that the base station had de-keyed when it had not received a transmission from the base station for some period of time. Because in a TDMA system the subscriber unit rapidly alternates between sending and receiving 30 msec bursts, a subscriber unit could detect that a base station had de-keyed even if the user was in the middle of speaking.
519 In practice, therefore, the problem manifested itself in a minimal fashion. The time it took for the subscriber unit to detect that the base station was de-keyed was typically small (<1 sec). If the subscriber unit sent the wake-up message immediately, the loss of transmission was of a similar order.
520 It is then necessary to mention the position in relation to FDMA systems. FDMA systems had existed since the 1990s when the P25 Standard was introduced. By contrast, the 2005 DMR Standard for TDMA systems had only been issued in 2005. FDMA split a 12.5 kHz channel into two smaller 6.25 kHz channels which could both be used for communications. In FDMA systems, a base station would also de-key after a period of no activity by subscriber units. However, because the transmission by the subscriber units was continuous on the frequency, and the subscriber unit could not receive at the same time that it transmitted, there was no way in which the subscriber unit could determine that the base station had ceased transmitting until after the user had completed their full transmission. As a result, for example, if the user continued to talk for 30 seconds after the base station had de-keyed, the subscriber unit would not know it had done so until the user stopped talking. The whole of the 30 second transmission would be lost.
521 The de-keyed base station problem was therefore a significant issue with FDMA systems but was a “minor” problem with TDMA systems. Mr Kuhrt acknowledged this. On the other hand, he and Professor Wicker both thought that it was nevertheless a real problem in the context of first responders in TDMA systems. Mr Kuhrt did not consider that as at July 2005 there was any technical motivation to solve the problem. It was not a large problem and its resolution was not a burning objective of those working in the DMR field.
Motorola’s cross-appeal on inventive step
Motorola’s submissions
522 Under ground 1 of its cross-appeal, Motorola makes a number of challenges to the primary judge’s reasoning and conclusions.
523 Motorola says that the primary judge erred in his assessment of inventive step by having regard to whether particular integers considered alone were obvious, rather than considering whether the combination claimed in the asserted claims was obvious. We note that it is impermissible to take any one integer or take each integer separately and ask whether each integer involved an inventive step (Aktiebolaget Hässle v Alphapharm Pty Limited (2002) 212 CLR 411 (Alphapharm) at [60] to [72]). It is common ground that the asserted claims of the 960 patent comprise a combination of integers. As such, the relevant question under inventive step in this case is whether the combination claimed as a whole is obvious in the requisite sense.
524 Motorola says that the primary judge’s impermissible approach in this regard manifested itself in a number of ways. The primary judge accepted that Mr Kuhrt would not, without prompting by Hytera’s solicitors, have utilised a solution centred on the base station, and instead would have implemented some change to the operation of the mobile station. However, his Honour then referred to Professor Wicker’s alternative solution, which involved the sending by the base station of a control message to the mobile station indicating that it was de-keying. The primary judge observed that it was notable that Professor Wicker thought it obvious to use a solution which centred on the operation of a base station. The primary judge then concluded that because Professor Wicker’s very different solution involved the use of a base station, the use of a base station was obvious. His Honour observed (at PJ [718]):
I think it notable however, that Professor Wicker thought it obvious to use a solution which centred on the operation of a base station. It is notable because it detracts from Motorola’s submission that Mr Kuhrt had been nudged in the direction of using a base station to achieve the solution. It detracts from that submission not because it shows that Mr Kuhrt was not nudged in that direction. Rather, it shows that the nudging is irrelevant because using a base station to solve the problem was obvious.
525 Motorola says that that approach involves error. Motorola says that it is inconsistent with Alphapharm. It takes the use of the base station by Professor Wicker out of all necessary context, that is, the base station sending a control message, and finds that that integer considered alone is obvious, before turning to consider other integers.
526 Motorola says that the error by the primary judge was reinforced by his Honour’s observation that Motorola did not submit that “the idea of using a solution in the base station was itself part of what was inventive about the patent” (PJ [721]). On a proper approach, there is no call or occasion for such a submission. Motorola submitted that the combination claimed by the 960 patent was inventive, which combination included the process being implemented in the base station.
527 Motorola says that the primary judge likewise considered whether other integers, considered alone, were obvious. The “idea of using a margin of error” was considered. The idea of using a timer was considered. But Motorola says that his Honour did not consider whether the combination was obvious.
528 The primary judge said at PJ [722] and [723]:
I therefore accept that the idea of using a margin of error (which is equivalent to TWINDOW in the patent) was obvious to Mr Kuhrt. That it was obvious is also borne out by the evidence of Professor Wicker who accepted that to the state the problem of lost transmissions was to state the solution: not to lose them. There is only one way that transmissions which are not in synchronisation with a base station may not be lost. That is for the base station to receive and process transmissions which are not in synchronisation. This inevitably leads to the timing window or, as Mr Kuhrt referred to it, a ‘margin of error’. No other possibility exists. Mr Kuhrt thought that the idea of using the margin of error was obvious. I accept that evidence.
I also accept, for the reasons I have given, Mr Kuhrt’s evidence that it was obvious to use a timer to delimit how long the process of receiving out-of-synchronisation transmissions was to persist. Indeed, Mr Kuhrt’s evidence went somewhat further. The use of the timer was not just obvious. It was inevitable.
529 Further, Motorola says that his Honour engaged in a process the subject of criticism in Lockwood Security Products (No 2) at [51] and [111]. Motorola says that the question is not a question of what is obvious to the court. The primary judge proceeded on the basis that if the problem was identified as a problem that transmissions may be lost, and if it is understood that mobile stations not receiving synchronisation patterns from the base station may drift in their timing away from the base station, then it was obvious that in order to avoid losing transmissions the base station will need to repeat “out-of-synchronisation” transmissions.
530 The primary judge said (at PJ [578]):
As I will explain in more detail, I accept Hytera’s submission that the combination of: (a) allowing a de-keyed base station some latitude in its receipt of out-of-synchronisation transmissions; with (b) a timer to delimit how long this process went on, was not inventive. Although I accept that Mr Kuhrt was pushed in the direction of considering the problem from the perspective of a base station, I do not think that this detracts from his evidence that it was obvious to give the base station some latitude in receiving out-of-synchronisation transmissions. To state the problem was, in this case, to solve it. So too, it was inevitable that a timer had to be applied to the process if only because there was no point running the process beyond the time after which the subscriber unit would have determined that the base station had de-keyed. I do not accept that Mr Kuhrt’s evidence that he would have used a timer was tarnished by the intercession of Hytera’s solicitors. What his evidence in fact established was that he had left it out because it was so obvious it went without saying and did not appear to be material to any of the issues of design. Motorola made a virtue of this evidence by submitting that it showed that Mr Kuhrt’s timer served an entirely different purpose to the timer in the patent. In any event, as I explain in more detail later, I accept that Mr Kuhrt always had a timer in mind and that his evidence in that regard was not prompted by Hytera’s solicitors. I do not accept that Professor Wicker’s evidence affects this outcome.
531 The primary judge also stated (at PJ [722]):
I therefore accept that the idea of using a margin of error (which is equivalent to TWINDOW in the patent) was obvious to Mr Kuhrt. That it was obvious is also borne out by the evidence of Professor Wicker who accepted that [to state] the problem of lost transmissions was to state the solution: not to lose them. There is only one way that transmissions which are not in synchronisation with a base station may not be lost. That is for the base station to receive and process transmissions which are not in synchronisation. This inevitably leads to the timing window or, as Mr Kuhrt referred to it, a ‘margin of error’. No other possibility exists. Mr Kuhrt thought that the idea of using the margin of error was obvious. I accept that evidence.
532 But Motorola says that there are a number of difficulties with this reasoning.
533 First, Motorola says that it appears to be based on a misunderstanding of the invention and the relevance of the “timing window”. It proceeds on the footing that the invention is simply for the base station to repeat out-of-synchronisation transmissions. But according to Motorola, that is not how the invention works. It ignores the integer of re-keying and repeating the transmission if it is received with “proper synchronisation”. Rather, so Motorola says, the invention involves the defining of a timing window to distinguish between different types of out-of-synchronisation messages. The skilled addressee would select the size of the timing window with an eye to appropriately delineating which out-of-synchronisation transmissions should be retransmitted. Various considerations would inform that choice, including how far out of precise timing the mobile station would be likely to drift once it loses its timing “beat”.
534 Motorola says that if the base station merely repeated all out-of-synchronisation transmissions it might repeat transmissions from mobile stations that were not associated with the base station and not part of the system, for example, rather than retransmitting transmissions from security personnel in a particular government building, the base station might retransmit a transmission from a mobile station that just happened to be driving past the building. Motorola says that the prior art required ongoing synchronisation, and therefore required a wake-up message and the re-establishment of a synchronised system. The invention of the 960 patent recognises an alternative whereby the base station would, for a certain time period, repeat transmissions received with proper synchronisation, that is, within a timing window.
535 Second, Motorola says that it is incorrect to say that the only way that transmissions may not be lost is to receive and process transmissions which are not in synchronisation, that this inevitably leads to the timing window, and that no other possibility exists. Motorola says that the concept of receiving “out-of-synchronisation” transmissions does not lead to a window, let alone do so “inevitably” (PJ [722]). It merely leads to the base station receiving out-of-synchronisation messages. For example, the base station could simply receive all transmissions without checking for proper synchronisation. Further, Motorola says that the fact that Mr Kuhrt’s solution used an identification code to determine whether the mobile station was previously associated with the base station shows that other possibilities most certainly exist. Adopting Mr Kuhrt’s identification code, Motorola says that one could dispense with the timing window altogether, and have the base station simply retransmit transmissions that arrive with the correct mobile station identification code. Motorola says that these errors by the primary judge caused his Honour’s assessment of inventive step to miscarry, and caused him to substitute his own conclusion that the invention was obvious even when the evidence of Hytera designed to prove that it was obvious did not do so.
536 Third, Motorola says that Professor Wicker did not say that the combination of integers of the 960 patent was obvious, or even that the timing window was obvious. Professor Wicker was asked whether, if the problem is that a transmission from a previously synchronised mobile station is ignored by the repeater, the solution is to program the repeater in a way that causes the transmission that otherwise would be ignored to be repeated. He said:
MR BURGESS: Thank you. Now, I wanted to return to the problem itself for a moment. The problem, as I think you agreed earlier, is that a transmission from a previously synchronised mobile station is ignored by the repeater; correct?
PROF WICKER: That’s right.
Q: And is this fair: it’s an inherent part of that problem that the solution is to program the repeater in a way that causes the transmission that would otherwise be ignored to be repeated; correct?
A: Yes. The – generally speaking, the solution to having a transmission lost would be to not lose it, in other words, to repeat it - - -
Q: Thank - - -
A: - - - to ensure that it reached its destination.
Q: Thank you. And that is what Mr Kuhrt’s second algorithm achieves; correct?
A: As you have characterised it, yes.
537 Professor Wicker said that the solution to having a transmission lost would be not to lose it and to repeat it. But that did not identify how that would be effected. And he did not accept that the use of a timing window, which could potentially discriminate between different types of out-of-synchronisation transmissions, was obvious. Motorola says that his Honour’s approach seems to have overlooked the claim language being “re-keying and repeating the transmission, if the transmission is received with proper synchronisation”. Motorola says that the primary judge was wrong to conclude at PJ [578] and [722] that the mere statement of the problem, that is, not to lose a transmission from a previously synchronised mobile station, was to solve it.
538 Fourth, Motorola says that the primary judge’s reasoning did not address why the combination of integers was obvious. In this regard, in addition to matters identified by the primary judge, the integers included the base station changing its behaviour to re-keying and repeating a transmission after de-keying, without the mobile station first sending a wake-up message to the base station. As the 960 patent notes, the invention improves the efficiency and reliability of conventional TDMA systems by not requiring the mobile station to transmit a wake-up message and resynchronise to the base station downlink before beginning its transmission. Contrastingly, in the prior art, once a base station has de-keyed it will no longer repeat transmissions from a mobile station until the mobile station first sends a wake-up message to the base station, and then the mobile station also synchronises with the base station. Motorola says that the primary judge did not analyse all integers in terms of inventive step, let alone why the combination was obvious.
539 Fifth, Motorola says that his Honour’s analysis fails to grapple with the consequences of Mr Kuhrt’s evidence.
540 Sixth, Motorola says that the primary judge mixed up the use of a timer and the use of a timing window in the combination of the 960 patent (PJ [680], [725] to [730]). Motorola says that the “timing window” in the 960 patent is a period of time within which the synchronization pattern is to fall so that the base station can determine it is received with “proper synchronisation” and then re-key and repeat the transmissions. This is a different concept to the “timer” described in the 960 patent: “the temporary de-keyed state timer is set to a maximum time that it takes for the MSs [mobile stations] in the cell to determine that the BS [base station] has de-keyed” (p 8 lines 7 to 10).
541 The primary judge stated (at PJ [680]) that Motorola submitted that the purpose of the timer was to determine whether the subscriber units whose transmissions are received within the margin of error are from subscriber units which were previously in synchronisation. Motorola says that that is incorrect and no such submission was made. His Honour was confusing the timer with the timing window. His Honour said at PJ [680]:
Hytera then took these two time limits (perhaps not distinguishing them) and submitted that it was also obvious to a person skilled in the art that algorithms only operated for the period of time for which they were required. I accept this principle was CGK. Combining the two time limits mentioned in the preceding paragraph with the principle mentioned in this one, it followed, according to Hytera, that it was obvious to use a timer to ensure that the checking for slightly out-of-synchronisation transmissions only persisted for a period of time. I will return to assess this proposition in due course. However, for the purposes of that discussion, it is useful now to note that Hytera’s proposition that it was obvious to use a timer rests on an idea of what the timer was to be used for, namely, to prevent the base station from engaging in pointless activity. As will be seen, Motorola submits that the purpose of the timer in the patent is quite different, namely, to determine whether the subscriber units whose transmissions are received within the margin of error are from subscriber units which were previously in synchronisation.
542 Motorola says that the same error is made by the primary judge at PJ [725] to [730] where, following a discussion about the use of the timing window to identify whether transmissions are from a subscriber unit with which the base station was formerly communicating, his Honour then refers to passages in the specification about the timer, and says that they are inconsistent with the timer being used for identification purposes. But nobody was suggesting that the timer was being used for identification purposes.
543 Motorola says that the mixing up of these different things, being the timing window and the timer, caused his Honour to fail to understand or to grapple in a proper way with Motorola’s submission that the timing window (not the timer) may delineate which transmissions would be received with “proper synchronisation” and thus retransmitted – not by way of “determining” which transmissions were previously associated with the base station. Further, Motorola says that it caused a miscarriage in the assessment of the distinction between the solution of Mr Kuhrt, which used a mobile station identification code to determine whether the transmission would be repeated, and the solution of the 960 patent. Although Mr Kuhrt’s solution also had a timing window, the combination of a timing window and an identification code functions in a different manner to the use of a timing window alone. The choice of the size of the timing window by the skilled addressee would likely be different. For Mr Kuhrt’s solution, the skilled addressee could afford to choose a much larger window because only transmissions with an identification code match would ultimately be transmitted. Mr Kuhrt’s solution operated in a different way.
Consideration
544 The particular scenario with which the 960 patent is concerned, which involved the de-keying and re-keying of a base station, was the following.
545 It was well accepted by the parties that in the prior art, a base station would de-key, which involved it turning off its downlink and ceasing to repeat transmissions from subscriber units, if it determined that no subscriber units were transmitting to it on its uplink. In that de-keyed state, the base station would continue to receive transmissions on its uplink, but the base station would not repeat them on its downlink. This would remain the case until a subscriber unit sent a wake-up message, being a message which would cause the base station to re-key by turning on its downlink and repeating transmissions from subscriber units. As was common ground, this arrangement meant that there was a small but finite period of time within which a transmission from a subscriber unit might be lost before a wake-up message was sent causing the base station to re-key.
546 The solution to this so-called problem presented in the 960 patent was to cause the base station to re-key and repeat a transmission from a subscriber unit if the transmission was received with proper synchronization during the small but finite period of time when the base station was in the temporary de-keyed state. The primary judge concluded that this was obvious. As his Honour said, “[t]o state the problem was, in this case, to solve it”; and the features of the claims were “so obvious it went without saying” (at PJ [578]). In our view, Motorola has not shown his Honour to be in error in this overall assessment, irrespective of any infelicities in his reasoning.
547 In considering the present challenge it is necessary to have regard to the primary judge’s findings as to the technical background and the common general knowledge at the priority date of the 960 patent, being 28 July 2005. In summary, his Honour described the concepts of synchronisation, de-keying and re-keying, and the use of alternating timeslots in TDMA systems before the priority date. His Honour also made findings regarding the 2005 DMR Standard which was applicable at the priority date. And his Honour found that a skilled person implementing the 960 patent would not do so in a way which did not comply with the 2005 DMR Standard. We have set out some of the detail of his Honour’s consideration earlier.
548 Motorola asserted claims 1 to 5, 8 to 15 and 17 and 18 of the 960 patent, but for present purposes it is sufficient to focus on claim 1, as the primary judge did. Claim 13, the other independent claim, has similar features.
549 It is not in doubt that obviousness is quintessentially “a question of fact” or “a kind of jury question”, which should be treated with appropriate respect by an appellate court (see Lockwood Security Products (No 2) at [51]). In our view, the primary judge’s finding of obviousness in relation to the 960 patent did not involve any operative error such as to justify disturbing his Honour’s over-all conclusion. The decision was open on the evidence.
550 Claim 1 defined “a method of accessing a de-keyed base station” including, as Hytera points out, four steps, being: (a) de-keying the base station; (b) starting a timer when that occurs; (c) receiving a transmission from a mobile station (that is, a subscriber unit); and (d) re-keying and repeating the transmission “if the transmission is received with proper synchronization before the expiration of the timer”.
551 The primary judge approached the question of obviousness on the basis that the invention involved “the idea of allowing a de-keyed base station to receive out-of-synchronization transmissions” (at PJ [580]). His Honour correctly held that that idea was obvious, and that a method for doing so would inevitably have to be delimited by a timer as required by the claim. He said (at PJ [578] to [580]):
As I will explain in more detail, I accept Hytera’s submission that the combination of: (a) allowing a de-keyed base station some latitude in its receipt of out-of-synchronisation transmissions; with (b) a timer to delimit how long this process went on, was not inventive. Although I accept that Mr Kuhrt was pushed in the direction of considering the problem from the perspective of a base station, I do not think that this detracts from his evidence that it was obvious to give the base station some latitude in receiving out-of-synchronisation transmissions. To state the problem was, in this case, to solve it. So too, it was inevitable that a timer had to be applied to the process if only because there was no point running the process beyond the time after which the subscriber unit would have determined that the base station had de-keyed. I do not accept that Mr Kuhrt’s evidence that he would have used a timer was tarnished by the intercession of Hytera’s solicitors. What his evidence in fact established was that he had left it out because it was so obvious it went without saying and did not appear to be material to any of the issues of design. Motorola made a virtue of this evidence by submitting that it showed that Mr Kuhrt’s timer served an entirely different purpose to the timer in the patent. In any event, as I explain in more detail later, I accept that Mr Kuhrt always had a timer in mind and that his evidence in that regard was not prompted by Hytera’s solicitors. I do not accept that Professor Wicker’s evidence affects this outcome.
That of course leaves Motorola’s point that the inventive step included the idea of using the timer as a criterion for determining whether the subscriber unit was one with which the base station was previously communicating. Whilst I accept that Mr Kuhrt’s timer does not perform this function because his method uses identification information for that purpose, Motorola’s submission itself rests on the false premise that the timer in the patent is used for identification purposes. Whilst one of the claims refers to a timer, the purpose of that timer is not stated in the claims and the specification does not support Motorola’s submission that that was the purpose that the timer had. I therefore do not accept the submission.
Based on the evidence of Mr Kuhrt, I conclude that the idea of allowing a de-keyed base station to receive out-of-synchronisation transmissions was obvious as at the priority date and that a method for doing so would inevitably have to be delimited by a timer. I therefore conclude that the invention disclosed by the 960 patent was obvious and that the relevant claims are invalid.
552 The primary judge found that the features of claim 1 which Motorola sought to emphasise were so obvious it went without saying. In doing so, we consider that his Honour accepted that the combination of integers in the claim was obvious and rejected Motorola’s contentions to the contrary. In our view his Honour has not been shown to be in error.
553 It is not in dispute that the problem, being a risk of a transmission made by a subscriber unit being ignored by a base station if the base station had de-keyed, was known. Further, his Honour held that the problem was common general knowledge. Accordingly, it was permissible, and appropriate, to include the base station in the formulation of the problem. But in any event, his Honour held that both experts would have adopted a solution that involved a base station. And we agree with Hytera that the fact that Professor Wicker’s approach using the base station differed from the claimed invention is irrelevant. Professor Wicker’s evidence demonstrated that addressing the problem by reference to the base station was an appropriate starting point.
554 As Hytera correctly contends, even if there may have been other solutions that were directed to the mobile station rather than the base station, that is irrelevant. The mere fact that solutions other than the claimed invention may exist does not avoid a finding of obviousness. More than one path can be obvious (see Mylan Health at [190] to [192]).
555 We agree with Hytera that the primary judge correctly rejected Motorola’s contention that Mr Kuhrt was impermissibly led to the inclusion of a timer in his solution. Rather, as his Honour found, the use of a timer was obvious. Further, as his Honour correctly recognised, the claim did not require the timer to be used for identification purposes or indeed any other purpose. And as his Honour indicated, it was not to the point that Mr Kuhrt’s solution included an additional identification step.
556 The suggestion that his Honour had regard only to whether individual integers were obvious rather than the combination claimed is not a fair characterisation of his Honour’s reasons. His Honour held that the combination of the features was obvious. As his Honour found, if the skilled person was addressing the problem by reference to the base station, it was not only obvious but inevitable that a timer would be used. In doing so, his Honour did not merely consider whether individual integers were obvious, but rather addressed the claimed combination.
557 Motorola says that the primary judge appears to have approached the question of obviousness on the basis that the invention involved the idea of allowing a de-keyed base station to receive out of synchronisation transmissions. But it says that the invention was not simply to allow a de-keyed base station to receive an out of synchronisation transmission. In our view, his Honour well understood this.
558 There is one final matter that we should address concerning whether his Honour confused or mixed the timer and the timing window concepts. As Motorola points out, in the last sentence of PJ [680] and in other passages such as PJ [727], it would seem that his Honour may have confused or mixed the timer and the timing window concepts. Motorola sought to elevate the significance of this to the level of contaminating fundamental aspects of his Honour’s reasoning. We consider this to be an exaggeration. But even if we considered the matter for ourselves and not so mixing these concepts, in our view his Honour’s ultimate conclusion still stands and is one that we would have come to.
559 We therefore reject ground 1 of Motorola’s cross-appeal.
Hytera’s notice of cross-contention
560 By grounds 8 to 11 of its notice of cross-contention, Hytera contends that the primary judge ought to have held that Hytera would not have infringed the asserted claims of the 960 patent, had they been valid, and further, ought to have held that the claimed invention was not a manner of manufacture. Given that we have upheld the primary judge’s finding on obviousness it is not strictly necessary to deal with Hytera’s notice of cross-contention. Nevertheless, the issues can be addressed relatively briefly. We address the manner of manufacture contention first.
Manner of manufacture (ground 11)
561 The primary judge said that for the reasons given in relation to the 355 patent, the method of the 960 patent involves an advance in computer technology and is therefore a manner of manufacture. Hytera’s ground 11 of its notice of cross-contention challenges that finding. But Hytera did not articulate any additional error in the primary judge’s reasoning particularly concerning the 960 patent.
562 We reject this ground of cross-contention for substantially the same reasons as expressed with respect to the 355 patent as to manner of manufacture.
Construction and infringement (grounds 8 and 9)
563 The construction issue before the primary judge concerned the requirement of the patent that the transmission be received “in proper synchronisation”. The issue which divided the parties was the meaning of the expression “if the transmission is received with proper synchronization” in independent claims 1 and 13.
564 Claim 1, with its integers set out with his Honour’s convenient numerical parentheses, is as follows:
1. In a conventional TDMA communications system, wherein the conventional TDMA communications system includes at least one base station and at least one mobile station, a method of accessing a de-keyed base station including:
[1] de-keying a base station in the conventional TDMA communications system;
[2] starting a timer in the base station when the base station de-keys;
[3] receiving a transmission from a mobile station; and
[4] re-keying and repeating the transmission, if the transmission is received with proper synchronization before expiration of the timer.
565 Claim 13, with its integers set out with his Honour’s convenient numerical parentheses also, is as follows:
13. In a conventional TDMA communications system, wherein the conventional TDMA communications system includes at least one base station and at least one mobile station, a method of accessing a de-keyed base station including:
at a base station in the conventional TDMA communications system:
[1] entering a temporary de-keyed state;
[2] remaining in the temporary de-keyed state for a period of time;
[3] receiving a transmission from a mobile station while in the temporary de- keyed state; and
[4] entering a repeat state, if the transmission is received with proper synchronization while in the temporary de-keyed state.
566 As discussed earlier, Hytera contended at trial that even though the patent provides for some wiggle room in the timing of the receipt of the bursts from a subscriber unit in the form of the timing window, that window cannot be larger than 7.5 msec. Another way of putting this is that a transmission will be received with proper synchronisation if its synchronisation pattern, which is 5 msec in duration, is permitted to arrive up to 2.5 msec early or late. Motorola denied the existence of any such limitation. The primary judge held that Hytera’s construction was untenable and that the patent required the window for which it provides to be greater than 7.5 msec.
567 Underpinning Hytera’s construction argument was the idea that if the timing window was larger than 7.5 msec, then the bursts transmitted by the subscriber units in adjacent timeslots would potentially overlap by trespassing beyond the 2.5 msec of guard time, being 1.25 msec at the beginning and end of each burst, provided for in the 2005 DMR Standard. But the primary judge said that this 2.5 msec is built into the concept of synchronisation itself. Under the 2005 DMR Standard, a burst containing a transmission will be treated as being in synchronisation if it is received up to 2.5 msec earlier or later than the time it expects the synchronisation pattern, and therefore burst, to arrive. The additional window for which the patent provides is necessarily in addition to this window and inherently must be larger than it. In any event, the primary judge said that Hytera’s objection that to proceed otherwise would result in timeslot overlapping is misconceived. The actions of a base station have no effect on that phenomenon which is dictated by the behaviour of the subscriber units. The primary judge said that even if the window was required to operate as Hytera suggested, the problem would persist.
Hytera’s submissions
568 On the appeal, Hytera says that the primary judge erred in construing claim 1 of the 960 patent and, as a result, in finding that Hytera would have infringed the asserted claims of the 960 patent by the supply of certain base stations before Hytera reprogrammed them, and by the supply of certain subscriber units which could be used with those base stations.
569 As we have said, the dispute below concerned the proper construction of the phrase “if the transmission is received with proper synchronization” as used in claim 1. Hytera says that the primary judge failed to make any clear finding as to the meaning of that phrase in claim 1. Instead, his Honour gave detailed reasons for rejecting what he perceived to be Hytera’s construction of that phrase (PJ [569] and [570], [584] to [638]). Hytera says that this involved a misapprehension of the construction advanced by Hytera. Further, although his Honour later suggested that he had accepted Motorola’s construction, Hytera says that his Honour’s reasons do not identify what that construction was (PJ [732]). Hytera says that one consequence of this is that what constitutes “proper synchronization”, on his Honour’s approach, has no apparent outer bound.
570 Hytera’s position is that the phrase “proper synchronization” incorporates the concept of synchronisation as it was understood in the field at the priority date, in light of the 2005 DMR Standard: that is, as referring to a transmission from a mobile station being received within the boundaries of a timeslot on the base station’s uplink. As the primary judge recognised, the 2005 DMR Standard allowed for a small timing window within which a base station would treat a transmission as being in synchronisation, by reason of the inclusion of 2.5 msec of “guard time” between each 27.5 msec “burst” for alternating timeslots of 30 msec (PJ [608], [609] and [616] to [619]). Hytera says that the primary judge’s error was to proceed on the basis that claim 1 allowed for an additional window over and above that provided for in the 2005 DMR Standard (PJ [570], [619] and [620]). Hytera says that as the language of “proper synchronization” indicates, the claim contemplates the same timing window as was recognised in the field.
571 It is well-established that the specification is not to be read in the abstract. It is to be construed in light of the common general knowledge before the priority date. Additionally, where the words used have a special or technical meaning in the relevant field, that should be taken into account. As to the language of claim 1, Hytera contends that the term “synchronization” had a special or technical meaning in the field which referred to a transmission from a mobile station being received within the boundaries of a timeslot on the base station’s uplink. It is said that the phrase “proper synchronization” as used in claim 1 incorporated that concept. As such, Hytera says that the phrase “proper synchronization” referred to the synchronisation that the transmission in question would have been recognised as being in had the base station not been de-keyed: that is, the permitted timing of the transmission within the boundaries of the timeslot on the base station’s uplink.
572 The primary judge discussed the concept of synchronisation at length in dealing with the common general knowledge. His Honour also found that under the 2005 DMR Standard, as applicable at the priority date, a base station would treat a transmission which arrived slightly early or late as being in synchronisation. This was the effect of the inclusion of 2.5 msec of guard time between 27.5 msec bursts for alternating timeslots of 30 msec (PJ [603] to [605], [608], [609] and [616] to [619]). In this regard, his Honour suggested that a transmission could arrive “up to 2.5 msec early or late” and still be treated as being in synchronisation. Hytera says that in fact, the correct figure is up to 1.25 msec early or late, beyond which a transmission would encroach into the next timeslot. In any event, his Honour correctly found that a person skilled in the art implementing the 960 patent would not do so in a way which did not comply with the 2005 DMR Standard (PJ [602]).
573 Hytera says that consistently with this, the expert evidence confirmed that the term “synchronization” as used in the field referred to a transmission from a mobile station being received within the boundaries of a timeslot on the base station’s uplink. The corollary is that a transmission from a mobile station encroaching into an adjacent timeslot could not be said to be “synchronized”. Against that background, Hytera says that the primary judge erred in characterising Hytera’s construction of claim 1 as being that “a transmission will only be received by a base station from a subscriber unit “with proper synchronization” if its synchronisation pattern arrives within a window no longer than 7.5 msec in duration” (PJ [584]; see also [569]). Hytera says that it is true that this is the result of Hytera’s construction if the invention is applied, as his Honour found it would be, in a system that was compliant with the 2005 DMR Standard. The synchronisation pattern is 5 msec in duration, and the permitted variation of up to 1.25 msec either way makes for a window of 7.5 msec within which that pattern must be received. But Hytera says that this does not involve simply substituting a timing window of 7.5 msec for the words of the claim.
574 Hytera says that its construction is consistent with the 960 patent as a whole, and involves a purposive approach in which the technical term “synchronization” is given a meaning consistent with its understanding in the field in the context of the 2005 DMR Standard.
575 The primary judge dismissed Hytera’s construction as untenable, on the basis that claim 1 allowed for an “additional window” over and above that provided for by the 2005 DMR Standard (PJ [569], [570], [619] and [620]). But Hytera says that there are several difficulties with this approach. First, it involved giving the word “synchronization” in claim 1 a different meaning to that which it bore in the field, and under the 2005 DMR Standard, which was a recognised special or technical meaning (PJ [570]). Second, it imported into the claim the concept of an “additional window” of latitude beyond the ordinary meaning of “synchronization” which is not reflected in the plain language used. Third, it is effectively open-ended, in that it places no apparent limit on the width or extent of that “additional window”. Instead, the only constraint apparently resulting from his Honour’s reading of the claim is that the window within which the synchronisation pattern must be received must be greater than 7.5 msec (PJ [619] and [620]).
576 Hytera says that reference to the body of the specification supports Hytera’s construction of claim 1. The term “synchronization” is used in many places in the 960 patent to refer to a transmission being within the boundaries of a timeslot. The passage at p 8 lines 11 to 31, referring to Figure 3, was the subject of particular consideration (PJ [598] and [599]). That passage explains that the concept of “proper synchronization” involves the receipt of a transmission within timing boundaries, consistently with the accepted understanding of “synchronization” as at the priority date. Further, it states that the “assumption” when a transmission is received outside timing boundaries “is that the MS [mobile station] was not in synchronization with the BS [base station] before the BS de-keyed”, such that the base station need not re-key and repeat the transmission: p 8 lines 24 to 31.
577 Hytera says that the same passage also illustrates the error in the primary judge’s approach. The passage refers to two windows of time, called TEXPECTED and TWINDOW. TEXPECTED refers to the window within which the base station “expects to receive transmissions” from the subscriber unit; TWINDOW refers to the window within which a transmission is received “with proper synchronization”: p 8 lines 13 to 15, 20 and 21. Two embodiments are given, in which TEXPECTED is said to be approximately 5 msec and 7.083 msec, respectively. Yet as his Honour recognised, on his Honour’s approach, an implementation of the invention which complied with the 2005 DMR Standard would require TEXPECTED to be 7.5 msec (PJ [638]).
578 As noted, his Honour correctly found that the invention would be implemented in compliance with the 2005 DMR Standard. Hytera says that it follows that, on his Honour’s approach, the only two embodiments given in this passage involve implementations of the invention which his Honour found the skilled person would not adopt.
579 Hytera says that by contrast, the first value of 5 msec for TEXPECTED given in the passage at p 8 lines 11 to 31 is consistent with Hytera’s construction and the 2005 DMR Standard. That is because TEXPECTED is a timing window equal to the length of the synchronisation pattern, being 5 msec under the 2005 DMR Standard, reflecting the expected timing of receipt of transmissions. In such a case, TWINDOW will reflect a slightly longer timing window of up to 7.5 msec within which the synchronisation pattern can be received and still be regarded as being in synchronisation in the manner outlined above. Hytera says that the second value of 7.083 msec for TEXPECTED is not inconsistent with Hytera’s construction.
580 The primary judge reasoned that Figure 3 of the 960 patent involved serious errors and could provide only limited assistance (PJ [632] and [634]). Hytera accepts that his Honour was right that Figure 3 involved an error. The timeslot boundaries at the bottom of the Figure are clearly wrongly drawn. A corrected version was put forward by Professor Viterbo. But Hytera says that the primary judge was wrong to find that Figure 3 involved further errors. The bursts are all the same size, and the fact that TEXPECTED is the same size as the synchronisation pattern does not involve any error, contrary to what his Honour said at PJ [633(b)-(c)]. Rather, this is consistent with the description of the invention, which states that “[i]n one embodiment, TEXPECTED is approximately 5 milliseconds”: p 8 lines 15 and 16.
581 Further, Hytera says that none of the experts gave evidence that TEXPECTED had to be 7.5 msec to comply with the 2005 DMR Standard. To the contrary, Mr Kuhrt referred to TEXPECTED as being approximately 5 msec, and Professor Wicker referred to it corresponding to the synchronisation pattern.
582 Hytera says that it is not necessary to redraw the timeslot boundaries at all, as Professor Viterbo did, in order to appreciate the key point made by Figure 3. The top line of Figure 3 shows the expected timing of the transmissions on the uplink around which TEXPECTED and TWINDOW are set. If the timeslot boundaries are disregarded rather than redrawn, it can be seen that the transmissions described as “properly synchronized” (at the left hand side) do not encroach into an adjacent timeslot (based on the expected timing on the uplink); the transmissions described as “not properly synchronized” (at the right hand side) do encroach into an adjacent timeslot; and TWINDOW is set to achieve this.
583 Further, Hytera says that the primary judge was correct to regard the dependent claims of the 960 patent as providing little assistance in construing claim 1 (PJ [636]).
584 On infringement (ground 9), Hytera says that its base stations, before they were reprogrammed, did not use the method of claim 1 of the 960 patent on the construction contended for. The base stations were not programmed to re-key and repeat only transmissions that were received with “proper synchronization”. Rather, transmissions that encroached by a certain amount into an adjacent timeslot would cause the base stations to re-key and repeat the transmissions. Hytera says that it follows that the primary judge erred in finding that the supply of the relevant base stations, and subscriber units that could be used with them, gave rise to infringement (PJ [732] and [733]).
Consideration
585 Hytera’s contention is that the phrase “proper synchronization” has a restrictive meaning, confining it to a window of time restricted to the limits of the extent of flexibility permitted by the timeslots in accordance with the 2005 DMR Standard. But the specification of the 960 patent does not support Hytera’s construction. Neither the asserted claims nor the specification makes any reference to limiting a “properly synchronized” transmission by reference to a timeslot boundary.
586 The specification expressly defines “proper synchronization”, and says that it “means that the transmission is received within timing boundaries, also known as a window”: p 8 lines 11 and 12. Immediately following this definition, the specification describes that, in one embodiment, in order to assess if the transmission is received with proper synchronization, it is necessary to determine whether the synchronization pattern is received within TWINDOW being a period that may be broader than TEXPECTED. At p 8 lines 20 to 24 the specification states:
Also, in one embodiment, proper synchronization means that the transmission is received within the window 308 of time termed TWINDOW. In any event, if transmissions are received outside the window 308 TWINDOW, then the transmission is not received with proper synchronization and will not be processed (RxSyncOutOfWindow, Transition 214).
587 TWINDOW is a period of time described by reference to where the synchronization pattern falls. It allows for that pattern to be received earlier or later than TEXPECTED. It follows that the specification makes clear that the requirement is simply that the transmission must be received within the timing window, also referred to as TWINDOW or “timing boundaries”, being a period of time within which the synchronization pattern is to fall: p 8 lines 11, 12, 20 to 24, Figure 2; Figure 3. The specification discloses no specific limit on how widely or narrowly the window is drawn. That is left to the skilled addressee, but with guidance as to how it might be defined so as to achieve its aim. In particular, there is no limitation that the window must be strictly limited so that the burst is received within the timeslot plus guard time in order to be properly synchronized.
588 Hytera emphasises Figure 3. But Hytera’s attempts to rely on Figure 3, and in particular the “corrected version” put forward by Professor Viterbo, are unsustainable and inconsistent with what is described in the specification. As the primary judge correctly observed in [634], “any attempt to draw conclusions about timeslot boundaries from Figure 3 [is] a forlorn escapade”, noting that Hytera accepts that Figure 3 has errors. First, it is apparent from the original version of Figure 3 that it is not directed to defining the boundaries of a timeslot, much less defining guard time, which is not mentioned in the specification at all, or where it starts and finishes. Second, Professor Viterbo’s “corrected version” of Figure 3 comprised annotations to depict timeslot boundaries and guard time which were not described in the specification and were done in a way which was inaccurate. Third, Figure 3 was intended to be illustrative of concepts of the claimed invention, in particular the relationship between TEXPECTED and TWINDOW, rather than placing limitations on the scope of the claim: p 3 lines 11 to 15. Figure 3 simply establishes that TWINDOW is longer than TEXPECTED and that in that embodiment, transmissions which are received where the synchronisation pattern falls within TWINDOW will be repeated (PJ [632]).
589 Further, ordinary words should be given their ordinary meaning, unless a person skilled in the art would give them a technical meaning or the specification ascribes a special meaning. In this case, the primary judge properly rejected Hytera’s contention that the expression “proper synchronization” in claims 1 and 13 had the technical or special meaning proposed by Hytera.
590 Further, contrary to Hytera’s assertion, the expert evidence did not confirm that the term “synchronization” as used in the field referred to a transmission from a mobile station being received within the boundaries of a timeslot on the base station’s uplink. The evidence cited by Hytera related to the circumstances of synchronization in the “keyed” context rather than to the circumstances of the “de-keyed” context to which the 960 patent is directed.
591 The phrase “proper synchronization” takes its meaning from the particular context in which it is used. The de-keyed context is different because the base station has ceased transmitting the timing reference or beat so that drift will occur. Indeed, prior to the invention of the 960 patent, there was no need for a base station to maintain synchronization in the de-keyed context because there was no “temporary de-keyed state” only a “permanent de-keyed state”. Further, the primary judge was right to recognise that, even if one is considering the construction of the patent specification in the 2005 DMR Standard context, then TEXPECTED must accommodate that the synchronisation pattern is not expected to be in a precise 5 msec timeslot, but rather might be expected to be earlier or later because of drift or jitter: PJ [617].
592 The concept of TWINDOW is a broader window than TEXPECTED to deal with the receipt of a transmission in a de-keyed situation where the base station is no longer providing the timing beat for the system and therefore the timing of the subscriber unit, which is no longer receiving the timing beat, may have drifted some way from the timing of the base station. Indeed, the entire context for the invention is at odds with the suggestion that TWINDOW is limited to the limits of timeslot boundaries when the base station has not de-keyed and is still regulating the timing of the system.
593 We therefore reject ground 8 of Hytera’s notice of cross-contention which concerns construction, and it follows that we also reject ground 9 concerning infringement which is dependent on ground 8.
Infringement by supply of subscriber units (ground 10)
594 By ground 10 of its notice of cross-contention, Hytera contends that the primary judge erred in finding that, if the 960 patent had been valid, Hytera would have infringed claims 1-5, 8-15 and 17-18 of the 960 patent by the supply of certain subscriber units (as opposed to base stations) until 20 November 2019, including after reprogramming its base stations to remove the functionality that his Honour considered would have given rise to infringement.
Hytera’s submissions
595 Claim 1 of the 960 patent defines “a method of accessing a de-keyed base station” involving four steps. The functionality defined by the claim is implemented by the base station. One of the steps involves the base station receiving a transmission from a subscriber unit, but all of the claimed steps are carried out by the base station. Indeed, his Honour accepted that “the subscriber units do not use the method of the patent in any way” (PJ [734]). Hytera says that in these circumstances, the supply of a subscriber unit which simply makes a transmission does not provide an adequate foundation for a finding of indirect infringement on any of the bases accepted by his Honour. Hytera says that this raises considerations equivalent to those addressed for the 355 patent, where a similar argument arises.
596 Hytera says that the error in the primary judge’s approach is underscored by the fact that, to comply with the 2005 DMR Standard, Hytera’s subscriber units must make transmissions of the kind in question involving the required synchronisation patterns. Hytera says that this is covered by the EP licence between the parties.
597 Hytera says that the error is further highlighted by his Honour’s finding (at PJ [735(a)]) that Hytera’s infringement by the supply of subscriber units continued for a period of several months after it voluntarily reprogrammed its base stations, without admission, to remove the functionality alleged to give rise to infringement.
Consideration
598 In our view the primary judge did not err in finding that Hytera’s supply of the base stations, and subscriber units that could be used with them, would have given rise to infringement had the 960 patent been valid.
599 As to the infringement by supply of subscriber units, Hytera contends that the primary judge erred in finding that Hytera infringed the asserted claims of the 960 patent by the supply of certain subscriber units because the functionality defined by the claim is implemented by the base station. We disagree. Infringement of the method involves the use of a combination of base stations and subscriber units. Both claim 1 and 13 stipulate that the claimed methods are “in a conventional TDMA communications system, wherein the conventional TDMA communications system includes at least one base station and at least one mobile station”.
600 Hytera does not disclose any basis to challenge the findings the primary judge made in respect of indirect infringement by Hytera’s supply of the subscriber units prior to November 2019. The primary judge found that, from November 2019, Hytera had taken sufficient steps to ensure that the reprogrammed base stations were not used in a system with unreprogrammed subscriber units so as to prevent infringement. But as Motorola correctly says, this demonstrates that Hytera was not required by the 2005 DMR Standard to act in a way which resulted in any infringement of the 960 patent, such that Hytera’s conduct prior to November 2019 did not fall within the scope of the EP licence.
601 We therefore reject ground 10 of Hytera’s notice of cross-contention.
C. Copyright infringement
C.1 Some preliminary concepts
602 In considering Motorola’s copyright infringement case on this appeal, it is helpful to explain the meaning and use of the following words and phrases: computer program, software, firmware, source code, object code, compilation, files and comments.
603 The phrase “computer program” and the word “software” are both commonly used, and in these reasons will be used, to refer to any computer program or code, whether written in source code or object code, and whether installed in a computer or within a device (such as a DMR). In that sense, “computer program” and “software” are generic terms. That common use of the phrase “computer program” is consistent with the definition of that phrase in s 10 of the Copyright Act:
computer program means a set of statements or instructions to be used directly or indirectly in a computer in order to bring about a certain result.
604 Section 10 of the Copyright Act also states that a computer program is taken by the Act to be included in the concept of a ‘literary work’:
literary work includes:
(a) a table, or compilation, expressed in words, figures or symbols; and
(b) a computer program or compilation of computer programs.
605 The phrase “source code” refers to software written in a computer language that is comprehensible to humans. Many computer languages have been written since the first invention of computing. Computer languages typically include “expressions” or “statements” (typically in the form of a string of letters, numerals or symbols) and have a defined syntax (being the structure and order of the expressions and statements to define relevant instructions). Source code consists of a sequential series of commands and operations written in the computer language. In the present case, Motorola’s source code for its DMRs was mostly written in a widely used computer language known as C++ (PJ [1149]).
606 The word “file” refers to a segment of source code. A file can take many forms, in that it may comprise data or definitions or it may comprise particular commands or instructions used within the computer program. In the present case, and as discussed further below, expert evidence was given in relation to the different function of “header files”, “source files” and “library files” within different parts of Motorola’s source code.
607 The phrase “object code” refers to software that has been converted from source code into binary code (a code that only uses the digits 0 and 1) in the form of commands and operations that can be executed by a processor within a computer or device (PJ [1147]). For that reason, “object code” is often referred to as “machine readable code”. The process of converting source code into object code is referred to as “compilation” (PJ [1148]).
608 The word “firmware” is commonly used to refer to object code that has been installed on a (hardware) device to control the operations of the device. However, in this proceeding, the parties also used the word “firmware” to refer to the source code from which the object code installed on DMR devices had been installed. The primary judge observed that that use of the word “firmware” was a source of confusion in the proceeding (PJ [1155]).
609 The word “comments” refers to statements (typically in the English language) that are inserted into source code to explain some aspect of the source code and thereby assist software engineers in their future development of the source code. Comments in the source code are not converted into object code and therefore are not executed by the processor within a computer or device.
C.2 Overview of Motorola’s infringement case
The copyright works allegedly infringed
610 Certain of the appeal grounds are affected by the proper identification of the copyright works that Motorola alleged were infringed by Hytera. It is therefore necessary to identify those works with some precision.
611 The primary judge drew attention to the fact that Motorola specified the copyright works that were allegedly infringed by Hytera at different levels of generality (PJ [1158]). In its pleaded case, Motorola formally specified the copyright works that were allegedly infringed by Hytera at two levels of generality. However, as the primary judge found, the second level itself specified programs at two levels of generality, with the result that Motorola specified the copyright works at three levels of generality (see table at PJ [1163]). It is necessary to have regard to Motorola’s pleaded case.
612 In its pleading (comprising the third further amended statement of claim and second further amended particulars of copyright claim), Motorola specified certain computer programs (defined as the Motorola Works) and alleged that each of those programs were:
(a) literary works within the meaning of s 10 of the Copyright Act; and
(b) an original literary work in which copyright subsists,
and that Motorola is the owner of copyright that subsists in each program.
613 In the pleading, the Motorola Works were defined as:
(a) (at the first level of generality) each of the “software suites” identified in section A of the particulars of copyright claim (defined as the Motorola Programs); and
(b) (at the second level of generality) each of the literary works comprised within the Motorola Programs identified in section A of the particulars of copyright claim.
614 In section A of the particulars of copyright claim, the Motorola Programs were defined as each of the following:
(a) the suite of software known as ‘MOTOTRBO Mobile Subscriber FW Package R01.00.01’ (Mobile Firmware);
(b) the suite of software known as ‘MOTOTRBO Portable Subscriber FW Package R01.00.01’ (Portable Firmware); and
(c) the suite of software known as ‘DSP (C55x) R01.00.01’ (DSP Firmware).
615 Thus, at the first level of generality, Motorola identified the copyright works that were allegedly infringed by Hytera as each of the above suites of software which it defined as the Mobile Firmware, the Portable Firmware and the DSP Firmware respectively. Although Motorola defined each of the above suites of software using the word “firmware”, the computer programs that were identified by Motorola as the “Motorola Programs” were in the form of source code, not object code. It is necessary to explain this further.
616 As found by the primary judge (PJ [1144]-[1145]), Motorola’s DMR products comprised subscriber units, which included portable DMRs (i.e. handheld) and mobile DMRs (i.e. those fitted inside vehicles), and base stations. Each type of device came installed with its own firmware (that is, object code installed within the device). The firmware for each kind of device differed. The host firmware for the portable devices was known as the ‘Portable Firmware’, and that for the mobile devices as the ‘Mobile Firmware’. Each mobile and portable device and each base station was also installed with what was known as the ‘DSP Firmware’. The DSP is that part of a device which implements and operates the requirements of the 2005 DMR Standard including synchronising and transmitting on a timeslot.
617 The suites of computer programs that were identified by Motorola as the Mobile Firmware, the Portable Firmware and the DSP Firmware were not the object code firmware installed on the devices; rather the suites of computer programs comprised the source code from which the firmware installed on the devices was compiled. As discussed below, Motorola alleged that the copyright in its source code was infringed by Hytera, not the copyright in its object code installed on its devices.
618 In respect of the second level of generality, section A of the particulars of copyright claim defined the literary works comprised within the Motorola Programs as the “works identified in respect of particular Motorola Programs in Confidential Annexure 1”. Confidential Annexure 1 is titled “Motorola Works contained within the Motorola Programs”. It contains two tables headed:
(a) Table 1(a): Motorola Works contained within the Mobile Firmware and the Portable Firmware; and
(b) Table 1(b): Motorola Works contained within the DSP Firmware.
619 Each table contains three columns headed “Motorola Work”, “Directory” and “Files”.
620 In Table 1(a), which identifies the Motorola Works contained within the Mobile Firmware and the Portable Firmware, the following 4 computer programs are listed under the first column headed “Motorola Work”: Darwin ergonomics platform; EMT component of the Darwin ergonomics platform; Xlate component of the Darwin ergonomics platform; and UIT component of the Darwin ergonomics platform. The second column identifies a computer directory where a copy of the computer program is located and the third column lists the files within the directory which comprise the computer program (in some occasions, simply stating “All files”). It is implicit from the names of the programs and directories in which the programs were located, and it was found by the primary judge, that the EMT, Xlate and UIT programs were each components of the Darwin ergonomics platform. Thus, as disclosed by Table 1(a), the Motorola Works were specified at the highest level as the Mobile Firmware and the Portable Firmware, at a second level as the Darwin Ergonomics Platform which formed part of each of the Mobile Firmware and the Portable Firmware, and at a third level as the EMT, Xlate and UIT components of the Darwin Ergonomics Platform.
621 In Table 1(b), which identifies the Motorola Works contained within the DSP Firmware, the following 4 computer programs are listed under the first column headed “Motorola Works”: Framer; L1 Timer; framerLib Library; and HAL Serial Buffer. Again, the second column identifies a computer directory where a copy of the computer program is located and the third column lists the files within the directory which comprise the computer program (in some occasions, simply stating “All files”). It is apparent from the names of the directories in which the programs were located, and it was found by the primary judge, that the Framer and L1 Timer programs were each components of the framerLib Library program. Thus, as disclosed by Table 1(b), the Motorola Works were specified at the highest level as the DSP Firmware, at a second level as the framerLib Library and the HAL Serial Buffer programs each of which formed part of the DSP Firmware, and at a third level as the Framer and L1 Timer programs each of which formed part of the framerLib Library program.
622 The eight Motorola Works listed in Tables 1(a) and 1(b) of the particulars of copyright claim comprise source code.
623 On occasion, the primary judge described Motorola’s case as relating to “11 separate computer programs” (see for example PJ [744]) or the “11 works in suit” (see for example PJ [1154]). This was a reference to the three Motorola Programs and the eight Motorola Works as identified in the particulars of copyright claim. It is necessary to keep in mind that the eight Motorola Works as identified in the particulars of copyright claim comprise computer programs within the three Motorola Programs. It is also necessary to keep in mind that the EMT, Xlate and UIT programs formed part of the Darwin Ergonomics Platform and the Framer and L1 Timer programs formed part of the framerLib Library program.
624 It was common ground that Motorola owned the Australian copyright in the Motorola Works (PJ [1154], [1173], [1176]).
625 Motorola’s pleading particularised the alleged infringement of the Motorola Works by reference to section D of the particulars of copyright claim, which in turn referenced Confidential Annexure 2 to the particulars. Confidential Annexure 2 contained two tables headed:
(a) Table 2(a): Instances of copying from the Mobile Firmware and the Portable Firmware; and
(b) Table 2(b): Instances of copying from the DSP Firmware.
626 Each table contained five columns which identified:
(a) the name of the Motorola source code file that Motorola alleged had been copied by Hytera;
(b) the directory address for where the Motorola file was located;
(c) the name of the Hytera source code file or files that Motorola alleged contained copies of part or all of the Motorola file;
(d) the specific lines of source code within the Motorola file that Motorola alleged had been copied by Hytera; and
(e) the specific lines of source code within the Hytera file that Motorola alleged contained copies of the lines of source code within the Motorola file.
627 The specific lines of source code within the Hytera file that Motorola alleged contained copies of lines of source code within the Motorola file are referred to in these reasons as the impugned Hytera source code.
The infringing conduct
628 Motorola’s case was that Hytera reproduced the whole or a substantial part of the Motorola Works in China when Hytera created its own source code for certain Hytera DMR devices (Hytera Devices) and compiled that source code into object code and installed the object code as firmware in the Hytera Devices (Hytera Firmware) (PJ [1151], [1153] and [1181]). None of those acts occurred in Australia and, as a consequence, could not involve a contravention of Australia’s Copyright Act (PJ [1182]). Motorola alleged that Hytera infringed its Australian copyright in the Motorola Works under the Copyright Act in the following two ways (PJ [1152]).
629 First, Motorola alleged that Hytera infringed copyright in the Motorola Works by importing the Hytera Devices into Australia for the purpose of sale and by selling the Hytera Devices in Australia. Motorola further alleged that:
(a) each of the imported Hytera Devices embodied a reproduction in material form of the whole or a substantial part of one or more of the Motorola Works and, further or in the alternative, an adaptation of the whole or a substantial part of one or more of the Motorola Works;
(b) had the imported Hytera Devices been made by Hytera in Australia, that would have constituted an infringement of copyright in one or more of the Motorola Works;
(c) Motorola had not licensed or authorised Hytera to do the above acts; and
(d) Hytera knew or ought reasonably to have known the above matters.
630 Second, Motorola alleged that Hytera infringed its copyright in the Motorola Works by creating certain versions of the Hytera Firmware which contained a reproduction or an adaptation of the whole or a substantial part of one or more Motorola Works and:
(a) by making the Hytera Firmware available on its dealer and distributor website referred to as the Partner Portal;
(b) by authorising other persons to access and download from its “Partner Portal”, and make further copies of, the Hytera Firmware in Australia; and
(c) by making further copies of the Hytera Firmware itself in Australia.
The applicable statutory provisions
Motorola’s case concerning the imported Hytera Devices
631 In respect of its copyright infringement case concerning the imported Hytera Devices, Motorola relied on the following statutory provisions.
632 First, it alleged that the importation of the Hytera Devices constituted copyright infringement under s 37 of the Copyright Act which relevantly provides as follows:
37 Infringement by importation for sale or hire
(1) Subject to Division 3, the copyright in a literary, dramatic, musical or artistic work is infringed by a person who, without the licence of the owner of the copyright, imports an article into Australia for the purpose of:
(a) selling, letting for hire, or by way of trade offering or exposing for sale or hire, the article;
(b) distributing the article:
(i) for the purpose of trade; or
(ii) for any other purpose to an extent that will affect prejudicially the owner of the copyright; or
(c) by way of trade exhibiting the article in public;
if the importer knew, or ought reasonably to have known, that the making of the article would, if the article had been made in Australia by the importer, have constituted an infringement of the copyright.
…
633 Second, it alleged that the sale of the Hytera Devices in Australia constituted copyright infringement under s 38 of the Copyright Act which relevantly provides as follows:
38 Infringement by sale and other dealings
(1) Subject to Division 3, the copyright in a literary, dramatic, musical or artistic work is infringed by a person who, in Australia, and without the licence of the owner of the copyright:
(a) sells, lets for hire, or by way of trade offers or exposes for sale or hire, an article; or
(b) by way of trade exhibits an article in public;
if the person knew, or ought reasonably to have known, that the making of the article constituted an infringement of the copyright or, in the case of an imported article, would, if the article had been made in Australia by the importer, have constituted such an infringement.
…
634 There is no dispute that the Hytera Devices were imported into Australia for the purposes of sale and were sold in Australia without the licence of Motorola. The dispute at trial concerned the questions whether:
(a) if the Hytera Devices had been made in Australia by Hytera, that would have constituted an infringement of Motorola’s copyright in the Motorola Works; and
(b) Hytera knew or ought reasonably to have known that.
635 Infringement of copyright is defined by s 36 of the Copyright Act which relevantly provides as follows:
36 Infringement by doing acts comprised in the copyright
(1) Subject to this Act, the copyright in a literary, dramatic, musical or artistic work is infringed by a person who, not being the owner of the copyright, and without the licence of the owner of the copyright, does in Australia, or authorizes the doing in Australia of, any act comprised in the copyright.
…
636 The expression “acts comprised in the copyright” is defined in s 13(1) as “any act that, under this Act, the owner of the copyright has the exclusive right to do”. The exclusive rights conferred by copyright are relevantly defined in s 31(1) as follows:
31 Nature of copyright in original works
(1) For the purposes of this Act, unless the contrary intention appears, copyright, in relation to a work, is the exclusive right:
(a) in the case of a literary, dramatic or musical work, to do all or any of the following acts:
(i) to reproduce the work in a material form;
(ii) to publish the work;
(iii) to perform the work in public;
(iv) to communicate the work to the public;
(vi) to make an adaptation of the work;
(vii) to do, in relation to a work that is an adaptation of the first-mentioned work, any of the acts specified in relation to the first-mentioned work in subparagraphs (i) to (iv), inclusive;
…
637 The scope of the exclusive rights conferred by s 31 is affected by s 14 which provides as follows:
14 Acts done in relation to substantial part of work or other subject-matter deemed to be done in relation to the whole
(1) In this Act, unless the contrary intention appears:
(a) a reference to the doing of an act in relation to a work or other subject-matter shall be read as including a reference to the doing of that act in relation to a substantial part of the work or other subject-matter; and
(b) a reference to a reproduction, adaptation or copy of a work shall be read as including a reference to a reproduction, adaptation or copy of a substantial part of the work, as the case may be.
…
638 A central issue in dispute between the parties at trial was whether, if the Hytera Devices had been made in Australia by Hytera (involving the installation of the Hytera Firmware in the devices), that would have involved a reproduction or an adaptation of the whole or a substantial part of one or more of the Motorola Works and thereby have constituted an infringement of Motorola’s copyright in the Motorola Works.
639 The primary judge concluded that the installation of the Hytera Firmware (being object code) in the Hytera Devices could not constitute a reproduction in material form of the Motorola Works (being source code), as the two sets of code were not objectively similar (PJ [1189]-[1190]). In that regard, his Honour concluded that s 21(5) of the Copyright Act, which was enacted in response to the 1994 report of the Copyright Law Review Committee entitled ‘Computer Software Protection’, had no application in the circumstances of the present case (PJ [1196]). Section 21(5) provides that, for the purposes of the Copyright Act, a computer program is taken to have been reproduced if an object code version of the program is derived from the program in source code by any process, including compilation, and any such version is taken to be a reproduction of the program. In the present case, the Hytera Firmware (being object code) was not derived from the Motorola Works but from Hytera source code (which Motorola alleged had been copied from the Motorola Works). There is no appeal from the primary judge’s conclusion concerning s 21(5). Accordingly, it is unnecessary to consider Motorola’s case based on the allegation that the installation of the Hytera Firmware in the Hytera Devices constituted a reproduction in material form of the Motorola Works.
640 Motorola’s alternative case was that, if the Hytera Devices had been made in Australia by Hytera (involving the installation of the Hytera Firmware in the devices), that would have involved an adaptation of the whole or a substantial part of one or more of the Motorola Works and thereby have constituted an infringement of Motorola’s copyright in the Motorola Works. The word “adaptation” is defined in s 10(1) of the Copyright Act in relation to a literary work being a computer program as “a version of the work (whether or not in the language, code or notation in which the work was originally expressed) not being a reproduction of the work”. The relevant question in this context is, therefore, whether the Hytera Firmware is a “version” of the whole or a substantial part of one or more of the Motorola Works. The primary judge observed that, unlike the concept of reproduction which requires objective similarity, the adaptation right is unconcerned with the computer language in which the impugned object code is expressed (PJ [1221]). Nevertheless, as the High Court plurality (Gleeson CJ, McHugh, Gummow and Hayne JJ) explained in Data Access Corporation v Powerflex Services Pty Ltd (1999) 202 CLR 1 (Data Access), the central conception of the adaptation right remains the protection of expression and not ideas. With reference to the Explanatory Memorandum accompanying the Copyright Amendment Bill 1984 (Cth), the plurality stated (at [109]-[110]):
Paragraph 12 of the Explanatory Memorandum states that “only translation is likely to be relevant to adaptation of programs”. This indicates that Parliament did not intend the word “version” to cover situations where, although the functionality of a computer program was copied, original code has been written to perform that function. The focus on translation indicates that Parliament was concerned to ensure that the different languages in which a computer program may be expressed did not provide a means by which copying could occur and infringement be avoided on the ground that the expression in the new language was not a “reproduction”.
The use of the words “derived from the original” in par 14 of the Explanatory Memorandum also indicates that the focus is on copying. In accordance with the fundamental principle that copyright protects expression and not ideas, this must relate to the copying of the code (the “expression ... of a set of instructions”), rather than a copying of the idea or function underlying the code.
641 The primary judge stated the relevant question as follows (PJ [1223]):
The question therefore is whether the Hytera object code may be seen as a form or variant of the Motorola source code. If one arrives at the conclusion, as Motorola suggests the Court should, that the Hytera object code contains a copy in machine language of a substantial part of the Motorola source code then, in my view, it would be a form or variant of that code. The fact that it may contain code which was not copied from Motorola’s source code does not detract from it being a version of that source code.
642 His Honour concluded (PJ [1224]) that Motorola needed to demonstrate that:
(a) a substantial part of the Motorola source code (in the Motorola Works) was copied into the Hytera source code which was then compiled into the Hytera object code (being the firmware installed on the Hytera Devices); and
(b) Hytera knew or ought reasonably to have known that the installation of its object code on its devices, if done in Australia, would have involved an infringement of Motorola’s copyright in its source code.
643 His Honour also framed the relevant test in the following manner (PJ [1301]): if the Hytera source code did not involve the copying of a substantial part of the Motorola source code, then Hytera’s compiled object code will not involve an adaptation of a substantial part of Motorola’s source code and the importation infringement suit will fail.
644 None of the parties submitted that his Honour’s formulation of the relevant questions on copyright infringement involved error.
Motorola’s case concerning the Hytera Firmware
645 Motorola’s copyright infringement case concerning the Hytera Firmware was based upon different exclusive rights in s 31(1) of the Copyright Act, but ultimately raised the same principal issues. In respect of the Hytera Firmware that was made available by Hytera for copying in Australia on its dealer and distributor website (the Partner Portal), Motorola alleged infringement of the exclusive right in s 31(1)(a)(vii) by reference to subparas (i) and (iv). As set out above, the exclusive right in s 31(1)(a)(vii) is the right to do, in relation to a work that is an adaptation of the first-mentioned work (the adaptation), any of the acts specified in relation to the first-mentioned work in subparas (i) to (iv). Applying s 31(1)(a)(vii), the exclusive right in s 31(1)(a)(i) is the right to reproduce the adaption in a material form and the exclusive right in s 31(1)(a)(iv) is the right to communicate the adaptation to the public.
646 There is no dispute between the parties that Hytera reproduced the Hytera Firmware in a material form in Australia and communicated the Hytera Firmware to the public. Thus, the relevant question on Motorola’s case concerning the Hytera Firmware was whether the Hytera Firmware was an adaptation of the whole or a substantial part of the Motorola Works. As for the case concerning the Hytera Devices, Motorola needed to demonstrate that a substantial part of the Motorola source code (in the Motorola Works) was copied into the Hytera source code which was then compiled into the Hytera Firmware. On this part of Motorola’s case, Hytera’s knowledge of infringement was not relevant.
C.3 Hytera’s admissions and defence
647 By its defence, Hytera did not admit that Motorola held copyright in the Motorola Works and stated that it put in issue the question of subsistence and ownership of copyright for the purposes of s 126 of the Copyright Act. However, by the time of trial, Hytera abandoned that issue and conceded subsistence and ownership (PJ [1154], [1173], [1176] and [1251]).
648 In respect of the allegedly infringing acts, Hytera admitted the primary facts relied upon by Motorola being:
(a) the importation of the Hytera Devices into Australia for the purpose of sale and the sale of the devices in Australia; and
(b) making the Hytera Firmware available on its dealer and distributor website referred to as the Partner Portal, authorising other persons to access and download from its “Partner Portal”, and make further copies of, the Hytera Firmware in Australia, and making further copies of the Hytera Firmware itself in Australia.
649 As summarised by the primary judge (PJ [1173]), Hytera defended the copyright infringement case on four bases:
(a) First, Hytera did not admit that there was objective similarity between the particularised parts of the Motorola Works and the impugned parts of the Hytera source code. Hytera conceded, however, that if objective similarity was established, the Court may proceed on the basis that the objectively similar portions of the impugned Hytera source code were copied from the corresponding portions of the Motorola Works.
(b) Second, Hytera submitted that Motorola had failed to show that the portions of its source code which were copied into the impugned Hytera source code were original. Whilst Hytera accepted that each of the Motorola Works was a literary work in which copyright subsisted, it submitted that Motorola had to demonstrate that each part of the source code which it alleged had been copied by Hytera was original, in the sense of not having been copied from elsewhere and, in particular, not copied from earlier iterations of the same source code (developed by Motorola over time).
(c) Third, Hytera submitted that Motorola had failed to demonstrate that the portions of its source code which were copied into the impugned Hytera source code were a substantial part of the relevant Motorola Work from which the code was copied.
(d) Fourth, in relation only to the importation and sale of the Hytera Devices case, Hytera submitted that Motorola had failed to make good the knowledge element of the infringement. While Hytera accepted that, if it became necessary to consider the knowledge element, the Court will have found that the ex-Motorola engineers deliberately copied a substantial part of the Motorola Works into the impugned Hytera source code, Hytera submitted that they did so without Hytera’s authority and therefore without Hytera’s knowledge.
650 Each of the above issues is raised on the appeal in some form, either by Hytera or by Motorola.
C.4 Evidentiary issues
651 Before turning to the primary judge’s reasoning and principal findings, it is necessary to note certain evidentiary issues that arose from the manner in which Hytera gave discovery in the proceeding and limitations in the computer code discovered by Hytera.
652 Hytera gave discovery in four tranches (PJ [1267]) as follows:
(a) Hytera’s initial round of discovery was of relevant source code. It came to be called the first tranche not because it was agreed that discovery would be given in tranches but because Hytera gave subsequent discovery after additional (digital) documents were found by Hytera.
(b) After the first tranche of discovery, Hytera unearthed three laptops which contained further relevant materials which were then discovered by Hytera as the second tranche. This tranche contained additional Hytera source code and two ‘library’ files containing object code. As explained by Hytera’s expert, Mr Brown, and found by the primary judge (PJ [1273]), when source code is compiled into object code, the object code is combined into an “archive” or “library”. The source code from which the object code in the library files had been compiled was not discovered (PJ [1274]). The two library files had the file names raf_arm9.lib and DmrDspLib.lib (PJ [1283]). Motorola alleged that the raf_arm9.lib library file copied (or, more accurately, was an adaptation of) 19 specified Motorola source code files that were part of the Mobile Firmware and Portable Firmware source codes (PJ [1284]), and alleged that the DmrDspLib.lib file copied (or, more accurately, was an adaptation of) 64 specified files that were part of the DSP Firmware source code (PJ [1285]).
(c) There was then further discovery by Hytera of two more object code library files, which is referred to as the third tranche. The two library files had the names rfhal_c55.lib and the CPA library files (PJ [1287]). Motorola alleged that the rfhal_c55.lib file copied (or, more accurately, was an adaptation of) nine specified files in the DSP Firmware source code (PJ [1288]). Ultimately, the CPA library file did not need to be addressed because the source code from which it had been compiled was discovered in the fourth tranche.
(d) Hytera gave further discovery of the source code files for the CPA library file as the fourth tranche (PJ [1289]). Three of the source code files had the names EventBase.cpp, NotifierBase.cpp and ListenerBase.cpp. Each was alleged to be part of the Mobile, Portable and DSP Firmware, but they were not alleged to be part of any of the component programs (that is, the EMT, Xlate or UIT). The fourth file had the name SingleLinkedList.cpp and was alleged to be part of the EMT program (within the Mobile and Portable Firmware).
653 Thus, some of the computer code discovered by Hytera was in the form of source code and some was in the form of object code for which the original source code was not discovered. In the absence of Hytera source code, Motorola faced a considerable evidentiary hurdle in showing that Hytera’s object code (the library files) was created by Hytera copying a substantial part of Motorola’s source code. As discussed below, Motorola sought to overcome that hurdle by undertaking a process of disassembling the object code and inviting the Court to draw an inference of copying from all the circumstances. The circumstances are discussed below. In relation to the process of disassembly, the primary judge explained that it is possible to disassemble object code into a family of low level languages known as ‘assembly languages’ (PJ [1272]). An assembly language is a depiction in a more readable form of the computer processing instructions within the object code. However, it is not possible to discern from assembly code any of the higher concepts that would have been within the source code from which the object code was compiled.
654 The sequential flow of discovery given by Hytera affected the expert evidence that was filed. Initially, Motorola’s expert, Professor Wicker, only had access to the first tranche of discovered source code and prepared his first affidavit (dated 28 March 2019) in respect of that material (PJ [1268]). After Professor Wicker’s initial evidence was filed, the second tranche of discovery was given by Hytera (PJ [1271]). Professor Wicker then prepared a second affidavit (dated 25 July 2019) in respect of the additional source code and the two library files (object code) discovered in the second tranche (PJ [1275]). In respect of the library files, Professor Wicker then caused to be conducted a process of disassembly of the object code to retrieve some information from it. This information largely consisted of the names of files and functions which had existed in the missing source code (PJ [1278]). Professor Wicker recognised some of these file and function names as matching or partially matching file and function names he had seen in Motorola’s source code. Professor Wicker prepared a third affidavit (dated 26 March 2020) in respect of the rfhal_c55.lib and CPA library files discovered in the third tranche and undertook the same analysis in respect of those library files (PJ [1287]). Professor Wicker’s fourth affidavit (dated 25 June 2020) was responsive to Hytera’s expert evidence. Professor Wicker’s fifth affidavit (dated 1 July 2020) considered the Hytera source code files for the CPA library file which were discovered by Hytera as the fourth tranche.
C.5 The primary judge’s reasoning and principal findings
Substantiality and originality
655 The primary judge summarised the principles concerning the question whether computer code copied from part of a computer program constitutes a substantial part of that computer program as follows (PJ [1229]):
… First, in deciding whether computer code copied from part of a computer program is a substantial part of that computer program, it is the quality of the work taken, not the quantity, which is critical: JR Consulting & Drafting Pty Ltd v Cummings [2016] FCAFC 20; 116 IPR 440 at [267] (‘JR Consulting’). Secondly, in carrying out that assessment, the essential or material features of the computer program should be ascertained by considering the originality of the part allegedly taken: Data Access at [84]. Thirdly, the analysis will include a comparison of the codes (JR Consulting at [269]) as well as a consideration of the code’s structure: Data Access at [85]. Functionality is not protected.
656 There was no challenge on appeal to that summary.
657 The primary judge then addressed the criterion of originality in this context, and the submission advanced by Hytera that Motorola had failed to demonstrate that the portions of Motorola’s source code which were copied into the Hytera source code were original, in the sense of not having been copied from elsewhere and, in particular, not copied from earlier iterations of the same source code (developed by Motorola over time). His Honour framed the question of principle as follows (PJ [1230]):
In considering whether the part taken is a substantial part of the computer program, it is necessary to conclude that the part taken is original. If the author would not have copyright in the part taken standing alone, then the part copied will not be a substantial part: IceTV Pty Ltd v Nine Network Australia Pty Ltd [2009] HCA 14; 239 CLR 458 at [37] (‘IceTV’). This entails that if the part copied did not originate with the author then it cannot be a substantial part: IceTV at [37]. But what if the author copied the part in question from an earlier work of their own? IceTV does not address that question directly and it is that question that presently arises.
658 The primary judge reasoned that, where a work has been created, in part, from a pre-existing work, two situations may be usefully distinguished: the first is a work which reproduces extracts from another work; and the second is a work which builds on earlier versions of itself (PJ [1234]). The primary judge observed that anthologies are a well-known example of the former (PJ [1235]). In such cases, there is no infringement of copyright by the copying of the underlying works that have been included in the anthology. In IceTV Pty Limited v Nine Network Australia Pty Limited (2009) 239 CLR 458 (IceTV), French CJ, Crennan and Kiefel JJ summarised the principle that emerges from cases involving anthologies as follows (at [37]): “where the part reproduced did not originate with the author, so that the author would not have had copyright in the part standing alone, the part reproduced will not be a substantial part”. As an example of the second situation, the primary judge referred to successive editions of a legal text, where each edition involves careful revision, reviewing and settling of the text (PJ [1236]). His Honour reasoned that (PJ [1237]-[1238]):
In the latter case, whilst the text may in some portions remain unchanged, this does not mean it was not reviewed. In the course of its production, the fact that part of the text remains unchanged will reflect the work of the author in checking to see that the law has not changed. Thus the fact that no alteration occurs does not mean that no effort was expended. Consequently, leaving to one side the precise status of effort in the context of origination as that concept is used in infringement, it has been accepted that such a work, as a whole, is original even though it may contain tracts of text identical to the previous edition.
It was that principle which was applied by the Full Court in JR Consulting to conclude that successive editions of software were each original works in their own right.
659 The primary judge noted that the issue that arose for determination before the Full Court in JR Consulting & Drafting Pty Ltd v Cummings [2016] FCAFC 20; 116 IPR 440 (JR Consulting) was subsistence of copyright: specifically, whether each version of the QSS software as updated and released was an original literary work in its own right in which copyright subsisted (JR Consulting at [304]). Despite that, his Honour considered that the Full Court’s conclusion was wider and included the idea that the review and revision of the code, whether resulting in new code or in parts of the code being left unchanged, was an act of origination under the Copyright Act and that the product of that act of origination was itself an original work (PJ [1240]). His Honour explained that a computer program must function coherently as a whole and that changes in one part of the code necessitate checking that, with the modifications, the code as a whole continues to operate (PJ [1243]).
660 The primary judge rejected Hytera’s submission on the issue of originality and concluded that (PJ [1250]):
… Where successive updates of software are released and originality is conceded for the purposes of subsistence, an argument for infringement purposes that a substantial part of a particular version of the software has been taken, is not defeated by showing that the part in question derives from antecedent code.
661 Hytera challenges that conclusion on this appeal.
The primary judge’s criticisms of Motorola’s copyright infringement case
662 The primary judge was critical of the manner in which Motorola presented its case on copyright infringement. The criticisms related to the particularisation of its case, the submissions advanced in support of its case and aspects of the evidence adduced in support of its case. The criticisms are summarised at PJ [1291]-[1297], but the criticisms are repeated throughout the judgment. In considering the primary judge’s reasons and Motorola’s grounds of cross-appeal, those criticisms have been kept in mind. However, two aspects of the criticisms made by the primary judge warrant specific mention.
Identification of the computer files relied on by Motorola in support of its infringement case
663 The first aspect concerns the identification of the computer files relied on by Motorola in support of its infringement case. Consistently with the manner in which Motorola had identified the copyright works that it alleged had been infringed, the primary judge wished to understand Motorola’s case at the three levels of generality advanced by Motorola:
(a) at the highest level of generality, the Mobile Firmware, the Portable Firmware and the DSP Firmware;
(b) at the second level of generality, the Darwin Ergonomics Platform (which formed part of the Mobile Firmware and the Portable Firmware) and the framerLib Library and the HAL Serial Buffer programs (each of which formed part of the DSP Firmware); and
(c) at the third level of generality, each of the EMT, Xlate and UIT programs (each being a component of the Darwin ergonomics platform), and each of the Framer and L1 Timer programs (each being a part of the framerLib Library program).
664 At each level of generality, the primary judge sought to identify the computer files relied on by Motorola in support of the infringement case for the program concerned. For the most part, the primary judge was able to do that. His Honour undertook the infringement assessment by commencing at the lowest (or narrowest) level of generality and working towards the highest (or widest) level of generality. In other words, his Honour first considered each of the EMT, Xlate and UIT programs separately, then his Honour considered the Darwin Ergonomics Platform, then his Honour considered the Mobile Firmware and the Portable Firmware. Similarly, his Honour first considered each of the Framer and L1 Timer programs separately, then the framerLib Library program and the HAL Serial Buffer program, and then his Honour considered the DSP Firmware.
665 On many occasions, the primary judge expressed frustration that Motorola had failed to identify the computer files that it relied on in support of its infringement case concerning the different Motorola Works. That criticism stemmed from the structure of the particulars of infringement contained in Confidential Annexure 2. While the Annexure listed Motorola’s files by reference to whether they formed part of the Mobile and Portable Firmware (Table 2(a)) and the DSP Firmware (Table 2(b)), it did not list the files by reference to the underlying Motorola Work of which they formed part. His Honour described the “formal presentation of Motorola’s case” in that regard as impenetrable (PJ [1262]).
666 The primary judge’s frustration with that aspect of the presentation of Motorola’s case is understandable. The Court expects sophisticated litigants to present their case with clarity and precision. Nevertheless, in almost all cases his Honour was able to identify the computer files relied on by Motorola in support of its infringement case concerning the different Motorola Works. While his Honour frequently had regard to the evidence adduced by Hytera for that purpose, it is clear that the evidence adduced by Hytera was simply based on the particulars of infringement contained in Confidential Annexure 2. It is apparent that Hytera understood Motorola’s case.
667 In respect of Motorola’s infringement case concerning the Mobile and Portable Firmware, the primary judge observed (PJ [1731]) that the case had two elements:
(a) a case based on the computer files within the EMT, Xlate and UIT programs and a further case based on those files plus four other files external to those three programs but still within the Darwin Ergonomics Platform; and
(b) a case based on a number of files which, whilst within both the Portable and Mobile Firmware, were not within the Darwin Ergonomics Platform.
668 In respect of the second case, the primary judge found that Motorola had not identified in its submissions what the files involved in that part of the case were (PJ [1733]). His Honour considered the evidence adduced by Motorola on that part of the case and concluded as follows (PJ [1737]):
I have considered whether it may be said that Motorola has failed to advance a case about these files. In my view, Motorola has not advanced such a case. My dispositive reason for dispatching this second element in Motorola’s case on the Portable and Mobile Firmware is that Motorola’s submissions simply do not advance it. In the event that this conclusion proves erroneous on appeal, I will nevertheless consider what the evidence shows.
669 The primary judge then proceeded to consider a number of files that had been identified in Hytera’s evidence as being files that are part of the Portable and Mobile Firmware and are not within the Darwin Ergonomics Platform. Those files are contained within Confidential Annexure 2 to Motorola’s particulars of copyright infringement, and it is apparent that Hytera’s evidence was given in response to those particulars. Thus, it can be concluded that Hytera understood Motorola’s case in that regard. For some of those files, his Honour concluded that, had Motorola advanced a case on those files, its infringement claim would have succeeded in respect of the copied segments of those files (see PJ [1761]), [1768]), [1796], [1797]).
670 Similarly, in respect of Motorola’s infringement case concerning the DSP Firmware, the primary judge observed (PJ [1935]) that the case had two elements:
(a) a case based on the L1 Timer, Framer, framerLib Library and the HAL Serial Buffer, as part of the DSP Firmware; and
(b) a case based on additional files within the DSP Firmware which are not part of the L1 Timer, Framer, framerLib Library or the HAL Serial Buffer.
671 In respect of the second case, the primary judge found that Motorola’s submissions on this aspect of its case were so minimal that his Honour did not accept that Motorola had in fact advanced such a case and, on that basis, his Honour rejected it (PJ [1937] and [1938]). Nevertheless, to avoid the “spectacle of a re-trial”, his Honour stated that he would endeavour to identify Motorola’s case and the evidence on which, had it been advanced, it would have rested (PJ [1938]).
672 The primary judge then proceeded to consider a number of files that had been identified in Hytera’s evidence as being files that are part of the DSP Firmware and are not within the L1 Timer, Framer, framerLib Library, the HAL Serial Buffer. Those files are contained within Confidential Annexure 2 to Motorola’s particulars of copyright infringement, and it is apparent that Hytera’s evidence was given in response to those particulars. Thus, it can be concluded that Hytera understood Motorola’s case in that regard. For some of those files, his Honour concluded that, had Motorola advanced a case on those files, its infringement claim would have succeeded in respect of the copied segments of those files (see PJ [1941] and [1961]).
673 Motorola sought to appeal the primary judge’s conclusion at PJ [1737] that it had failed to advance a case about the identified additional files within the Mobile and Portable Firmware that were not within the Darwin Ergonomics Platform and the conclusion at PJ [1937] that it had failed to advance a case about the identified additional files within the DSP Firmware that were not within the L1 Timer, Framer, framerLib Library or the HAL Serial Buffer. Hytera submitted that Motorola should not be permitted to challenge those findings on the appeal because the findings were not raised in Motorola’s amended notice of cross-appeal or in Motorola’s amended notice of contention in Hytera’s appeal. That dispute is addressed below.
Submissions concerning the materiality of copied computer code
674 The second aspect of the criticisms made by the primary judge that warrants specific mention relates to Motorola’s submissions concerning the materiality of copied computer code. On numerous occasions the primary judge stated that Motorola had not advanced submissions concerning the materiality of a specific segment of computer code within a file that formed part of a Motorola Work that had been copied. The primary judge frequently found that, in the absence of submissions, Motorola had failed to establish that the segment of computer code was material to the operation of the relevant Motorola Work. Motorola contends on this appeal that most of those criticisms were made on an incorrect basis, stemming from what Motorola contends was an erroneous methodology undertaken by the primary judge to the question whether the impugned Hytera source code was a copy of a substantial part of the Motorola Works. As discussed in the following section, the primary judge assessed the question of materiality, and thereby substantiality, separately for each segment of copied code, which Motorola contends was in error. Motorola argued on the appeal that its submissions and evidence addressed the issue of substantiality of the copied code by considering the substantiality of the totality of the code from each Motorola Work that was copied by Hytera.
675 On a number of occasions, the primary judge also stated that, while the function of particular computer code had been the subject of Motorola’s expert evidence, his Honour did not understand the evidence (and was unassisted by submissions). In those circumstances, the primary judge concluded that Motorola had not established that the segment of code was material to the operation of the Motorola Work (see for example PJ [1699], [1756], [1868], [1874]). It is unfortunate, but not entirely uncommon, that technical expert evidence is presented to the Court in a manner that renders it unintelligible to the Court. Ordinarily, the Court expects the parties to advance submissions in a manner that provides a suitable explanation of technical evidence. It is also the case that procedures are available to assist the Court in both understanding and assessing technical evidence, such as the use of referees with technical expertise to report on questions referred to them or the use of an assessor sitting with the judge when hearing the evidence. It will become necessary to return to this topic at the conclusion of these reasons.
Whether the impugned Hytera source code was a copy of a substantial part of the Motorola Works
676 The primary judge stated that Motorola was required to show that the impugned Hytera source code involved the copying of a substantial part of the Motorola source code (PJ [1301]). His Honour explained that this involved two principal steps. First, it was necessary to determine, for each tract of Hytera source code, whether the code was copied as alleged. However, because Hytera conceded that the code was copied if it was shown to be objectively similar, that question devolved to whether Motorola had demonstrated that the impugned lines of the Hytera source code were objectively similar to the nominated lines of the Motorola source code (PJ [1302]). Second, if copying had occurred, it was then necessary to determine whether the lines copied were a substantial part of the relevant program which Motorola put forward as a literary work. His Honour summarised the test of substantiality as whether the lines of code were material to the operation of the program and were original (in the infringement sense) (PJ [1303]). His Honour stated that the issues for determination involved the following seven steps (PJ [1304]):
(1) an explanation of the nature and operation of each of the 11 works;
(2) the identification of the files constituting each work which are alleged to have been copied by Hytera;
(3) the identification of the lines of code within each file which are alleged to have been copied;
(4) a comparison between those lines and the lines of the Hytera code which are said to do the copying so as to determine whether the two sets of code are objectively similar. If they are, then Hytera concedes that its lines of code have been copied;
(5) in relation to those lines of code which have been copied, a determination of whether they are material to the work in suit;
(6) in relation to the same lines of code, a determination of whether they are original in an infringement sense; and
(7) a conclusion in relation to each of the 11 works as to whether a substantial part has been copied by Hytera and therefore whether Motorola's infringement suit (based on adaptation) succeeds.
677 Later, his Honour explained his approach to the question of copying a substantial part of the source code as follows (PJ [1326]):
In relation to each file (where a file is involved), I will deal successively with objective similarity, copying (if it arises), and substantial part. In relation to substantial part, Motorola must establish that each copied portion of its code was both original (Computer Edge Pty Ltd v Apple Computer (1986) 161 CLR 171 at 182) and that it constituted a material or essential feature of the EMT: IceTV at [158]-[159]; Data Access at [84]. In determining what is material or essential it is not appropriate to approach the matter on a ‘but for’ basis, i.e. by asking whether the program would work without it: Data Access at [81]-[84]. Instead the Court is to engage in a process of qualitative abstraction of the material features of the computer program allegedly copied: IceTV at [158]-[159]. Generally speaking, the quality of what is taken is more important than the quantity, but quantity is not completely irrelevant. It will be seen therefore that the substantial part analysis involves two inquiries: materiality and originality. I will consider these in relation to each file after the objective similarity analysis.
678 Motorola contends that the above statement reveals error in approach. Motorola submitted that while it was correct for the primary judge to assess objective similarity on a file by file basis, it was incorrect to assess substantiality on a file by file basis. Motorola submitted that substantiality had to be assessed at the level of the copyright works alleged to have been infringed and that the primary judge erred by failing to consider substantiality by reference to all parts of all files within a copyright work that had been copied. Motorola further submitted that the primary judge erred by treating the questions of materiality and originality of the code that was copied as two conditions of the assessment of substantiality, rather than as elements of an overall assessment of substantiality.
679 An examination of the primary judge’s reasons confirms that his Honour’s approach was to assess both objective similarity and substantiality on a file by file basis. Indeed, his Honour considered objective similarity and substantiality at a sub-file level, being segments of code within a file. It is convenient to illustrate his Honour’s approach by reference to the first file examined, which was the Motorola file named cor_emt_user_defines.h within the EMT program (which itself was a component of the Darwin ergonomics platform). The equivalent Hytera file was named raf_app.h. His Honour considered 13 segments of code within those two files (PJ [1338]). The segments ranged in length from 2 to 28 lines of code. His Honour found, on the basis of expert evidence and his Honour’s own review of the code, that each of the 13 segments of code were objectively similar (PJ [1339]). His Honour then separately considered the “materiality” of each segment of code. By way of illustration, in respect of the first segment of code (comprising lines 141-166 of the file), his Honour concluded (PJ [1344]):
It is … not shown that lines 141-166 are a substantial part of the EMT and Motorola’s infringement allegation with respect to these lines fails.
680 The primary judge proceeded to consider each of the 13 segments of code separately and, in respect of each of them, found that Motorola had not established that the segment of code was a substantial part of the EMT. For most of the segments, his Honour concluded that the evidence was insufficient to enable him to understand the significance of the particular segment of code to the operation of the EMT, and therefore insufficient to persuade him that the segment of code was “material” (see PJ [1342], [1350], [1353], [1354], [1355], [1358], [1360], [1361], [1362], [1363]). For some of the segments, his Honour also concluded that, because he was not satisfied that the segment was material, it was unnecessary to reach a view on whether the segment was original (see PJ [1350], [1353]). For all of the segments, his Honour stated that Motorola made no submissions about the specific segment in question. After considering each segment separately, the primary judge concluded, in respect of the Motorola file named cor_emt_user_defines.h, that (PJ [1364]):
Motorola’s infringement claim in relation to this file fails.
681 The primary judge repeated the above methodology in respect of seven other files that formed part of the EMT and which had been part of the first tranche of discovery given by Hytera. In a small number of instances, the primary judge found that particular segments of code were not objectively similar and, for that reason, Motorola’s infringement claim failed (see for example at PJ [1398]). In most instances, the primary judge reached the same conclusion in respect of each file: first, that none of the segments of the code in the file were a material part of the EMT; and second, that as a consequence, Motorola’s infringement claim in relation to the file in question failed.
682 After considering each of the eight files that formed part of the EMT and which had been part of the first tranche of discovery given by Hytera, the primary judge concluded, without any other deliberation, that (PJ [1406]):
In relation to the above eight files, Motorola has failed to establish that a substantial part of the EMT was copied by Hytera into its source code.
683 The primary judge adopted the same methodology in respect of all of the tranches of source code that were discovered by Hytera. For a large majority of the segments of source code examined by the primary judge, his Honour concluded that the segment had been copied into Hytera’s source code, but the segment was not a substantial part of the relevant Motorola Work. The primary judge’s reasoning with respect to the tranches of object code (the library files) discovered by Hytera is described below.
684 Ultimately, the primary judge concluded that only the following two segments of Motorola source code, copied by Hytera, involved the copying of a substantial part of a Motorola Work:
(a) lines 227-287 of the file named rs_xlt_utilities.c, which the primary judge concluded was a substantial part of the Xlate program (PJ [1670], [1684]), the Darwin Ergonomics Platform (PJ [1729]) and the Portable and Mobile Firmware (PJ [1732] and [1798]); and
(b) the file named SerialHalBuffer.h, which the primary judge concluded was a substantial part of the HAL Serial Buffer program (PJ [1933]) and the DSP Firmware (PJ [1936]).
685 Each of Hytera and Motorola appeal the primary judge’s conclusions on a number of grounds, discussed below.
Whether the object code library files were an adaptation of a substantial part of the Motorola Works
686 As stated earlier, in its second and third tranches of discovery, Hytera discovered three ‘library’ files in object code called raf_arm9.lib, DmrDspLib.lib and rfhal_c55.lib. Hytera was unable to produce the source code from which those library files had been compiled.
687 In the absence of Hytera’s source code, Motorola submitted at trial that the Court should infer that Hytera had copied a substantial part of Motorola’s source code in producing the Hytera source code which was compiled into the library files. Motorola alleged that the library files were an object code adaptation of a substantial part of relevant Motorola Works. Relevantly, Motorola alleged that the Court should infer that:
(a) the raf_arm9.lib library file was an adaptation of a substantial part of 19 specified Motorola source code files that were part of the Mobile Firmware and Portable Firmware source codes;
(b) the rfhal_c55.lib file was an adaptation of a substantial part of nine specified Motorola source code files that were part of the DSP Firmware source code; and
(c) the DmrDspLib.lib file was an adaptation of a substantial part of 64 specified Motorola source code files that were part of the DSP Firmware source code.
688 Motorola asked the Court to draw that inference from the following eight facts and circumstances (summarised by the primary judge at PJ [1514]):
(a) Motorola had engaged a patent attorney to disassemble the object code, and that process revealed function names that were the same as or very similar to function names that appeared in Motorola’s source code. Professor Wicker expressed the opinion that it was likely that the source code from which the object code had been compiled had been copied from Motorola’s source code.
(b) It was to be inferred from the extent of copying which had otherwise been demonstrated in relation to the available Hytera source code that copying on the same scale was likely to have occurred in the missing Hytera source code.
(c) Hytera’s DMR project was in disarray as at the start of 2008 and it could be inferred that Hytera had a motive to steal Motorola’s intellectual property.
(d) Hytera’s computer engineers had access to confidential Motorola material including its source code.
(e) The fact that the Hytera source code was not available was the result of a deliberate course of conduct by persons within Hytera whose purpose was to frustrate any copyright infringement proceedings.
(f) The Hytera computer engineers involved in the creation of the missing source code had set out deliberately to copy Motorola’s source code and then make it appear that it had not been copied.
(g) It was to be inferred from the speed with which Hytera’s DMR project was brought to a rapid conclusion that it must have done so by the use of Motorola’s source code.
(h) Hytera called no one who was involved in the writing of the source code, enabling an inference to be drawn against Hytera that the evidence of those persons would not have assisted its case.
689 The primary judge found that he was unable to draw the inference sought by Motorola. His Honour’s conclusions on each of the facts and circumstances referred to above was as follows.
690 First, the primary judge did not accept that the fact that the function names retrieved from the disassembled object code were the same or similar to the function names in the Motorola source code was sufficient to draw an inference that the missing source code was objectively similar to the Motorola source code (PJ [1529]). This was because there were examples in the evidence where Hytera functions with similar names to a Motorola function turned out to comprise different code.
691 Second, the primary judge found that, while in the development of the firmware for its DMR devices, Hytera’s software engineers sometimes engaged in the copying of Motorola’s source code, the extent of copying was not sufficient to support the inference sought to be drawn by Motorola (PJ [1535]).
692 Third, the primary judge accepted that Hytera had a motive to steal Motorola’s intellectual property (PJ [1536]).
693 Fourth, the primary judge found that the ex-Motorola engineers brought with them to Hytera all of Motorola’s source code both for the Mobile and Portable Firmware and also the DSP Firmware and did so to provide themselves with a resource from which they could later harvest that code for the purposes of writing Hytera’s source code (PJ [1538]).
694 Fifth, the primary judge found that the missing source code had been “made to disappear” and that this was “a deliberate attempt to suppress evidence which might assist in an infringement suit” (PJ [1553]).
695 Sixth, the primary judge found that Hytera personnel set out to disguise the fact that they were copying Motorola’s source code (PJ [1554]).
696 Seventh, the primary judge found that it was not possible for Hytera to have composed its DMR firmware in the time that it did using legitimate means (PJ [1574]).
697 Eighth, the primary judge drew an adverse inference from the failure of Hytera to call its software engineers involved in the development of its DMR firmware (apart from the ex-Motorola engineers who had all left Hytera’s employment) (PJ [1575]).
698 Consistently with his Honour’s approach to the question whether Hytera had copied a substantial part of the Motorola Works, the primary judge first considered the question of objective similarity and then considered the question of materiality.
699 The primary judge expressed his ultimate findings on the question of objective similarity in respect of the raf_arm9.lib library file as follows:
1577 … I am confident that in the missing Hytera source code there were tracts of code which were, before their untimely disappearance, objectively similar to portions of Motorola’s source code and that these portions had been copied. In some cases, the copying would have been verbatim, in other cases there would have been cosmetic changes.
1578 However, I am also confident that there were tracts of code in the missing Hytera source code which are not objectively similar to the Motorola source code. This may be because they had been written independently. For example, because the Hytera devices are not the same as the Motorola devices, there are of necessity differences in the codes. There may also be other circumstances where Hytera’s software engineers used the Motorola code as a basis for producing something which, although descended from the Motorola source code, is sufficiently different that it is no longer objectively similar. The removal of functionality from the Motorola source code for the simplified Hytera source code is an example.
1579 These possibilities are opened up by the source code which is available. In considering Motorola’s case that its source code had been copied, I have concluded in very many cases that objective similarity is not established. Motorola urged me to reason from what had happened in those cases where the Hytera source code was available that something similar was likely to have happened in the case of the source code which was not available. It did so by its submission that the former exhibited evidence of ‘wholesale’ copying with the invitation that similar wholesale copying must have taken place in the missing source code. I have rejected that submission. But I nevertheless accept the invitation to reason by analogy from the source code which is available to the source code which is not.
1580 It is very likely that amongst the missing source code files there are files which have been copied from the Motorola source code (using copied as a shorthand for objective similarity and causation). It is also quite possible that some of the missing source code files are not objectively similar. Turning then to the 12 files presently under consideration the problem becomes in each case how to determine which class the file falls into.
1581 I see no way of resolving that question in relation to any particular file. I am not satisfied on the balance of probabilities that any of the nominated missing Hytera source code files is objectively similar to the 12 Motorola files in question. I think it likely that some of them have been copied but I am neither able to estimate how many nor to identify the files where this has happened.
…
1583 Despite therefore being persuaded that Hytera took Motorola’s source code and fashioned it into its own source code (which has then been lost), I am not persuaded in the context of a copyright infringement suit that it has been demonstrated, at the level of these particular files, that the missing Hytera source code was objectively similar to the corresponding Motorola source code. I have not the slightest hesitation in concluding that the missing Hytera source code was in many instances fashioned from the Motorola source code. However, the fact that refashioning certainly took place and that not all of it was cosmetic, means that when one asks what conclusions can be drawn about particular files, the answer is that one cannot say.
1584 I conclude that Motorola has not shown that the missing source code contained tracts of source code which are objectively similar to the source code in the 12 files. Motorola’s infringement claim in relation to them therefore fails.
700 The primary judge expressed his ultimate findings on the question of materiality in respect of the raf_arm9.lib library file more briefly:
1585 Motorola made no submissions about the materiality of the 12 files. I have no explanation of what any of the files do in terms of the EMT. Consequently, even if I had been satisfied that copying as alleged had taken place, I could not have been satisfied of their materiality. There are 151 files in the EMT. I cannot reason simply from the fact that a file has been taken that it was material to the overall work.
701 For the same reasons, the primary judge also concluded that he was unable to draw an inference that:
(a) the raf_arm9.lib library file was an adaptation of a substantial part of Motorola source code files which were part of the Xlate program (PJ [1683]) and part of the UIT program (PJ [1715]);
(b) the rfhal_c55.lib library file was an adaptation of a substantial part of Motorola source code files that were part of the L1 Timer program (PJ [1849]) and the Framer program (PJ [1878], [1881], [1884], [1887], [1890]); and
(c) the DmrDspLib.lib file was an adaptation of a substantial part of Motorola source code files that were part of the DSP Firmware source code (PJ [1968]).
702 Motorola appeals those conclusions.
Hytera’s knowledge of copying
703 As stated earlier, Motorola alleged that Hytera infringed its copyright in the Motorola Works within ss 37 and 38 of the Copyright Act by importing and selling the Hytera Devices in Australia. This required Motorola to show that Hytera knew or ought reasonably to have known that, if the Hytera Devices had been made in Australia by Hytera, that would have constituted an infringement of Motorola’s copyright in the Motorola Works. The primary judge accepted Motorola’s submission that the relevant date for assessing Hytera’s knowledge is at the date the Hytera Devices were imported, which began in September 2013 (PJ [1988]).
704 The primary judge concluded that, as at September 2013, the facts known by Mr GS Kok would have indicated to a reasonable person that if the devices had been made in Australia, Motorola’s copyright would have been infringed (PJ [1995]). In reaching that conclusion, his Honour referred to his earlier findings which included that:
(a) Mr GS Kok was in charge of the DMR team and had been given authority by Mr Chen to organise the structure of the DMR team, to manage that team and also to hire new personnel;
(b) the ex-Motorola engineers employed by Hytera did not conceal from the DMR team that parts of Motorola’s source code were being used to create Hytera’s source code and it is more likely than not that the entire DMR team was aware that Motorola’s source code was being used to create Hytera’s source code;
(c) had Hytera continued on its original product development arc, it is likely that it would have brought its devices to market no earlier than the middle of 2011 and the devices would not have been competitive with Motorola’s devices;
(d) the motivation of the ex-Motorola engineers in using some of Motorola’s source code to create Hytera’s source code was to get the Hytera devices to market as quickly as possible at the lowest cost and with the best battery life, and the Hytera devices were brought to market in early March 2010, being at least 15 months earlier than would otherwise have occurred;
(e) Mr GS Kok was the directing mind behind the use of Motorola’s source code to create some of Hytera’s source code.
705 The primary judge concluded that, on ordinary principles, the knowledge of Mr GS Kok should be attributed to Hytera. His Honour found that Mr GS Kok was, as at September 2013, sufficiently closely and relevantly connected to Hytera that the state of his mind should be attributed to it (PJ [1998]).
706 At trial, Hytera relied on the fraud exception to imputation of knowledge and submitted that the knowledge of Mr GS Kok was not to be attributed to Hytera because he had acted in breach of fiduciary duty and his conduct was reprehensible. The primary judge reasoned (PJ [2000]) that the fraud exception does not apply where the fiduciary’s activities are not totally in fraud of the principal (referring to Grimaldi v Chameleon Mining NL (No 2) (2012) 200 FCR 296 (Grimaldi) at [284]) and that the conduct by which Mr GS Kok acquired his knowledge of the relevant facts was not totally in fraud of Hytera. His Honour concluded that Mr GS Kok’s actions resulted in Hytera having a commercially viable product (when it otherwise would not have) and having it faster than its original development arc would have entailed, Mr GS Kok intended to benefit Hytera by his actions, and he was successful in this endeavour.
707 Hytera appeals those conclusions.
Additional damages
708 The primary judge gave detailed consideration to the question whether the Court should award additional damages for Hytera’s infringement of copyright under s 115(4) of the Copyright Act. In doing so, the primary judge had regard to the mandatory considerations specified in s 115(4)(b), being:
(a) the flagrancy of the infringement;
(b) the need to deter similar infringements of copyright;
(c) the conduct of the defendant after the act constituting the infringement or, if relevant, after the defendant was informed that the defendant had allegedly infringed the plaintiff’s copyright;
(d) whether the infringement involved the conversion of a work or other subject‑matter from hardcopy or analog form into a digital or other electronic machine‑readable form;
(e) any benefit shown to have accrued to the defendant by reason of the infringement; and
(f) all other relevant matters.
709 In relation to flagrancy, the primary judge concluded that the conduct of the ex-Motorola engineers was morally reprehensible (PJ [2034] and that Mr GS Kok orchestrated that conduct and his knowledge is to be attributed to Hytera (PJ [2038]). On that basis, his Honour concluded that Hytera’s importation of the devices into Australia was a flagrant infringement of Motorola’s copyright, as were the other forms of infringement (making the firmware available for download in Australia) (PJ [2038])).
710 In relation to the conduct of Hytera after it was informed of the alleged infringement, the primary judge found that Hytera was aware of the alleged infringement from May 2017, but it did not stop importing the Hytera Devices until May 2019 (PJ [2053]).
711 In relation to any benefit shown to have accrued to Hytera by reason of the infringement, the primary judge referred to his earlier findings that Hytera had benefitted from the actions of the ex-Motorola engineers in two ways: by developing a commercially viable product and by an accelerated date of entry into the market (PJ [2061]). However, his Honour concluded that those benefits did not accrue by reason of the infringements as those benefits had accrued prior to the importation of the Hytera Devices (PJ [2062]).
712 The primary judge accepted a range of other matters advanced by Hytera in its favour, including that:
(a) the portions of copied code that were found to have been infringing copies were relatively small (PJ [2067]);
(b) Hytera had two reasonably arguable defences to infringement, being that the Motorola source code was not original in the infringement sense and that the knowledge of the ex-Motorola engineers should not be attributed to Hytera (PJ [2068]); and
(c) the importation of the Hytera devices into Australia and the distribution of the Hytera Firmware in Australia was not the same conduct as that which led to the creation of the firmware (PJ [2069]).
713 Weighing all mandatory factors and other relevant facts raised by the parties, the primary judge concluded that an award of additional damages was appropriate (PJ [2086]).
714 Hytera appeals that conclusion
C.6 Appeal grounds concerning substantiality and originality
Overview
715 A central issue in this appeal is whether a part of a copyright work that is derived from, and identical to, an earlier version of the work can constitute a “substantial part” of the copyright work within the meaning of s 14 of the Copyright Act, so as to establish infringement when that part is copied. If the answer to that question is in the negative, it would follow that the owner of the copyright in the work must sue upon the earliest version of the work in which the copied part appears.
716 This issue underpins several of the grounds of appeal advanced by Hytera. By ground 1 of its amended notice of appeal, Hytera contends that the primary judge erred in finding that Hytera had taken a substantial part of Motorola’s copyright works by reason that his Honour erred in his approach to the consideration of the originality of the parts held to have been taken. By several subsequent grounds, Hytera challenges the primary judge’s findings on the issue of “substantial part” with respect to specific copyright works on the same basis (see grounds 2(e)-(f), 3(b)-(c), 4(a) and 5(a) of the amended notice of appeal). The same issue is raised by grounds 1 and 3 of Hytera’s amended notice of cross-contention in Motorola’s cross-appeal.
Hytera’s submissions
717 Hytera submitted that the primary judge correctly observed that, in determining whether a part of a copyright work, such as a computer program, is a “substantial part” for the purposes of s 14 of the Copyright Act, it is necessary to consider its quality, not merely its quantity; and that “in carrying out that assessment, the essential or material features of the computer program should be ascertained by considering the originality of the part allegedly taken” (PJ [1229]). Hytera argued that the primary judge erred, however, in concluding that “[w]here successive updates of software are released and originality is conceded for the purposes of subsistence, an argument for infringement purposes that a substantial part of a particular version of the software has been taken, is not defeated by showing that the part in question derives from antecedent code” (PJ [1250]). Hytera submitted that the effect of this reasoning was to treat all parts of the computer program as being original, including parts which were copied from antecedent works. Hytera submitted that that is the very antithesis of originality.
718 Hytera submitted that the primary judge erred in his Honour’s reliance on JR Consulting. Hytera argued that the Full Court concluded in that matter that each copyright work as a whole was an original work for the purposes of subsistence of copying. It did not conclude that any particular parts of those works were sufficiently original to constitute a substantial part for the purpose of infringement. That question, which the Full Court recognised would have required a separate consideration of originality, did not arise. Hytera argued that, in contrast, the primary judge treated the existence of originality in the context of subsistence, and the question of originality of part of a work for the purpose of infringement, as the same inquiry.
719 Hytera submitted that the primary judge justified the collapsing of these two distinct inquiries by drawing a distinction between a work which reproduces extracts from another work, and a work which builds on earlier versions of itself. Hytera argued that that distinction is illusory and contrary to authority. The primary judge’s reasoning that work is involved in the decision to leave certain parts of the earlier computer program unchanged in the later program, and in ensuring that the unchanged parts cohere with the later program as a whole, applies equally to any work that is derived from earlier work (including work created by a different author). Moreover, if an alleged infringer reproduces only parts of a work which are unchanged relative to an earlier edition, they do not take any advantage of the author’s investment in the later edition: they are simply copying material which is unoriginal and therefore insubstantial. The circumstance that the prior work is created by the same author as the later work is immaterial. Originality in a work turns upon the skill and labour put by the author or authors into the particular form of expression in that work.
720 Hytera further submitted that, in any event, the evidence did not establish that the parts of the asserted copyright works which were found to have been reproduced by Hytera were built upon earlier versions of the “same” works (as distinct from works which reproduced extracts of other works). Nor did the evidence provide any foundation for concluding that the authors of the antecedent and asserted works were the same.
721 Hytera also submitted that the primary judge’s approach would lead to a de facto extension of the term of copyright in those parts of Motorola’s source code which were unchanged. Copying of the parts identical to the earlier edition or version of a work would amount to infringement even in an edition or version created many years after copyright expired in the original text.
Motorola’s submissions
722 Motorola submitted that Hytera’s approach is wrong as a matter of law, and inconsistent with the well-established principle that, in the case of works that are subject to successive revision, each new version is protectable in its own right. Hytera’s proposed approach would have “catastrophic effects” on the protection of works that undergo successive revisions, such as legal textbooks or computer programs, the latter of which might be subject to thousands of minor revisions. On Hytera’s approach, any lines of code that appeared in antecedent versions of the computer program must be excluded from consideration of substantial part. Copyright owners could not rely on revision or modification as acts of origination, but only on the addition of new lines of code. As a result, the protections afforded by the Copyright Act would be limited, and proceedings to enforce those protections would become more costly and complex.
723 Motorola argued that Hytera had not identified any case in which its proposed approach to the assessment of “substantial part” had been adopted. Moreover, its approach is contrary to recent authorities where the originality of parts of copyright works were considered without regard to whether they existed in a previous version.
724 Motorola submitted that the primary judge’s application of JR Consulting was correct, insofar as the Full Court’s conclusion on originality was one of broader application; namely, that originality was not limited to careful choices about the selection and ordering of pre-existing code, but also included other acts of origination such as the review and revision of code.
725 Motorola submitted that the primary judge’s approach does not operate to extend the copyright of parts of an antecedent work that appear in the subsequent version. Once copyright in the earlier work has expired, anyone can reproduce it.
Consideration
726 The issue raised by Hytera by these grounds of appeal has not been addressed directly in any of the decided cases. It is therefore necessary to proceed from first principles, as was the approach of the primary judge.
727 In resolving these grounds of appeal, it is necessary to start with the centrality of the concept of originality to the subsistence of copyright. As stated in s 32 of the Copyright Act, copyright subsists in an original literary, dramatic, musical or artistic work. As explained by French CJ, Crennan and Kiefel JJ in IceTV (at [33] and [34], references omitted):
The requirement for copyright subsistence that a literary work be “original” was first introduced into the Copyright Act 1911 (Imp), although it had already been recognised at common law. Originality for this purpose requires that the literary work in question originated with the author and that it was not merely copied from another work. It is the author or joint authors who bring into existence the work protected by the Act. In that context, originality means that the creation (ie the production) of the work required some independent intellectual effort, but neither literary merit nor novelty or inventiveness as required in patent law.
There has been a long held assumption in copyright law that “authorship” and “original work” are correlatives; the legislation does not impose double conditions.
728 Similarly, in the earlier decision of Data Access, the plurality (Gleeson CJ, McHugh, Gummow and Hayne JJ) observed (at [22], references omitted):
… the requirement in copyright law that a work be “original” is to be distinguished from the requirements [in patent law] that an alleged invention be novel and that it not be obvious. The question for copyright law is whether “the work emanates from the person claiming to be its author, in the sense that he has originated it or brought it into existence and has not copied it from another”. If so, the work does not lack originality because of the anterior independent work of another, although, in such circumstances, an invention might lack novelty.
729 Copyright has been found to subsist in a wide variety of works, from wholly original works, to works derived from other works of the author or other persons, and to works that consist of compilations of parts of other works or of other information. By way of illustration, the House of Lords decision in Ladbroke (Football) Ltd v William Hill (Football) Ltd [1964] 1 WLR 273 (Ladbroke) concerned the subsistence and infringement of copyright in coupons prepared by bookmakers comprising lists of forthcoming matches between well-known football teams, accompanied by bets offered in respect of the matches. The House of Lords unanimously found that copyright subsisted in the respondents’ coupons as a whole, and that the parts copied by the appellants constituted a substantial part, amounting to infringement. Lord Reid observed, in determining whether copyright subsisted in the respondents’ coupons as a whole and in rejecting the appellants’ contention that the coupons did not constitute original compilations (at 277):
A wrong result can easily be reached if one begins by dissecting the plaintiffs’ work and asking, could section A be the subject of copyright if it stood by itself, could section B be protected if it stood by itself, and so on. To my mind, it does not follow that because the fragments taken separately would not be copyright, therefore the whole could not be. Indeed, it has often been recognised that if sufficient skill and judgment have been exercised in devising the arrangements of the whole work, that can be an important or even decisive element in deciding whether the work as a whole is protected by copyright.
730 Another illustration is the Full Federal Court decision in Interlego AG v Croner Trading Pty Ltd (1992) 39 FCR 348 which concerned the subsistence of copyright in drawings of toy bricks marketed in Australia under the names “Lego” and “Duplo”. It was accepted that the drawings in issue were derived from earlier drawings in which copyright subsisted. Justice Gummow (with whom Black CJ and Lockhart J agreed) stated (at 378):
Though recognising that a slavish copy of an earlier work will not enjoy copyright (Ladbroke (Football) Ltd v William Hill (Football) Ltd [1964] 1 WLR 273 at 276; [1964] 1 All ER 465 at 469) and that originality must pertain not to ideas but to their expression (University of London Press Ltd v University Tutorial Press Ltd [1916] 2 Ch 601 at 608), the appellants contended that drawings which derive from earlier drawings can still be seen as distinct original artistic works, each attracting its own copyright. This proposition was supported by reference to L B (Plastics) Ltd v Swish Products Ltd [1979] RPC 565 where Whitford J said (at 569):
The draughtsmen called on both sides made it quite plain that even where there has been a previous drawing or some sketches have been made which are in part redrawn, the making of any drawing of the kind I have to consider is a skilled business involving hours of labour, although the end result may seem relatively simple.
731 Justice Gummow observed (at 379) that, whilst the author of an original artistic work must have expended a significant amount of his skill and labour, “originality” does not mean novelty or uniqueness and does not require inventiveness in the sense of patent law. His Honour concluded that there was no question about the labour involved, or the skill and judgment of the draftsman, and that copyright subsisted in the drawings.
732 Yet another illustration is afforded by the English Court of Appeal decision in Hyperion Records Ltd v Sawkins (2005) 64 IPR 627. The claimant, Dr Sawkins, composed modern performing editions of three grand motets written by Michel-Richard de Lalande, a composer at the courts of several kings of France in the 17th and 18th centuries. The evidence established that Dr Sawkins spent approximately 300 hours working on each motet, selecting the best original versions, transcribing the original scores into modern musical notation, adding notes and directions to players, and recreating certain parts that had been lost. Dr Sawkins’ work did not, in general, involve the re-composition of de Lalande’s music or making an arrangement of it in the copyright sense. The Court of Appeal concluded that the effort, skill and time that Dr Sawkins spent in making the three performing editions were sufficient to satisfy the requirement that they should be “original” works in the copyright sense. That was so even though Dr Sawkins worked on the scores of existing musical works composed by another person, those works were out of copyright, and Dr Sawkins had no intention of adding any new notes of music of his own (at [36] per Mummery LJ, with Jacob LJ and Mance LJ agreeing).
733 The application of the above principles in the context of successive drafts of a work, successive editions of a textbook, or successive versions of a computer program, was discussed by the Full Court in JR Consulting (at [273]-[279]). Their Honours referred with apparent approval to the commentary of Professor Ricketson in his learned work The Law of Intellectual Property: Copyright, Designs and Confidential Information. In respect of works derived from an earlier work including revised works, their Honours quoted the following passage (at [277]):
A further aspect of originality arises in relation to works that are derived from earlier works. In many cases, it happens that the work for which protection is claimed is only one in a series of works which have been evolved over a period of time, for example, successive drafts of a play or novel or a series of working drawings made in the process of producing a painting or engraving. Although the point is not often taken, it is clear that a work will not be denied protection on the basis of lack of originality simply because it is derived from, or based on, an earlier work of this kind. Thus, providing the later work is not a mere slavish copy, it will constitute an original work in its own right if the author has expended sufficient independent skill and labour in bringing it into material form.
734 In respect of successive editions of a textbook, their Honours quoted the following passage (at [278]):
Successive editions of a book, such as a legal text or a dictionary, will probably not pose great difficulties [in terms of originality], even if the differences may be fairly slight. It may be assumed that the author(s) has/have carefully reviewed and considered the preceding text and that any alterations or insertions are intended to be consistent with, and enhancements of, what has gone before. In other words, there has been a revision of the text as a whole and the application of sufficient skill and judgement to make each new edition an original work in its own right. The same reasoning can be applied to differences in successive versions of such things as house plans, computer programmes and clothing designs. In many instances, of course, the differences will be quantitatively as well as qualitatively significant.
735 In JR Consulting, the Full Court concluded that copyright subsisted in each successive version of a computer program called “Quick Series Software” (or QSS). That was so even if the revisions made to a particular version of the program might be regarded as quantitively insubstantial. The Full Court reasoned (at [304]):
… To the extent that each sequential update … reflects changes to the source code by addition or deletion (whether the rectification of errors or a new set of instructions to bring about a certain result) that might be regarded as, quantitatively at least, insubstantial, an inference arises from the circumstance of his authorship of the entire programs comprising QSS, over time, and his election to release, with each numerical version of QSS, the entire program as updated, to the following effect: that he has carefully considered the preceding state of the suite of programs and that the alterations, insertions or deletions are intended to be consistent with and enhancements of what has gone before. In other words, Mr Cummings has undertaken a particular revision of the programs on each occasion as part of the whole of the work with the application of sufficient skill and judgement to make each version as updated and released an original work in its own right.
736 It is from that foundation that the concept of originality has relevance to issues of infringement, including the question whether a substantial part of a work has been copied within the meaning of s 14 of the Copyright Act.
737 The question of substantiality is one of mixed law and fact in the sense that it requires the judge to apply a legal standard to the facts as found: Designers Guild Ltd v Russell Williams (Textiles) Ltd [2000] 1 WLR 2416 at 2423 (Lord Hoffman). To the same effect is the following statement of Wilson J in SW Hart v Edwards Hot Water Systems (1985) 159 CLR 466 at 482:
... the question whether there has been a reproduction is a question of fact and degree depending on the circumstances of each case. The emphasis upon quality rather than quantity directs attention to the significance of what is taken.
738 In Ladbroke, Lord Pearce stated the well-known test concerning “substantial part” as follows (at 293):
… Whether a part is substantial must be decided by its quality rather than its quantity. The reproduction of a part which by itself has no originality will not normally be a substantial part of the copyright and therefore will not be protected. For that which would not attract copyright except by reason of its collocation will, when robbed of that collocation, not be a substantial part of the copyright and therefore the courts will not hold its reproduction to be an infringement. It is this, I think, which is meant by one or two judicial observations that “there is no copyright” in some unoriginal part of a whole that is copyright. They afford no justification, in my view, for holding that one starts the inquiry as to whether copyright exists by dissecting the compilation into component parts instead of starting it by regarding the compilation as a whole and seeing whether the whole has copyright. It is when one is debating whether the part reproduced is substantial that one considers the pirated portion on its own.
739 It is important to emphasise that the relevant copyright works in Ladbroke (the betting coupons) were a collocation, or compilation, of information. The statements of principle in that case concerning infringement are necessarily framed having regard to the nature of the copyright work and the features and characteristics of the work that led to the conclusion that the work was original for the purposes of subsistence of copyright.
740 In Data Access, the High Court considered the applicable principles in the context of computer programs. The plurality (at [83]) endorsed the approach taken by Mason CJ in dissent in Autodesk Inc v Dyason (No 2) (1993) 176 CLR 300 (Autodesk (No 2)) at 305. After quoting the above passage of Lord Pearce from Ladbroke, Mason CJ said (citations omitted):
… in the context of copyright law, where emphasis is to be placed upon the ‘originality’ of the work’s expression, the essential or material features of a work should be ascertained by considering the originality of the part allegedly taken. This is particularly important in the case of functional works, such as a computer program, or any works which do not attract protection as ends in themselves (eg, novels, films, dramatic works) but as means to an end (eg, compilations, tables, logos and devices).
741 The plurality in Data Access continued (at [84]-[86], citations omitted):
There is great force in the criticism that the “but for” essentiality test which is effectively invoked by the majority in Autodesk (No 2) is not practicable as a test for determining whether something which appears in a computer program is a substantial part of it. For that reason, we prefer Mason CJ’s opinion that, in determining whether something is a reproduction of a substantial part of a computer program, the “essential or material features [of the computer program] should be ascertained by considering the originality of the part allegedly taken”.
In order for an item in a particular language to be a computer program, it must intend to express, either directly or indirectly, an algorithmic or logical relationship between the function desired to be performed and the physical capabilities of the “device having digital information processing capabilities”. It follows that the originality of what was allegedly taken from a computer program must be assessed with respect to the originality with which it expresses that algorithmic or logical relationship or part thereof. The structure of what was allegedly taken, its choice of commands, and its combination and sequencing of commands, when compared, at the same level of abstraction, with the original, would all be relevant to this inquiry.
That being so, a person who does no more than reproduce those parts of a program which are “data” or “related information” and which are irrelevant to its structure, choice of commands and combination and sequencing of commands will be unlikely to have reproduced a substantial part of the computer program. We say “unlikely” and not “impossible” because it is conceivable that the data, considered alone, could be sufficiently original to be a substantial part of the computer program.
742 The High Court affirmed those principles in IceTV which, like Ladbroke, was a case concerning a literary work that was a compilation of information. Nine prepared and published programme guides for the Nine Network (the “weekly schedules”). The weekly schedules were prepared using Nine’s database, and contained starting times and titles for that week, as well as other information, such as whether the programme was a repeat or live, format information, classification, consumer advice and programme synopses. Nine provided the weekly schedules to third party aggregators, who produced aggregated guides for scheduled programmes for each television channel. IceTV compiled and provided a subscription-based electronic television programme guide (the “IceGuide”). The IceGuide displayed details of programmes to be broadcast by free-to-air television stations. When preparing the IceGuide, IceTV employees predicted the date, time, and title of the programmes proposed to be broadcast based on what was broadcast on the same day the previous week, and compared it with the relevant aggregated guide. Where there was a discrepancy, the IceGuide was amended to reflect the aggregated guide. The IceGuide did not use the synopses of programmes in the aggregated guides. Nine alleged that, in preparing and publishing the IceGuide, IceTV infringed Nine’s copyright in its weekly schedules by indirectly reproducing in a material form a substantial part of each weekly schedule, being the time and title information as arranged in the schedule. Nine alleged that each weekly schedule was a “compilation” and therefore an original literary work in which copyright subsisted, and which copyright Nine owned. At trial, IceTV accepted that copyright subsisted in each weekly schedule as an original literary work owned by Nine, but denied infringement. On appeal, one of the questions for determination was whether the time and title information which was reproduced in the IceGuide constituted a “substantial part” of the weekly schedules so as to constitute infringement. In two separate judgments, the High Court unanimously answered that question in the negative.
743 In their joint judgment in IceTV, French CJ, Crennan and Kiefel JJ emphasised the relationship between the features and characteristics of the work that lead to the conclusion that the work was original for the purposes of subsistence of copyright, and the question of infringement. Their Honours observed (at [28]-[29], citations omitted):
Copyright does not protect facts or information. Copyright protects the particular form of expression of the information, namely the words, figures and symbols in which the pieces of information are expressed, and the selection and arrangement of that information. That facts are not protected is a crucial part of the balancing of competing policy considerations in copyright legislation. The information/expression dichotomy, in copyright law, is rooted in considerations of social utility. Copyright, being an exception to the law’s general abhorrence of monopolies, does not confer a monopoly on facts or information because to do so would impede the reading public’s access to and use of facts and information. Copyright is not given to reward work distinct from the production of a particular form of expression.
These concepts are relevant to the determination, called for by the Act, of whether a part reproduced is a “substantial part” of a work in which copyright subsists.
744 Their Honours confirmed that, in order to assess whether material copied is a “substantial part” of an original literary work, it is necessary to consider not only the extent of what is copied, but also the quality of what is copied (at [30]) and that a factor critical to the assessment of the quality of what is copied is the “originality” of the part which is copied (at [32]). With reference to the facts and reasoning in Ladbroke, their Honours stated (at [37]) that “where the part reproduced did not originate with the author, so that the author would not have copyright in the part standing alone, the part reproduced will not be a substantial part”. Their Honours added, however, that the fact that a part reproduced originates from the author does not, of itself, mean that it is necessarily a substantial part of the whole work; originality in the context of infringement has a broader aspect (at [38]). After referring to the judgment of Mason CJ in Autodesk (No 2) and the plurality in Data Access, their Honours stated (at [40], citations omitted):
These cases direct attention to the degree of originality in the expression of the part of the work reproduced. The same point is made in the current edition of Copinger and Skone James on Copyright:
“[T]he more simple or lacking in substantial originality the copyright work, the greater the degree of taking will be needed before the substantial part test is satisfied.”
745 The joint judgment of Gummow, Hayne and Heydon JJ discussed a number of issues that are not pertinent to the present appeal. However, their Honours cautioned that the assessment of infringement, including the question whether a substantial part of a work has been copied, cannot be reduced to a question whether a person has appropriated the skill and labour of another (at [131]).
746 In the course of argument in the present appeal, the parties relied on a number of first instance decisions concerning the question whether a substantial part of a copyright work had been copied including the following decisions that concerned computer programs: CA Inc v ISI Pty Ltd (2012) 201 FCR 23; IPC Global Pty Ltd v Pavetest Pty Ltd (No 3) [2017] FCA 82; 122 IPR 445; University of Sydney v ObjectiVision Pty Ltd [2019] FCA 1625; 148 IPR 1. It is unnecessary to refer specifically to those decisions in this context. Each applied the principles set out above to the facts and circumstances of the case. Whilst each of those decisions concerned computer programs that had been issued in successive versions, the issue raised by Hytera on this appeal was not raised in those cases.
747 When analysed, the principles concerning the assessment of “substantial part”, as elucidated in Ladbroke, Data Access and IceTV, do not support Hytera’s contention. The crux of Hytera’s contention is that Motorola had failed to show that the portions of its source code which were copied into the impugned Hytera source code were original. Although it was not in dispute that each of the Motorola Works was a literary work in which copyright subsisted, Hytera contended that Motorola had to demonstrate that each part of the source code which it alleged had been copied by Hytera was original, in the sense of not having been copied by Motorola from elsewhere and, in particular, not copied from earlier iterations of the same source code (developed by Motorola over time). The flaw in Hytera’s contention is to assert that the copied parts of the Motorola Works that had been drawn from earlier Motorola software necessarily lacked “originality” for the purposes of assessing whether those parts were a substantial part of the Motorola Works.
748 The principles elucidated in Ladbroke, Data Access and IceTV recognise that, within a work in which copyright subsists, different parts of the work may have different degrees of originality. The assessment of whether a part of the work that is copied is a substantial part for the purposes of the Copyright Act will be affected by the degree of originality in that part. At one end of the spectrum are copyright works that consist of a compilation of information, in respect of which (typically) there is no originality (and indeed no copyright) in the information that is compiled, and where the originality only resides in the form of compilation. In such a case, the copying of the information, but not the form of compilation, will not infringe copyright. At the other end of the spectrum are works that might be described as wholly original (whilst recognising that the vast majority of works have elements that are derivative of other work). When assessing, in such cases, whether a part of the work that is copied is a substantial part, it remains relevant to consider the degree of originality in that part; however, as explained in Data Access, originality of the part copied is assessed by reference to the essential or material features of the copyright work.
749 In that context, we respectfully agree with the primary judge that, where a work has been created, in part, from a pre-existing work, two situations may be usefully distinguished from each other: the first is a work which reproduces extracts from another work (such as an anthology); and the second is a work which builds on earlier versions of itself (PJ [1234]). In respect of the former, if the part copied did not originate with the author of the anthology, it will not be a substantial part (PJ [1235], citing IceTV at [37]). In the case of the latter, provided the relevant version of the work involved sufficient intellectual and/or creative effort in reviewing and revising the work, the whole of the work will be an original work (PJ [1236]-[1243], citing JR Consulting). That is not to suggest, in the case of a work which builds on earlier versions of itself, that the question of originality of the part copied has no relevance to the assessment of whether the part copied is a substantial part of the work. As explained by French CJ, Crennan and Kiefel JJ in IceTV, originality in the context of infringement has a broader aspect (at [38]); it is necessary to consider the degree of originality in the expression of the part of the work reproduced (at [40]). It does mean, though, that Hytera’s contention must be rejected. Contrary to Hytera’s contention, in the case of a work that builds on earlier versions of itself, it is not necessary for the copyright owner to show that the parts of the work which were copied were original in the sense of not having been copied from earlier iterations of the work developed by the author over time. The primary judge was correct to conclude (at [1250]) that, where successive updates of software are released and originality is conceded for the purposes of subsistence, an argument for infringement purposes that a substantial part of a particular version of the software has been taken is not defeated by showing that the part in question derives from antecedent code.
750 We also reject Hytera’s submission that the primary judge treated the existence of originality in the context of subsistence, and the question of originality of part of a work for the purpose of infringement, as the same inquiry. It is clear from the primary judge’s reasons, read as a whole, that his Honour well understood that subsistence and infringement involved separate enquiries. His Honour did not reason that, because Motorola had proved (and Hytera had admitted) that copyright subsisted in the Motorola Works as original literary works, the parts copied by Hytera had sufficient originality to constitute a substantial part of the Motorola Works. Indeed, for the most part, his Honour concluded that the parts copied did not constitute a substantial part of the Motorola Works. Rather, his Honour merely rejected Hytera’s contention that, in establishing infringement, Motorola was required to prove that the parts of the Motorola Works that were copied by Hytera were not derived from antecedent code.
751 Although the questions of subsistence and infringement are separate questions, the authorities discussed above explain that they are related through the concept of originality. The nature of the copyright work and the features and characteristics of the work that support a conclusion that the work is original for the purposes of subsistence of copyright are relevant to the assessment of infringement, particularly in the context of assessing whether a substantial part of a work has been copied. For that reason, evidence concerning the making of the work has relevance to the overall assessment of originality both on the question of subsistence and the question of infringement. In the present case, the primary judge observed that Motorola led a great deal of evidence about the manner in which the Motorola Works were made, which evidence was directed at meeting Hytera’s initial non-admission that copyright subsisted in the Motorola Works (PJ [1251]). At trial, Hytera abandoned that defence and admitted subsistence. Given the admission, his Honour expressed his findings with respect to the making of the Motorola Works in relatively brief terms, but which are nonetheless significant (at [1253]-[1255]):
In fact, the 11 works are not merely the result of review and revision of earlier code. The 11 works in suit were part of the Matrix DMR project which began in 2003. Motorola had not manufactured DMRs before then and the Matrix program was designed to provide an advance over its existing analogue models. The 2005 DMR Standard was published two years before Motorola’s devices came to market in early 2007. As such, the three sets of firmware (the Mobile Firmware, the Portable Firmware and the DSP Firmware) were an attempt to create an entirely new product range. As the reasoning above in relation to the patents in suit demonstrates, the creation of a system which gave effect to the kind of two timeslot TDMA system that the 2005 DMR Standard required was no simple undertaking. The difficulties it presented are significantly underscored, in my opinion, by the failure of the Hytera DMR program to surmount them.
On the other hand, it may readily be accepted that much of what was contained in the software developed under the Matrix program was not brand new. Motorola had made radios before and it is evident that it did not begin its development of the firmware from scratch. For example, it had had to deal with the interface between the user and the device before so this was not a new problem. The Darwin Ergonomics Platform was not new when it was introduced into the DMR devices since it had been used in analogue devices. But neither was it the same. It had to be adapted to work in a new operating environment. It was not simply a case of copying the platform over without any changes. Indeed, the process of development took nearly four years. Hundreds of computer engineers worked on it.
In that circumstance, I do not hesitate to conclude that the 11 works are themselves substantial original works. Whilst it is true that earlier code was reused, a better description would be to say that it was adapted to the new devices. As such, it clearly meets the requirement for careful revision and review flowing from JR Consulting. No doubt, this why Hytera did not ultimately contest the originality of the 11 works from the standpoint of subsistence.
752 As the primary judge found, given the evidence adduced by Motorola, Hytera’s admission that copyright subsisted in the Motorola Works was inevitable (PJ [1251]). The above findings are also relevant, however, to the question whether the parts of the Motorola Works copied by Hytera were a substantial part of the Motorola Works. The findings do not, of course, determine that question; but the assessment of substantiality proceeds from a foundation in which the Motorola Works have been found to be original computer programs developed by Motorola for an entirely new product range comprising DMRs. It will be necessary to return to that evidence in connection with the next grounds of appeal concerning the question whether the Hytera source code involved the copying of a substantial part of the Motorola Works.
753 For the foregoing reasons, ground 1 of Hytera’s amended notice of appeal and the associated grounds and contentions (comprising grounds 2(e)-(f), 3(b)-(c), 4(a) and 5(a) of the amended notice of appeal and grounds 1 and 3 of Hytera’s amended notice of cross-contention) should be rejected.
C.7 Appeal grounds concerning whether the impugned Hytera source code was a copy of a substantial part of the Motorola Works
Overview
754 As stated earlier, the primary judge concluded that only the following two segments of Motorola source code, copied by Hytera, involved the copying of a substantial part of a Motorola Work:
(a) lines 227-287 of the file named rs_xlt_utilities.c, which the primary judge concluded was a substantial part of the Xlate program (PJ [1670], [1684]), the Darwin Ergonomics Platform (PJ [1729]) and the Portable and Mobile Firmware (PJ [1732] and [1798]); and
(b) the file named SerialHalBuffer.h, which the primary judge concluded was a substantial part of the HAL Serial Buffer program (PJ [1933]) and the DSP Firmware (PJ [1936]).
755 Each of Hytera and Motorola appeal that conclusion.
Hytera’s grounds of appeal
756 Hytera’s grounds of appeal are stated in grounds 2 to 5 of its amended notice of appeal. In respect of lines 227-287 of the file named rs_xlt_utilities.c, Hytera contests the finding that its code was objectively similar to the Motorola code, and also contests that the allegedly copied code constituted a substantial part of the Xlate program, the Darwin Ergonomics Platform or the Portable or Mobile Firmware. In respect of the file named SerialHalBuffer.h, Hytera contests the finding that the copied code constituted a substantial part of the HAL Serial Buffer program or the DSP Firmware.
Motorola’s grounds of appeal
757 Motorola’s grounds of appeal are stated in grounds 2 and 4 of its amended notice of cross-appeal.
758 By ground 2, Motorola contends that the primary judge erred in the manner in which his Honour determined whether the parts of Motorola’s code found to have been copied by Hytera constituted a substantial part of each of the EMT, UIT, Framer, L1 Timer and framerLib library programs, for the purposes of determining whether Hytera had infringed Motorola’s copyright in those Motorola Works. Motorola alleges three principal errors. First, rather than taking all of the code copied from each work and considering whether the copied code as a whole formed a substantial part of the work from which it was copied, the primary judge instead took small portions of code in isolation and considered whether the small portion on its own formed a substantial part of the work in question. Second, in undertaking that assessment, the primary judge focussed solely on the functionality of the small portions of source code rather than considering the originality of the code taken. Third, as a result of those approaches, the primary judge did not have proper regard to the evidence, including of Motorola’s witnesses, relevant to the issue of substantial part, and indeed criticised Motorola’s evidence and submissions on an incorrect basis.
759 By ground 4, Motorola contends that, had the primary judge assessed the issue of substantial part correctly, the primary judge ought to have found that the Motorola source code that was copied by Hytera constituted a substantial part of the EMT, UIT, L1 Timer, Framer and framerLib Library programs.
760 In its written submissions, Motorola confirmed that grounds 2 and 4 relate only to a sub-set of the relevant Hytera source code alleged at trial to have been copied from the relevant Motorola Works, being the portions of the Hytera code held by the primary judge to have been objectively similar to, and therefore on Hytera’s admission copied from, Motorola’s source code. In other words, Motorola does not appeal the primary judge’s findings with respect to objective similarity.
Motorola’s contention in the Hytera appeal
761 By ground 2 of its amended notice of contention in Hytera’s appeal, Motorola advances the same contention as advanced by grounds 2 and 4 of its amended notice of cross-appeal in respect of the other Motorola Works, namely Xlate, the Darwin Ergonomics Platform, the Mobile Firmware, the Portable Firmware, the HAL Serial Buffer and the DSP Firmware.
Hytera’s contention in the Motorola appeal
762 By grounds 2 and 4 of its amended notice of cross-contention in Motorola’s cross-appeal, Hytera contends that the primary judge erred in finding that parts of the impugned Hytera source code were objectively similar to parts of the Motorola Works.
763 By ground 5 of its amended notice of cross-contention in Motorola’s cross-appeal, Hytera contends that the primary judge also erred in finding that the Motorola source code that was copied by Hytera was material to the Motorola Works. Despite advancing that contention, Hytera’s submissions on the appeal failed to address the primary judge’s specific findings of materiality other than in respect of lines 227-287 of the file named rs_xlt_utilities.c and the file named SerialHalBuffer.h.
764 By ground 6, Hytera contends that, if the primary judge erred as contended by Motorola in its cross-appeal, the Full Court ought to find that Motorola failed to establish that the part of the Motorola Works taken by Hytera, considered as a whole for each copyright work, constituted a substantial part of the relevant copyright work.
Additional files
765 As noted earlier, by its written submissions on Hytera’s appeal, Motorola sought to appeal:
(a) the primary judge’s conclusion (at PJ [1737]) that it had failed to advance a case about additional files within the Mobile and Portable Firmware that were not within the Darwin Ergonomics Platform; and
(b) the primary judge’s conclusion (at PJ [1937]) that it had failed to advance a case about additional files within the DSP Firmware that were not within the L1 Timer, Framer, framerLib Library or the HAL Serial Buffer.
766 Hytera submitted that Motorola should not be permitted to challenge those findings on the appeal because the findings were not raised in Motorola’s amended notice of cross-appeal or in Motorola’s amended notice of contention in Hytera’s appeal.
Questions to be addressed
767 It can be seen that, by their respective notices of appeal and contention, the parties put in issue both the methodology adopted by the primary judge in assessing whether the Motorola source code that was copied by Hytera was a substantial part of the Motorola Works and many of the principal findings made by the primary judge on that question (save that Motorola does not challenge the primary judge’s findings on objective similarity). It is convenient to address the issues raised by the parties by their respective notices of appeal and contention by reference to the following questions:
(a) Did the primary judge err in the approach to infringement by considering whether small segments of Hytera source code which had been copied from a Motorola Work formed a substantial part of the relevant Motorola Work, rather than considering whether all of the Motorola source code that had been copied by Hytera collectively formed a substantial part?
(b) Did the primary judge err in the assessment of substantial part by exclusively focusing on the functionality of the segments of Motorola source code copied by Hytera and by failing to have regard to the originality of the Motorola source code copied by Hytera?
(c) If the primary judge erred in the manner postulated by questions (a) and (b), was the result that the primary judge did not have proper regard to the evidence of Motorola’s witnesses, or to Motorola’s submissions at trial, as to the significance of the Motorola source code copied by Hytera as a whole to each of the Motorola Works?
(d) Did the primary judge err in finding that parts of the impugned Hytera source code were objectively similar to parts of the Motorola Works (including in respect of lines 227-287 of the file named rs_xlt_utilities.c)?
(e) Did the primary judge err in finding that lines 227-287 of the file named rs_xlt_utilities.c constituted a substantial part of the Xlate program, the Darwin Ergonomics Platform or the Mobile or Portable Firmware?
(f) Did the primary judge err in finding that the file named SerialHalBuffer.h constituted a substantial part of the HAL Serial Buffer program or the DSP Firmware?
(g) Should Motorola be permitted to challenge the primary judge’s conclusions (at PJ [1737] and [1937]) that it had failed to advance a case about the additional files and should that challenge be upheld?
(h) Did Motorola fail to establish that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work?
(i) Conversely, ought the primary judge to have found that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work?
768 Each of those questions will be considered in turn.
Question (a): Did the primary judge err in the approach to infringement by considering whether small segments of Hytera source code which had been copied from a Motorola Work formed a substantial part of the relevant Motorola Work?
769 This is one of the headline issues on Motorola’s appeal. Motorola submitted that the primary judge erred by considering whether small portions of code, that were shown to have been copied by Hytera from a Motorola Work, considered in isolation, formed a substantial part of the relevant Motorola Work, rather than considering whether all of the code copied from a relevant work collectively formed a substantial part.
770 In response, Hytera submitted that the primary judge’s approach in considering whether specific segments of source code within files amounted to a substantial part was dictated by the way Motorola presented its case. In that regard, Hytera placed reliance on the fact that Motorola pleaded its case by reference to “instances of copying”, being specific groups of lines of source code within certain files in the Mobile and Portable Firmware and DSP Firmware. This is a reference to Motorola’s particulars of infringement in section D of the particulars of copyright claim, which in turn referenced Confidential Annexure 2 to the particulars, described earlier in these reasons. Hytera further submitted that Professor Wicker’s evidence also approached the question of substantial part by reference to each individual portion of code said to have been copied.
771 The manner in which the primary judge assessed whether the impugned Hytera source code involved the copying of a substantial part of the Motorola Works was described earlier in these reasons. It is clear that his Honour approached that question by reference to each segment of Motorola code that was allegedly copied by Hytera. His Honour explained that his approach involved two principal steps: first, it was necessary to determine, for each segment of Hytera source code, whether the code was objectively similar to the nominated lines of the Motorola source code (as Hytera had admitted that, if the code was objectively similar, it had been copied) (PJ [1302]); and second, if copying had occurred, it was necessary to determine whether the segment copied was a substantial part of the relevant program which Motorola put forward as a literary work (PJ [1303] and [1304]). His Honour then proceeded to make individual findings in respect of each segment of impugned Hytera source code.
772 Respectfully, that approach to the question of infringement involved error. Contrary to Hytera’s submissions, it was not an approach dictated by Motorola’s pleadings or evidence. Nor was it an approach taken in Motorola’s submissions at trial.
773 Motorola’s pleaded case was summarised earlier in these reasons. Motorola alleged that Hytera infringed copyright in the Motorola Works, and thereby contravened the Copyright Act, in two relevant ways. First, Motorola alleged that Hytera infringed copyright in the Motorola Works by importing the Hytera Devices into Australia for the purpose of sale and by selling the Hytera Devices in Australia. Relevantly for present purposes, the integers of that allegation included that each of the imported Hytera Devices embodied an adaptation of a substantial part of one or more of the Motorola Works. Second, Motorola alleged that Hytera infringed copyright in the Motorola Works by making certain versions of the Hytera Firmware available on its Partner Portal, authorising other persons to access and download the Hytera Firmware in Australia from the Partner Portal, and making further copies of the Hytera Firmware itself in Australia. Again, relevantly for present purposes, the integers of that allegation included that the relevant versions of the Hytera Firmware contained an adaptation of a substantial part of one or more Motorola Works. As stated earlier, the primary judge concluded (PJ [1224]) that those allegations required Motorola to demonstrate that a substantial part of the Motorola Works was copied into the Hytera source code which was then compiled into the Hytera Firmware (being object code) installed on the Hytera Devices or made available for download in Australia through the Partner Portal. Neither party challenges that synthesis of the statutory requirements.
774 Although Motorola’s case was complicated by the fact that it defined the Motorola Works at three levels of generality, the nature of its case was clear. The allegations of copyright infringement were not made in respect of each segment of Hytera source code that had been copied from Motorola’s source code. The allegations of copyright infringement concerned the whole of the Hytera Firmware within the Hytera Devices, and the whole of the Hytera Firmware that was made available for download in Australia and which was reproduced in Australia. Motorola’s case necessarily required an assessment of whether the impugned Hytera source code (from which the Hytera Firmware was compiled), considered as a whole, involved the copying of a substantial part of one or more of the Motorola Works.
775 Contrary to Hytera’s submission, that conclusion is not contradicted by Motorola’s particulars of infringement in section D of the particulars of copyright claim, including Confidential Annexure 2 to the particulars, described earlier in these reasons. Those particulars were given in respect of para 31D of Motorola’s pleading which alleged that each of the imported Hytera Devices embodied an adaptation of a substantial part of one or more of the Motorola Works, and were repeated in respect of para 31P of Motorola’s pleading which alleged that the Hytera Firmware made available in Australia contained an adaptation of a substantial part of one or more Motorola Works. The particulars identified each segment of Hytera source code which was relied on by Motorola as an alleged reproduction of Motorola source code within the Motorola Works. As discussed earlier, the primary judge was critical of the particulars because the relevant Motorola source code (which was allegedly copied into the particularised Hytera source code) was only categorised by reference to whether it formed part of the Mobile Firmware and Portable Firmware on the one hand and the DSP Firmware on the other hand. The particulars did not expressly categorise the relevant Motorola source code by reference to the lower level Motorola Works (that is, the Motorola Works that constituted programs within the Mobile Firmware, Portable Firmware and DSP Firmware). As also stated earlier, the primary judge’s frustration with that aspect of the presentation of Motorola’s case is understandable. Nevertheless, that difficulty is not relevant to the present issue. The particulars did not alter the nature of Motorola’s pleaded case. By particularising each instance of alleged copying by Hytera, and by identifying each segment of Hytera source code allegedly copied by reference to line numbers within a computer file, Motorola was not alleging copyright infringement by reference to each segment of code considered on its own. As paras 31D and 31P of Motorola’s pleading made clear, the particulars were given in support of Motorola’s allegation that the imported Hytera Devices embodied, and the Hytera Firmware made available in Australia contained, an adaptation of a substantial part of one or more of the Motorola Works.
776 Also contrary to Hytera’s submission, the manner in which Motorola instructed its expert witness, Professor Wicker, to express his opinions did not change the nature of the case presented by Motorola. That can be illustrated by reference to Professor Wicker’s affidavit dated 28 March 2019. Professor Wicker was asked to express an opinion on the question whether the impugned Hytera source code was objectively similar to Motorola source code within the Motorola Works and whether the similarity was consistent with the Hytera code having been copied from the Motorola code or whether there were any other reasons why they may be similar. That exercise necessarily focussed on each segment of impugned Hytera source code as identified in Motorola’s particulars of infringement. Professor Wicker was also asked to explain, in relation to Motorola source code within a Motorola Work that Professor Wicker considered had been copied into Hytera source code, the “role and importance of that source code to the Motorola Work”. It can be accepted that that latter question involved a degree of ambiguity. At one level, the question might be taken to require an opinion concerning the role and importance of each segment of Motorola source code that had been copied by Hytera. At another level, though, the question can be understood as requiring an opinion with respect to all segments of Motorola source code within a Motorola Work that had been copied by Hytera. As it turned out, Professor Wicker expressed his opinions concerning the role and importance of the copied Motorola source code at both levels.
777 Professor Wicker’s substantive expert evidence was divided into four sections. In the first section, Professor Wicker explained background source code concepts including certain computer file types, functions, variables, macros and comments. In the second section, Professor Wicker described the Motorola Works that were relevant to the code he was asked to examine. In that section, Professor Wicker explained the function, structure and features of the relevant Motorola Works at both the second level of generality (for example, the Darwin ergonomics platform) and the third level of generality (for example, Xlate, EMT and UIT). In the third section, Professor Wicker compared the impugned Hytera source code with the Motorola source code within the Motorola Works for the purpose of assessing objective similarity and the likelihood of copying, and expressed his conclusions in that regard. In connection with that task, Professor Wicker also produced annotations in respect of each segment of impugned Hytera source code explaining any differences with the relevant Motorola source code and providing comments on the function and significance of the Motorola source code to the Motorola Work or Works of which it formed part. In the fourth section, Professor Wicker brought together his opinions on the function and significance of the copied Motorola source code to the Motorola Work or Works of which the copied code formed part. Significantly, those opinions were expressed having regard to all of the segments of the Motorola source code that Professor Wicker considered had been copied by Hytera.
778 The manner in which Professor Wicker brought together his opinions on the function and significance of the copied Motorola source code to the Motorola Work or Works of which the copied code formed part can be illustrated by his opinions with respect to the EMT component of the Darwin ergonomics platform. Professor Wicker gave evidence to the effect that much of the code that he considered had been copied from the EMT program into the Hytera source code related to fundamental data structures (such as type definitions), macros and function prototypes that are used by EMT. Professor Wicker expressed the opinion that these are important parts of EMT as they set out the framework upon which the rest of the code comprising EMT is built, and the ‘language’ with which the code communicates with other code both within EMT and outside it, and that those parts of the code reflected much of the skill, effort and creativity that went into developing EMT.
779 The purpose of referring to the above evidence is not to express any conclusion that the evidence necessarily established infringement. The purpose is merely to negative Hytera’s submission that the primary judge’s approach to the assessment of infringement was dictated by Motorola’s expert evidence, specifically that Professor Wicker approached the question of substantial part by reference to each individual segment of code said to have been copied.
780 The expert witnesses for the parties conferred prior to the hearing and produced a Joint Expert Report (JER). The JER contained a summary of the experts’ opinions with respect to a series of questions, identifying points of agreement and disagreement. It is apparent from the JER that the experts assessed the materiality of the Motorola source code that was copied by Hytera by reference to the totality of the code that was copied. Question 4(a) asked the experts to identify any points of agreement or disagreement regarding their understanding of the nature and extent of any similarities between the impugned Hytera source code and each of the Motorola Works. In their agreed response, the experts expressed their agreement with respect to the functionality of each of the Motorola Works. Hytera’s expert, Mr Brown, commented on the quantity of the Hytera code that was a copy of Motorola code, stating: “Where Hytera source code is available, the [impugned Hytera source code] is approximately ½ the size of the corresponding Motorola code by line count” and “Of this, less than 60% of the [impugned Hytera source code] shows similarity to the Motorola code”. Motorola’s expert, Professor Wicker, summarised the key functional attributes of the copied Motorola source code by reference to each Motorola Work in turn. Similarly, question 4(c) asked the experts to identify any points of agreement or disagreement regarding their understanding of the extent that the impugned Hytera source code has been copied from part of a Motorola Work, the importance (or lack of importance) of that part to that Motorola Work, and any comments as to the creativity, complexity, or simplicity of the code comprised in that part. Again, in their agreed response, the experts expressed their agreement with respect to the functionality and features of each of the Motorola Works, but stated:
The experts disagree on the overall importance of these components as compared with the rest of the Motorola Works. There is also disagreement on how much of the code was copied and the importance of the portions of code that are copied.
The experts disagree on the importance of header files specifically. The experts agree that, in general, header files are developed in conjunction with other source code and the architecture of the code more generally. But there is disagreement on the relative importance of header files in general, and the importance of the copied header files specifically.
The experts agree that the concept of software layers (including abstraction layers, operating systems and signaling layers) were known in general. However, there is disagreement on the extent to which the Motorola specific architecture is unique and creative.
There is disagreement on how much of Motorola’s overall architecture was copied and the extent to which the copied portions are critical to that architecture.
While the experts agree that there may in some instances be some value in line counting as a measure of the copied code, there is disagreement on its overall validity in this case.
…
The experts agree that line counting is only one aspect in the assessment of software.
781 Again, the significance of referring to the JER is to observe that the questions framed for the expert witnesses and their responses were directed to Motorola’s pleaded case, that the imported Hytera Devices embodied, and the Hytera Firmware made available in Australia contained, an adaptation of a substantial part of one or more of the Motorola Works. The experts expressed their opinions on the function and significance of the whole of the copied Motorola source code to the Motorola Work or Works of which the copied code formed part.
782 Motorola’s submissions at trial were also consistent with its pleaded case. As noted earlier in these reasons, the primary judge frequently criticised Motorola for having failed to advance submissions concerning the materiality of a specific segment of computer code within a file that formed part of a Motorola Work that had been copied. The primary judge frequently found that, in the absence of submissions, Motorola had failed to establish that the segment of computer code was material to the operation of the relevant Motorola Work. Motorola submitted on this appeal that most of those criticisms were the result of the primary judge adopting an erroneous methodology to the question whether the impugned Hytera source code was a copy of a substantial part of the Motorola Works. To a large extent, that submission must be accepted. Motorola’s submissions at trial summarised the case advanced by Motorola and the evidentiary basis in support of that case: that the source code within each of the Motorola Works was created over many years through substantial skill and labour supporting a conclusion of a significant degree of originality; that the question whether the copied code was a substantial part of a Motorola Work involved an assessment of the originality of the copied code, which includes an assessment of the skill and labour involved in its creation, and is not determined merely by reference to the quantity (lines of code) of the copied code; and that the copied code replicated important structural features of the relevant Motorola Work.
783 Respectfully, the primary judge was in error to approach the question of infringement by considering whether small segments of Hytera source code which had been copied from a Motorola Work formed a substantial part of the relevant Motorola Work. In light of the case brought by Motorola, that was not the question to be determined. The question to be determined was whether, in respect of each of the Motorola Works, the totality of the Motorola source code copied by Hytera (into the impugned Hytera source code) was a substantial part of the Motorola Work. It follows that Motorola’s appeal must be upheld on this ground.
Question (b): Did the primary judge err in the assessment of substantial part by exclusively focusing on the functionality of segments of copied source code and by failing to have regard to the originality of the source code taken from the relevant Motorola Work?
784 This is also a headline issue on Motorola’s appeal. The issue is related to the immediately preceding issue in that, as explained above, the primary judge’s methodology was to assess whether individual segments of copied code were a substantial part of the relevant work. Nevertheless, by this ground Motorola raises a discrete issue concerning the test for assessing whether copied computer code constitutes a substantial part of the program (work) from which it is copied.
785 Motorola submitted that the primary judge erred in the assessment of substantial part by exclusively focussing on the functionality of individual lines of source code and by failing to have regard to the originality of the code taken from the relevant Motorola Work. Motorola argued that, particularly in the context of computer code, the question of substantial part is to be determined by reference to the originality of the part taken, including considering whether the creation of that part involved effort, skill and creativity. Motorola argued that the primary judge incorrectly treated “materiality” and “originality” as two separate requirements, with the former satisfied only if the code had (direct) functional significance, rather than assessing materiality by considering originality. Motorola submitted that the primary judge’s error was apparent from his Honour’s statement that, to establish that a substantial part of a program had been taken “it is necessary for Motorola to demonstrate that the lines of code are material to the operation of the program and that they are original” (at PJ [1303]). Motorola submitted that the error was also evident in the primary judge’s analysis of whether small portions of code were “material” to the relevant Motorola Work where his Honour paid no regard to originality in the context of assessing materiality and frequently noted that in cases where materiality was not established it was therefore “not necessary to reach a view on originality” (PJ [1350], [1353], see also [1404]). Motorola further submitted that, to the extent that the primary judge referred to the evidence of Motorola’s software engineers, for example Mr Ley (in relation to the EMT and UIT works) and Mr Simms (in relation to the FramerLib, L1 Timer and Framer works), his Honour did so in order to consider the functional significance of the lines of code in question (PJ [1380], [1388], [1824], [1842]), whereas the lay evidence also established that significant creativity and intellectual effort went into the form of expression used by Motorola’s engineers.
786 In response, Hytera submitted that the primary judge’s approach to assessing materiality of copied computer code, by considering its function, is consistent with the authorities. Hytera argued that it is relevant to have regard to the originality with which a computer program expresses the algorithmic or logical relationship between the function desired to be performed and the device. Unless the primary judge knew what result or function the objectively similar code enabled, he was not in a position to determine whether it formed a material or substantial part of Motorola’s Works.
787 The primary judge’s summary of the applicable principles concerning the assessment of “substantial part” in the context of computer code has been referred to earlier in these reasons. His Honour stated that, to determine whether lines of copied code were a substantial part of the relevant Motorola Work, it was necessary for Motorola to demonstrate that the lines of code were material to the operation of the program and were original (in the infringement sense) (PJ [1303], emphasis added). His Honour listed the main issue for determination, which included as separate issues the questions whether the lines of code were material to the work in suit and whether the lines of code were original in the infringement sense (PJ [1304], items (5) and (6)). Later, his Honour explained his approach to the question of copying a substantial part of the source code as follows (PJ [1326]):
… In relation to substantial part, Motorola must establish that each copied portion of its code was both original (Computer Edge Pty Ltd v Apple Computer (1986) 161 CLR 171 at 182) and that it constituted a material or essential feature of the EMT: IceTV at [158]-[159]; Data Access at [84]. In determining what is material or essential it is not appropriate to approach the matter on a ‘but for’ basis, i.e. by asking whether the program would work without it: Data Access at [81]-[84]. Instead the Court is to engage in a process of qualitative abstraction of the material features of the computer program allegedly copied: IceTV at [158]-[159]. Generally speaking, the quality of what is taken is more important than the quantity, but quantity is not completely irrelevant. It will be seen therefore that the substantial part analysis involves two inquiries: materiality and originality. I will consider these in relation to each file after the objective similarity analysis.
788 It is apparent from the foregoing statements of principle that his Honour considered that the assessment of whether copied code constituted a substantial part of the relevant program (work) involved two tests, which he referred to as materiality and originality. His Honour then proceeded to assess each segment of the impugned Hytera source code by reference to the tests of materiality and originality. As described earlier in these reasons, for most of the segments of impugned Hytera source code, his Honour concluded that the evidence was insufficient to enable him to understand the significance of the particular segment of code to the operation of the relevant Motorola Work, and therefore insufficient to persuade him that the segment of code was material. For some of the segments, his Honour also expressly concluded that, because he was not satisfied that the segment was material, it was unnecessary to reach a view on whether the segment was original. More often than not, having concluded that the segment was not material, his Honour made no express reference to originality.
789 Respectfully, the primary judge’s approach to the question whether copied code constituted a substantial part of a relevant program (work) involved error. There is only one question to be answered, being the statutory question of substantial part. The authorities provide guidance as to the factors that are relevant to that question, but the relevant factors are not separate tests or conditions to a finding of substantiality for the purposes of s 14 of the Copyright Act. Further, the authorities show that, in the context of computer code, it is erroneous to reduce the question of substantiality to the significance of the copied code to the operation (or function) of the computer or device. Respectfully, the primary judge erred by making a determination of whether copied code was a substantial part of the relevant Motorola Work solely on the basis of evidence (or lack of evidence) concerning the significance of the particular segment of code to the operation of the relevant computer program and the device of which it formed part.
790 The plurality judgment in Data Access provides the most extensive guidance to the assessment of substantiality in the context of computer code. Relevant passages from Data Access have been reproduced earlier in these reasons. Nevertheless some repetition, and indeed expansion, is required for the purposes of the present issue.
791 In Data Access, the plurality stated their agreement with the following observations of Mason CJ in Autodesk (No 2) (at 305, citations omitted):
It is clear that the phrase ‘substantial part’ refers to the quality of what is taken rather than the quantity. In Ladbroke (Football) Ltd v William Hill (Football) Ltd, Lord Pearce stated:
“Whether a part is substantial must be decided by its quality rather than its quantity. The reproduction of a part which by itself has no originality will not normally be a substantial part of the copyright and therefore will not be protected. For that which would not attract copyright except by reason of its collocation will, when robbed of that collocation, not be a substantial part of the copyright and therefore the courts will not hold its reproduction to be an infringement. It is this, I think, which is meant by one or two judicial observations that "there is no copyright" in some unoriginal part of a whole that is copyright.”
As this statement makes clear, in determining whether the quality of what is taken makes it a “substantial part” of the copyright work, it is important to inquire into the importance which the taken portion bears in relation to the work as a whole: is it an ‘essential’ or ‘material’ part of the work?
In this case, it is argued by the appellants that such an inquiry compels an affirmative answer as the look-up table is essential to the operation of the AutoCAD locking mechanism. Such an argument, however, misconceives the true nature of the inquiry and seeks to re-introduce by another avenue an emphasis upon the copyright work's function. True it is that the look-up table is essential to the functioning of the AutoCAD lock. However, in the context of copyright law, where emphasis is to be placed upon the 'originality' of the work's expression, the essential or material features of a work should be ascertained by considering the originality of the part allegedly taken. This is particularly important in the case of functional works, such as a computer program, or any works which do not attract protection as ends in themselves (eg, novels, films, dramatic works) but as means to an end (eg, compilations, tables, logos and devices).
792 The above passage makes three points in the context of computer code. First, the phrase “substantial part” refers to the quality of what is copied rather than the quantity. Second, in determining whether the quality of what is copied makes it a substantial part of the copyright work, it is important to inquire into the importance which the copied portion bears in relation to the work as a whole: is it an “essential” or “material” part of the work? Third, in this context “essential” does not mean essential to the operation of the computer code. Rather, in the context of copyright law, where emphasis is to be placed upon the originality of the work’s expression, the essential or material features of a work should be ascertained by considering the originality of the part allegedly taken.
793 After referring to the above observations of Mason CJ, the plurality in Data Access said (at [85]):
In order for an item in a particular language to be a computer program, it must intend to express, either directly or indirectly, an algorithmic or logical relationship between the function desired to be performed and the physical capabilities of the “device having digital information processing capabilities'”. It follows that the originality of what was allegedly taken from a computer program must be assessed with respect to the originality with which it expresses that algorithmic or logical relationship or part thereof. The structure of what was allegedly taken, its choice of commands, and its combination and sequencing of commands, when compared, at the same level of abstraction, with the original, would all be relevant to this inquiry.
794 It follows that the assessment of whether copied computer code constitutes a substantial part of a relevant computer program (work) is concerned with the quality of what is taken rather than the quantity. The quality of the copied code is to be assessed by reference to the importance which the code bears in relation to the work as a whole, which can also be described as the materiality of the code. But importance and materiality do not refer to the function of the code in the sense of whether the code is important or material to the operation of the computer or device in which the code is installed. Rather, importance and materiality refer to the originality with which the code expresses the functions sought to be performed by the computer or device, which includes such matters as the structure of the code and the choice and sequencing of commands.
795 The foregoing principles were also affirmed by the High Court in IceTV, albeit that IceTV did not concern computer software and was a “compilation” case. As noted earlier in these reasons, French CJ, Crennan and Kiefel JJ confirmed that, in order to assess whether material copied is a “substantial part” of an original literary work, it is necessary to consider not only the extent of what is copied, but also the quality of what is copied (at [30]). After observing that the question of whether a substantial part has been copied is a question of fact and degree, their Honours stated that a factor critical to the assessment of the quality of what is copied is the “originality” of the part which is copied (citing Mason CJ in Autodesk (No 2) at 305 and Data Access at [83]-[84]). Their Honours referred (at [40]) with approval to the following statement made by the authors of Copinger and Skone James on Copyright:
[T]he more simple or lacking in substantial originality the copyright work, the greater the degree of taking will be needed before the substantial part test is satisfied.
796 An issue that was considered by the High Court in IceTV is the relevance to the assessment of whether material copied is a substantial part of an original work of the “appropriation” of the author’s skill and labour. French CJ, Crennan and Kiefel JJ observed (at [49]) that it is always necessary to focus on the nature of the skill and labour, and in particular to ask whether it is directed to the originality of the particular form of expression. Their Honours explained (at [52]):
… The Act mandates an inquiry into the substantiality of the part of the work which is reproduced. A critical question is the degree of originality of the particular form of expression of the part. Consideration of the skill and labour expended by the author of a work may assist in addressing that question: that the creation of a work required skill and labour may indicate that the particular form of expression adopted was highly original. However, focusing on the “appropriation” of the author’s skill and labour must not be allowed to distract from the inquiry mandated by the Act. …
797 Gummow, Hayne and Heydon JJ disapproved, in stronger terms, of reasoning based on the “misappropriation” of the author’s skill and labour. Their Honours stated (at [131], references omitted):
The first is to emphasise the dangers when applying the Act of adopting the rhetoric of “appropriation” of “skill and labour”. A finding that one party has “appropriated” skill and labour, of itself, is not determinative of the issue of infringement of a copyright work. The Act does not provide for any general doctrine of “misappropriation” and does not afford protection to skill and labour alone.
798 In assessing the originality of a computer program and specific code within the program for the purposes of infringement, the functionality of the code cannot be ignored because it is intrinsic to the nature of the copyright work. As observed by Mason CJ in Autodesk (No 2) at 305, a computer program is a “functional” work. That fact is reflected in the definition of “computer program” in s 10 of the Copyright Act, being “a set of statements or instructions to be used directly or indirectly in a computer in order to bring about a certain result”. The relevant question is, though, in what manner is the functionality of computer code relevant to the assessment of infringement, and specifically the assessment of whether copied computer code constitutes a substantial part of a relevant computer program. The authorities discussed above show that the assessment of substantiality is focussed on the originality with which the code expresses the functions sought to be performed by the computer or device in which the code is installed, which includes such matters as the structure of the code and the choice and sequencing of commands. The assessment is not concerned with the function of the code in the sense of whether the code is important or material to the operation of the computer or device.
799 Respectfully, the primary judge erred in two respects in his approach to the assessment of the substantiality of the copied code. First, his Honour incorrectly applied two tests or conditions for the assessment, being materiality and originality, when there is only one question to be answered. Second, his Honour applied a test of whether the copied code was functionally material to the relevant Motorola Work in the sense of being significant or important to the operation of the DMR. Motorola’s submissions should be accepted that, particularly in the context of computer code, the question of substantial part is to be determined by reference to the originality of the code that has been copied, which requires consideration of the creative and intellectual contribution to the form of expression of the code, including such matters as the structure of the code and the choice and sequencing of commands. Such an enquiry does not concern any “misappropriation” of skill and labour. Rather, it requires an assessment of the extent of creative and intellectual contribution to the form of expression of the original code including the parts that have been copied, such that a qualitative assessment can be made whether the copied code is a substantial part of the relevant program (work). It follows that Motorola’s appeal must be upheld on this ground.
Question (c): If the primary judge erred in the manner postulated by questions (a) and (b), was the result that the primary judge did not have proper regard to the evidence of Motorola’s witnesses, or to Motorola’s submissions at trial, as to the significance of the copied source code as a whole to each of the Motorola Works?
800 Motorola submitted that, as a result of the foregoing errors in the assessment of substantial part, the primary judge did not have proper regard to the evidence of Motorola’s witnesses, or to Motorola’s submissions at trial, as to the significance of the copied material as a whole to each of the Motorola Works. With respect to evidence, Motorola submitted that the primary judge failed to have proper regard to Motorola’s lay evidence as to the originality of the parts copied, and also failed to have proper regard to Motorola’s expert evidence as to the materiality of the copied code. Motorola argued that, to the extent that the primary judge referred to Professor Wicker’s evidence, the reference was largely limited to Professor Wicker’s side-by-side presentation of lines of code. The primary judge was frequently critical of Professor Wicker’s evidence for failing to explain the function of particular lines of code, but his Honour made no reference to Professor Wicker’s evidence on the significance of the copied code or even to the JER where the experts’ agreements and disagreements on the importance of the copied code were summarised. Instead, the primary judge sought to independently review each segment of code and ascertain for himself what each segment did and whether that was functionally material. With respect to Motorola’s submissions at trial, Motorola argued that the primary judge’s criticisms of Motorola for making no submissions about the materiality of small segments of code was misplaced. Motorola argued that the primary judge was addressing the wrong question. The correct question was whether all of the copied code, considered as a whole, constituted a substantial part of the relevant Motorola Work. Motorola submitted that its submissions at trial addressed the correct question.
801 In response, Hytera submitted that the primary judge had proper regard to Motorola’s evidence and submissions in assessing substantiality. In that regard, Hytera placed reliance on the primary judge’s criticisms of the manner in which Motorola presented its case and submitted that the primary judge’s approach was reasonable in the circumstances. The primary judge’s criticisms of the manner in which Motorola presented its case are described earlier in these reasons.
802 It necessarily follows from the conclusions expressed in respect of questions (a) and (b) that question (c) is to be answered in the affirmative. It is clear from the primary judge’s lengthy judgment that his Honour had regard to the entirety of the evidence adduced by the parties. However, by reason of adopting an erroneous approach to the assessment of whether the copied code was a substantial part of relevant Motorola Works as discussed in respect of questions (a) and (b), the primary judge necessarily failed properly to have regard to the evidence of Motorola’s witnesses, or to Motorola’s submissions at trial, as to the significance of the copied code as a whole to each of the Motorola Works. That conclusion can be illustrated by reference to the following examples.
803 First, the primary judge found that Motorola led a great deal of evidence about the manner in which the Motorola Works were made, but his Honour considered that the evidence was only relevant to the issue of subsistence of copyright in the works (PJ [1251]). As that issue was admitted by Hytera before trial, his Honour dealt with the relevant evidence quite briefly. However, as submitted by Motorola, the lay evidence concerning the creation of the Motorola Works, including particularly the evidence given by Motorola software engineers such as Mr Ley (in relation to the EMT and UIT programs) and Mr Simms (in relation to the FramerLib, L1 Timer and Framer programs) is centrally relevant to the assessment of the originality of those works for the purposes of infringement, including particularly the identification and explanation of the structure of the code and the choice and sequencing of commands.
804 Second, although the judgment makes some reference to Motorola’s lay evidence in explaining the Motorola Works (see for example PJ [1310], [1315], [1336], [1804]-[1817]), at no point in the judgment did the primary judge assess and make findings about such matters going to the issue of originality of the Motorola Works generally and the copied code specifically. Rather, as submitted by Motorola, the judgment refers to that evidence principally for the purpose of considering the functional operation of particular lines of code (see for example PJ [1345], [1380], [1388], [1824], [1836]-[1844]).
805 Third, the judgment makes extensive reference to the evidence of Motorola’s expert witness, Professor Wicker, but does so on the same basis as the lay evidence. The judgment refers to Professor Wicker’s evidence principally for the purpose of considering the functional operation of particular lines of code (see for example PJ [1341], [1345], [1349]). Most strikingly, the judgment does not refer to Professor Wicker’s evidence concerning the function and significance of the copied Motorola source code as a whole to the Motorola Work or Works of which the copied code formed part, and does not refer to the agreement and disagreement of the expert witnesses on those matters as expressed in the JER.
806 The foregoing observations are not intended to suggest that the primary judge overlooked parts of the evidence adduced by the parties. Rather, the observations are only intended to illustrate that, by reason of adopting an erroneous approach to the assessment of substantial part, the primary judge necessarily failed properly to have regard to the evidence of Motorola’s witnesses as to the significance of the copied code as a whole to each of the Motorola Works.
Question (d): Did the primary judge err in finding that parts of the impugned Hytera source code were objectively similar to parts of the Motorola Works (including in respect of lines 227-287 of the file named rs_xlt_utilities.c)?
807 Hytera challenges a relatively small number of the primary judge’s findings of objective similarity. It is necessary to address each of the challenged findings in turn.
Lines 227-287 of the file rs_xlt_utilities.c within the Xlate program
808 Hytera contends that the primary judge erred in finding (at PJ [1656]-[1659]) that lines 41-122 of Hytera’s file ps_xlt_utilities.cpp were objectively similar to lines 227-287 of Motorola’s file rs_xlt_utilities.c within the Xlate program. Hytera submitted that the primary judge made the finding on the basis that the goal of both sets of code was similar although they achieved it by different means: the primary judge accepted evidence that the Motorola code used an “if/else chain” while the Hytera code used a “switch statement” (PJ [1659]). Hytera submitted that the primary judge focused unduly on the function of the code and failed to give proper consideration to material differences in the expression and form of the respective codes.
809 Hytera has not demonstrated error in the primary judge’s reasoning or conclusion. The evidence supported a finding of objective similarity. In his affidavit dated 25 July 2019 (which responded to Hytera’s second tranche of discovered source code), Professor Wicker expressed the summary opinion that there was a very high degree of similarity between each of the portions of the Hytera source code and the corresponding portions of the Motorola source code (at [17]). In respect of these specific portions of code, Professor Wicker expressed the opinion that, but for a small number of changes that had been made, the lines of code were almost identical (at [44]-[45]). Hytera focused on one change (the use of a “switch” statement rather than and “if/else” statement) which involved a relatively small portion of code. Hytera’s witness, Mr Brown, also confirmed the similarity between the lines of code, but gave evidence to the effect that the switch statement used in the Hytera code had a similar goal to the “if/else” statement in Motorola’s code. It is apparent that the primary judge formed the view that this one change in the code was insufficient to negative a finding of objective similarity. Objective similarity does not require identicality of expression. Contrary to Hytera’s submission, the primary judge did not focus unduly on the function of the code; his Honour was correctly focussed on the form of expression.
Lines 64-102 of the file com_cp_button_def.h within the EMT and UIT programs
810 Hytera contends that the primary judge erred in finding (at PJ [1403], [1691]) that lines 15-52 of Hytera’s file raf_input.h was objectively similar to lines 64-102 of Motorola’s file com_cp_button_def.h because his Honour failed to take into account the evidence of Mr Brown of key differences in structure between the files which affected memory usage.
811 Again, Hytera has not demonstrated error in the primary judge’s reasons or conclusion. It can be accepted that the primary judge did not refer expressly to Mr Brown’s evidence on these portions of code. However, that does not necessarily support an inference that his Honour failed to take into account that evidence. The primary judge’s reasons demonstrate that his Honour had close regard to Mr Brown’s evidence. His Honour stated that, having examined both codes, he agreed with Professor Wicker that they were objectively similar, a conclusion that was underscored because a spelling error at line 95 of the Motorola code also appeared at line 32 of the Hytera code (‘structutes’ instead of ‘structures’) (PJ 1403]). Mr Brown’s evidence was merely that, by reason of one change in the code, “the size and alignment of these overall structures will differ in the two codebases” and that, in Mr Brown’s opinion, the “difference is important”. Mr Brown’s evidence did not negative objective similarity. Again, objective similarity does not require identicality of expression.
The file rs_emt_imt_com.c within the EMT program
812 Hytera contends that the primary judge erred in finding (at PJ [1464]) that Hytera’s file ps_imt.cpp was objectively similar to Motorola’s file rs_emt_imt_com.c (part of the EMT work), because his Honour failed to take account of Mr Brown’s evidence that, although the structure of [Redacted] defined by the code in Hytera’s file was similar to Motorola’s, the source code itself was “quite different”.
813 Hytera’s contention mischaracterises the finding made by the primary judge. The evidence showed, and his Honour found (PJ [1443]), that the code within these files defined the form of an [Redacted]. [Redacted]. [Redacted]. [Redacted]. After considering the expert evidence, his Honour found that the Hytera code copied the structure of Motorola’s [Redacted] but not the contents of [Redacted] (PJ [1464]). In making that finding, his Honour did not fail to take account of Mr Brown’s evidence. The finding reflected Mr Brown’s evidence.
814 In making that finding, the primary judge did not blur the distinction between copying the idea and copying the form of expression. Although Hytera’s code defined an [Redacted] which contained [Redacted] specific to Hytera’s devices, the primary judge found that the code nevertheless had the same syntax as the Motorola code (see PJ [1460]-[1461]). It follows that, when the primary judge concluded that Hytera had copied the structure of the [Redacted] (PJ [1464]), his Honour was referring to more than the idea of the [Redacted]. His Honour was referring to the code syntax by which [Redacted] was defined. There is no error in that finding.
815 The finding made by the primary judge with respect to the objective similarity of the code syntax was not a finding that the Hytera code copied a substantial part of the Motorola code. Indeed, his Honour ultimately found that, because the Hytera code only copied the code syntax and not the [Redacted] embodied in the [Redacted], the Hytera code was not a copy of a substantial part of the Motorola code (PJ [1465]-[1466]). For the reasons explained earlier, however, his Honour erred in assessing the question of substantial part separately for each segment of copied code.
Lines 170-198 and 199-229 of the file cor_emt_user_defines.h within the EMT program
816 Hytera contends that the primary judge erred in finding (at PJ [1339]) that lines 170-198 and 199-229 of the file cor_emt_user_defines.h within the EMT program were copied into lines 120-147 and 148-178 of the Hytera file raf_app.h because his Honour failed to take into account that those lines of Hytera code were “commented out” and not compiled in the firmware installed on the devices that were imported into Australia.
817 Motorola submitted that this contention was not raised by Hytera’s notice of appeal or notice of cross-contention and should not be permitted to be raised. It can be accepted that the contention was not raised by Hytera’s notice of appeal or notice of cross-contention. The contention is not strictly an argument about objective similarity; it is an argument that the Hytera Devices imported into Australia and the Hytera Firmware made available in Australia did not contain an adaptation of the relevant Motorola source code because the copied source code was not compiled into Hytera’s firmware on its DMRs. As found by the primary judge (at PJ [1415] in respect of other lines of code), if Hytera source code that was copied from Motorola was not compiled into Hytera’s object code in the Hytera Devices or as part of the Hytera Firmware, an essential element in Motorola’s infringement case is missing.
818 Despite the foregoing observations, Hytera should be permitted to advance the contention. There is no procedural unfairness as the contention was addressed in Hytera’s written submissions and Motorola had a fair opportunity to respond to the contention.
819 Further, Hytera’s contention should be accepted. It was common ground between the experts that text within source code that is in the form of a comment is not compiled into object code (it is disregarded by the compiler). Both Professor Wicker (at [41]-[43] of his affidavit dated 28 March 2019) and Mr Brown (at [53] of his affidavit dated 6 December 2019) gave evidence that, in the C and C++ programming languages, comments are identified in the code in one of two ways:
(a) any text between the symbols /* and */ ; and
(b) any text following the symbol // on a line.
820 Both Professor Wicker and Mr Brown explained that, because comments are not executed (compiled into object code), it is possible to “comment out” operative code by placing it within the above comment symbols. The result is that the operative code will be treated as if it is a comment and not compiled. The evidence showed that almost all of the lines 120-147 and 148-178 of the Hytera file raf_app.h commenced with the symbol //. Mr Brown gave evidence in respect of those lines that the pre-processor would have discarded those lines and they would not have been used in Hytera’s firmware. Professor Wicker also gave evidence that those lines were “commented out”. Accordingly, Hytera’s contention with respect to those lines should be accepted.
Lines 54-127 of the file rs_emt_load_init_mode_info.c within the EMT program
821 Hytera contends that the primary judge erred in finding (at PJ [1424]) that lines 54-127 in Motorola’s source code file rs_emt_load_init_mode_info.c were copied in lines 66-91 of Hytera’s file ps_app_mgr.cpp, in circumstances where that file only contained information that was not compiled and a single line of code which [Redacted].
822 Hytera’s contention should be accepted for the reasons given in respect of the preceding segment of code. Apart from one line of code, Hytera’s source code is in the form of comment which the experts agreed is not compiled into object code. The one line of operative Hytera code is to [Redacted]. Professor Wicker accepted that the effect is to delete the “entire functionality provided by the function” (at [23] of Professor Wicker’s affidavit dated 25 July 2019).
The file svc_display_protocols.h within the UIT program
823 The primary judge found (at PJ [1693]-[1696]) that lines 139-140, 141-143, 179, 183-253 and 517 of the file svc_display_protocols.h within the UIT program were objectively similar to lines 40-41, 17-20, 15, 51-80 of Hytera’s file raf_display.h. In respect of that finding, Hytera contends that the primary judge erred in relation to lines 183-253 of the file svc_display_protocols.h and lines 51-80 of Hytera’s file raf_display.h in circumstances where only 4 of the 70 lines of Motorola code would be compiled into Hytera object code.
824 Hytera has not shown any error in the primary judge’s findings with respect to lines 183-253 of the file svc_display_protocols.h and lines 51-80 of Hytera’s file raf_display.h. It can be accepted that most of this segment of code is in the form of comments that would not be compiled into Hytera object code. Nevertheless, the operative lines of code, while few in number, were objectively similar. The fact that the operative lines of code were few in number is relevant to the assessment of substantial part, but does not undermine his Honour’s finding of objective similarity.
Lines 92-119 of the file cor_uit_user_defs.h within the UIT program
825 The primary judge found (at PJ [1705]) that lines 99-100, 106-106 and 112-116 of the file cor_uit_user_defs.h within the UIT program were objectively similar to lines 28-29, 37-38 and 31-35 of Hytera’s file raf_display.h. In respect of that finding, Hytera contends that the primary judge erred in circumstances where only 4 of the 28 lines of Motorola code would be compiled into Hytera object code.
826 Again, Hytera has not shown any error in the primary judge’s findings with respect to this segment of code. It can be accepted that most of this segment of code is in the form of comments. Nevertheless, the operative lines of code, while few in number, were objectively similar.
Question (e): Did the primary judge err in finding that lines 227-287 of the file named rs_xlt_utilities.c constituted a substantial part of the Xlate program, the Darwin Ergonomics Platform or the Mobile or Portable Firmware?
827 By Hytera’s second ground of appeal, Hytera contends that the primary judge erred in finding that lines 227-287 of Motorola’s file rs_xlt_utilities.c constituted a substantial part of the Xlate program (and the Darwin Ergonomics Platform and the Mobile and Portable Firmware). This is one of the headline issues on Hytera’s appeal. However, the contention has been rendered nugatory by the acceptance of Motorola’s principal ground of cross-appeal on the copyright issues (ground 2): that the primary judge erred by considering whether small portions of code, that were shown to have been copied by Hytera from a Motorola Work, considered in isolation, formed a substantial part of the relevant Motorola Work, rather than considering whether all of the code copied from a relevant work collectively formed a substantial part. The effect of accepting that ground of appeal is that the primary judge’s finding with respect to lines 227-287 of the file named rs_xlt_utilities.c must be reconsidered together with all other code that was copied by Hytera from, in turn, the Xlate program, the Darwin Ergonomics Platform and the Mobile and Portable Firmware.
Question (f): Did the primary judge err in finding that the file named SerialHalBuffer.h constituted a substantial part of the HAL Serial Buffer program or the DSP Firmware?
828 By Hytera’s third ground of appeal, Hytera contends that that the primary judge erred in finding that the file named SerialHalBuffer.h constituted a substantial part of the HAL Serial Buffer program (or the DSP Firmware). The contention has been rendered nugatory for the same reason as question (e).
829 Notwithstanding that conclusion, it is appropriate to address an additional argument advanced by Hytera with respect to the file named SerialHalBuffer.h, even though it is a relatively minor matter in the large sweep of this case. Hytera submitted that the primary judge erred in finding (at PJ [1932]) that Hytera had not argued at trial that significant portions of the file were copied by Motorola from the open source code for MySQL and were not original for that reason. For the following reasons, any error by the primary judge in that regard was not material.
830 At trial, Motorola alleged that Hytera had copied two related computer files within the HAL Serial Buffer: the SerialHalBuffer.h and the SerialHalBuffer.cpp. The file SerialHalBuffer.h is a header file and the file SerialHalBuffer.cpp is a source file. As found by the primary judge (at PJ [1331]-[1336]), when code is written in the C++ language, it is common to split the code between ‘header’ files (files with the suffix ‘.h’) and ‘source’ files (files with the suffix ‘.c’). Header files can be used to declare variables and function prototypes that can be used in multiple files without having to repeat the process of declaration in each file. During the process of compilation the source code picks up the declarations contained in the relevant header file.
831 The primary judge considered each of the source file SerialHalBuffer.cpp and the header file SerialHalBuffer.h in turn. His Honour addressed an argument advanced by Hytera that those files lacked originality because they were similar to the publicly available file NdbApiSignal.hpp which was available from the public resource MySQL in 2003, which was the time at which Mr Carter of Motorola wrote the first version of the source file SerialHalBuffer.cpp (and which was subsequently revised by Mr Simms of Motorola).
832 After considering the lay and expert evidence in some detail, the primary judge concluded in respect of the source file SerialHalBuffer.cpp (at PJ [1924]):
Having examined them, they are certainly not identical but they bear striking structural similarities. It is likely that Mr Carter used the MySQL file in the process of creating SerialHalBuffer.cpp. But I would not say that it has been copied. The adaptations are non-trivial. It seems to me that Mr Carter (and after him, Mr Simms) did more than just copy this code. Consequently, I do not accept Hytera’s submission that these lines of code are not original in the requisite sense.
833 Thus, the primary judge concluded that SerialHalBuffer.cpp had not been copied from the publicly available file NdbApiSignal.hpp and that SerialHalBuffer.cpp was an original work.
834 After considering the source file SerialHalBuffer.cpp in some detail, the primary judge’s reasoning with respect to the header file SerialHalBuffer.h was relatively brief. His Honour noted Mr Simms’s evidence that he had written most of the header file himself (PJ [1930]) and concluded (at PJ [1932]):
Turning then to originality, closely read, Hytera’s submissions did not contend that the header file had been copied from the MySQL resource. In light of Mr Simms’ evidence that he wrote the file, I accept that these lines are original.
835 It is contextually apparent that his Honour’s conclusion with respect to the header file SerialHalBuffer.h built upon his Honour’s reasoning with respect to the source file SerialHalBuffer.cpp. On the issue of originality, Hytera’s evidence and submissions had not drawn any significant distinction between the two files. Therefore, his Honour’s finding with respect to the originality of the source file was also applicable to the header file. Further, his Honour’s statement that, closely read, Hytera’s submissions did not contend that the header file had been copied from the MySQL resource, was correct. Hytera’s closing submissions (at paras 310 to 315) were that the header file SerialHalBuffer.h (and indeed the source file SerialHalBuffer.cpp) lacked originality; the submission did not go so far as to assert that either file had been copied from the MySQL resource.
836 For those reasons, Hytera has failed to demonstrate any material error in the primary judge’s conclusion that the header file SerialHalBuffer.h was an original work.
Question (g): Should Motorola be permitted to challenge the primary judge’s conclusions (at PJ [1737] and [1937]) that it had failed to advance a case about the additional files and should that challenge be upheld?
837 Motorola did not refer to the primary judge’s conclusion at PJ [1737] and [1937], that it had failed to advance a case about the additional files, in either its notice of cross-appeal or its notice of contention on Hytera’s appeal. Despite that, in its written submissions, Motorola submitted that the primary judge’s conclusion at PJ [1737] and [1937] was incorrect. Motorola argued that the primary judge arrived at that erroneous conclusion because his Honour had adopted an erroneous approach to the assessment of substantiality as discussed above: assessing whether each segment of copied code formed a substantial part of the relevant Motorola Work, and doing so by assessing whether the copied code was functionally material to the relevant Motorola Work in the sense of being significant or important to the operation of the DMR. Motorola accepted that it did not advance submissions relating to the function of each segment of code that had been copied by Hytera, but submitted that that was not the correct approach to the question of substantial part.
838 Motorola should be permitted to raise this issue on the appeal, notwithstanding its failure to raise the issue in either its notice of cross-appeal or its notice of contention on Hytera’s appeal. As Motorola raised the matter in its written submissions, Hytera had adequate notice of the issue to respond.
839 As noted earlier in these reasons, each of the additional files were listed in Confidential Annexure 2 to Motorola’s particulars of copyright infringement. Each was therefore formally part of Motorola’s copyright infringement case. Furthermore, Hytera adduced evidence in response to those particulars, which included the additional files, indicating that Hytera understood Motorola’s case in that regard. Respectfully, Motorola’s submission should be accepted that the primary judge’s conclusion at PJ [1737] and [1937], that Motorola had failed to advance a case about the additional files, was based on his Honour’s erroneous approach to the assessment of substantiality as discussed above. The case was advanced.
Questions (h) and (i): Did Motorola fail to establish that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work? Conversely, ought the primary judge to have found that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work?
840 On both appeals, Hytera advanced the contention that, by the manner in which it had presented its case, Motorola had failed to establish that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work. In support of that contention, Hytera largely relied on the criticisms that had been made by the primary judge of the manner in which Motorola had presented its case at trial. Conversely, Motorola advanced the contention that the primary judge ought to have found that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work.
841 Hytera’s reliance on the primary judge’s criticisms of the manner in which Motorola presented its copyright infringement case at trial is misplaced. For the reasons given earlier, many of the primary judge’s criticisms are affected by his Honour’s erroneous approach to the key issues. In particular, the primary judge frequently criticised Motorola for having failed to advance submissions concerning the materiality of specific segments of computer code. Respectfully, those criticisms were the result of the primary judge adopting an erroneous approach to the question whether the impugned Hytera source code was a copy of a substantial part of the Motorola Works. The errors were twofold: first, considering whether small portions of code, that were shown to have been copied by Hytera from a Motorola Work, considered in isolation, formed a substantial part of the relevant Motorola Work; and second, applying a test of whether the copied code was functionally material to the relevant Motorola Work in the sense of being significant or important to the operation of the DMR. The question of substantial part is to be determined by reference to the originality of the code that has been copied, which requires consideration of the creative and intellectual contribution to the form of expression of the code, including such matters as the structure of the code and the choice and sequencing of commands.
842 As noted earlier, Motorola’s submissions at trial summarised the case advanced by Motorola and the evidentiary basis in support of that case: that the source code within each of the Motorola works were created over many years through substantial skill and labour supporting a conclusion of a significant degree of originality; that the question whether the copied code was a substantial part of a Motorola Work involved an assessment of the originality of the copied code, which includes an assessment of the skill and labour involved in its creation, and is not determined merely by reference to the quantity (lines of code) of the copied code; and that the copied code replicated important structural features of the relevant Motorola Work. Having reviewed Motorola’s submissions and evidence at trial, we reject Hytera’s contention that, by the manner in which it had presented its case, Motorola failed to establish that the parts of the Motorola source code copied by Hytera, considered as a whole for each Motorola Work, constituted a substantial part of the relevant Motorola Work.
843 However, to this point, the Court is not able to determine whether Motorola’s claim of copyright infringement should succeed in whole or in part. By reason of the approach taken by the primary judge to the issues, relevant factual findings have not been made that would enable this Court to determine the case applying the methodology that the Court believes is correct. Furthermore, within the time allowed for the appeal to this point, the Court was not taken to the entirety of the evidence that might enable further factual findings to be made.
844 As discussed further below, the Court considers that the appropriate course is to conduct a further hearing at which the parties will be given an opportunity to advance further submissions in respect of the copyright infringement claims that arise on the appeal in accordance with the Court’s reasons. The appropriate orders are addressed at the end of these reasons.
C.8 Appeal grounds concerning whether the object code library files were an adaptation of a substantial part of the Motorola Works
Overview
845 By ground 3 of its amended notice of cross-appeal, Motorola contends that the primary judge erred in not finding, on the balance of probabilities, that the source code from which the Hytera library files raf_arm9.lib, rfhal_c55.lib and DmrDspLib.lib were compiled included code that was objectively similar to Motorola code forming or comprising a substantial part of the Motorola Works. The same contention is raised by ground 3 of Motorola’s amended notice of contention in Hytera’s appeal.
846 By ground 7 of Hytera’s amended notice of cross-contention, Hytera contends that the primary judge’s findings, that Motorola had failed to prove that the source code from which the Hytera library files raf_arm9.lib, rfhal_c55.lib and DmrDspLib.lib were compiled included code that was objectively similar to Motorola code, or that such code formed or comprised a substantial part of the Motorola Works, are further supported when the evidence concerning the “non-radio-specific files” is considered. Hytera did not advance specific written submissions on that contention and the contention appeared to be subsumed within its overall arguments in oral submissions. By reason of the considerations discussed below, it has been unnecessary to address this contention separately.
847 The facts and circumstances pertaining to the library files, and the primary judge’s consideration of them, have been summarised earlier in these reasons. To recap, in its second and third tranches of discovery, Hytera discovered three library files in object code named raf_arm9.lib, DmrDspLib.lib and rfhal_c55.lib. Hytera was unable to produce the source code from which those library files had been compiled. In the absence of Hytera’s source code, Motorola submitted at trial that the Court should infer that Hytera had copied a substantial part of Motorola’s source code in producing the Hytera source code from which the library files were compiled. The primary judge concluded that he was unable to draw that inference from the relevant facts and circumstances. Whilst his Honour found (at PJ [1577]) that within the missing Hytera source code there would have been tracts of code which were objectively similar to portions of Motorola’s source code, his Honour also found (at PJ [1578]) that there would have been tracts of code which were not objectively similar to the Motorola source code. His Honour concluded that because he was unable to determine which of the Motorola source code files were copied, Motorola had not proved that the missing Hytera source code contained tracts of source code which were objectively similar to the source code in any particular Motorola file (PJ [1584]). His Honour also concluded that, because he did not know what the particular Motorola source code files did (in a functional sense), he could not be satisfied that any part of Motorola’s source code that was copied by Hytera was material to the relevant Motorola Work (PJ [1585]).
Motorola’s submissions
848 Motorola advanced three principal submissions in support of this ground of appeal.
849 The first submission was that the primary judge’s conclusion with respect to the three library files was affected by his Honour’s erroneous approach to the question whether Hytera source code was a copy of a substantial part of the Motorola Works. In that respect, Motorola relied on its contentions (which have been accepted earlier in these reasons) that the primary judge erred, first, by considering whether small portions of copied code, considered in isolation, formed a substantial part of the relevant Motorola Work and, second, by applying a test of whether the copied code was functionally material to the relevant Motorola Work.
850 The second submission was that the primary judge’s reasoning in respect of the three library files hinged on his Honour’s assessment that, in respect of Motorola’s overall case that its source code had been copied, his Honour had found “in very many cases that objective similarity is not established” (PJ [1578]-[1579]). Motorola submitted that this reasoning involved error for the following reasons.
851 First, Motorola argued that the assessment was overstated (having regard to his Honour’s findings overall).
852 Second, Motorola argued that it was erroneous to extrapolate from circumstances in which Hytera had not deleted its source code to a circumstance in which Hytera had deleted its source code for the purpose of making the detection of infringement more difficult. In the course of argument on the appeal, Motorola submitted that the primary judge erred in failing to draw an adverse inference against Hytera by reason of its deliberate deletion of the source code from which the library files had been compiled. In that context, Motorola relied on the primary judge’s findings (at PJ [1540], [1551]) that the source code was deliberately deleted at the instigation of the ex-Motorola software engineers and his Honour’s findings (at PJ [1553]) that: much of the evidence which would have thrown light on the infringement suit has been lost; there is no legitimate reason for the deletion of the source code; and the deletion was a deliberate attempt to suppress evidence which might assist in an infringement suit. Motorola also referred to the evidence of its expert witness, Professor Rangan, that (at para 91 of his affidavit dated 26 March 2020):
It would be extremely irregular for a software company to no longer be in possession of the source code used to compile library files used in devices that it continues to sell. This is particularly the case for critical functionality such as the DSP firmware on Hytera’s DMR radio devices (which the rfhal_c55.lib library file relates to). This is because, in order to make modifications to the underlying code, for example in response to changes in processors or other parts, to fix technical bugs, or to add a feature, it would be necessary for developers to have access to the source code used to compile the library files. It is also important to keep the underlying source code as a reference, including for example for evaluation purposes. Accordingly, it is unimaginable to me that the source code used to compile library files would not be stored in a software company’s central repository along with the rest of the code used on its devices. Further, I can think of no legitimate reason, from a software engineering perspective, why a software company would no longer be in possession of the source code used to compile library files.
853 Third, Motorola argued that the primary judge had failed to have regard to the evidence concerning source code header files that were associated with the object code library files. In its closing submissions at trial, Motorola had submitted that “the extent of copying into the library files cannot be considered in isolation from the extent of copying in the header files associated with those library files”. In that regard, it had referred to the following evidence of Professor Wicker (at para 86 of his affidavit dated 26 March 2020):
… The header and other source files analysed from the same directories as these libraries are related to, not separate from, the library files. Hence, the matters I referred to in paragraph 89 of my second copyright affidavit regarding both the nature of copying from these header files, combined with the similarity in the files and identifiers in the library to which I refer above, in my opinion create an overwhelming likelihood that the Hytera libraries contain code copied from the Motorola Programs.
854 In its submissions on the appeal, Motorola submitted that objective similarity was established in the significant majority of cases in respect of the header files (asserting that, out of the 46 instances of copying pleaded by Motorola in relation to such header files that were available for inspection, the primary judge concluded that the Hytera code was objectively similar to the Motorola code in 44 cases).
855 Fourth, Motorola argued that the assessment did not give proper weight to the evidence concerning the disassembly of the library files, accepted by the primary judge (PJ [1527]), that the missing Hytera source code (from which the library files were compiled) used function names which were similar to or the same as the function names appearing in the Motorola source code.
856 The third submission advanced on this ground of appeal was that the Full Court is in as good a position as the trial judge to decide on the proper inference to be drawn from the facts established by his Honour’s findings (referring to Warren v Coombes at 551).
Hytera’s submissions
857 On this ground, Hytera advanced the following submissions.
858 First, the Full Court should give due weight to the primary judge’s findings of fact, recognising the primary judge’s advantages in hearing the entirety of the evidence including the expert evidence given concurrently. Second, the primary judge did not err by seeking to assess objective similarity by reference to specific segments of code. Third, the primary judge did not err in concluding that in very many instances Motorola had not established objective similarity between segments of code. In response to Motorola’s submissions concerning the copying of header files, Hytera submitted that Motorola had not established that those header files were associated with the library files in issue. Fourth, a significant factor in the reasoning of the primary judge was his Honour’s finding that there were examples in the evidence where Hytera functions with similar names to Motorola functions did not use objectively similar code (PJ [1529]-[1531]). Fifth, the primary judge had rejected Motorola’s submission that there had been “wholesale” copying of its code (PJ [1579]). Sixth, Motorola asked the court to draw the inference in respect of objective similarity in circumstances where Motorola had failed to undertake other investigations that were available to it to ascertain the source code from which the Hytera library files were compiled. While Motorola had adduced evidence in the form of a disassembly process, other types of investigations that were available included a decompilation process which would have yielded additional information.
859 In the course of argument on the appeal, Hytera also placed reliance on the primary judge’s finding (at PJ [1585]) that, because Motorola had not made submissions about the materiality of its source code files (which it alleged had been copied into Hytera source code files from which the library files had been compiled), his Honour could not be satisfied about the materiality of those files to the relevant Motorola Works.
Consideration
860 Respectfully, the primary judge erred in not drawing an inference of copying in favour of Motorola in respect of the library files in the circumstances of this case. This case is an exemplar of the circumstances in which the evidentiary principle encapsulated by the Latin maxim omnia praesumuntur contra spoliatorem (all things are presumed against the wrongdoer) may be applied. The evidentiary principle was stated by Sir Arthur Channell delivering the opinion of the Privy Council in The Ophelia (1916) 2 AC 206 (The Ophelia) at 229-230:
If any one by a deliberate act destroys a document which, according to what its contents may have been, would have told strongly either for him or against him, the strongest possible presumption arises that if it had been produced it would have told against him, ...
861 The principle is one of long-standing and was applied by the High Court (Dixon CJ, McTiernan and Williams JJ) in Allen v Tobias (1958) 98 CLR 367 in respect of a question of fact whether the defendant had executed an agreement, copies of which were subsequently destroyed by the defendant. In that case, the High Court cited the above statement in The Ophelia in support of an inference against the defendant that he had executed the agreement (at 375). In Katsilis v Broken Hill Pty Co Ltd (1977) 18 ALR 181, both the majority (Stephen, Mason, Jacobs and Murphy JJ) (at 203) and Barwick CJ in dissent as to the result (at 197-198) confirmed that no adverse inference would be drawn against a party who has lost or destroyed evidence if the loss or destruction is innocent. The authorities were discussed by Kenny J in Research in Motion v Samsung Electronics Australia Pty Ltd (2009) 176 FCR 66 at [25]-[34], where her Honour observed that the evidentiary principle applies where it is shown that a party has deliberately destroyed documents with the intention of destroying evidence. More recently, the principle was referred to by Bell, Keane and Nettle JJ in Berry v CCL Secure Pty Ltd (2020) 271 CLR 151 in the context of proof of loss and damage, where their Honours observed (at [29], citations omitted):
While a claimant bears the legal burden of establishing the amount of its loss or damage, the nature and circumstances of the wrongdoer’s conduct may support an inference or presumption that shifts the evidentiary burden. That accords with the principle encapsulated in Armory v Delamirie that, where a wrongdoer has destroyed or failed to produce evidence which the innocent party requires to show how much he or she has lost, it is just that the wrongdoer should suffer the resulting uncertainty. Hence, in that case, since the defendant by his wrongful conversion of the plaintiff’s stones, and failure to produce them at trial, had made it impossible for the plaintiff to prove the quality of them, the stones were presumed to be of the highest quality and value. …
862 The findings made against Hytera by the primary judge in this proceeding are damning of its conduct. As noted earlier, the primary judge found that the ex-Motorola engineers took with them to Hytera all of the computer source code for Motorola’s DMR device to provide themselves with a resource for the purposes of writing Hytera’s source code for its DMR device (PJ [1538]). His Honour characterised Hytera’s actions as a “substantial industrial theft” (PJ [5]) and found that Hytera’s software engineers engaged in industrial scale harvesting of Motorola’s source code and that they set out to make this as difficult to detect as possible (PJ [1576]). Most egregiously, and most relevantly for present purposes, the primary judge found that the source code from which the library file was compiled was deliberately deleted by or at the instigation of the ex-Motorola software engineers, that much of the deleted evidence would have thrown light on the infringement suit, and the deletion was a deliberate attempt to suppress evidence which might assist in an infringement suit (PJ [1553]). The evidence given by Professor Rangan explains why it is an extraordinary step for a software company to delete the source code used to compile object code (the library files) code used in devices that it continues to sell. Without the source code, the software developers would be unable to make modifications to the underlying code, whether in response to changes in processors or other parts, to fix technical bugs, or to add a feature.
863 The finding that the source code was deliberately deleted so as to suppress evidence which might assist in an infringement suit, when coupled with the other factual findings made by the primary judge concerning the library files, strongly supports an inference that the deleted source code would have revealed that it was a copy of a substantial part of the relevant Motorola source code.
864 The other factual findings made by the primary judge that support that inference are the following:
(a) Hytera had the opportunity to copy Motorola’s source code. In that regard, the primary judge found that the ex-Motorola engineers brought with them to Hytera all of Motorola’s source code both for the Mobile and Portable Firmware and also the DSP Firmware and did so to provide themselves with a resource from which they could later harvest that code for the purposes of writing Hytera’s source code (PJ [1538]).
(b) Hytera had the incentive to copy Motorola’s source code. In that regard, the primary judge found that at the end of 2007 Hytera’s DMR project was in disarray and Hytera had a motive to steal Motorola’s intellectual property (PJ [1536]).
(c) Hytera in fact copied some of Motorola’s source code. The judgment as a whole records that the primary judge found numerous instances of objective similarity between Motorola’s source code and Hytera’s source code and Hytera admitted copying where objective similarity was shown.
(d) Through a process of disassembly, it was shown that the library files contained many function names which were the same or similar to the function names in the Motorola source code (PJ [1527]). At the very least, this demonstrated that the missing source code, from which the library files were compiled, was fashioned from the Motorola source code (PJ [1531]). That conclusion was further supported by the finding that Hytera could not have developed its DMR software in the timeframe it did without using the Motorola source code (PJ [1573]).
865 On the basis of the above facts, the primary judge concluded (at PJ [1577]) that, within the missing Hytera source code, there were tracts of code which were objectively similar to portions of Motorola’s source code and that in some cases the copying would have been verbatim and in other cases there would have been cosmetic changes. However, his Honour also concluded (at PJ [1578]) that there were likely to be tracts of code in the missing Hytera source code which were not objectively similar to the Motorola source code, either because the code was written independently or because the Motorola code required changes because of differences with the Hytera DMRs. Reasoning by analogy from the Hytera source code that had not been deleted and had been adduced in evidence in the proceeding, the primary judge concluded (at PJ [1580]) that it is very likely that amongst the missing source code files there are files which are objectively similar to Motorola source code and that it is also quite possible that some of the missing source code files are not objectively similar. His Honour reasoned that he was unable to determine which files were copied, and therefore could not be satisfied on the balance of probabilities that any particular missing Hytera source code file was objectively similar to a Motorola source code file (PJ [1581]).
866 Respectfully, the primary judge erred in reasoning by analogy from the Hytera source code that had not been deleted and had been adduced in evidence in the proceeding. The fact that the ex-Motorola engineers had deliberately deleted Hytera’s source code relating to the library files to suppress evidence which might have assisted in an infringement suit placed the library files in a different category to all other Hytera Firmware for which source code was available. The deletion of the source code was egregiously wrongful conduct to evade detection of copyright infringement, exacerbating already wrongful conduct which was described by the primary judge as “substantial industrial theft”. In circumstances where Hytera deliberately destroyed documents (source code) which, according to their contents, would have told strongly either for or against Hytera on the question of copyright infringement, a strong inference arises that the documents would have shown infringement. All other factual findings made by the primary judge were consistent with a conclusion that the library files were compiled from source code which copied Motorola’s source code. Certainly, Hytera did not adduce evidence to negative that conclusion.
867 The factual findings made by the primary judge with respect to the library files require the conclusion that, on the balance of probabilities, the Hytera source code from which the library files were compiled reproduced a substantial part of the relevant Motorola source code. To that extent, Motorola’s ground of cross-appeal should be upheld.
868 Motorola also seeks a finding that the source code from which the Hytera library files were compiled reproduced a substantial part of the Motorola Works. The factual findings made by the primary judge do not enable this Court, at this point, to reach a conclusion on that question. For the reasons explained earlier, the primary judge’s factual findings reflected an erroneous approach to the question whether Hytera source code was a copy of a substantial part of the Motorola Works (by considering whether small portions of copied code, considered in isolation, formed a substantial part of the relevant Motorola Work and by applying a test of whether the copied code was functionally material to the relevant Motorola Work). The question whether the source code from which the Hytera library files were compiled reproduced a substantial part of the Motorola Works requires further hearing and determination, together with all other Hytera source code that was copied from Motorola source code. As stated earlier, the Court considers that the appropriate course is to conduct a further hearing at which the parties will be given an opportunity to advance further submissions in respect of the copyright infringement claims that arise on the appeal in accordance with the Court’s reasons.
C.9 Appeal grounds concerning Hytera’s knowledge of copying
Overview
869 By ground 6 of its amended notice of appeal, Hytera contends that the primary judge erred in finding (at PJ [1986]-[2002]) that Hytera knew, or ought reasonably to have known, for the purposes of s 37(1) of the Copyright Act, that if Hytera’s DMR devices has been made in Australia, this would have constituted an infringement of the copyright in Motorola’s copyright works.
870 It should be noted that Hytera’s appeal refers to s 37 of the Copyright Act but not s 38. This is no doubt because the primary judge made express findings with respect to Hytera’s knowledge in respect of s 37 (infringement by importation for the purpose of sale), but not in respect of s 38 (infringement by sale). Motorola alleged that the importation and sale of the Hytera Devices in Australia constitute infringement under both ss 37 and 38. Each of those sections requires proof that a person who imports an article into Australia (in the case of s 37) and a person who sells an imported article in Australia (in the case of s 38) knew or ought reasonably to have known that, if the article had been made in Australia, it would have constituted an infringement of copyright. The declaratory orders made by the primary judge on 7 June 2023 include a declaration that Hytera infringed Motorola’s copyright by importing the Hytera Devices into Australia and by selling the Hytera Devices in Australia. It is therefore appropriate to understand the primary judge’s findings with respect to Hytera’s knowledge as being applicable to both ss 37 and 38 of the Copyright Act. It is also appropriate to read ground 6 of Hytera’s amended notice of appeal as applying to both sections.
Hytera’s submissions
871 Hytera advanced the following submissions in support of this ground of appeal.
872 First, Hytera submitted that the primary judge ought to have found that Mr GS Kok was not acting within the scope of his authority and, therefore, Hytera should not be imputed with his knowledge. In support of that submission, Hytera relied principally on two paragraphs of an affidavit made by Mr Chen (the President of Hytera), who was not called as a witness by Hytera, but which paragraphs were tendered in evidence. The relevant paragraphs, and the circumstances of their tender (including the giving of a direction under s 136 of the Evidence Act 1995 (Cth) (Evidence Act)), were described in the primary judgement as follows:
948 Although Mr Chen was not ultimately called by Hytera as a witness, he did prepare an affidavit. Paragraph §12 and, at Hytera’s insistence, §13 of that affidavit were tendered by Motorola. They were in these terms:
12. … We gave Mr Kok authority to manage the personnel of the DMR team, including organising the structure of the team and hiring additional people when required which is Hytera’s normal practice with senior managers.
13. At around the time that Mr Kok joined Hytera, in early 2008, I recall saying to him words to the effect of ‘I expect that you will adhere to your obligations to Motorola’. I trusted that Mr Kok knew what he could and could not do within the limits of his continuing obligations to his former employer, Motorola.
949 Paragraph §13 was admitted subject to a direction under s 136 of the Evidence Act 1995 (Cth) limiting its use to qualifying the second sentence of §12 (the only sentence in §12 extracted above). …
873 The substance of Hytera’s argument was that the primary judge placed reliance on para 12 of Mr Chen’s affidavit to conclude that Mr Chen gave authority to Mr GS Kok to act to organise the structure of the DMR team, to manage that team and also to hire new personnel. However, his Honour placed no reliance on para 13, that Mr Chen told Mr GS Kok that Mr Chen expected Mr GS Kok would adhere to his obligations to Motorola, because his Honour did not consider it reliable evidence. Hytera argued that the primary judge erred by acting inconsistently with his evidentiary ruling in respect of para 13 as a statement that qualified para 12.
874 Secondly, Hytera submitted that the primary judge erred in failing to find (at PJ [2000]) that the “fraud exception” recognised in Grimaldi at [284] applied to prevent the imputation of Mr GS Kok’s knowledge to Hytera. Hytera argued that the error was manifest in the primary judge’s conclusion that the conduct by which Mr GS Kok acquired his knowledge of the facts was “not totally in fraud” of Hytera because “his actions resulted in Hytera having a commercially viable product (when it otherwise would not have) and having it faster than its original development arc would have entailed”. Hytera submitted that, for the exception to apply, the benefit must flow from the “fraud” (here the copyright infringement) (referring to Beach Petroleum NL v Johnson (1993) 43 FCR 1 (Beach Petroleum) at 30-32 and Grimaldi at [745]-[749]). Hytera submitted that the primary judge failed to have regard to the copyright infringement in this case, being merely the copying of parts of the rs_xlt_utilities.c file and the SerialHALBuffer.h file. Hytera argued that there was no evidence to support a finding that the copying of parts of those files resulted in the benefits underpinning the primary judge’s rejection of the fraud exception. Hytera also argued that the benefits found by the primary judge did not accrue by reason of the importation of the Hytera Devices into Australia, which was the relevant infringement.
Motorola’s submissions
875 In response to Hytera’s first submission, Motorola submitted that there was no error in the primary judge’s refusal to place reliance on para 13 of Mr Chen’s affidavit. Motorola noted that Mr Chen did not give evidence at trial, and his failure to attend to give evidence was unexplained by Hytera. Motorola submitted that para 13 of Mr Chen’s affidavit was not admitted in proof of the asserted fact and its only permissible use was to qualify para 12. The primary judge was entitled to place no reliance on para 13 in assessing the evidence.
876 In response to Hytera’s second submission, Motorola submitted that the primary judge was correct to recognise (at PJ [1999]) that it was not clear that the “fraud exception” applies to employees or agents simpliciter, or that Mr GS Kok was a fiduciary in the requisite sense. Motorola further submitted that, in any event, the activities of Mr GS Kok were directed towards conferring a technological and commercial benefit on Hytera, and achieved their aim, as found by the primary judge. Motorola argued that the relevant actions for the purposes of the “fraud exception” are the acts or activities of the director concerned (relying on Grimaldi at [282], [285]). In this case, the relevant actions were the acts or activities of Mr GS Kok, being Mr GS Kok’s orchestration and organisation of the DMR development team’s deliberate copying of parts of Motorola’s source code (as found by the primary judge at PJ [964], [1990], [2033]-[2034] and [2037]). Motorola argued that not only was it clear that the key benefits to Hytera outlined by the primary judge (at PJ [2000]) flowed from Mr GS Kok’s acts and activities, but Mr GS Kok was motivated to perform those acts in order to achieve those benefits for Hytera (as found by the primary judge at PJ [1990(f)] and [2033]).
Consideration
877 Before addressing the two submissions advanced by Hytera on this ground of appeal, it is necessary to explain the legal framework within which the submissions are advanced.
878 Infringement of copyright under s 37 (importation of articles into Australia for the purpose of sale) and s 38 (sale of articles in Australia) requires proof that the person who imports an article (in the case of s 37) and the person who sells an article (in the case of s 38) knew, or ought reasonably to have known, relevantly, that if the article had been made in Australia, it would have constituted an infringement of copyright. The authorities establish that the relevant knowledge is of the facts from which the finding of infringement would be made (on the hypothetical basis of the article being made in Australia), not knowledge of a contravention of the law: see Albert v S Hoffnung & Co Ltd (1921) 22 SR (NSW) 75 at 81 (Harvey J) as explained in subsequent decisions including Raben Footwear Pty Ltd v Polygram Records Inc (1997) 75 FCR 88 (Raben Footwear) at 91 (Burchett J), 97 (Tamberlin J) and 105-106 (Lehane J).
879 In the present case, the ground of appeal is not concerned with the facts known by the alleged infringer, Hytera, but with the attribution to Hytera, a corporation, of the knowledge of one its employees, Mr GS Kok.
880 As explained by the Privy Council in Meridian Global Funds Management Asia Ltd v Securities Commission [1995] 2 AC 500 (Meridian) at 506-511, the actions and knowledge of a corporation are based upon rules of attribution, as a corporation cannot act or have knowledge other than by virtue of the acts and knowledge of individuals that are attributed to the company. Prior to the decision in Meridian, the common law rules of attribution in England were generally framed by reference to the “directing mind and will” of the corporation: see generally Lennard's Carrying Co. Ltd. v. Asiatic Petroleum Co. Ltd. [1915] AC 705 (Lennard’s case) at 713 (Viscount Haldane LC) and Tesco Supermarkets Ltd v Nattrass [1972] AC 153 at 170 (Lord Reid). In Meridian, however, the Privy Council explained that the applicable rule of attribution in a given case depends upon the proper construction of the relevant rule of responsibility, liability or proscription (at 507); the test of “directing mind and will” adopted in cases such as Lennard’s case was not a universal rule for attributing knowledge to a corporation, but rather a rule determined to be applicable in the circumstances of the case (at 509).
881 The principles concerning corporate attribution stated in Meridian have been referred to with approval by the Victorian Court of Appeal in Director of Public Prosecutions (Vic) Reference No 1 of 1996 [1998] 3 VR 352 at 354 (Callaway JA, with whom Phillips CJ and Tadgell JA agreed) and by the Full Federal Court in Commonwealth Bank of Australia v Kojic (2016) 249 FCR 421 (Kojic) at [97]-[98] (Edelman J, with whom Allsop CJ generally agreed at [62]-[63]). More recently, Edelman J, as a member of the High Court in Productivity Partners Pty Ltd (trading as Captain Cook College) v Australian Competition and Consumer Commission [2024] HCA 27; 419 ALR 30, cited Meridian and Kojic in support of the following statements (at [236]):
A corporation is a construct. It does not have a natural existence in the real world. The notion of a company "doing something" is a heuristic which helps to understand legal rules for corporate liability. Usually, the description of a company as having performed some act, or having held some intention, means that there is someone whose act or intention, under the legal rules of attribution, would count as the act or intention of the company. These legal rules depend upon context or statutory interpretation but they generally require the identification of a person whose act or intention will count as the act or intention of the company.
882 The Copyright Act does not state any statutory rule for the attribution of knowledge to a corporation (compared with, for example, s 84(1) of the Competition and Consumer Act 2010 (Cth)). It follows that the applicable rule of attribution must be determined as a matter of construction of the relevant rule of liability, being ss 37 and 38 of the Copyright Act. As already noted, those sections impose liability for infringement of copyright in circumstances where an article is imported into Australia for sale, or an imported article is sold in Australia, in circumstances where the person knew or ought reasonably to have known that, if the article had been made in Australia, it would have constituted an infringement of copyright. Having regard to the relevant rule of liability, it is reasonable to conclude that the applicable rule of attribution would include persons with responsibility for, or authority over, the making of the infringing article or at least the making of that part or component of the article which renders it an infringing article.
883 In the present case, the primary judge referred to the following statement of Bright J in Brambles Holdings Ltd v Carey (1976) 15 SASR 270 at 279 (which statement was approved by the High Court in Krakowski v Eurolynx Properties Ltd (1995) 183 CLR 563 (Krakowski) at 582-583) as being an appropriate rule for attributing knowledge to a corporation for the purposes of ss 37 and 38 of the Copyright Act:
Always, when beliefs or opinions or states of mind are attributed to a company it is necessary to specify some person or persons so closely and relevantly connected with the company that the state of mind of that person or those persons can be treated as being identified with the company so that their state of mind can be treated as being the state of mind of the company. This process is often necessary in cases in which companies are charged with offences such as conspiracy to defraud.
884 On the appeal, neither party submitted that the primary judge erred in referring to the foregoing statement. However, and notwithstanding its citation by the High Court in Krakowski, the foregoing statement might be criticised for merely stating the necessary task, but not stating any guiding principle. The High Court’s decision in Krakowski concerned an allegation of fraudulent misrepresentation in connection with a contract for the sale of land. In that context, it is apparent that the majority (Brennan, Deane, Gaudron and McHugh JJ) considered that the knowledge of those given responsibility for the negotiation of the contract was attributable to the corporation (at 582). The approach taken by the High Court in Krakowski is consistent with the conclusion that, for the purposes of ss 37 and 38 of the Copyright Act, the applicable rule of attribution would include persons with responsibility for, or authority over, the making of the infringing article or at least the making of that part or component of the article which renders it an infringing article.
885 The primary judge concluded that Mr GS Kok’s knowledge as at September 2013 should be attributed to Hytera. His Honour did so because Mr GS Kok was, as at September 2013, sufficiently closely and relevantly connected to Hytera that the state of his mind should be attributed to it (PJ [1998]). His Honour also concluded that Mr YT Kok and Mr Chia were also sufficiently closely and relevantly connected to Hytera that their state of mind should be attributed to it also (PJ [1998]). In that context, his Honour made findings that:
(a) Mr GS Kok was in charge of the DMR team and had been given authority by Mr Chen to organise the structure of the DMR team, to manage that team and also to hire new personnel (PJ [1990(a)]);
(b) by September 2013, Mr GS Kok had been promoted to the position of Senior Vice President in the Office of the President Department, which was a very senior management position (PJ [1994(k)]);
(c) Mr GS Kok was both aware of the fact that some of Motorola’s code was being used to create some of Hytera’s code and was the directing mind behind this activity and responsible for it (PJ [1994(m)]);
(d) Mr Chia and Mr YT Kok occupied senior positions within the DMR team and assisted Mr GS Kok by giving effect to his instructions (PJ [1994(n) and (o)]).
886 Against that background, Hytera’s first submission on this ground of appeal can be rejected as hopeless. There was a wealth of evidence and factual findings made by the primary judge which supported a conclusion that Mr GS Kok was in charge of the DMR team and had overall responsibility for the development of Hytera’s software for its DMR devices. That fact could not seriously be challenged by Hytera on this appeal. Hytera seeks to establish, by the side wind of para 13 of Mr Chen’s affidavit tendered at the hearing, that Mr GS Kok’s authority had been limited by Mr Chen by reason of Mr Chen saying to Mr GS Kok words to the effect of ‘I expect that you will adhere to your obligations to Motorola’. Hytera’s submission faces the insurmountable hurdle that the asserted fact, that Mr GS Kok’s authority had been limited by Mr Chen in the manner specified, was not established on the evidence. Mr Chen chose not to give evidence. While para 12 of Mr Chen’s affidavit (set out above) was tendered by Motorola under s 81(1) of the Evidence Act as an exception to the rule against hearsay as an admission, para 13 was tendered at the request of Hytera under s 81(2) of the Evidence Act on the basis that it was a statement to which it was reasonably necessary to refer in order to understand the admission. The primary judge permitted para 13 to be tendered on that basis but gave a direction under s 136 of the Evidence Act limiting its use to qualifying the evidence in para 12. As submitted by Motorola, para 13 was not admitted into evidence as proof of the facts asserted into that paragraph. The only permissible use of para 13 was to qualify the evidence given by para 12. However, the primary judge was not obligated to place any weight or reliance on para 13 by way of qualification to the evidence in para 12. There is no error in the following passage of his Honour’s reasoning (at [949]):
… Whilst Mr Chen’s affidavit is inherently reliable in terms of establishing what Mr GS Kok’s role was (and, indeed, is an admission in that regard) I do not regard §13 as having the same quality. The question of whether Mr GS Kok was instructed by Mr Chen that he should adhere to his obligations to Motorola is a central question in the case. Had Mr Chen given evidence this would, no doubt, have been tested by cross-examination. There are questions about Mr Chen’s role in the events which transpired. Since his evidence has not been tested, I think it would be unsafe to rely upon it. I therefore do not find on the basis of §13 that Mr Chen told Mr GS Kok that he should adhere to his obligations to Motorola. I do not find it on any other basis either.
887 The short answer to Hytera’s first submission is that the evidence did not establish that Mr GS Kok’s authority over Hytera’s DMR team was limited in any relevant way.
888 Hytera’s second submission on this ground of appeal is an exercise in artificiality and should also be rejected. It should be noted at the outset that, in considering Hytera’s second submission, it will be assumed without deciding that the so-called “fraud exception” to the attribution of knowledge to a corporation is applicable to statutory provisions such as ss 37 and 38 of the Copyright Act. Whilst at trial Motorola submitted that the fraud exception was inapplicable on the facts of the case, it did not submit that the fraud exception was inapplicable as a matter of law. The primary judge therefore considered the matter on the basis that the fraud exception was capable of applying. On the appeal, Motorola adopted the same position as at trial. For the reasons that follow, the primary judge was correct to reject Hytera’s reliance on the fraud exception and it is therefore unnecessary, and it would be inappropriate, for this Court to consider the legal applicability of the fraud exception more generally.
889 The fraud exception was discussed by the Full Federal Court in Grimaldi at [282]-[286]. The Court referred first to the principle stated by Vaughan Williams J in Re Hampshire Land Company [1896] 2 Ch 743 that a director’s knowledge of his or her own fraud (or breach of duty) against the company is not to be imputed to the company. The Full Court next observed that the fraud exception has been accepted in first instance decisions in Australia (citing Beach Petroleum) and has also been extended beyond knowledge of fraud to that of breach of fiduciary duty “at least where the fiduciary’s conduct is morally reprehensible” (citing Aequitas Ltd v AEFC Leasing Pty Ltd (2001) 19 ACLC 1,006 at 1,062 and Farrow Finance Company Ltd (in liq) v Farrow Properties Pty Ltd (in liq) [1999] 1 VR 584 at 627-628). The Court then referred to the relevant limitation upon the exception stated by von Doussa J in Beach Petroleum, that the exception will not apply if the director’s conduct is not totally in fraud of the company. Relevantly, von Doussa J stated in Beach Petroleum at 31-32:
Provided that the director is acting within the scope of his or her authority, in civil proceedings the state of mind of a director ordinarily will be attributed to the company where there is a duty on that director to communicate his or her knowledge to the company. The exception to this rule is where the director is acting totally in fraud of the company, that is, where all the director's activities are directed against the interests of the company, and not partly for the benefit of the company. If the director is guilty of fraudulent conduct which is not totally in fraud of the corporation, and by design or result the fraud partly benefits the company, the knowledge of the director in the transaction will be attributed to the company.
890 With reference to those principles, the primary judge concluded (at [2000]):
… In this case, the conduct by which Mr GS Kok acquired his knowledge of the facts was not totally in fraud of Hytera. Quite to the contrary, his actions resulted in Hytera having a commercially viable product (when it otherwise would not have) and having it faster than its original development arc would have entailed. Mr GS Kok intended to benefit Hytera by his actions and he was successful in this endeavour. If it be relevant, the same may be said of Mr Chia and Mr YT Kok.
891 Hytera’s challenge to those findings is artificial and barely comprehensible. Hytera argued that the relevant “fraud”, being the copyright infringement, was confined to the copying of two Motorola source code files and the importation of Hytera Devices which contained (an adaptation of) the copied code. Hytera contends that the fraud, as so defined, did not generate benefits for Hytera. Rather, Hytera’s development of its DMR devices was the result of extensive other work.
892 The submission fails to comprehend the proper basis of the fraud exception. To apply, the director must be acting “totally in fraud of the company”, that is, “where all the director’s activities are directed against the interests of the company and not partly for the benefit of the company”. In the present case, Mr GS Kok was responsible for and had full knowledge of the activities of the DMR team which, as found by the primary judge (at PJ 1576]), engaged in industrial scale harvesting of Motorola’s source code and which, the primary judge found (at PJ [5]), involved a “substantial industrial theft”. The motivation was to get the Hytera devices to market as quickly as possible at the lowest cost (PJ [1990(f)]). Hytera benefitted from the actions of the ex-Motorola engineers in at least two ways: it got to market with devices which were commercially competitive with Motorola’s products where otherwise it would not have done so and it got to market by no less than 15 months earlier than it otherwise would have (PJ [1992]). It is impossible for Hytera to contend, in those circumstances, that all of Mr GS Kok’s activities were directed against the interests of Hytera and not partly for the benefit of Hytera. The fraud exception has no application in this case and Hytera’s ground of appeal must be rejected.
C.10 Appeal grounds concerning additional damages
Overview
893 By ground 7 of its amended notice of appeal, Hytera contends that the primary judge erred in finding (at PJ [2086]), in relation to Hytera’s infringement of copyright, that the requirements set out in s 115(4) of the Copyright Act, pursuant to which the Court may award additional damages, were satisfied. Hytera’s particulars to appeal ground 7 allege two principal categories of error, the first relating to the flagrancy of infringement, the factor referred to in s 115(4)(b)(i), and the second relating to other factors referred to in s 115(4)(b).
894 Hytera contends that the primary judge erred in finding that Hytera’s infringements were flagrant (PJ [2033]-[2051]). In that regard, Hytera contends that the primary judge erroneously equated the type of knowledge required for the purpose of s 37 of the Copyright Act with the type of knowledge required for the purpose of flagrancy under s 115(4)(b)(i) of the Copyright Act (PJ [2037], [2038]). Hytera also contends that, in assessing flagrancy, the primary judge made the same errors concerning Hytera’s knowledge of infringement as alleged by Hytera in respect of ground 6 (concerning ss 37 and 38 of the Copyright Act). Those matters have been addressed in respect of ground 6 and rejected.
895 Hytera also contends that the primary judge erred by not giving sufficient weight to factors other than flagrancy, particularly the limited extent of the infringements (at PJ [2067]), the finding that Hytera had reasonably arguable defences (at PJ [2068]) and Hytera’s conduct after it was notified of Motorola’s allegations (PJ [2079]-[2082]).
896 Hytera’s particulars to appeal ground 7 also contend that, if the primary judge’s findings of copyright infringement are varied by this Court, it will also be necessary for the primary judge’s conclusion with respect to additional damages to be revisited. That contention should be accepted, but does not concern error in the primary judge’s conclusion with respect to additional damages.
Hytera’s submissions
897 Hytera acknowledged that the power to award additional damages under s 115(4) of the Copyright Act is discretionary. It submitted, however, that the primary judge’s exercise of discretion was affected by error within the principles stated in House v The King (1936) 55 CLR 499 (House v The King) at 505.
898 With respect to the primary judge’s finding that Hytera’s copyright infringement was flagrant, Hytera did not develop its contention that the types of knowledge required for the purpose of ss 37 and 38 of the Copyright Act differ from the types of knowledge required for the purpose of flagrancy under s 115(4) of the Copyright Act. It is therefore unnecessary to consider that contention. More generally on the question of flagrancy, Hytera relied on the submissions made in respect of ground 6. As noted above, those submissions have been rejected. However, Hytera also sought to develop one aspect of its ground 6 submissions for the purposes of ground 7. Hytera submitted that the primary judge erred in finding that Hytera’s infringements were flagrant by failing to have regard or proper regard to “the infringements” themselves to determine whether they were flagrant as required by the language of s 115(4)(b)(i). In particular, Hytera argued that his Honour gave no consideration to the parts of code taken from the rs_xlt_utilities.c file and the SerialHALBuffer.h file in assessing flagrancy. Hytera also submitted that the reasoning underpinning the flagrancy finding was that “the ex-Motorolans set out to copy parts of Motorola’s source code to assist in the production of a commercially competitive product and to expedite the development process” (PJ [2033]). Hytera argued that the evidence did not establish a causal relationship between those two key benefits and the parts held to have been taken from the rs_xlt_utilities.c file and the SerialHALBuffer.h file. Hytera also argued that, in any event, those two key benefits did not accrue by reason of the infringements that relate to the importation of Hytera’s devices into Australia and providing updated firmware in Australia.
899 With respect to the primary judge’s assessment of factors other than flagrancy, Hytera’s primary submission was that the primary judge did not give them sufficient weight. First, Hytera emphasised the primary judge’s finding that the infringements were limited to the copying of parts of two computer files (PJ [2067]). Second, Hytera emphasised the primary judge’s finding that Hytera had reasonably arguable defences (PJ [2068]). In that regard, Hytera placed reliance on the statement of the Full Federal Court in Oxworks Trading Pty Ltd v Gram Engineering Pty Ltd [2019] FCAFC 240; 154 IPR 215 (Oxworks), made in the context of an award of additional damages under the Patents Act, that a reasonably arguable defence “is a strong factor telling against the award of additional damages” (at [66]). Hytera submitted that the same principle applies under the Copyright Act. Third, Hytera emphasised the primary judge’s findings concerning Hytera’s conduct after it was notified of Motorola’s allegations, particularly the steps taken to rewrite its firmware (PJ [2079]-[2082]).
Motorola’s submissions
900 Motorola’s headline submission was that Hytera had not identified any relevant House v The King error.
901 In respect of the flagrancy of infringement, Motorola relied principally on the submissions advanced in respect of ground 6. Additionally, Motorola argued that Hytera was wrong to submit that the basis for the primary judge’s finding of flagrancy was merely that the ex-Motorola engineers set out to copy Motorola’s source code to assist in the production of a commercially competitive product and to expediate the development process; the basis included the matters referred to at PJ [2039]-[2051] including in particular his Honour’s finding (at PJ [2050]) that, from the date of Mr Chia’s interview (sometime between March and 23 May 2017) and after Hytera’s internal investigation in June 2018, Hytera knew in every sense that its firmware had been developed using Motorola’s source code, quite apart from the knowledge of Mr GS Kok.
902 In respect of the other factors referred to by Hytera, Motorola submitted that the primary judge made findings on each and took them into account. As such, no House v The King error had been identified.
Consideration
903 The authorities make clear that the award of additional damages under s 115(4) of the Copyright Act is discretionary. The matters enumerated in s 115(4)(b) are not conditions to the award of additional damages, but factors to be taken into account; additional damages may be awarded notwithstanding that one or more of those factors is not present: Raben Footwear at 93 (Burchett J, with whom Lehane J agreed) and 103 (Tamberlin J); Aristocrat Technologies Australia Pty Ltd v DAP Services (Kempsey) Pty Ltd (in liq) (2007) 157 FCR 564 (Aristocrat v DAP Services) at [41] (Black CJ and Jacobson J). Additional damages under s 115(4) may be awarded on principles that correspond to those governing awards of aggravated and exemplary damages at common law, which include punitive and deterrent objectives: Raben Footwear at 93; Aristocrat v DAP Services at [42] and [43]; Venus Adult Shops Pty Ltd v Fraserside Holdings Ltd (2006) 157 FCR 442 (Venus) at [114] (French and Kiefel JJ).
904 It follows that an appeal from the exercise of discretion under s 115(4) is subject to the principles stated in House v The King. The weight to be given to the mandatory considerations enumerated in s 115(4)(b) is a matter for the trial judge and error is not established merely by a contention that the trial judge gave too much or too little weight to a particular factor: Venus at [119].
905 Hytera’s submissions do not identify any error of fact or law in the primary judge’s assessment of additional damages under s 115(4) of the Copyright Act.
906 With respect to the flagrancy of infringement, there is no merit in Hytera’s submission that the primary judge failed to have proper regard to the nature of the infringements that were found. It was unnecessary for the primary judge to repeat all of his Honour’s earlier findings when considering flagrancy. His Honour was plainly conscious of the extent of copying because he expressly addressed Hytera’s submission that the nature of the infringements was limited and in respect of relatively insignificant parts of the pleaded and particularised works (at PJ [2065]ff).
907 There is also no merit in Hytera’s submission that there was a lack of “causal connection” between the extent of copying that was found to infringe Motorola’s copyright and the finding that the ex-Motorola engineers set out to copy parts of Motorola’s source code to assist in the production of a commercially competitive product and to expedite the development process (at PJ [2033]). The relevant issue is not what caused the copying but what were the circumstances in which the copying occurred. The relevant circumstances were summarised by the primary judge and included the facts that:
(a) the ex-Motorola engineers set out to copy parts of Motorola’s source code to assist in the production of a commercially competitive product and to expedite the development process (PJ [2033]);
(b) the ex-Motorola engineers took steps to conceal their copying (PJ [2033]);
(c) the conduct of the ex-Motorola engineers was morally reprehensible (PJ [2034]);
(d) at the time that the Hytera Devices were imported into Australia, Hytera knew (by reason of the attribution of the knowledge of Mr GS Kok) that, if the devices had been made in Australia, this would have constituted an infringement of copyright (PJ [2037], [2038]).
908 There is no error in the primary judge having taken those circumstances into account.
909 There is even less merit in Hytera’s submission that in some manner the primary judge failed to take into account the fact that Hytera’s infringement of copyright related to the importation of the Hytera Devices into Australia and making the Hytera Firmware available in Australia. The submission was difficult to comprehend, but appeared to be that those acts of infringement were unconnected with the morally reprehensible behaviour of the ex-Motorola engineers. The submission should be rejected. The importation of the Hytera Devices into Australia, and the making available of the Hytera Firmware in Australia, involved copyright infringement for the reason that Hytera’s firmware was an adaptation of a substantial part of the Motorola Works. The fact that Hytera’s firmware was an adaptation of a substantial part of the Motorola Works was by reason of the morally reprehensible conduct of the ex-Motorola engineers when employed by Hytera.
910 With respect to the primary judge’s assessment of factors other than flagrancy, Hytera’s primary submission, that the primary judge did not give those factors sufficient weight, does not of itself establish error. The primary judge made careful findings of fact in respect of each of the mandatory statutory factors. Hytera has not demonstrated error in any of those factual findings, nor that the primary judge failed to take account of a mandatory relevant consideration or took account of an irrelevant consideration.
911 Nor has Hytera demonstrated that the primary judge acted on a wrong principle. While Hytera placed reliance on the statement in Oxworks that a reasonably arguable defence “is a strong factor telling against the award of additional damages” (at [66]), the primary judge made a finding, and took into account, that Hytera had a reasonable defence (PJ [2068]). Furthermore, the statement in Oxworks must be understood in the context of that case. The relevance of a “reasonably arguable defence” depends upon the factor being considered. If the factor is the flagrancy of the copying (whether under patent law or copyright law), it is relevant to consider whether the infringer believed that they had a reasonably arguable defence at the time of copying. That was the factor being considered in Oxworks. If the factor is the conduct of the infringer after they are informed of the alleged infringement, it is relevant to consider whether the infringer believed that they had a reasonably arguable defence at that time. The fact that the infringer conceives of a reasonably arguable defence at trial, which ultimately fails, may have little bearing on the question of additional damages: see Fuchs Lubricants (Australasia) Pty Ltd v Quaker Chemical (Australasia) Pty Ltd (2021) 284 FCR 174 at [403]-[406].
912 Hytera has not demonstrated error in the primary judge’s conclusion with respect to additional damages and ground 7 is therefore rejected.
C.11 Summary of conclusions on the copyright infringement grounds of appeal
913 In summary, the following grounds of appeal and contention are upheld (in whole or in part).
914 The first is ground 2 of Motorola’s amended notice of cross-appeal and ground 2 of Motorola’s amended notice of contention in Hytera’s appeal. With respect to those grounds, the following conclusions have been reached:
(a) The primary judge was in error to approach the question of infringement by considering whether small segments of Hytera source code which had been copied from a Motorola Work formed a substantial part of the relevant Motorola Work. The question to be determined was whether, in respect of each of the Motorola Works, the totality of the Motorola source code copied by Hytera (into the impugned Hytera source code) was a substantial part of the Motorola Work.
(b) The primary judge erred in two respects in his approach to the assessment of the substantiality of the copied code. First, his Honour incorrectly applied two tests or conditions for the assessment, being materiality and originality, when there is only one question to be answered. Second, his Honour applied a test of whether the copied code was functionally material to the relevant Motorola Work in the sense of being significant or important to the operation of the DMR. Motorola’s submissions should be accepted that the question of substantial part is to be determined by reference to the originality of the code that has been copied, which requires consideration of the creative and intellectual contribution to the form of expression of the code, including such matters as the structure of the code and the choice and sequencing of commands.
(c) By reason of adopting an erroneous approach to the assessment of substantial part, the primary judge necessarily failed properly to have regard to the evidence of Motorola’s witnesses as to the significance of the copied code as a whole to each of the Motorola Works.
915 The second is ground 3 of Motorola’s amended notice of cross-appeal and ground 3 of Motorola’s amended notice of contention in Hytera’s appeal. On those grounds, the following conclusions have been reached:
(a) The primary judge erred in not drawing an inference of copying in favour of Motorola in respect of the source code from which the Hytera library files raf_arm9.lib, rfhal_c55.lib and DmrDspLib.lib were compiled.
(b) The factual findings made by the primary judge with respect to the library files require the conclusion that, on the balance of probabilities, the Hytera source code from which the library files were compiled reproduced a substantial part of the relevant Motorola source code.
916 The third is grounds 2 and 4 of Hytera’s amended notice of cross-contention in Motorola’s cross-appeal. On those grounds, it has been concluded that the primary judge erred in finding that the following parts of Hytera source code were objectively similar to (or reproduced) parts of the Motorola Works:
(a) lines 120-147 and 148-178 of the Hytera file raf_app.h; and
(b) lines 66-91 of Hytera’s file ps_app_mgr.cpp.
917 All other grounds of appeal and contention with respect to copyright infringement have been rejected or have been rendered nugatory by the acceptance of the foregoing grounds of appeal.
D.Conclusion and orders
918 In conclusion, Hytera’s appeal, constituted by its amended notice of appeal dated 8 November 2023, is dismissed. An order to that effect will be made.
919 With respect to Motorola’s cross-appeal, constituted by its amended notice of cross-appeal dated 27 November 2023, ground 1 is rejected while grounds 2 and 3 are upheld. However, as stated earlier in these reasons, to this point the Court is not able to determine whether Motorola’s claim of copyright infringement should succeed in whole or in part. Relevant factual findings have not been made that would enable this Court to determine finally the copyright infringement case applying the methodology that the Court considers is correct. Within the time allowed for the appeal to this point, the Court was not taken to the entirety of the evidence that might enable further factual findings to be made. The Court considers that the appropriate course is to conduct a further hearing at which the parties will be given an opportunity to advance further submissions in respect of the copyright infringement claims that arise on the appeal in accordance with the Court’s reasons. The hearing will be a continuation of the cross-appeal. The Court will list the matter for further case management to make timetabling orders for the conduct of the further hearing. It necessarily follows that the Court will not make final orders with respect to Motorola’s cross-appeal at this time.
920 As observed earlier in these reasons, the evidence adduced at trial was voluminous and the subject matter of the proceeding was technical and complex. In a case such as the present, the assessment by the Court of whether the Hytera Firmware constitutes an adaptation of a substantial part of one or more of the Motorola Works is an onerous and burdensome task. The reasons of this Court require the assessment of that issue to be undertaken on a different basis to that undertaken by the primary judge. It is necessary to determine, in respect of each of the Motorola Works, whether the totality of the Motorola source code copied by Hytera (into the impugned Hytera source code) was a substantial part of one or more of the Motorola Works. The question of substantial part is to be determined by reference to the originality of the code that has been copied, which requires consideration of the creative and intellectual contribution to the form of expression of the code, including such matters as the structure of the code and the choice and sequencing of commands.
921 There are procedures available to the Court to assist it in both understanding and assessing technical evidence, such as the appointment of an assessor with relevant technical expertise to assist the Court and the referral of one or more questions to a referee with relevant technical expertise for inquiry and report. In conducting the further hearing of the copyright infringement claims that arise on the appeal in accordance with the Court’s reasons, the Court will give consideration to seeking the assistance of an assessor or the referral of relevant questions to a referee. The continuation of the hearing of the cross-appeal will require fresh consideration of the lay and expert evidence with respect to the relevant computer code, and there appears to be considerable scope for the Court and the parties to implement procedures that enable the just and efficient resolution of the issues in dispute.
922 The Court proposes to defer the question of the costs of the appeals until the finalisation of the issues arising on Motorola’s cross-appeal. In due course, the Court proposes to make a single order as to the costs of the appeals, rather than make separate orders in each appeal, because of the intermingling of issues between the appeals and the difficulties that would be encountered by the parties in attempting to allocate the total costs incurred between the appeal and the cross-appeal on a fair basis. Nevertheless, it is appropriate to record the Court’s assessment at this point that Hytera was wholly unsuccessful on its appeal, on both patent and copyright grounds, and that Motorola has been successful on its cross-appeal on the copyright grounds but unsuccessful on the patent ground. As such, the Court considers that an appropriate allocation of the costs of the appeals to this point is that Hytera pays 90% of Motorola’s costs of the appeals (being both Hytera’s appeal and Motorola’s cross-appeal). The final order as to the costs of the appeals will take into account the Court’s assessment to this point and any further submissions to be made by the parties.
923 Finally, the substantive part of these reasons will be temporarily suppressed to afford the parties an opportunity to consider whether any part of the reasons reveals commercial in confidence information and to make an application for redaction of any such information from the published version of the reasons.
I certify that the preceding nine hundred and twenty-three (923) numbered paragraphs are a true copy of the Reasons for Judgment of the Honourable Justices Beach, O'Bryan and Rofe. |
Associate:
Dated: 18 December 2024




